New Extortion Tricks: Now Including Your Password!
For a while now, we have seen sporadic extortion emails that claim to have a video of you watching pornographic material. The emails usually count on the guilt and shame of the victim to convince them to pay up. However, the bad guys, of course, do not have any evidence of their kompromat, which makes the extortion weak. You would expect them to at least include a frame from the video.
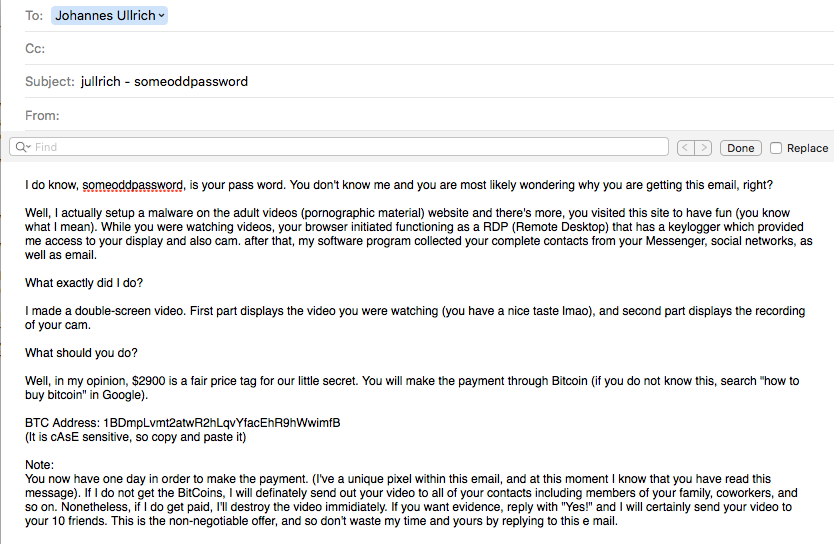
Short of actually producing the video, I just saw another trick used to make the threat more plausible. The e-mail now includes a username and password that you used on *some* website. The bad guys are harvesting leaked account lists, and use them to make their threat more plausible. I include a screenshot of such an email below. "someoddpassword" was a password I used on some sites in the past. Kind of my throw-away password for a while, and I know it leaked in more than one breach.
The emails also include some random text at the end which is typical for spam to evade spam filters. I did not reproduce that part in the screenshot. The copy I received was plain text and did not include any images or other trackers as promised.
Currently, the bitcoin address in this email has not received any ransom payments. It is possible that each email uses a different address. (Update: Brian Krebs and others also received emails like this and wrote about it. Looks like each address is different)
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Jul 12th 2018
7 years ago
Anonymous
Jul 15th 2018
7 years ago
Extortion through guilt/shame is, unfortunately, likely to be effective at least some of the time.
From the bad guy perspective, it is a relatively easy way to get "extra value" out of leaked credentials. It doesn't matter that the victim might have changed all their passwords since the credential loss - if they have an old password floated in front of them, many will not be aware that the claims in the rest of the email are unlikely from a technical perspective, and follow through motivated by guilt/shame.
Anonymous
Jul 15th 2018
7 years ago
This information reveals some things about this campaign
- the BTC addresses are not unique. While I do not have enough information to determine the size of the pool, I have seen two cases of two emails with the same BTC address and the fact that multiple people have paid using the same BTC address confirms that. While anecdotal, since none of the 15 addresses has more than two payments it is possible the addresses were not recycled a large number of times.
- people are paying for this scam. This is not a surprise, but certainly disappointing.
- none of the money has moved out of the BTC addresses, so the bad guys haven't started collecting their ill gotten gains yet.
Anonymous
Jul 15th 2018
7 years ago
Anonymous
Jul 17th 2018
7 years ago
Amount to be sent: 0.8 BTC
BTC ADDRESS: 14DesJvy9NieVDMbeJG4zEtELizzB9jKdG
Anonymous
Jul 30th 2018
7 years ago
Anonymous
Jul 30th 2018
7 years ago
by <> with ESMTP id 4D7A217A5
for <>; Mon, 30 Jul 2018 13:37:57 +0300 (MSK)
Date: Mon, 30 Jul 2018 03:37:57 -0700
$1000
Bitcoin Address: 14oHpqvFLgi7Y4KDDD2ksUvpQFo4q4y8Dj
Anonymous
Jul 31st 2018
7 years ago
Anonymous
Jul 31st 2018
7 years ago
1Laj8VkobMn1BTQvvmUhABbAGf7N7QLTs3
https://bitcoinwhoswho.com/address/1Laj8VkobMn1BTQvvmUhABbAGf7N7QLTs3 - 0 BTC So Far
https://www.reddit.com/r/Scams/comments/90tmo6/scam_they_have_a_password_of_mine/
1GkqvGk6rWTwW1EqJooyZeNjC2T7aDAPHW - The one from the email that made me aware of this scam in the first place.
https://bitcoinwhoswho.com/address/1GkqvGk6rWTwW1EqJooyZeNjC2T7aDAPHW/urlid/12689026 - 0 BTC So far
1QAVaukg4es84us9XRTaPqztYB1XXoXEdA
https://bitcoinwhoswho.com/address/1QAVaukg4es84us9XRTaPqztYB1XXoXEdA/urlid/12655819 - They've got at least someone to bite. 0.77 BTC So far
https://www.reddit.com/r/Scams/comments/908ax4/porn_blackmail_email_with_old_password/
Anonymous
Jul 31st 2018
7 years ago