Malspam pushing Word documents with Hancitor malware
Introduction
I previously wrote a diary on Hancitor back in February 2017. Even though I haven't written a diary about it lately, it's been a near-daily occurrence since then. There's been no significant change, which is why I haven't bothered. Thursday 2017-09-21 included yet another wave of malicious spam (malspam) pushing Hancitor Word documents. Since it's been a while, let's review indicators for this most recent wave.
Hancitor, also known as Chanitor or Tordal, pushed Pony and Vawtrack last year. However, this year it stopped using Vawtrack and now pushes DELoader/ZLoader. The most recent technical write-ups I've seen on Hancitor are here, here, and here.
At least two Twitter accounts routinely tweet indicators for Hancitor malspam like URLs and file hashes. The ones I routinely check are @cheapbyte (example) and @James_inthe_box (example). However, other accounts also tweet Hancitor indicators. You can keep up with this near-daily information by searching Twitter for recent tweets tagged #hancitor.
The emails
Thursday's emails were disguised as yet another invoice, this time spoofing a company named Advanced Maintenance. Advanced Maintenance is a general contract and maintenance "handyman" company with various locations in the US. The emails all spoof a domain name registered by the company's President/CEO named advutah.com. However, these messages are not related to Advanced Maintenance, and they do not actually come from that domain.
Advanced Maintenance is aware of this malspam. If you go to the company's official website, you'll see a warning to ignore these emails.
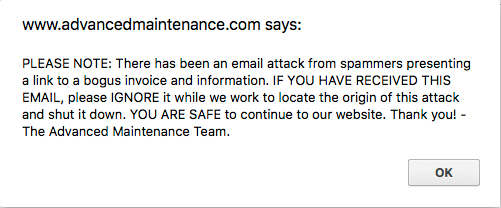
Shown above: Pop-up message from the company's official website.
Links in the email point to various URLs designed to download a malicious Word document. As in previous waves of malspam, the downloaded Word document has macros designed to infect a vulnerable Windows computer, if enabled.
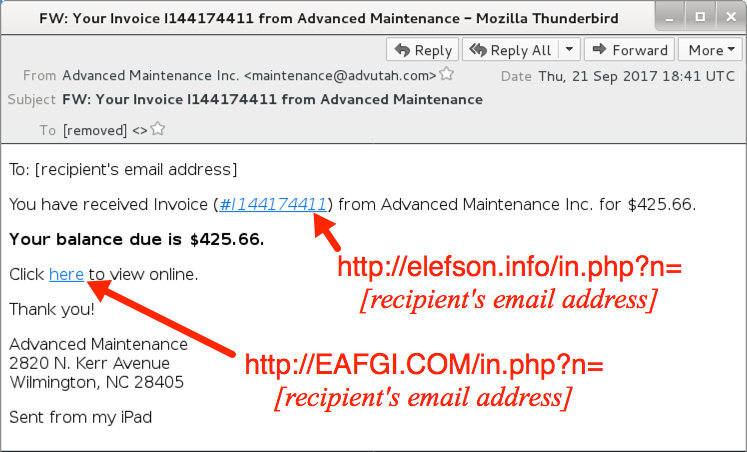
Shown above: Screenshot from one of the emails.
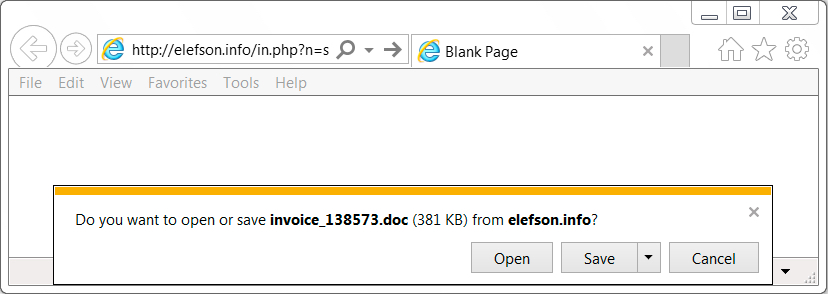
Shown above: Clicking on a link from the email sent me a malicious Word document.
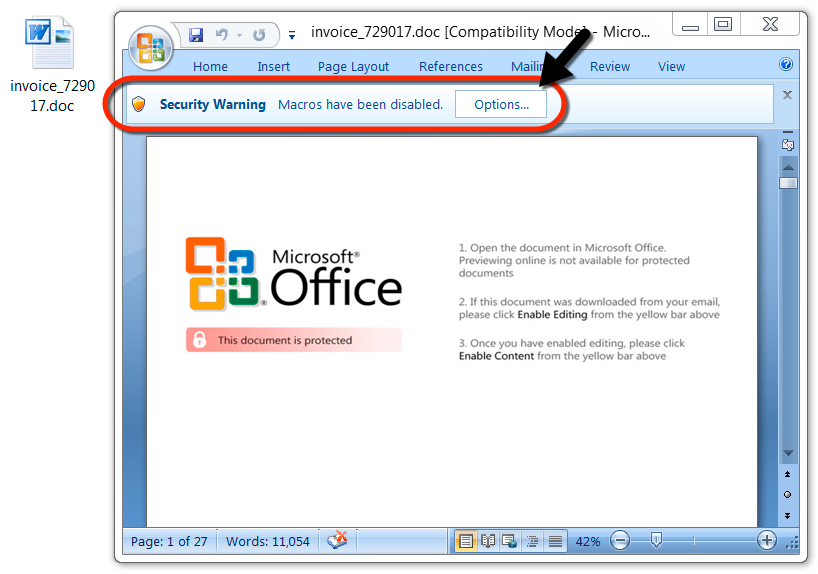
Shown above: The malicious Word document waiting for me to enable macros.
The traffic
I infected a host in my lab. Network traffic was typical for what we've seen in recent months from Hancitor malspam. The only difference? I didn't see a base64 string in the initial HTTP GET request for the Word document like I did earlier this week. That base64 string represents the recipient's email address, which has been standard practice for months now. However, this time, the initial HTTP GET request used a plaintext string for the recipient's email address.

Shown above: Traffic from an infection filtered in Wireshark.
Snort and Suricata alerts on the network traffic are the same as we've seen for months now. This campaign has slowly evolved, but it's noticeably the same as earlier this year.
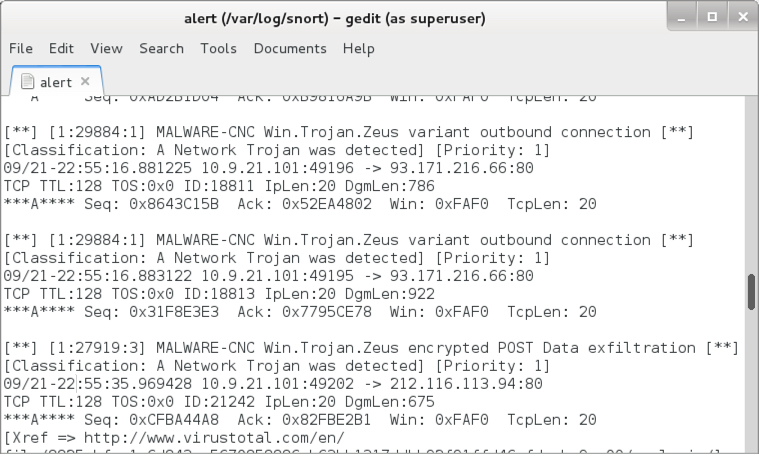
Shown above: Some alerts from the Snort subscription ruleset using Snort 2.9.9.0.
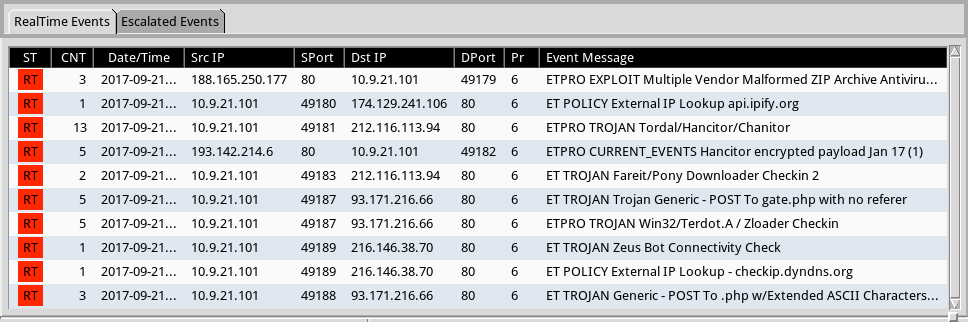
Shown above: Some alerts from the EmergingThreats Pro ruleset using Squil with Suricata on Security Onion.
The infected host
After a cursory search, I couldn't determine how malware stays persistent on an infected Windows host. However, I did find several artifacts for encrypted traffic-related services like Tor.
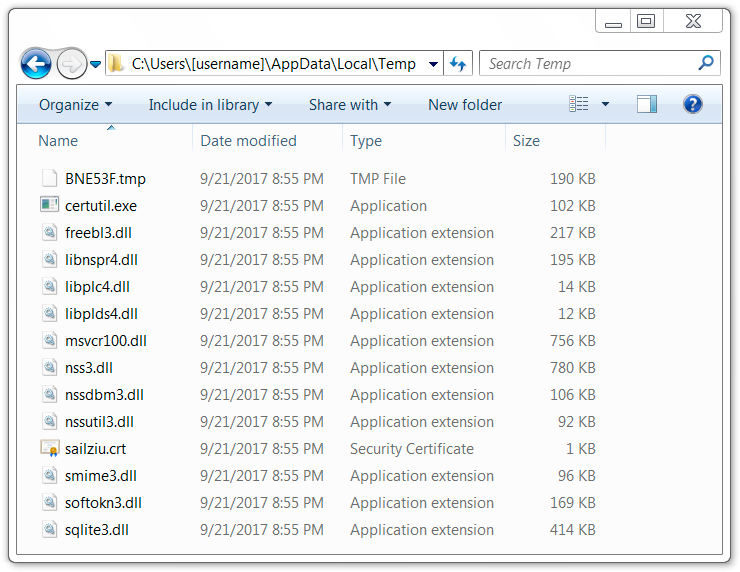
Shown above: Artifacts found in a infected user's AppData\Local\Temp directory.
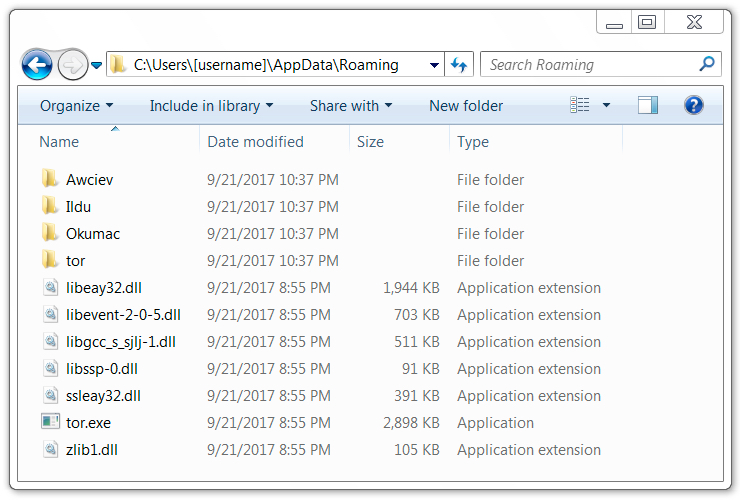
Shown above: Artifacts found in a infected user's AppData\Roaming directory.
Indicators of Compromise (IOCs)
The following IOCs and other indictors are for Hancitor malspam on Thursday 2017-09-21.
Email headers:
- Date/Time: Thursday 2017-09-21 as early as 16:58 UTC through at least 18:42 UTC
- Sender (spoofed): "Advanced Maintenance Inc." <maintenance@advutah.com>
- Examples of subject lines:
- Subject: FW: Your Invoice I114738207 from Advanced Maintenance
- Subject: FW: Your Invoice I131761045 from Advanced Maintenance
- Subject: FW: Your Invoice I144174411 from Advanced Maintenance
- Subject: FW: Your Invoice I156641102 from Advanced Maintenance
- Subject: FW: Your Invoice I182402737 from Advanced Maintenance
Associated traffic:
- EAFGI.COM - GET /in.php?n=[recipient's email address]
- elefson.info - GET /in.php?n=[recipient's email address]
- elefsonhvac.biz - GET /in.php?n=[recipient's email address]
- TRUSTDEEDCAPITAL.NET - GET /in.php?n=[recipient's email address]
- TRUSTDEEDCAPITAL.ORG - GET /in.php?n=[recipient's email address]
- wpipm.org - GET /in.php?n=[recipient's email address]
- 212.116.113.94 port 80 - saritbida.com - POST /ls5/forum.php
- 212.116.113.94 port 80 - saritbida.com - POST /mlu/forum.php
- 212.116.113.94 port 80 - saritbida.com - POST /d2/about.php
- 193.142.214.6 port 80 - 3dprintbudapest.com - GET /wp-content/plugins/all-in-one-seo-pack/1
- 193.142.214.6 port 80 - 3dprintbudapest.com - GET /wp-content/plugins/all-in-one-seo-pack/2
- 193.142.214.6 port 80 - 3dprintbudapest.com - GET /wp-content/plugins/all-in-one-seo-pack/3
- 93.171.216.66 port 80 - hanrinkedhed.com - POST /bdl/gate.php
- api.ipify.org - GET /
- checkip.dyndns.org - GET /
- Various IP addresses over various TCP ports - Tor traffic
- 10.0.2.2 port 443 - TCP SYN packet approx once avery 5 minutes
Malware recovered from the infected host:
SHA256 hash: 39d99fdcc0bd9bb9c7ccf65af499eec073265424f1310bc02b51954b8f6f9782
- File size: 390,656 bytes
- File name: invoice_729017.doc
- File description: Word document with macros that run Hancitor
SHA256 hash: 7ffcaf562952dc920e5026c862b4034cadb4ef8c59ec96a5ae0a2768db513746
- File size: 194,048 bytes
- File location: C:\Users\[username]\Local\Temp\BNE53F.tmp
- File location: C:\Users\[username]\Roaming\Awceiv\coof.exe
- File description: Follow-up malware, DELoader/ZLoader
Final words
As it stands, the open nature of our Internet makes it easy for criminals behind Hancitor malspam and other campaigns to operate. For example:
- Email protocols make it trivially easy for criminals to spoof a sending address and other header lines to mislead recipients.
- Hosting providers and tools like Wordpress allow practically anyone to set up a website, then forget to keep it patched and up-to-date. Enormous numbers of these legitimate websites are compromised by criminals and used in various campaigns.
- Requirements to fraudulently establish an account at a hosting provider are easy to obtain. This encourages a cycle of abuse as criminals establish new servers, those servers are reported, the hosting provider shuts them down, and criminals set up new servers.
- Windows is still a mainstream operating system, and its default settings provide criminals relatively easy targets to infect. Outdated versions like Windows 7 and XP still account for over 50% of the desktop market share. These hosts are even easier to infect, especially if they're not up-to-date and patched.
I view network-enabled computing devices like I view most middle-aged adults living a sedentary lifestyle. Both are probably healthier than they seem, even if there is plenty of room for improvement. All you need is the right mindset. The Internet is a wonderful place, but it's also a great equalizer. Both good and bad people coexist in the same space when we're online. It pays to be careful if you're out and about in a cyber sense--whether you're reading email, browsing the web, or interacting with social media.
As usual, it's relatively easy for system administrators (and the technically inclined) to follow best security practices on their Windows computers. Using Software Restriction Policies (SRP) or AppLocker can easily prevent these types of malspam-based infections from occurring. If you have any other tips, please share them in the comments.
Traffic and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
Anonymous
Oct 17th 2017
8 years ago