December 2021 Forensic Contest: Answers and Analysis
Introduction
Thanks to everyone who participated in our December 2021 forensic challenge! 61 individuals submitted answers, and most people answered correctly. Unfortunately, we could only pick one winner. The winner was randomly chosen from those with the correct answers. Join us in congratulating this month's winner, Paul Lennox! We will contact Paul, so we can send him a Raspberry Pi 4 kit.
You can still find the pcap for our December 2021 forensic contest here.
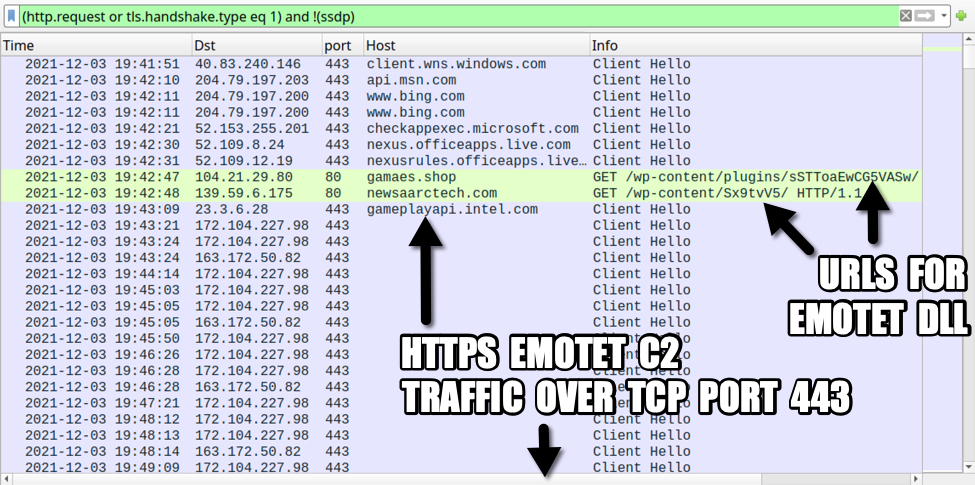
Shown above: Pcap from the December 2021 forensic challenge filtered in Wireshark.
Questions
- What was the IP address of the infected Windows computer?
- What was the host name of the infected Windows computer?
- What was the user account names from the infected Windows computer? (should be "name" not "names")
- What was the date and time the infection activity began?
- What was the family of malware that caused this infection.
Answers
- IP address of the infected Windows computer: 10.12.3.66
- Host name of the infected Windows computer: DESKTOP-LUOABV1
- User account name of the infected Windows computer: darin.figueroa
- Date/time the infection activity started: 2021-12-03 at 19:42:47 UTC
- Family of malware that caused this infection: Emotet
The environment
As stated in our diary for the December challenge, characteristics of the Active Directory (AD) environment are:
- LAN segment range: 10.12.3.0/24 (10.12.3.0 through 10.12.3.255)
- Domain: fargreentech.com
- Domain Controller: 10.12.3.3 - FARGREENTECH-DC
- LAN segment gateway: 10.12.3.1
- LAN segment broadcast address: 10.12.3.255
The Infected Windows Host
The IP address 10.12.3.66 is th e only Windows client in the pcap. According to one of the tutorials listed in the December challenge, you can find the host name using various methods. The image below shows filtering on NBNS traffic in Wireshark and finding the host name that way.
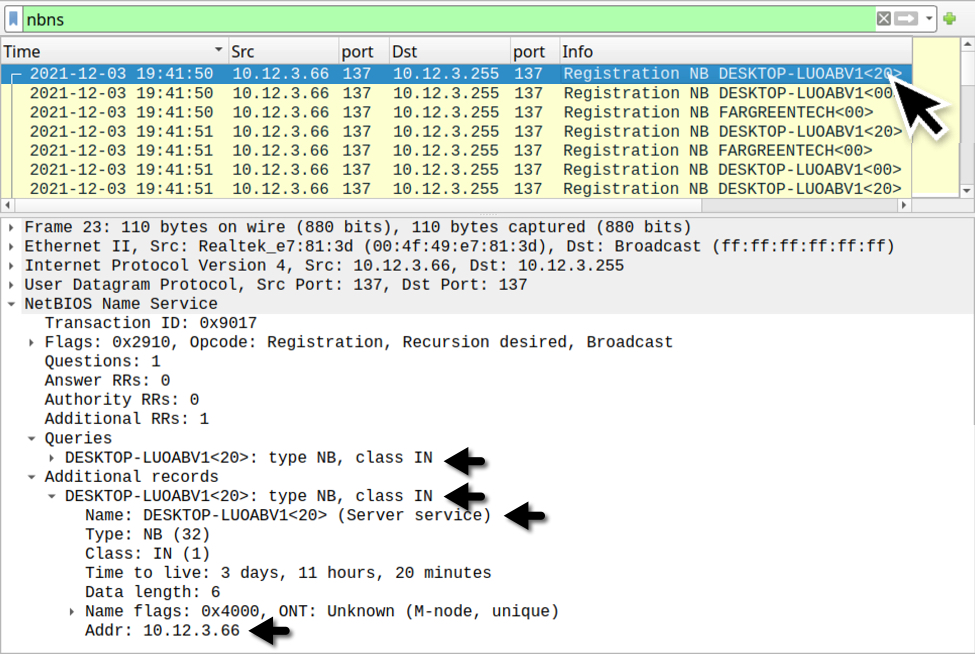
Shown above: Finding the infected Windows host name through NBNS traffic.
The Windows user account name associated with this infected Windows host can be found through filtering on Kerberos traffic as described in the same Wireshark tutorial.
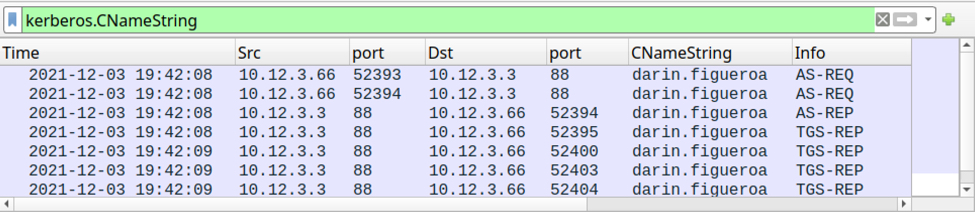
Shown above: Finding the Windows user account name through Kerberos traffic.
The Infection Traffic
A basic web filter reveals two unusual HTTP GET requests followed by HTTPS traffic without an associated domain. The two HTTP requests were caused by a malicious macro from a Microsoft Office document. One of those requests returned a DLL for Emotet malware.
Unfortunately, we cannot export the Emotet DLL from this pcap.
Emotet caused C2 traffic using HTTPS without any associated domain names. Emotet C2 traffic previously used HTTP, but since November 2021, its C2 traffic has been HTTPS.

Shown above: Traffic from the pcap filtered in Wireshark.
The two HTTP URLs used to retrieve the Emotet DLL were:
- hxxp://gamaes[.]shop/wp-content/plugins/sSTToaEwCG5VASw/
- hxxp://newsaarctech[.]com/wp-content/Sx9tvV5/
The first attempt to games[.]shop was not successful, but the HTTP request to newsaarctech[.]com returned an Emotet DLL. Both of the above URLs have been reported to URLhaus as hosting DLL files for Emotet. These two domains have also been referenced elsewhere.
- Entry for gamaes[.]shop URL in URLhaus
- Reference in CyberInt blog post for gamaes[.]shop URL
- Entry for newsaarctech[.]com URL in URLhaus
- Tweet about newsaarctech[.]com as domain used by Emotet on 2021-12-02
The following IP addresses over TCP port 443 have been reported as C2 channels for Emotet:
- 172.104.227.98 port 443 [Link to IP address in Feodo Tracker]
- 163.172.50.82 port 443 [Link to IP address in Feodo Tracker]
With a basic web filter, scroll down a bit to find SSL/TLS traffic using TCP ports 465 and 587 starting at 20:09 UTC. This represents encrypted SMTP traffic, and it reveals our Emotet-infected host also acted as a spambot. Emotet uses Emotet-infected Windows hosts to help distribute new Emotet malspam.
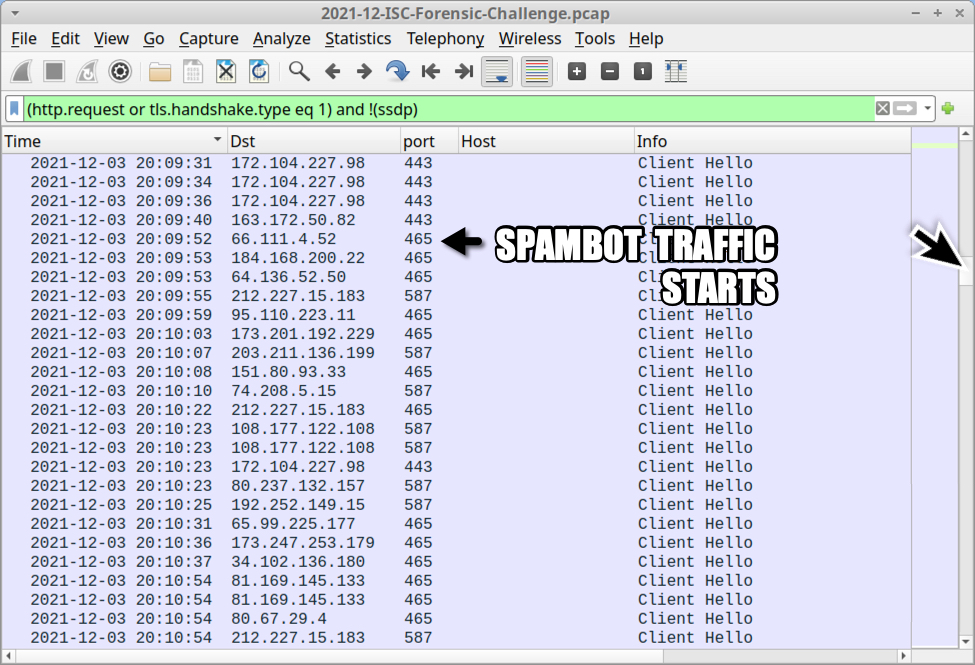
Shown above: Showing where spambot traffic begins in the pcap.
Filter on SMTP traffic to find 2097 frames in the column display with unencrypted SMTP commands and data.
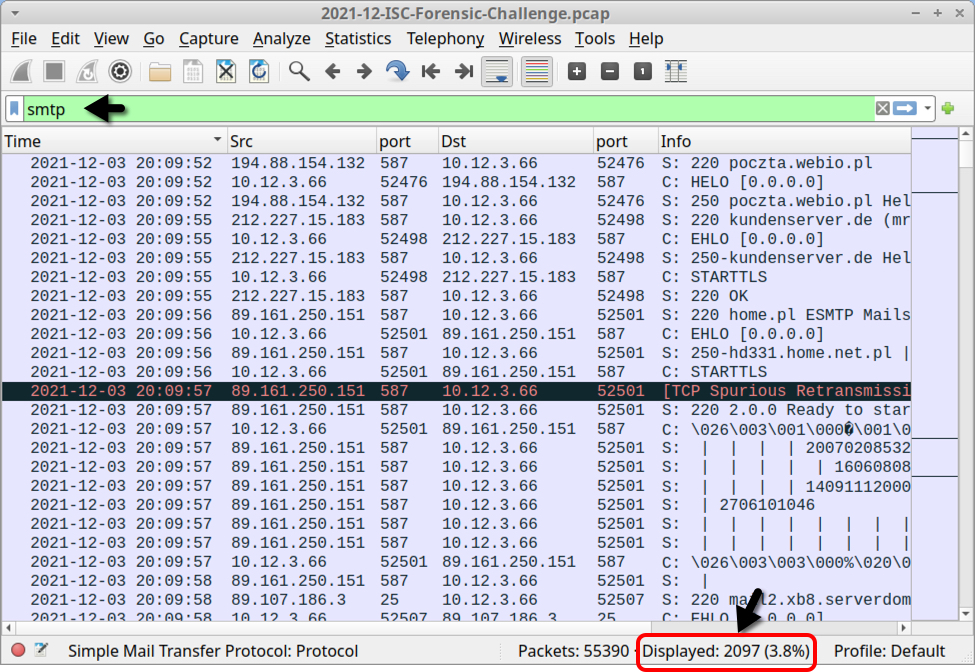
Shown above: Filtering on SMTP traffic in the pcap.
Filter on smtp.data.fragment, to find indicators for 17 emails sent through unencrypted SMTP.
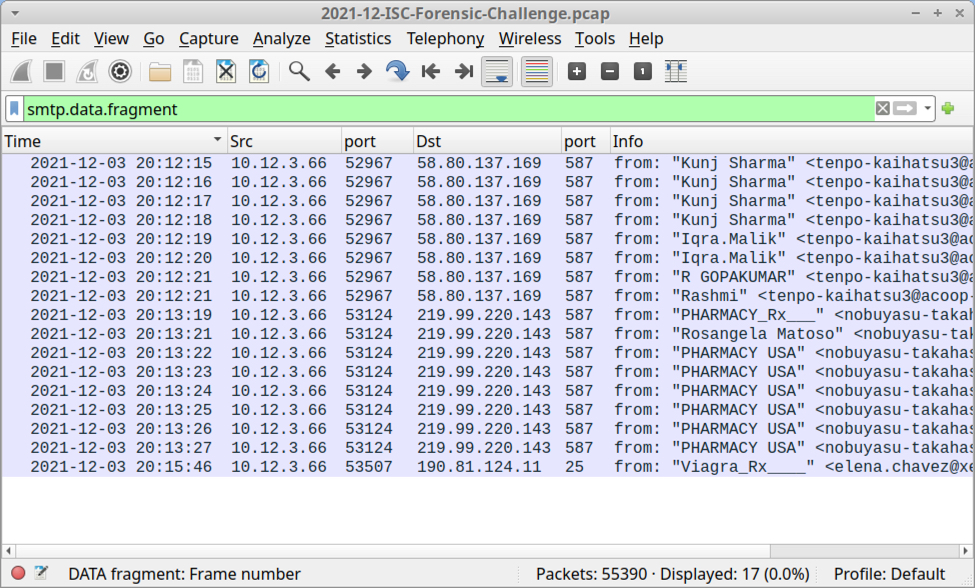
Shown above: Filtering to find spambot emails sent over unencrypted SMTP.
You can extract these 17 emails using File --> Export Objects --> IMF... as shown below.
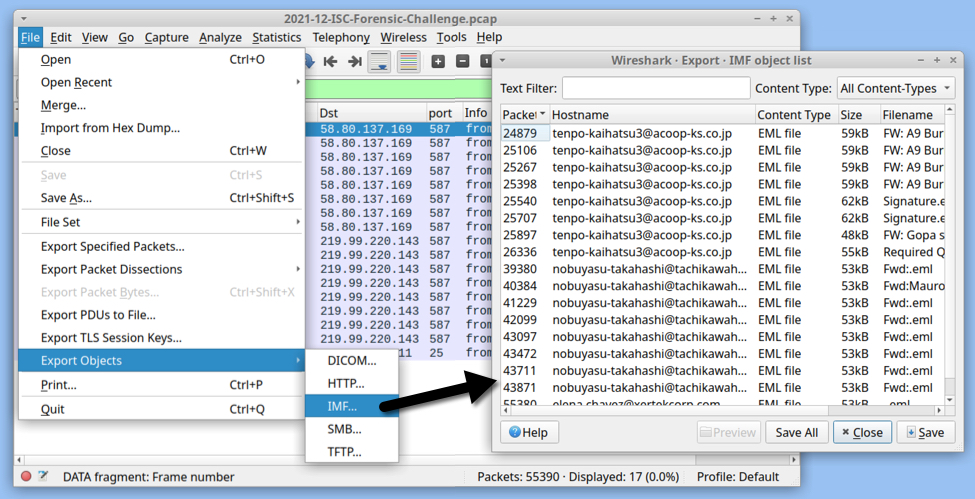
Shown above: Exporting 17 malicious emails from the pcap.
All of these emails are spoofed replies to legitimate email chains collected from previously-infected Windows hosts. All of these emails have attachments. Some of the attachments are Excel spreadsheets. Other attachments are password-protected zip archives. We can review the emails using an email client. My choice is Mozilla Thunderbird.
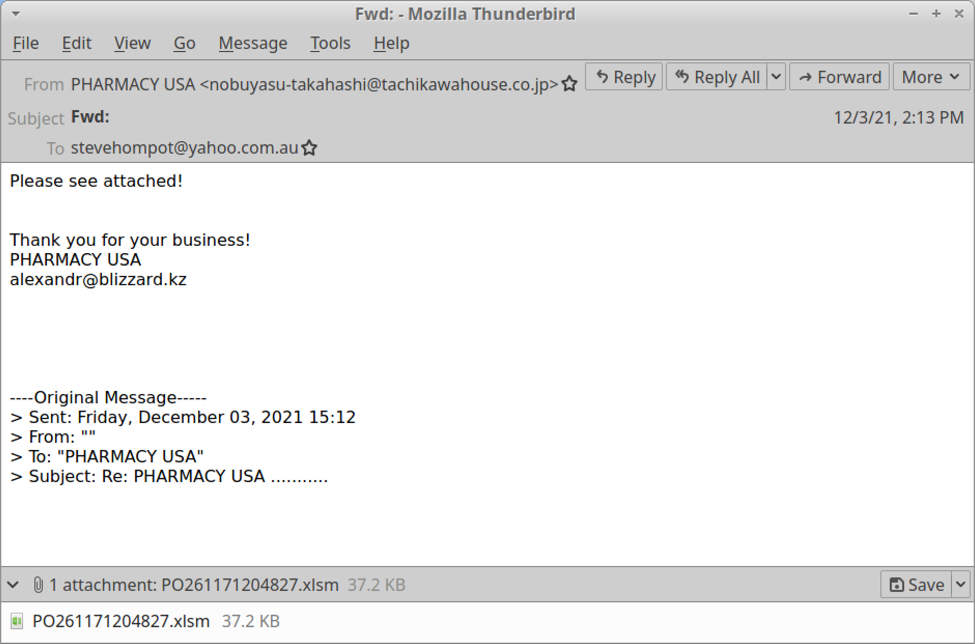
Shown above: Example of spambot email with an attached Excel file.
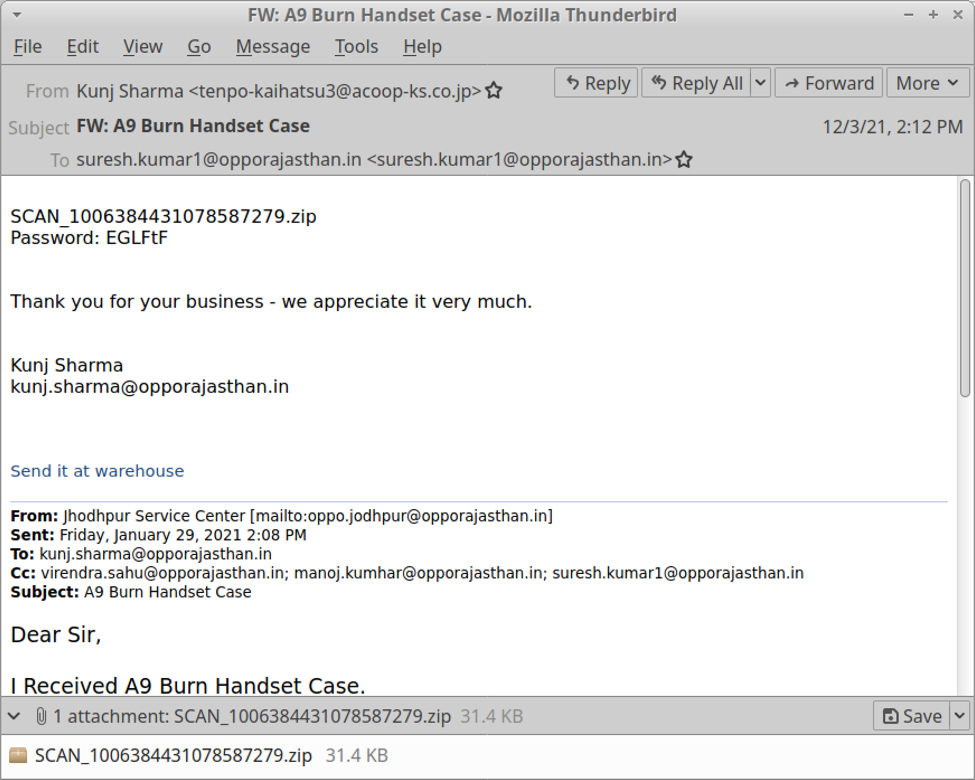
Shown above: Example of spambot email with a password-protected zip archive.
This month's forensic challenge reveals traffic you might see when Emotet turns an infected Windows host into a spambot. Windows clients should not generate SMTP traffic to several different IP addresses as we see here. This is classic spambot behavior.
Final words
Emotet is gearing up for a new wave of activity as we enter the holiday season. Recent reports reveal Emotet is now pushing Cobalt Strike, which has been used to distribute ransomware. Even with recent high-profile explotation issues with log4j, security professionals should remain aware of Emotet and other continuing threats.
Congratulations again to Paul Lennox for winning this month's challenge!
You can still find the pcap for our December 2021 challenge here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments