Facebook Phishing and Malware via Tumblr Redirects
We got a couple reports of pretty convincing Facebook spam redirecting users to malware and a Facebook phishing site.
The initial bait is a message that you may receive from one of your Facebook friends, whose account was compromised. The message claims to contain a link to images that show a crime that was committed against the friend or a close relative of the friend. The image below shows an example, but the exact message varies. The images then claim to be housed on Tumblr.
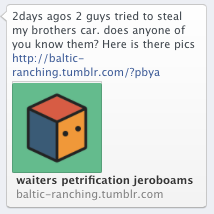
The Tumblr links follow a pattern, but appear to be different for each recipient. The host name is always two or three random English words, and the URL includes a few random characters as an argument. The preview of the Tumblr page lists some random words and various simple icons.
Once the user clicks on the link to the Tumblr page, they are immediately redirected to a very plausible Facebook phishing page, asking the user to log in. The links I have seen so far use the "noxxos.pw" domain, which uses a wildcard record to resolve to 198.50.202.224 . For example, the URL would look like:
hxxp:// facebook.com .accounts.login.userid.243534.noxxos.pw/awks/
Due to the size of the URL, and the fact that the host name starts with "facebook.com", it is hard for the victim to realize that this is not a valid Facebook page.
The fake Facebook page will ask the user for a username and password as well as for a "secret question".
Finally, the site attempts to run a java applet (likely an exploit, but haven't analyzed it yet), and the user is sent to a Youtube look-alike page asking the user to download and install an updated "Youtube Player". The player appears to be a generic downloader with mediocre AV detection.
(was 3/42 when I first saw it. Now 10/42 improved)
As an indicator of compromise, it is probably best right not to look for DNS queries for "noxxos.pw" as well as connections to 198.50.202.224 (which is likely going to change. The server only returns 404 errors right now)
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
noxxos.pw
noxsno.pw
camsas.pw
comsos.pw
somsaw.pw
somsew.pw
I would treat the whole 198.50.202.224/27 block as suspect.
Anonymous
Dec 11th 2013
1 decade ago
Quite a bit more on the Twitter / Facebook part here . . .
http://garwarner.blogspot.com/2013/12/help-your-compromised-friends-on.html
still working on what the after action part was over on Tumblr. I'm told sometimes it was phish and sometimes malware.
_-_
gar
Anonymous
Dec 24th 2013
1 decade ago