Adobe certification revocation for October 4th
Yesterday Adobe came out in a bog post stating an "inappropriate use of an Adobe code signing certificate for Windows".
Apparently they discovered a "compromised build server with access to Adobe code signing infrastructure". (Which is corporate speak for "one of our servers was hacked".) They "immediately decommissioned the existing Adobe code signing infrastructure and initiated a forensics investigation to determine how these signatures were created".
This apparently only effects "the Windows platform" and "three Adobe AIR applications for both Windows and Macintosh". I found a list of the applications involved, and how to update them on this page: http://helpx.adobe.com/x-productkb/global/certificate-updates.html. This update revocation will not occur until the 4th of October. (Next Thursday).
The interesting section (to me at least) of this post is the middle section:
We have identified a compromised build server that required access to the code signing service as part of the build process. Although the details of the machine’s configuration were not to Adobe corporate standards for a build server, this was not caught during the normal provisioning process. We are investigating why our code signing access provisioning process in this case failed to identify these deficiencies. The compromised build server did not have rights to any public key infrastructure (PKI) functions other than the ability to make code signing requests to the code signing service.
Our forensic investigation is ongoing. To date we have identified malware on the build server and the likely mechanism used to first gain access to the build server. We also have forensic evidence linking the build server to the signing of the malicious utilities. We can confirm that the private key required for generating valid digital signatures was not extracted from the HSM. We believe the threat actors established a foothold on a different Adobe machine and then leveraged standard advanced persistent threat (APT) tactics to gain access to the build server and request signatures for the malicious utilities from the code signing service via the standard protocol used for valid Adobe software.
The build server used a dedicated account to access source code required for the build. This account had access to only one product. The build server had no access to Adobe source code for any other products and specifically did not have access to any of Adobe’s ubiquitous desktop runtimes such as Flash Player, Adobe Reader, Shockwave Player, or Adobe AIR. We have reviewed every commit made to the source repository the machine did have access to and confirmed that no source code changes or code insertions were made by the build server account. There is no evidence to date that any source code was stolen.
Naturally people are writing in to us asking what this impacts (see the first link above) and what happened, (the second link above). But there is one thing we are sure of, we don't know the extent of the damage, and hope there was nothing more compromised than what Adobe has found in their investigation. I know Brad Arkin and trust him, so I don't have any reason to doubt him and his team (who are very good, and work very hard by the way, I don't want anyone to get the wrong impression), but "you never know", I guess, is my point.
Since I work for an IDS vendor, (Sourcefire, in the interest of full disclosure), our customers were very interested in the rules we released yesterday to cover this. So this is definitely on people's minds.
-- Joel Esler | http://blog.joelesler.net | http://twitter.com/joelesler
ISC Feature of the Week: Glossary
Overview
Our feature today is a page we just launched, the Glossary: Terms and Definitions page at https://isc.sans.edu/glossary.html! This page allows for browsing and list filtering of Computer and Security-related terms and definitions. There is also an API at https://isc.sans.edu/api/#glossary which I'll also detail below.
We will soon be adding a Suggest a New Term or Definition form where you can contribute your thoughts to the list.
Features
Overview - https://isc.sans.edu/glossary.html#overview
Description of page sections, API and displays current number of Terms in the system.
List of Terms - https://isc.sans.edu/glossary.html#terms
Text box will dynamically filter the multi-column list to terms that contain what you enter. For example, if you start typing 'by' the list will be restricted to terms such as 'byte' and 'gethostbyaddr'. Delete characters you've typed to expand list back to all terms.
Clicking the term will jump down to the matching Term and Definition section.
List of Definitions - https://isc.sans.edu/glossary.html#definitions
A heading row with the Alpha-numeric preface is above each section. The quick links under the title at the top of the page contains number and letter links to each header section such as https://isc.sans.edu/glossary.html#A.
The term and definition list alphabetically. Keep an eye out for a "Share Term" and "Suggest a definition" link soon.
Glossary API - https://isc.sans.edu/api/#glossary
The API outputs all terms and definitions by default. https://isc.sans.edu/api/glossary
You can add a partial or full word to the url to "search" for a matching term. https://isc.sans.edu/api/glossary/data
As a reminder, all content is governed under the Creative Common share alike attribution policy. More details can be found at http://creativecommons.org/licenses/by-nc/3.0/us/ and https://isc.sans.edu/privacy.html
Post suggestions or comments in the section below or send us any questions or comments in the contact form on https://isc.sans.edu/contact.html#contact-form
--
Adam Swanger, Web Developer (GWEB, GWAPT)
Internet Storm Center https://isc.sans.edu
3 Comments
More Java Woes
A number of readers alerted us of news reports stating that new "full sandbox escape" vulnerabilities had been reported to Oracle. At this point, there are no details available as to the nature of these vulnerabilities, and there is no evidence that any of these vulnerabilities are exploited. However, it is widely known that Oracle is working on a substantial backlog of these vulnerabilities. It is still recommended to use Java "with caution". Some best practices:
- Uninstall Java if you don't need it.
- if you do need Java, make sure it doesn't start automatically in your web browser.
- keep Java up to date
- reduce the number of Java variants you have installed to the minimum you need.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
Some Android phones can be reset to factory default by clicking on links
Many mobile browsers do support "tel" urls, These URLs start with "tel:" instead of "http:", and can be used to create "call me" links on web pages. Usually, if a user clicks on one of these links, the phone will present a dialog, confirming if the user would like to "dial" the number.
However, some Android phones use special dial codes to access some of the phone's features. These codes are known as USSD codes (Unstructured Suplemental Service Data), and reasonably well documented. For example, if you type "*#06#" on your phone, it will show it's IMEI number before you hit "dial" (this works on most GSM phones, not just Android phones). Some Android phones add their own proprietary codes. For example, the Samsung Galaxy S3 phone has a code like this to perform a factory reset, which will delete all data on the phone, and once started, can not be canceled. As no "dial" action is required for these codes, just clicking the URL will execute the feature.
Here a quick test link that will show the IMEI: *#06# (iPhones will ask for confirmation first)
Demo video: http://www.youtube.com/watch?v=Q2-0B04HPhs
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
5 Comments
Update for CVE-2012-3132
In July of this year Oracle sent a vulnerability notification to it's users for the Oracle Security Alert CVE-2012-3132. At the time of the publication of the security bulletin it was noted that this exploit was not remotely exploitable. The remote capabilities, or lack thereof, in this vulnerability was called into question, with a very interesting write up on the Kaspersky Labs Security News Service. Many organizations I have worked with would initially deem this a very low risk, due to the lack of remote capabilities, so it may be time for a reassessment of the risk.
I am not on the Oracle Security newsfeeds, so if anybody has a notification from Oracle that they are permitted to share, we would love to help get the word out.
tony d0t carothers - gmail
1 Comments
Storing your Collection of Malware Samples with Malwarehouse
Scott Roberts released a simple yet easy to use Python script to store and query your collection of malware samples into a SQLite database. The process is simple; it allows storage (indexing basic sample metadata) and retrieval of your samples. The database allows for query by filename, MD5 and SHA256 hashes. The malwarehouse package can be downloaded here.
I changed my database location from the malwarehouse.py script option_base_dir = os.path.expanduser("~/Desktop/malwarehouse/") to option_base_dir = os.path.expanduser("~/malwarehouse/") because this server doesn't have X-Windows running.
- First a simple menu:
- Entering a malware sample into the SQLite database:
guy@seeker:~/malwarehouse$ ./malwarehouse.py -s zz87lhfda88.com -t PWS-LegMir.dll -n "Low detection" 1.exe
- Result when malware sample 1.exe is processed:
guy@seeker:~/malwarehouse$ ./malwarehouse.py -s zz87lhfda88.com -t PWS-LegMir.dll -n "Low detection" 1.exe
Parsing Malware
Analysis complete. Loading.
Sample 1.exe loaded...
Loading Malware 1.exe
Creating /home/guy/malwarehouse/41f5e475e086c991873a35c58234213fc01331d655f3f39a2f1a6d2f0e0ed6b8
- Reviewing the last record with the 3 available methods:
guy@seeker:~/malwarehouse$ ./malwarehouse.py -f 41f5e475e086c991873a35c58234213fc01331d655f3f39a2f1a6d2f0e0ed6b8
guy@seeker:~/malwarehouse$ ./malwarehouse.py -f 4f871a6b9f17c0923963e7dfc73efa58
guy@seeker:~/malwarehouse$ ./malwarehouse.py -f 1.exe
- Reviewing the last 3 recorded inserted into the malwarehouse database:
If you are looking for a simple and yet effective way of tracking your malware samples, malwarehouse is probably for you. I'm sure Scott Robert is open to suggestions to improve this project . His contact information is listed on the Github download page.
[1] blog.thevigilant.com
[2] https://github.com/sroberts/malwarehouse
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
3 Comments
Update for Vulnerabilities in Adobe Flash Player in Internet Explorer 10 (2755801)
Microsoft released Security Advisory 2755801 that addresses vulnerabilities in Adobe Flash Player in Internet Explorer 10 on Windows 8. The bulletin is available here.
[1] http://technet.microsoft.com/en-us/security/advisory/2755801
[2] http://blogs.technet.com/b/msrc/archive/2012/09/21/security-advisory-2755801-addresses-adobe-flash-player-issues.aspx
[3] http://www.adobe.com/support/security/bulletins/apsb12-19.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
IE Cumulative Updates MS12-063 - KB2744842
This is a list of links of where each patches can be downloaded that addresses the vulnerability discussed in Microsoft Security Bulletin MS12-063 and reported in diary IE Fixes Available yesterday.
Cumulative Security Update for Internet Explorer 7 for Windows XP (KB2744842)
[1] http://www.microsoft.com/en-us/download/details.aspx?id=34723&WT.mc_id=rss_allproducts_ie
Cumulative Security Update for Internet Explorer 8 for Windows XP (KB2744842)
[2] http://www.microsoft.com/en-us/download/details.aspx?id=34731&WT.mc_id=rss_allproducts_ie
Cumulative Security Update for Internet Explorer 8 in Windows Vista (KB2744842)
[3] http://www.microsoft.com/en-us/download/details.aspx?id=34718&WT.mc_id=rss_allproducts_ie
Cumulative Security Update for Internet Explorer 9 in Windows Vista (KB2744842)
[4] http://www.microsoft.com/en-us/download/details.aspx?id=34732
Cumulative Security Update for Internet Explorer 8 in Windows 7 (KB2744842)
[5] http://www.microsoft.com/en-us/download/details.aspx?id=34736&WT.mc_id=rss_allproducts_ie
Cumulative Security Update for Internet Explorer 9 in Windows 7 (KB2744842)
[6] http://www.microsoft.com/en-au/download/details.aspx?id=34713
Cumulative Security Update for Internet Explorer for Windows Server 2003 (KB2744842)
[7] http://www.microsoft.com/en-us/download/details.aspx?id=34725&WT.mc_id=rss_allproducts_ie
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
8 Comments
iOS 6 Security Roundup
With the release of iOS 6 earlier this week, a couple of iOS security related features changed in how they behaved. These come in addition to the long list of security fixes that Apple released in iOS 6. [1]
Siri: Siri gained additional capabilities, including the ability to Tweet and update Facebook. This feature is available even on a locked iPhone. To disable this feature, make sure Siri is disabled when the phone is locked.
Password less updates: Updating Apps no longer requires that you enter your password. I haven't found a method yet to turn this off (but actually like it, as my iTunes password is quite complex)
Social Media Integration: Adding a Facebook account to your iOS device will sync your contact settings with Facebook (there is a clear warning that this will happen). Facebook recently changed the default address of all accounts to @facebook.com and e-mail addresses in your contact list may be updated with the @facebook.com address as a result.
A bug found at this week's pwn20wn contest at the EuSecWest conference apparently leaks personal information like contacts and pictures to malicious websites. The bug was demonstrated in iOS 5.1.1, but has not been fixed yet in iOS 6 as it was just reported to Apple this week. [2]]
[1] http://prod.lists.apple.com/archives/security-announce/2012/Sep/msg00003.html
[2] http://www.techspot.com/news/50232-galaxy-s3-and-iphone-4s-exploited-at-pwn2own-competition.html
Any other security related issues you noticed?
Update: Link to patches added per the comment below.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
Financial sector advisory: attacks and threats against financial institutions
1 Comments
Apple and Cisco Security Advisories 19 SEP 2012
Security Update 2012-004
0 Comments
IE Fixes Available
Hoping to put a close on Monday's IE Zero-day vulnerability (https://isc.sans.edu/diary.html?storyid=14107) Microsoft has announced the release of a FixIt (http://support.microsoft.com/kb/2757760) to address the issue, with a patch to be made available via Windows Update this friday (http://blogs.technet.com/b/msrc/archive/2012/09/19/internet-explorer-fix-it-available-now-security-update-scheduled-for-friday.aspx)
Can we look forward to more timely security patch releases from Microsoft? That would be good news indeed.
12 Comments
Sophos detecting itself as SHH/Updater-B
The latest definition file for Sophos is having some unintended consequences. It is currently being discussed on their website: http://community.sophos.com/t5/Sophos-Endpoint-Protection/Is-any-one-else-seing-this-alert/td-p/29723
More to come.
6 Comments
Volatility: 2.2 is Coming Soon
Volatility 2.2 RC1 is available and supports Linux images
The good folks in the Volatilty/Memory Analysis community have been pretty busy lately. Release candidate for version 2.2 has been recently published (http://code.google.com/p/volatility/downloads/list) which adds support for Linux and adds plugins addressing the Windows GUI. There is also a plugin that will pull the event logs from memory for XP and 2003. Take a moment to read through the release notes for 2.2 RC1: http://code.google.com/p/volatility/wiki/Release22
Month of Volatility Plugins
Last week, the Volatility Labs Blog started a Month of Volatility plugin series, to introduce the new features becoming available in 2.2 (http://volatility-labs.blogspot.com/2012/09/month-of-volatility-plugins-movp.html) Final release for 2.2 should be available in October.
Using Volatilty in the Workplace
I've employed volatility in a couple different ways in the workplace. Gathering a memory snapshot was added to our malware response process, so adding a few default volatility jobs to the analysis procedure made sense.
In other instances, it was used in an ad hoc fashion, depending on the particulars of the case. When used in this manner, I would install volatlity in with the case file itself, and scripts were used to create any volatility output that was later used in the write-up. While this was a waste of disk-space, it allowed for others to reproduce my work, and this was in the early days of Volatility where updates might break plugins that I'd used in a case. Now we're moving towards using a VM for each case so that the entire too-lset used in the investigation is
maintained.
Dealing with Upgrades
In both methods, I'm still faced with how to deal with updates to the tool. In the former I run the risk of breaking the process. In the latter, it's not as big of a deal, since I would install the latest whenever a case was started. It may be a good idea to keep a couple of versions of volatility installed due to plugin dependencies.
When a particular finding is crucial in a case, it makes sense to verify that finding using different tools. Compare your volatilty results with those from say, Mandiant's redline or memoryze, or whatever commercial memory analysis tool you enjoy.
You should also follow a similar process with new versions of plugins. Test the new version on an old case's memory image (or compare using some of the example memory captures here: http://code.google.com/p/volatility/wiki/PublicMemoryImages)
0 Comments
Script kiddie scavenging with Shellbot.S
3 Comments
What's on your iPad?
In a recent story (see the bottom of this article), there's been some discussion about a prominent NMS (Network Management System) with an iPad interface that uses a simple to duplicate algorithm for it's password.
Do we care? Isn't the resulting password more secure than most passwords we ourselves would have picked? Not so much if it's simple to derive, but in my opinion, the real story here is that we are trusting our mobile devices and apps way more than we should. We buy low cost or free simple apps to do things that really matter, without checking doing our homework on security. In this case, the app is using cleartext authentication and xmpp (the jabber protocol) to remotely access and control their NMS. The "password math" doesn't help either. The NMS in turn has access to the full device configurations, as well as the ability to send email directly to network admins (great spearphishing target!), and most importantly, in many cases has admin access to all the network routers, switches, firewalls and even servers.
People just as blithely (blindly?) use tablets and phones to access their bank accounts and control their cars (what could go wrong with that?)
In the case of an NMS I can certainly see the attraction, now that tablet screens are just as good as many laptops, running your NMS from a tablet can be much easier from a tablet than a traditional laptop - especially if you're not at work.
I gotta admit that it still bothers me when I see the bank adds on TV, encouraging people to access their bank accounts using their phone (you know, the one without a screensaver or keyboard lock) - you know, so that their bank account is even *less* protected when the phone is stolen.
Mind you, some folks would likely be more upset if their social media accounts could be accessed this way ... umm, wait a second! A favourite highschool prank is to steal a phone from your classmate for 10 minutes to put a bogus (and embarassing) facebook or twitter post up.
When did we stop using VPNs - the classic solution to encapsulating and encrypting sensitive traffic? The VPN that encrypts both the data, the destination IP address and the authentication?
My worry here isn't really that the datastream could be MITM'd to steal credentials or hijack sessions, though that's certainly possible in this case. The worry should really be that if your phone or tablet is stolen, big parts of our modern life go with it - banks accounts, facebook and twitter, ebay, your car keys. And in this case control of your network. If all we protect this stuff with is a simple keyboard password (my 11 yr old shoulder surfed mine - https://isc.sans.edu/diary.html?storyid=13084), then if your phone is lost, all is lost - you BETTER have a remote wipe function ready to go!
More here:
http://www.h-online.com/security/news/item/WhatsApp-takes-the-lazy-route-to-authentication-1703628.html
http://www.h-online.com/security/news/item/WhatsApp-allegedly-creates-overly-simple-passwords-under-iOS-too-1704972.html
===============
Rob VandenBrink
Metafore
6 Comments
IE Zero Day is "For Real"
We've had numerous readers write in about an IE8 zero day, most pointed us here for more info on it ==> http://eromang.zataz.com/2012/09/16/zero-day-season-is-really-not-over-yet/
Since I'm not a "Malware Analysis Guy" (at least until I take Lenny's Forensics 610 class), I hunted around for some confirmation before I posted.
I guess a Metasploit module that exploits it counts as confirmation !
http://dev.metasploit.com/redmine/projects/framework/repository/revisions/aac41e91fd38f99238971892d61ead4cfbedabb4/entry/modules/exploits/windows/browser/ie_execcommand_uaf.rb
Also more info here: http://blog.vulnhunt.com/index.php/2012/09/17/ie-execcommand-fuction-use-after-free-vulnerability-0day
And yes, there is code in the wild that exploits this (since Sept14th). And no, there is no patch for it yet
If you're still running IE7,8 or 9, today is a good day to think about switching browsers for a couple of weeks.
(thanks to our readers, who corrected my original post - this zero day affects not just IE8, but also IE7 and IE9)
===============
Rob VandenBrink
Metafore
15 Comments
ISC Feature of the Week: Privacy Policy
Overview
There have been a lot of data leaks of email, password, credit card information and more lately. I wanted to take a moment and remind everyone about the Internet Storm Center's and the SANS Institute's commitment to protecting private information as outlined in our ISC/DShield Privacy Policy at https://isc.sans.edu/privacy.html.
Additionally, any source information in DShield submissions as well as any other project such as the 404project are anonymised in public reports.
Features
I'll give a brief summary here and you can follow the links for complete details.
First line is Last Updated date so you'll know immediately if there are any current changes.
1. How We Gather Information - https://isc.sans.edu/privacy.html#1
The ISC Portal system saves your information and references it to your email address and password.
2. Log Files - https://isc.sans.edu/privacy.html#2
Web logs are stored and used to analyze trends, to administer the site, to track how visitors interact with the site.
3. Cookies - https://isc.sans.edu/privacy.html#3
ISC may use both session ID cookies and persistent cookies. We use session cookies to make it easier for you to navigate our site. You can remove your ISC Portal login cookie by clicking the "Logout" link.
4. How We Protect Your Personal Information - https://isc.sans.edu/privacy.html#4
ISC safeguards the security of the data you send us with physical, electronic, and managerial procedures. The ISC website uses SSL v3 and TLS v1 encryption on all web pages where personal information is submitted.
5. Access To Your Personal Information - https://isc.sans.edu/privacy.html#5
To review and update your personal contact information, simply click https://isc.sans.edu/login.html and log in with your email address and password, then click My Information.
6. Notifications and Promotional Email - https://isc.sans.edu/privacy.html#6
You are free to opt-in and/or opt-out of any notification or email.
7. Links To Other Sites - https://isc.sans.edu/privacy.html#7
The ISC web site contains links to other sites that are not owned or controlled by ISC. Please be aware that the ISC is not responsible for the privacy practices of such other sites.
8. Affiliates And Subsidiaries - https://isc.sans.edu/privacy.html#8
DShield.org provides Google Ads and uses Google Analytics in certain areas of the site.
9. Information Obtained From Third Parties - https://isc.sans.edu/privacy.html#9
ISC does not sell or trade your personal information. We may at times receive contact lists from other organizations. We may send mailings such as brochures to these addresses.
10. Changes To This Privacy Statement - https://isc.sans.edu/privacy.html#10
If we decide to change our privacy policy, we will post those changes to this privacy statement, the homepage, and other places we deem appropriate so that you are aware of what information we collect, how we use it, and under what circumstances, if any, we disclose it.
11. Contact Us - https://isc.sans.edu/privacy.html#11
If you have any questions or suggestions regarding our privacy policy, please contact us at handlers@sans.edu.
Post suggestions or comments in the section below or send us any questions or comments in the contact form on https://isc.sans.edu/contact.html#contact-form
--
Adam Swanger, Web Developer (GWEB, GWAPT)
Internet Storm Center https://isc.sans.edu
1 Comments
Scam Report - Fake Voice Mail Email Notification Redirects to Malicious Site
We received a report of a recent scam that persuaded the victim to click on a link that claimed to be a recorded voice mail message. (Thanks for the pointer, Sean Thomas.)
According to VCU, the scammer's message had the following contents:
Subject: Voice Mail from 703-892-1228 (55 seconds)
You received a voice mail : N_V50-062-NIDS.WAV (182 KB)
Caller-Id: 703-892-1228
Message-Id: 458AH-PEL-02UEU
Email-Id: voice.mail@vcu.edu
This e-mail contains a voice message.
Double click on the link to listen the message.
Sent by Microsoft Exchange Server
Better Business Bureau published a screenshot of a similar message. According to BBB, although the "attachment appears to be a .wav audio file, but it’s really an HTML link that redirects recipients to a malicious website."
As far as we can tell, there is no email attachment in this attack; the message claims to contain a WAV file, but merely includes a link that claims to allow the victim to play that "voice mail."
XtremeComputer.com examined one instance of this attack, stating that the link directed the recipient to "hxxp: //tweetsbazaar.com /5ACeRRyc /index.html" or "hxxp: //www.luckylu.de / EuaWg3cd / index.html". The victim's browser was then presented with a malicious Java applet "Gam.jar" and was further redirect to a URL at 173. 255. 221.74.
The Jsunpack website captured contents of one instance of the exploit being delivered via Gam.jar from 173.255.221.74, which (not surprisingly) contained the malicious Java applet and obfuscated JavaScript. This looks like an instance of the Blackhole Exploit Kit.
If you have additional details regarding this scam and the associated client-side attack, please let us know or leave a comment.
-- Lenny Zeltser
Lenny Zeltser focuses on safeguarding customers' IT operations at NCR Corp. He also teaches how to analyze malware at SANS Institute. Lenny is active on Twitter and Google+. He also writes a security blog.
4 Comments
Analyzing Malicious RTF Files Using OfficeMalScanner's RTFScan
Attackers have been using Rich Text Format (RTF) files to carry exploits targeting vulnerabilities in Microsoft Office and other products. We documented one such incident in June 2009 ("details.rtf"). In a more recent example, the CVE-2012-0158 vulnerability was present in Active X controls within MSCOMCTL.OCX, which could be activated using Microsoft Office and other applications. McAfee described one such exploit, which appeared in the wild in April 2012:
"In the malicious RTF, a vulnerable OLE file is embedded with \object and \objocx tags. ... Upon opening a crafted file with the vulnerable application, as in other document exploit files, we see an innocent file posing as bait, while in the background, the Trojan files are installed."
How might you analyze a suspicious RTF file, perhaps delivered to you or your users as an email attachment? RTFScan, now available as part of Frank Boldewin's OfficeMalScanner toolkit, can examine RTF files and assist in extracting embedded artifacts.
Consider the "details.rtf" file, which contained an embedded PE executable without any obfuscation. In an earlier diary we demonstrated a technique for extracting the PE executable from this file with the help of sed, Perl, hexdump and dd. RTFScan makes the task easier:
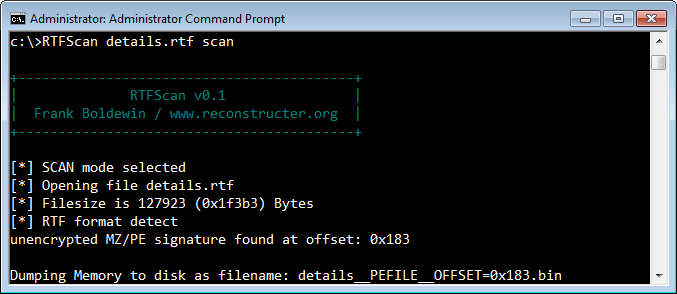
RTFScan automatically located the embedded PE file and extracted it.
Consider the more sophisticated example that took advantage of the CVE-2012-0158 vulnerability mentioned above. In one such incident, a file named "6TH WPCT Action Plan from Environment Group.doc" was delivered to victims by email as part of a targeted attack. Though the file ends with the .doc extension, it is actually an RTF file. RTFScan can scan it and identify malicious artifacts:
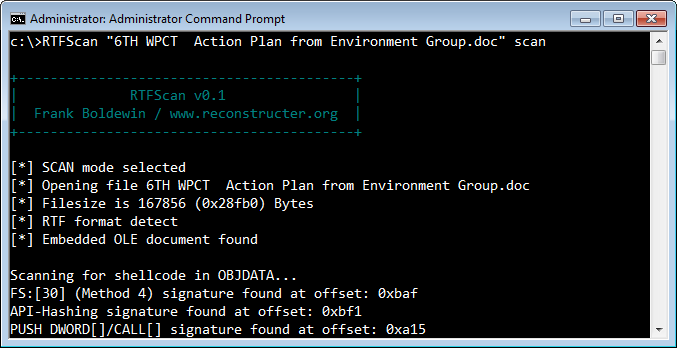
In this case, the malicious executable wasn't directly stored within the RTF file. Instead, the RTF file embedded an OLE object that included the attacker's shellcode. A vulnerable version of Microsoft Word could be tricked into executing the shellcode, which deobfuscated and extracted the malicious PE executable hidden within it.
RTFScan located the embedded OLE object and extracted it. Moreover, it scanned the OLE object for the patterns commonly included in shellcode, such as "FS:[30]" (looking for PEB), API hashing and others. At this point, you could use another tool in the OfficeMalScanner toolkit, called MalHost-Setup, to extract the shellcode and debug it to better understand its functionality. (If you're wondering what the executable embedded into this sample does, see an overview by Byt0r.)
If this is interesting to you, take a look at the article How Malicious Code Can Run in Microsoft Office Documents.
-- Lenny Zeltser
Lenny Zeltser focuses on safeguarding customers' IT operations at NCR Corp. He also teaches how to analyze malware at SANS Institute. Lenny is active on Twitter and Google+. He also writes a security blog.
4 Comments
More SSL trouble
Researchers Juliano Rizzo and Thai Duong will present a new tool called "CRIME" at the upcoming Ekoparty 2012 conference in 5 days. Their tool takes advantage of a flaw in the SPDY (speedy) TLS compression protocol implementation. It allows an attacker to hijack an encrypted SSL session. It appears that for this attack to work both the website and the browser must support the SPDY protocol. Several widely used websites such as Google, Gmail and Twitter do support the SPDY protocol. Both the Firefox and Chrome browsers also support this protocol. Internet Explorer and Safari does not support SPDY and are not vulnerable.
It is recommended that you disable the use of the SPDY protocol on your HTTPS websites until the problem is addressed.
References:
http://security.stackexchange.com/questions/19911/crime-how-to-beat-the-beast-successor
http://arstechnica.com/security/2012/09/crime-hijacks-https-sessions/
Join me in San Antonio Texas November 27th for SANS 504 Hacker Techniques, Exploits and Incident Response! Register Today!!
Mark Baggett
Twitter: @MarkBaggett
2 Comments
Microsoft disrupts traffic associated with the Nitol botnet
There is an interesting article that was just published by Microsoft's Digital Crimes Unit. Attackers have been infecting manufacturer supply chains to spread their evil warez. Some unnamed manufacturers have been selling products loaded with "counterfeit versions of Windows software embedded with harmful malware." The article goes on to say that the "Malware allows criminals to steal a person’s personal information to access and abuse their online services, including e-mail, social networking accounts and online bank accounts. Examples of this abuse include malware sending fake e-mails and social media posts to a victim’s family, friends and co-workers to scam them out of money, sell them dangerous counterfeit drugs, and infect their computers with malware." Microsoft worked with law enforcement and began filtering traffic associated with the domain 3322.org to disrupt the botnet's communications.
The full story is here: http://blogs.technet.com/b/microsoft_blog/archive/2012/09/13/microsoft-disrupts-the-emerging-nitol-botnet-being-spread-through-an-unsecure-supply-chain.aspx
Join me in San Antonio Texas November 27th for SANS 504 Hacker Techniques, Exploits and Incident Response! Register Today!!
Mark Baggett
Twitter: @MarkBaggett
1 Comments
TCP Fuzzing with Scapy
Greetings ISC Readers! Today I wanted to share a technique that I find quite useful when I fuzz TCP applications with scapy. Scapy is a Python module used for packet parsing and packet crafting. With scapy you can create just about any packet your heart desires, transmit it to a target, capture the response and respond again accordingly. It is an excellent tool to use for fuzzing network protocols. But it does require a bit of work when fuzzing TCP protocols because you need to track the sequence and acknowledgement numbers. There are countless examples of this on the internet, but let's look at it here briefly. To establish a three way handshake you could do the following.
First you start Python, import scapy and craft your SYN packet.
# python
>>> from scapy.all import *
>>> tcp_syn=IP(src="192.168.1.1", dst="10.1.1.1")/TCP(dport=9000, flags="S", seq=10000)
Then we transmit our SYN packet and capture the SYN/ACK from the remote host.
>>> tcp_syn_ack=srp1(tcp_syn)
Now you can calculate the final ACK and transmit it.
>>> tcp_ack=IP(src="192.168.1.1", dst="10.1.1.1")/TCP(dport=9000, flags="A", seq=tcp_syn_ack.ack, ack=tcp_syn_ack.syn+1)
>>> tcp_pack1=srp1(tcp_ack)
Then you can transmit your crafted packet to the remote listener as long as you calculate and send the correct sequence numbers. There are a couple of downsides to this technique. First, you have to track the sequence numbers and acknowledgement numbers yourself and increment them as you transmit data. Second, because these are crafted packet, the real TCP stack on your host will send RESETS to the unexpected responses. You have to add some IPTABLES rules to block these RESETS from the real TCP stack. There is another way to do this that can help with these problems.
If you just want to shoot your packets at a TCP target, tracking sequence and acknowledgement numbers isn't necessary. Instead you can use Python sockets to establish the connection, then convert the existing socket to a scapy stream. Once it is a scapy stream you can use all of the normal scapy methods to transmit crafted packets over the established socket. Using this method you don't have to track the TCP sequence numbers and can focus on creating and transmitting your fuzzing packets.
Here is an example. We start the same way and importing scapy. Then we establish a normal Python Socket connection like this:
>>> from scapy.all import *
>>> mysocket=socket.socket()
>>> mysocket.connect(("10.1.1.1",9000))
With one simple call to "connect()" the TCP Handshake is completed. But this is just a normal Python socket object. To use it in scapy you need to create a "StreamSocket()" object that is based on the established socket. You can create a StreamSocket object like this:
>>> mystream=StreamSocket(mysocket)
The resulting "mystream" object is a scapy object that can be used to transmit crafted packets across the existing socket. The mystream object supports the same .recv(), .send(), .sr(), .sr1() and even the sniff() methods that you have with other scapy objects. Now all you have to do is craft a packet and send it to your target.
>>> ascapypacket=IP(dst="10.1.1.1")/TCP(dport=9000)/fuzz(Raw())
>>> mystream.send(ascapypacket)
1109
>>> mystream.send(ascapypacket)
1091
>>>
That is all there is to it. I hope you find this technique as useful as I do for fuzzing TCP services. Do you have another technique or another way to apply this technique? Leave a comment.
Join me in San Antonio Texas November 27th for SANS 504 Hacker Techniques, Exploits and Incident Response! Register Today!!
Mark Baggett
Twitter: @MarkBaggett
2 Comments
Microsoft September 2012 Black Tuesday Update - Overview
Overview of the September 2012 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS12-061 | XSS in Visual Studio Team Foundation Server | |||||
| Visual Studio CVE-2012-1892 |
KB 2719584 | No. | Severity:Important Exploitability: 1 |
N/A | important | |
| MS12-062 | System Center Configuration Manager (SCCM) Elevation of Privileges via Cross Site Scripting | |||||
| SCCM CVE-2012-2536 |
KB 2741528 | No. | Severity:Important Exploitability: 1 |
N/A | important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): The exploitability rating we show is the worst of them all due to the too large number of ratings Microsoft assigns to some of the patches.
--
Adam Swanger, Web Developer (GWEB, GWAPT)
Internet Storm Center https://isc.sans.edu
2 Comments
Godaddy DDoS Attack
Godaddy is currently experiencing a massive DDoS attack. As of this writing, the main GoDaddy Website is not reachable. There are reports of outages of GoDaddy hosted e-mail as well as hosted website. We will update this as we learn more.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
17 Comments
Microsoft Patch Tuesday Pre-Release
We only expect two bulletins from Microsoft tomorrow [1]. Both bulletins are rated important. The first one affects Microsoft Visual Studio Team Foundation Server 2010 Service Pack 1, and the second one affects Microsoft Systems Management Server 2003 Service Pack 3 as well as Microsoft System Center Configuration Manager 2007 Service Pack 2.
While these are popular software packages, they are far less popular then some of the usual suspects (Office, Windows, Internet Explorer). In part, the low number of bulletins appears to be intentional, to not distract from the more complex issue which will affect Windows users starting with the October update set: Windows will no longer allow SSL certificates with RSA keys that are less then 1024 bits in length. The update is already available to allow for testing, but in October, it will be pushed as a patch.
The reason Microsoft is so careful with this update is that it will not just effect certificates issues by Microsoft and other well known certificate authorities, but it will also affect internal certificates. For example if you are using an internal certificate authority, and created certificates with insufficient key sizes to sign e-mail messages via S/MIME, these certificates will no longer work after you applied the update [3].
As a first step, you should install the patch on a test system, and watch for any problems. You should also carefully inventory your certificates, in particular if you are using non-standard (internal) certificate authorities. As you are recreating new certificates, DO NOT create 1024 bit RSA keys. Windows will still accept them, but 1024 bits is an absolute minimum size, and not necessarily sufficient. 2048 or 4096 bits is the size you should try to use.
[1] http://technet.microsoft.com/en-us/security/bulletin/ms12-sep
[2] http://technet.microsoft.com/en-us/security/advisory/2661254
[3] http://support.microsoft.com/kb/2661254
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
Phishing/Spam Pretending to be from BBB
We received another piece of spam (thanks Curtis) pretending to be from the Better Business Bureau. Analysis of the file transferred (W6w8sCyj.exe) from prog.it appears to be a piece of malware (Win32/Cridex.Q) use to communicates via SSL with a C&C server.
List of domains/IP to watch for and block:
ajaxworkspace.com
prog.it
la-liga.ro
ejbsa.com.ar
technerds.ca
108.178.59.12
The email looks like this:
Better Business Bureau©
Start With Trust©
Sat, 08 Sep 2012 01:54:02 +0700
RE: Case # 78321602 <http[:]//prog.it/EH564Bf/index.html>
Dear Sirs,
The Better Business Bureau has got the above mentioned complaint from one of your customers concerning their business relations with you. The details of the consumer's concern are contained in attached document. Please give attention to this case and advise us of your opinion as soon as possible. We encourage you to open the COMPLAINT REPORT to answer on this complaint.
We look forward to your prompt response.
Faithfully yours,
Ann Hegley
Dispute Counselor
Better Business Bureau
________________________________
[1] http://anubis.iseclab.org/?action=result&task_id=15e0c40724f468154b9b07dba8a34bfa4&format=html
[2] http://wepawet.iseclab.org/view.php?hash=b4817d858b4e1862c8a828c85be365b1&t=1347109082&type=js
[3] http://wepawet.iseclab.org/view.php?hash=06ea2fd5b8931844981d7c718ea89060&t=1347109182&type=js
[4] http://wepawet.iseclab.org/view.php?hash=7d629a7fea394ce0be5782de592d8f68&t=1347109422&type=js
[5] https://www.virustotal.com/file/126ea9ed6828a1eaa37250aa015a9f8518fdb54c8175ce87559a68eac47b9187/analysis/
[6] http://www.microsoft.com/security/portal/Threat/Encyclopedia/Entry.aspx?Name=Win32%2fCridex
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
1 Comments
Webmin Input Validation Vulnerabilities
If you are using Webmin within your network to administer Unix services, you should consider upgrading to the latest version 1.590 (include 2 patches) because an input validation vulnerabilities has been reported in version prior to and including 1.580. The latest version can be downloaded here or the update can be done directly in Webmin (Via menu Webmin, Webmin Configuration and Upgrade Webmin).
CVE-2012-2981 - Improper Input Validation
CVE-2012-2982 - Improper Neutralization of Special Elements used in a Command
CVE-2012-2983 - Improper Limitation of a Pathname to a Restricted Directory
[1] http://www.kb.cert.org/vuls/id/788478
[2] http://www.webmin.com/download.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
2 Comments
Keeping an eye on those BYODs with DHCP
A plethora of technologies, bespoke systems and acronyms offer management offer protection against unauthorised devices being connected to networks, but money, time, effort and management backing is needed to make this a reality. Imagine company X's policy is only authorized, company-approved computers can be connected and all violations have to be logged and reported or the auditors will be very unhappy. And no-one like to see sad auditors. But there’s no budget. So what’s a poor security admin to do? Well here's a suggestion.
Dynamic Host Configuration Protocol (DHCP) ubiquitous to most networks, making connectivity to the network only an Ethernet cable away*. For those with an eye on security, DHCP logs are a gold mine.
On gaining a DHCP lease the IP address assigned to the system and that IP address, the expiry time, the system’s hostname and Media Access Control address (MAC address) get stored in the DHCP database. So let’s look a couple of ways to turn these pieces of data in to security gold, remember our goal is to detect and alert on non-company approved systems being plugged in to the network.
The first step is to get access and a copy of the DHCP logs (or direct access to the DHCP database), so the data can be parsed and sorted into a format that can be dropped in to a script to automate the detection process. Most company networks are hopefully built using decent naming conventions and using only a couple of vendor’s computing hardware. This means by using some simple scripting, detecting those anomalies to the company standards should be a breeze. To clarify this:
System hostnames:
Companies tend to have a naming standard for their machines to make inventories, auditing and identifying manageable. Some example machines names: a00001, XYZ1234 and so on. Hostnames of JamesMegaLappy, SkyRocket and haz0r don’t fit that naming standard and a basic regular expression [1] check against the naming standard will be able to pick this up instantly.
MAC address:
IEEE assigns an Organizationally Unique Identifier (OUI) [2] to each company manufacturing Ethernet devices. The company must use its own OUI [3] for the first three bytes of MAC addresses for equipment it produces. For example, the OUI of MAC address 00:06:5B:32:12:A0 is 00065B. For this example, company X uses two brands of computer hardware OIDs 00065B and 0001E6. A scripted task can run through the DHCP logs to pick out any MAC addresses that don’t start with these OIDs.A script running hourly against the
A script reading DHCP logs detecting either a non-standard hostname or OID and sending an email alert is quick, easy to implement and an effective detection method to find those non-company approved systems. Using the expiry time entry to confirm when the device got its IP address, it provides a time frame of someone adding a device to the network, so local staff looking for the unauthorized system have a starting point to ask questions.
This isn’t fool proof as it is trivial to change both the hostname and MAC address to blend in, but it’s highly effective against the majority of devices being plugged in to networks by those uncomprehending of the company’s polices or those acting maliciously.
For those who like to take the offensive defence approach on their networks against policy violations, the offending MAC address can be added as a DHCP reservation with DHCP scope options that point the default gateway and DNS server to, say 127.0.01. This is limits what the offending device can connect to the next time it renews it DHCP lease or requests a new IP address.
Join Ashley Deuble for MGT 414: SANS® +S™ Training Program for the CISSP® Certification Exam in Brisbane, Australia
* DHCP leases can be offered to wirelessly as well but that would have broken my flow.
[1] http://en.wikipedia.org/wiki/Regular_expression
[2] http://standards.ieee.org/faqs/regauth.html
[3] http://standards.ieee.org/develop/regauth/oui/oui.txt
Chris Mohan --- Internet Storm Center Handler on Duty
4 Comments
SSL Requests sent to port 80 (request for help/input)
A while ago, a reader submitted some odd looking web log entries like the following:
default 10.5.0.48 - - [06/Sep/2012:23:11:36 +0000] "\x16\x03" 200 15 "-" "-"
default 10.5.0.48 - - [06/Sep/2012:23:12:26 +0000] "\x16\x03" 200 15 "-" "-"
After some experimenting, we figured out that these are SSL connection attempts that are directed at a non-SSL server. These log entries are common if your web server is misconfigured, and the SSL module is not enabled on port 443. But in this case, the log entries showed up on a web server listening on port 80.
To "force" an https request on port 80, you have to add the port explicitly to the URL. For example the log entries above, I created using the command:
wget https://webserver:80/index.html
The bytes "\x16\x03" are the first two payload bytes transmitted for the connection (a \x00 is the third byte, which terminates the string as far as the server is concerned). The server may actually still respond with a default error page. The server I used was configured to respond with a "200" code for any request (to make URL brute forcing harder).
The Wireshark analysis of course doesn't make much sense here:
However, luckily we can use Wireshark's "decode as" feature to make more sense of the packet. If we ask Wireshark to decode this traffic as SSL, we do get a perfectly fine Client Hello packet:
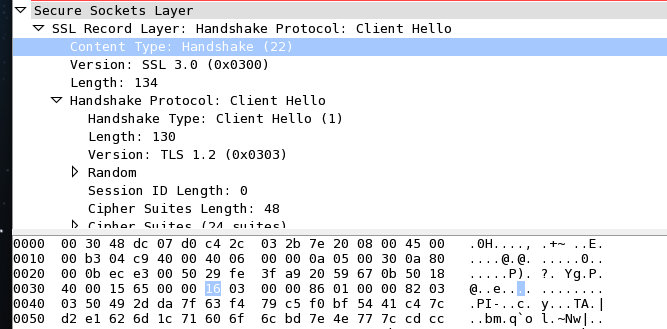
The "0x16" byte indicates that this is a "Handshake" and the "0x03" tells us that we are dealing with SSL 3.0. So now we can do a bit fingerprinting on these requests.
Here is a sample from today's ISC log:
\t\xe2)\x18\x12\xbc\xcc\x04U\xbf\xddj\xc4\xf9q\x163\xa0\x90
\xc4]\xd6\x1cg\x90\xc1\xf2\xe9\x9a\x1e\xba\v\xca2N\x92\x1a\xd0
\xb2\xf28i\xe5{A\x16`\xc2\x01\xa1\x84\xd4_\xfe%\x93\x92\xf8\xb1
\xb7\x85\x15\x05\xdc\xae\xde\x9d\xbb'\x05\x8e\x11\x17\xb9\xdf\xee|%\xd19\xf3\x9b\xeb
\xb9\xa4\x03{\xea\x88\xf4\x88\x87\xfb\x17\xc5\x07\x9c\xc5{\xaa?{\xc7]v\xcf
\x04c\x98\xbf\x87+in
\x83\x91w\xe2\x13\x85\xae,qs\xdb\xbe\xd78\xa4\xed\xbf\
\xd2\xa2 *\xcaUV\xd7\x0e\xab\xaa\x91A\x13\xf7E\xaf\x01\xc1\x9e\xbf\xd3
\x99\xd2\xad\x1b5\xcc\x85\xef\xaa\r:9\xdc>p\xdf\xfb\xb8\xb6\xd1Pj4\x04\xb1\
\x1f\xe4\xbet\xec\x0c\xcc>\xf3\
Avg\xdc\x94\xd5\xd9\bO\x18y+\xcd\xb0
\xd1\xaf\x855\xeb\xb4\x19/3\xa8\xab\x15ZNZU9>=\x0e\x87\xb8\xa0\xe2\x12
\x16\x03
\x16\x03
(I shortened some lines a bit to avoid page width problems)
Based on our analysis above, on the last two appear to be SSL requests. The others, appear to be "something else". Can you identify them? Telnet doesn't cause any additional characters to show in the log (I suspected telnet's terminal negotiation, but was not able to trigger the characters ). Have you seen similar entries in your logs? Haven't seen anything with SSH either. The SSH client first waits for the "banner" from the server before sending anything (I may have to wait longer).
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
Auditing a Network for VOIP Call Quality Metrics
What I'm seeing in the security field is a focus on vulnerabilties and exploits, in short - the "cool stuff". And in "real life", we see a much stronger focus on operations and cost.
But what we rarely see is a focus on Audit. Where Audit differs from the day-to-day round of penetration tests, log review and like is that an audit compares a configuration or a set of parameters to a known standard for yes/no or exceed/deficient compliance.
In this diary, I'll do a short description of auditing a WAN link for metrics key to VOIP (Voice over IP) call quality. Just a short proviso - this is not a complete guide to VOIP call quality or auditing for VOIP metrics, it's meant as a starting point which you can take to your own environment and tailor to your own needs and toolset.
So, why would you want to audit a WAN link for VOIP call quality metrics?
1/ To assess if your edge routers are properly re-marking TOS or DSCP bits in the right packets, for delivery to the wAN (commonly done with PBR, Policy Based Routing)
2/ To assess if your WAN provider is honoring your QOS settings, and delivering the appropriate QOS to your various types of traffic
I'll assume that there's at least one Cisco device at each end of the WAN link we're assessing (the commands described are available on IOS switches and routers), but the functions I'm describing are certainly available in most of the other name-brand network platforms.
So first of all, what will we audit in this setup?
Delay - how long does it take a packet to make a round-trip from one end to the other?
Jitter - how much does Delay change during any given call? (zero would be ideal)
MOS (Mean Opinion Scores) - a mathematical distillation of overall call quality to a single value, with 5 being perfect fidelity.
Let's look at the configuration. On the core router, we'll create an IP SLA setup to send test packets to IP SLA Responders at the remote sites. These commands create a simulate actual VOIP traffic and reports on the results. Again, these are Cisco commands (routers or switches), but have analagous functions in other network platforms.
ip sla 1
udp-jitter 192.168.4.249 5001 codec g711alaw codec-numpackets 100 advantage-factor 10
tos 160
timeout 10000
threshold 10000
history enhanced interval 3600 buckets 12
ip sla schedule 1 life forever start-time now
snmp-server community somestring RO ACL_SNMP
access-list standard ACL_SNMP
permit ip snmp.monitor.host.1
permit ip snmp.monitor.host.2
What this does is:
- Simulates a voice conversation of 100 packets, with a TOS (Type of Service) setting of 160.
- The conversation is repeated every 60 seconds (the default), and statistics are kept for 1 hour.
- The "ip sla schedule" line does exactly what it looks like - starts the process with no end time. The snmp-server setup allows us to monitor the statistics using our Network Managemnt System (or the CLI which we'll get to).
Next, at the remote end we'll set up a responder, which responds to the request packets from the core. Basically it takes the UDP packet and sends it back where it came from. Note that the listener port of the responder (5001) has to match the target port in the SLA config on the core router (above)
ip sla responder
ip sla responder udp-echo port 5001
Now, to monitor this we'll use simple SNMP queries. The OIDs (Object IDs) to monitor for Cisco devices are documented at:
http://tools.cisco.com/Support/SNMP/do/BrowseOID.do?local=en&translate=Translate&objectInput=1.3.6.1.4.1.9.9.42.1.5.2.1.42#oidContent
This is a really handy link if you need an explanation of what any particular OID or group of OIDs is about.
So, to monitor MOS from the command line:
C:\>snmpget 192.168.2.237 1.3.6.1.4.1.9.9.42.1.5.2.1.42.1 -ccomplex.string
SNMP++ Get to 192.168.2.237 SNMPV1 Retries=1 Timeout=100ms Community=complex.string
Oid = 1.3.6.1.4.1.9.9.42.1.5.2.1.42.1
Value = 434
Divide that value by 100, to get an MOS value of 4.34
To get Jitter, we'll query the rttMonLatestJitterOperAvgJitter parameter, which is defined as "The average of positive and negative jitter values in SD and DS direction for latest operation":
C:\>snmpget 192.168.2.237 1.3.6.1.4.1.9.9.42.1.5.2.1.46.1 -ccomplex.string
SNMP++ Get to 192.168.2.237 SNMPV1 Retries=1 Timeout=100ms Community=complex.string
Oid = 1.3.6.1.4.1.9.9.42.1.5.2.1.46.1
Value = 1
And for delay, we'll query the maximum RTT (Round Trip Time) value for the latest conversation:
C:\>snmpget 192.168.2.237 1.3.6.1.4.1.9.9.42.1.5.2.1.5.1 -ccomplex.string
SNMP++ Get to 192.168.2.237 SNMPV1 Retries=1 Timeout=100ms Community=complex.string
Oid = 1.3.6.1.4.1.9.9.42.1.5.2.1.5.1
Value = 4
I would expect that in most cases, you'd plug these OID values into your Network Management System and graph them over time. But in a pinch, you can collect them using a Windows CMD file and graph the values in Excel. The batch file QOS.CMD below creates a once-per-minute CSV file that you can read directly into most spreadsheets:
date /t > qos.tmp
time /t >> qos.tmp
rem round trip delay
snmpget 192.168.2.237 1.3.6.1.4.1.9.9.42.1.5.2.1.5.1 -cerbro | find "Value" >> qos.tmp
rem max jitter on last conversation
snmpget 192.168.2.237 1.3.6.1.4.1.9.9.42.1.5.2.1.46.1 -cerbro | find "Value" >> qos.tmp
rem MOS on last conversation
snmpget 192.168.2.237 1.3.6.1.4.1.9.9.42.1.5.2.1.42.1 -cerbro | find "Value" >> qos.tmp
type qos.tmp | sed "s/Value = //" | tr '\n' ',' | tr -d '\r' >> qos.out
echo. >>qos.out
sleep 60
goto LOOPSTART
I use the GNU utils for my sed and tr, mostly because I can bundle everything up in only a few exe and dll files to run on any version of Windows. But the "Services for Unix" (SFU) that's in Windows these days works great also, and is probably a better way to go in most cases - - that tr weirdness might be better handled with SFU for instance. There are also several "snmpget" utilities floating around, each with slightly different syntax.
To meet our standard for "good quality voice", the target values we are auditing against are:
Delay
When listening to speech, the human ear normally accepts up to about 150 ms of delay without noticing it (discussed in the ITU G.114 standard) Once the delay exceeds 150 ms, a conversation becomes akin to speaking on a walkie-talkie, with weird pauses in the conversation. In high delay environments, people tend to wait for their partner to finish speaking before talking (as on a walkie-talkie)
Jitter
Jitter values should be low, zero is the ideal. Values of over 20-30 ms will degrade voice quality, resulting in choppy sounding conversations or sometimes "echo". Jitter can be compensated for in the end devices (jitter buffers on the phones for instance), or by proper prioritization and queuing of voice traffic. Excessive Jitter can indicate a problem in the queueing and forwarding algorithms on the WAN, exceeding the EF (express forwarding) budget on the WAN, or non-uniform delays imposed by queuing, encapsulation or encryption, or any forwarding operation in the path.
MOS
MOS is a simple, overall measure of call quality. If you graph one statistic for Management, this should be it, with the caption "Greater than 4 is Good". The formal matrix for MOS definitions is:
| MOS |
Quality | Impairment |
| 5 | Excellent | Imperceptible |
| 4 | Good | Perceptible but not annoying |
| 3 | Fair | Slightly annoying |
| 2 | Poor | Annoying |
| 1 | Bad | Very annoying |
I hope this short description helps you in assessing your network for VOIP readiness, or helps in troubleshooting VOIP issues. More importantly, I hope that this emphasizes the importance of Audit (the "A" in SANS) as an important part of your Security matrix.
===============
Rob VandenBrink
Metafore
2 Comments
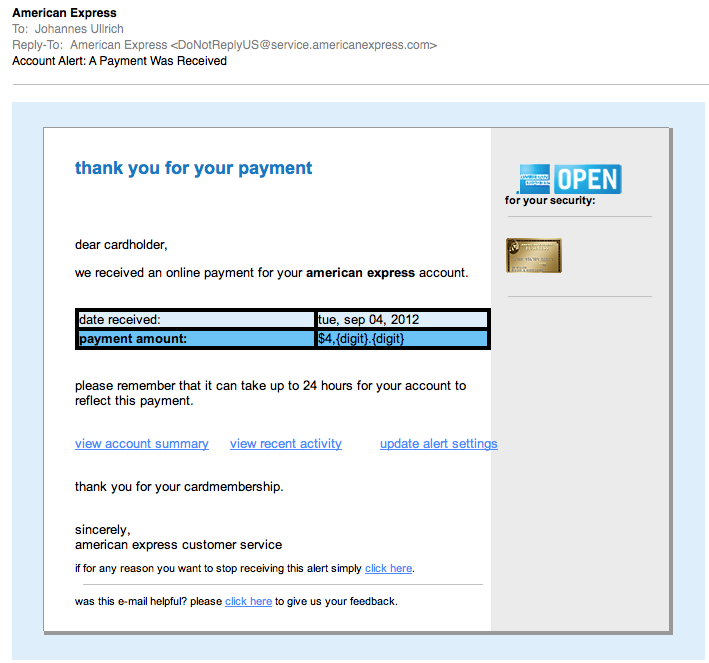
Another round of "Spot the Exploit E-Mail"
We have come to expect quality phishing/fake email work these days. In a recent diary I showed how well one crew impersonated Verizon e-mails to spread malware. So I was a bit disappointed when I got this e-mail this morning:
(click on image to see it full size)
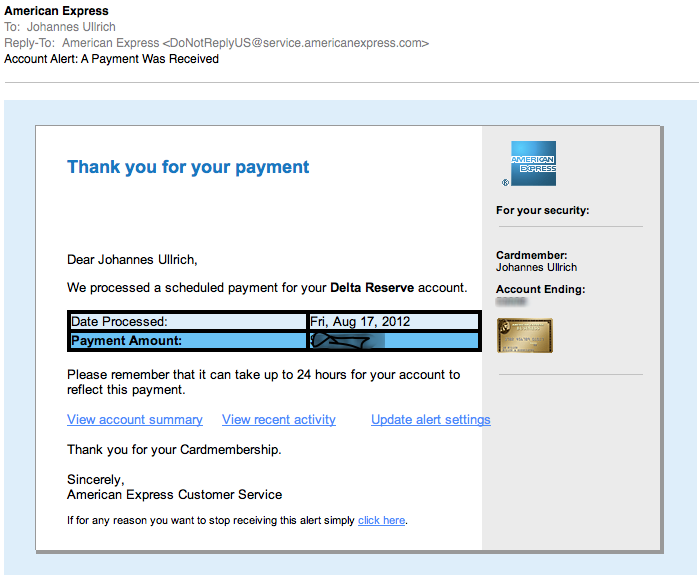
The e-mail has a number of obvious deficiencies. For example, the missing "digits" in the payment amount., and the fact that it is all lower case. But all wasn't lost. Looks like ACME Phishing was hard at work fixing the bugs, and the QA team shortly sent a second email (but to another account of mine):
Finally, a real e-mail from American Express. I blurred the amount and the last few digits of the account number. I also replaced the image of the card. But as you can see, the real e-mail is VERY CLOSE. Probably the most significant difference is that the last digits of the account number are missing at the fake. But I doubt many people look for this.
So what is the fake e-mail trying to do? Imagine that: It will get you malware... In my copies, the initial link goes to hxxp:// vserver94 . antagus . de
That page then includes three javascript files loaded from these domains:
atriumworkcomp.com, mlegion.com , watchdogwebdesign.com . The javascript file name is js.js.
The javascript will then redirect the user to one of these two IP addresses:
96.47.0.163, 108.178.59.26
both IP addresses yield heavily obfuscated javascript. The wepawet analysis can be found here:
http://wepawet.iseclab.org/view.php?hash=3c550bbf81ebfcd7979f2147fb69729c&type=js
It appears to be the usual "what vulnerable plugin are you running today?" javascript.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
8 Comments
Demonstrating the value of your Intrusion Detection Program and Analysts
Bojan's last couple of diaries on Analyzing Network Traffic Part 1 and Part 2, got me to thinking about all the knowledge required as well as the work and effort that intrusion analysts go through to protect the networks they monitor. Often times, this knowledge and skill is gained on off duty hours because this world is more than just a job. So, how do you demonstrate to management the value of your intrusion detection program and your analysts? One of the toughest barriers to breach is taking data from the technical side and presenting it in a meaningful way to the management side. In this specific instance, I wanted to focus on translating to management the value of Intrusion Detection and the analysts. I have heard it said more than once "We have a firewall and IDS, they will alert us when something happens" or "We have a tool that can monitor our network, we don't need all these people do we?" and one of my favorites "We have Antivirus, isn't that enough?" In today's tough economic times, one of the first things that usually gets cut in the budget is security. The tools generally stay in place, but the number of people required to manage and monitor them drops. The goal to to make management know and understand the value of your intrusion detection program so they realize they can't afford to lose the service you provide.
Generally, the role performed by the analysts is usually only brought to light when there is an incident. Day after day goes by without a major issue and the analysts are out of sight and out of mind. That often includes holidays when everyone else is off but the analyst is still working to protect the network. There are many ways that you can bring to light what your analysts are doing. Metrics are always to first thing that comes to mind, but sometimes its difficult to measure what an analyst does in a way that means something to management. There are also many positions on whether these numbers should be tangible or theoretical. I think its more than metrics, but metrics have their place as well. No matter how you approach this, you have to show value added to your company/organization's mission by making sure management understands that your group exists and the role it performs. Here are some thoughts:
- Have a one page newsletter highlighting your group and its accomplishments as well as what its working on. (Does management know that you had a block put in place for a significant threat until a patch was issued which means your network did not suffer any impact?) I have found that management likes to brag about things like this when others are suffering the effects from it. It also makes them appreciate your efforts.
- Highlight each of your analysts and their success by having a "Catch of the Week/month" writeup and include their photo.
- Keep them informed of current and emerging threats (in easy to understand non-technical terms) Alot of times they have no idea such a threat was possible or exists.
- Provide them metrics of the number of alerts that occur during each shift and approximately how long it takes to look at them. This being tracked by the number of analysts on a shift will show the residual, if any, of what did not get looked at in a timely fashion. Management needs to understand the risk and agree that they are willing to accept the risk.
- How many many blocks (firewall, email, web, etc.) were put in place to protect the network? That shows management a proactive stance.
- Keep management informed of the costs being incurred by other companies who have to clean up after being compromised. Do not imply that it won't happen on your network. It will, its just a matter of time. But the cost is much less if early detection occurs. Skilled analysts to key to early detection.
These are just a few ideas and you will have to tailor this to what means something to your management. Solicit their feedback and ask them if there is something more/less they would like to see. Start with something for them to look at, they usually do not know what to ask you for because they don't understand this world. The bottom line is to make sure management knows your team exists and the efforts that your team is putting forth to protect the network. If you have ideas or things that worked for you, please let us know.
6 Comments
Blackhole targeting Java vulnerability via fake Microsoft Services Agreement email phish
Thanks to Susan Bradley for reporting this to ISC.
We're receiving multiple reports of a phishing campaign using the template from a legitimate Microsoft email regarding Important Changes to Microsoft Services Agreement and Communication Preferences.
The legitimate version of this email is specific to a services agreement seen here, per a change to Microsoft services as of 27 AUG.
The evil version of this email will subject victim to a hyperlink that will send them to a Blackhole-compromised website, which will in turn deliver a fresh Zeus variant.
I'll walk you though the full sample set I analyzed. Susan sent us an email including the following header snippet:
Received: from [101.5.162.236] ([101.5.162.236]) by
inbound94.exchangedefender.com (8.13.8/8.13.1) with ESMTP id q7VFDPjO029166
A legitimate header snippet:
Received: from smtpi.msn.com ([65.55.52.232]) by COL0-MC3-F43.Col0.hotmail.com with Microsoft SMTPSVC(6.0.3790.4900)
101.5.162.236 is in China, 65.55.52.232 is Microsoft.
The legitimate email will include a hyperlink for http://email.microsoft.com/Key-9850301.C.DLs15.C.KK.DlNkNK, which points to the above mentioned services agreement.
Obfuscated to protect the innocent: The phishing mail will instead include a hyperlink to the likes of allseasons****.us, radiothat****.com, and likely a plethora of others. I assessed radiothat****.com and was redirected to 209.x.y.14 which is running the very latest Blackhole evil as described on 28 AUG by Websense in this post.
Source code review of the web page served included <applet/code="ndshesa.ndshesf"/archive="Leh.jar"><param/nam=123 name=uid value="N013:011:011:04:037:061:061:047:034:076:074:0102:076:074:047:047:047:074:067:053:061:04:074:04:013:04:075:054:071:034:067:053:034:034:02:065:071:034"/></applet>
The VirusTotal link for Leh.jar is here, and the VirusTotal link for the Zeus variant offered is here.
Recommendations:
- Hover over hyperlinks and ensure they are directing you to legitimate sites before clicking. Be cautious even thereafter.
- Contemplate disabling Java until the next update is released.
- Review email headers if in doubt for messages you receive that seem suspicious.
- Keep your antimalware signatures up to date. While limited at the moment, detection for both the Java exploit and the Zeus variant is increasing.
Ping us with questions or comments, as well as anything you'd like to share regarding similarly received emails from this phishing campaign.
3 Comments




10 Comments