Down the RogueAV and Blackhat SEO rabbit hole
Couple of days ago, a fellow handler Joel sent an obfuscated PHP script he acquired. Having a PHP script that is 100KB+ and pretty heavily obfuscated definitely sounds like something I'm interested in, so with couple of extra days I decided to give it some time. At that point in time I did not know that I'm looking at the master PHP script (albeit an old version) that is being used by the RogueAV guys.
I managed to acquire the very latest version of the script that is being used at the moment which provided me with some unique insight into how their operations work. So, I will publish a series of diaries analyzing various parts in the script in next couple of days/weeks (depending on feedback/free time etc). Let's get to work.
First step: poison search engines
If you have been following campaigns by the RogueAV guys you probably noticed that they very quickly poison search engines with the latest events/keywords. The poisoning part is, of course, completely automated and partially done by the script I will talk about.
The scripts that are used are almost exclusively set on compromised web sites. They are mainly interested in web sites running Apache with PHP, of course. It looks like in many cases they are abusing incorrect installations or known vulnerabilities such as open TinyMCE editors. In any case, their goal is to install couple of PHP scripts on those compromised servers. The scripts will allow them to setup poisoning campaigns, offer redirections to other sites serving RogueAV, but at the same time to also conceal their activities as much as possible since they don't want the real owner to find out that his site has been compromised.
This means that the attackers modify the web site, but in such a way that the web site continues to operate normally, unless special parameters/keywords are used! So there are probably thousands of such compromised web sites which the attackers are not using at the moment. Since the scripts allow automatic updates they can use them at any time and configure for a specific campaign in a matter of seconds.
The following figure shows how the SEO part works, with steps described below. While I was researching this I was in contact with some colleagues in CA who posted an article about this back in January (great work by them!) with analysis similar to mine, but the script I analyzed is the latest version used at the moment. You can read CA's article here.
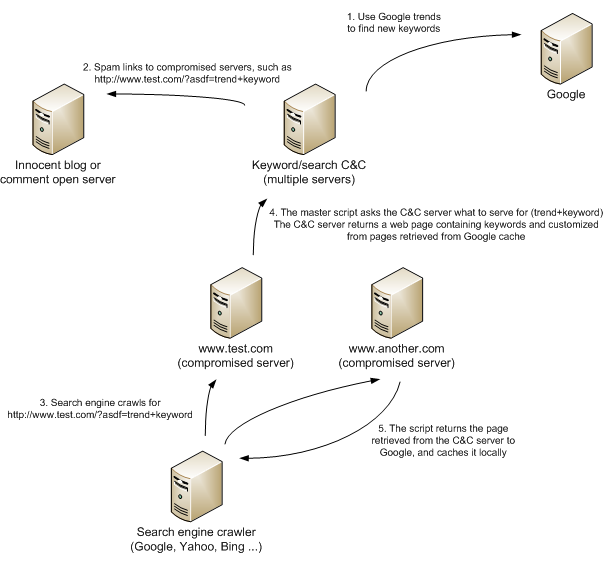
This is what is happening:
- In first step, the master C&C server(s) use Google Trends to collect keywords that are currently hot (interesting).
- The master C&C server(s) now use various methods to spam links to compromised sites containing specially crafted parameters with such keywords.
- Now search engine crawlers either find spammed links or just crawl the compromised web sites again (in which case they get a bit different response – I will cover that in the next diary).
- When the crawler accesses a compromised web site, the master script immediately contacts the C&C server and asks what to return to the crawler. The C&C server creates a web page in real time containing a lot of references to the asked keyword, as well as links to other compromised web sites!
- The custom web page is returned to the crawler and cached locally.
In step 2, besides spammed links, search engine crawlers will also visit compromised web sites. Now an interesting thing happens that helps poison the results: when the script detects a visit from a search engine crawler, but without the required poisoned parameters, the PHP script by the attackers will return the original requested web page, but with concatenated links to other compromised web sites that it has in the local database. This local database can be updated automatically through an interface on the PHP script so the attackers can update the database constantly as well.
Here we can see such a web page requested first time normally (normal user agent, main index.html requested) and second time pretending to be a search engine crawler. Notice the difference in size of the returned file:
$ ls -l index.html*
-rw-rw-r-- 1 nobody nobody 38383 Jun 26 12:53 index.html-normal
-rw-rw-r-- 1 nobody nobody 95703 Jun 26 14:47 index.html-crawler
And this is what gets appended in raw HTML:
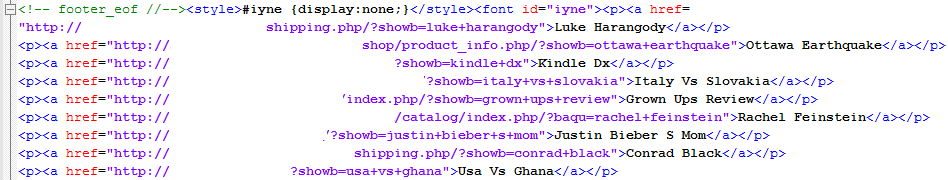
(compromised sites deliberately removed as they are still live).
By doing this they are getting all compromised sites linked to each other, hopefully increasing their rating with various search engines. See the style setup as display:none? This makes sure that if someone renders this web page through a browser that the inserted links will be invisible. They are not invisible to a crawler, of course.
Redirecting to RogueAV
Now, after all this poisoning, if a normal user (plain user agent) accesses the web site directly, he will just get the same cached web page that the crawler got. However, if the web site is accessed by clicking the link that appeared as a search result in any search engine (Google, Yahoo, Bing ...), such a request will have a corresponding referrer set and the script will redirect the user to another web site that will serve (you guessed it) RogueAV, as shown in the figure below:
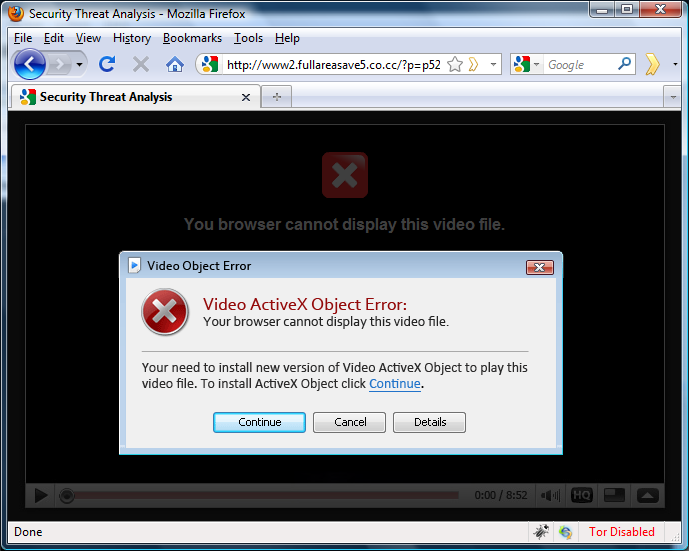
This time they are trying to get the user to install it by displaying an ActiveX error.
With this I will end with the first diary. In the next diary I'll go deeper into analyzing interesting details found in the script (will be posted on Thursday).
If you would like me to go into more details with anything let us know through our contact form.
--
Bojan
INFIGO IS
| Web App Penetration Testing and Ethical Hacking | London | Mar 2nd - Mar 7th 2026 |


Comments
-A
anirban
Jun 28th 2010
1 decade ago