Recommended Reading: Intrusion Detection Using Indicators of Compromise Based on Best Practices and Windows Event Logs
My Twitter feed brought a good paper to my attention, courtesy of Andrew Case @attrc, that is appropriate for your consideration, Storm Center readers.
@Cyber_IR_UK stated that it's the "best paper I've ever read for Intrusion detection with Windows Events!" That might be a bit strong, but it is good, and well worth reading and consideration.
 Here's the abstract:
Here's the abstract:
"Nowadays computer attacks and intrusions have become more common affecting confidentiality, integrity or the availability of computer systems. They are more sophisticated making the job of the information security analysts more complicated, mainly because of the attacking vectors are more robust and complex to identify. One of the main resources that information security people have on their disposition are Indicators of Compromise (IOCs), which allow the identification of potentially malicious activity on a system or network. Usually IOCs are made off virus signatures, IP addresses, URLs or domains and some others elements, which are not sufficient to detect an intrusion or malicious activity on a computer system. The Windows event logs register different activities in a Windows® operating system that are valuable elements in a forensic analysis process. IOCs can be generated using Windows event logs for intrusion detection, improving Incident Response (IR) and forensic analysis processes. This paper presents a procedure to generate IOCs using Windows event logs to achieve a more efficient diagnostic computer system for IR."
You can grab the paper from ThinkMind here: http://www.thinkmind.org/index.php?view=article&articleid=icimp_2016_2_20_30032
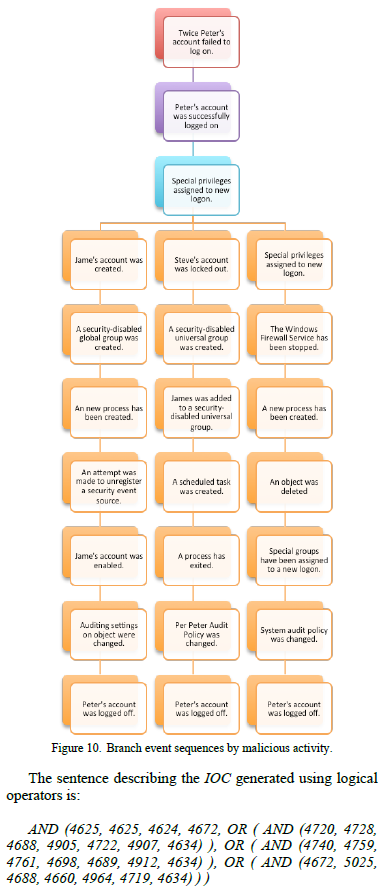
Using IOC Editor and Splunk, the authors asserted a reasonable approach to IOC development with logical operators connecting Event IDs based on kill chain concepts.
I plan to test this approach further, and will advise readers regarding success. Additionally, if you've deployed similar methods with some success, please let us know here via comments. Thanks and cheers.



Comments
Anonymous
Aug 30th 2016
8 years ago
Anonymous
Sep 6th 2016
8 years ago