Controlling network access to ICS systems
by Manuel Humberto Santander Pelaez (Version: 1)
After 6 years, I have returned to the world of operating technologies. One of my main concerns at that time regarding the use of new technologies was to seek access control via the network to the different devices that make it up, because unlike the world of information technologies where access is sought to be widespread and there are multiple ways to perform access control at the application and network level, the world of industrial control has limitations depending on the version of the supervision and control protocols that are supported.
This cybersecurity requirement is mandatory for sectors such as electricity under the active standards NERC CIP-003-8 and NERC CIP-005-7. The suggested architecture to implement is based on the Purdue Enterprise Reference Architecture taken for the SANS ICS410 course, which we can see in figure 1. Its components are:
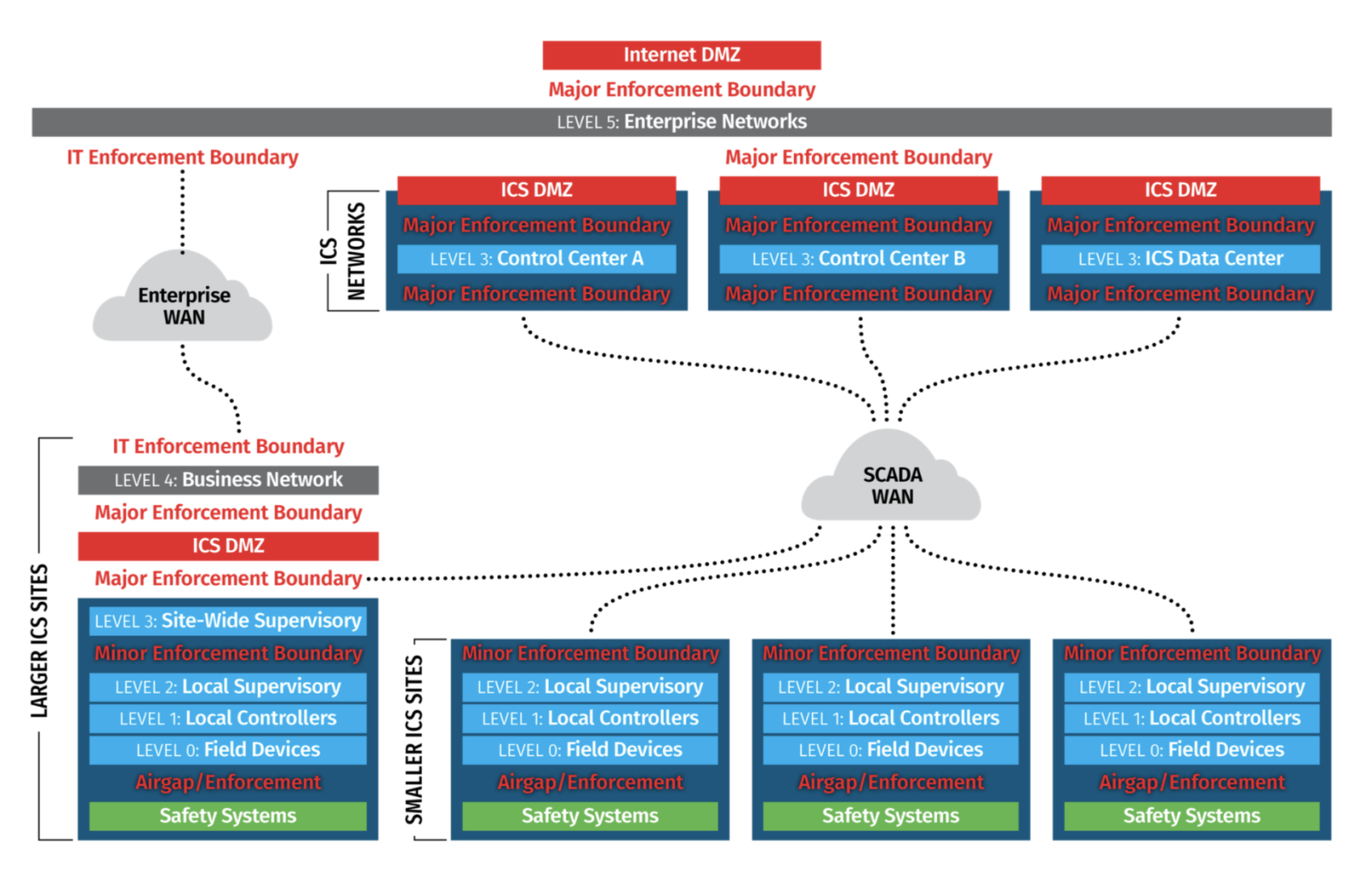
Figure 1: SANS ICS410 reference model based on Purdue Enterprise Reference Architecture.
Let's discuss the details for each level:
PURDUE LEVEL |
DESCRIPTION |
EXAMPLES |
|
Level 5: Enterprise Networks |
Services at the corporate level that assist specific business divisions and individual users. Typically, these systems are housed within the company's data centers. |
Servers providing:
|
|
Level 4: Business Networks |
Information technology networks specifically tailored for business users at localized sites. These networks provide connection to the enterprise's wide area network (WAN) and may also allow local internet access. However, direct internet access should not be granted beyond this level. |
|
IT/OT BOUNDARY (DMZ) |
||
|
Level 3: Site-Wide Supervisory |
Monitoring, supervisory, and operational support for all or part of the regions covered by the company |
|
|
Level 2: Local Supervisory |
Observation and managerial oversight for an individual process, cell, line, or a Distributed Control System (DCS) solution. Processes should be segregated based on function, type, or risk, ensuring they remain distinct from each other. |
|
|
Level 1: Local Controllers |
Apparatus and systems designed to offer automated regulation of a process, cell, line, or a Distributed Control System (DCS) solution. Contemporary Industrial Control System (ICS) solutions frequently integrate Levels 1 and 0. |
|
|
Level 0: Field Devices |
Sensors and actuators utilized in the cell, line, process, or DCS solution. These are frequently amalgamated with Level 1. |
|
Figure 2: Purdue Enterprise Reference Architecture description
Why am I talking about this? I did some research on shodan and found the following:
- I found a universe of 499 open-access HMI. This means attackers can get full view of an ICS process from the internet with no restriction. The following chart shows the country distribution:
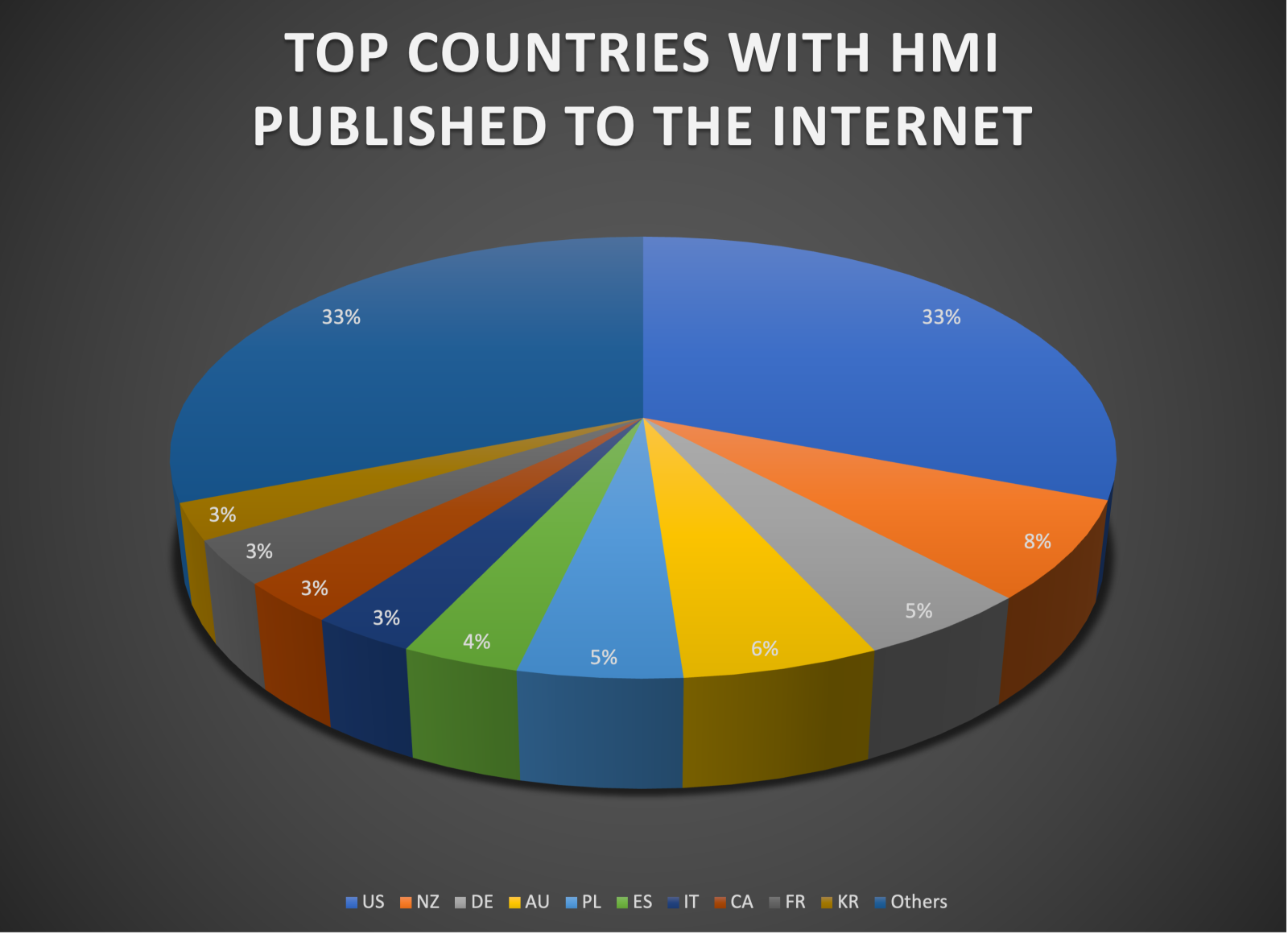
Figure 3: Top countries with HMI published to the internet.
- For all those HMI published to the Internet, almost half uses VNC without authentication:
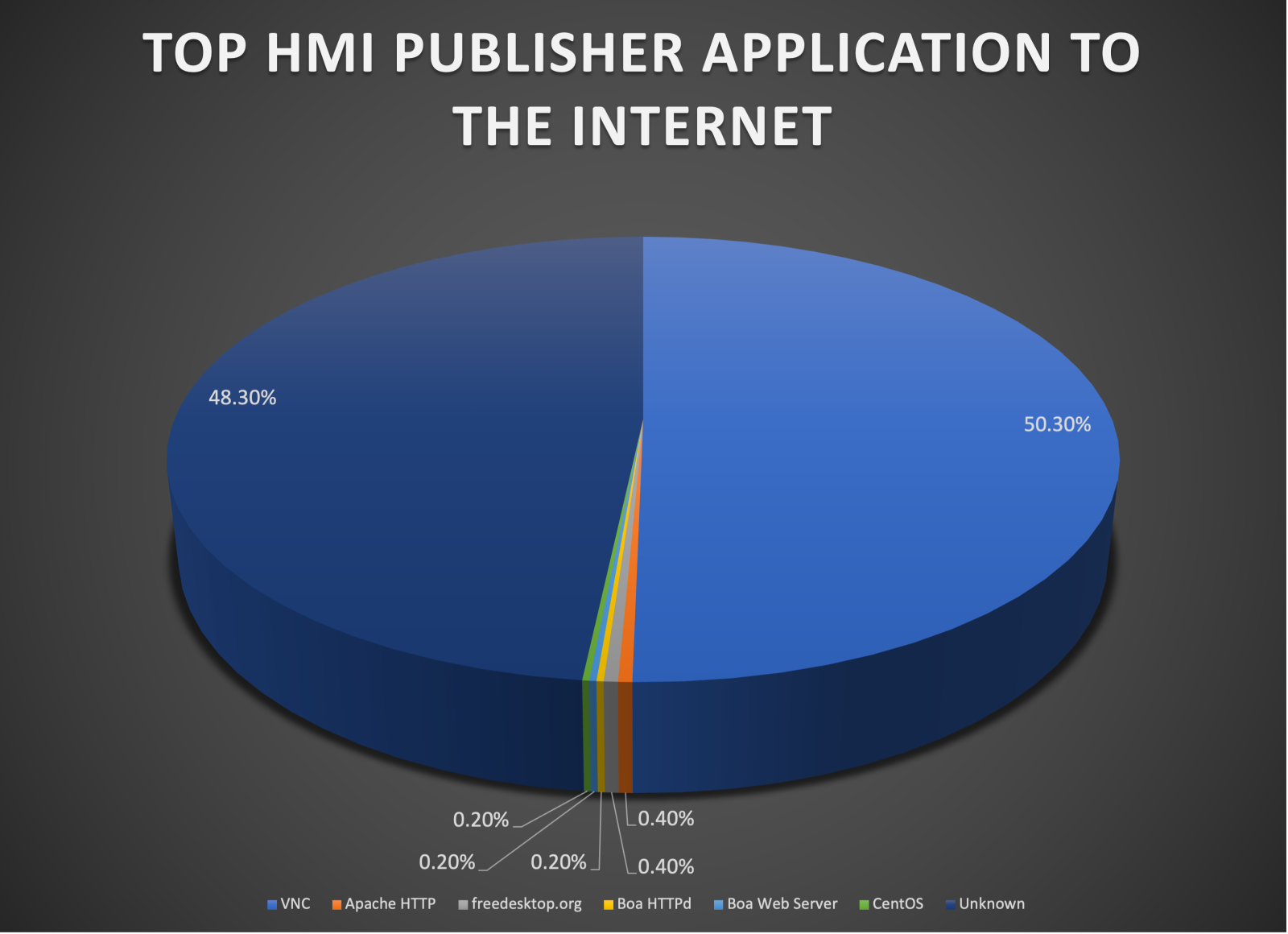
Figure 4: Top HMI publisher applications to the internet
- I found a universe of 25234 Modbus RTU devices published on the internet. The following chart shows the country distribution:
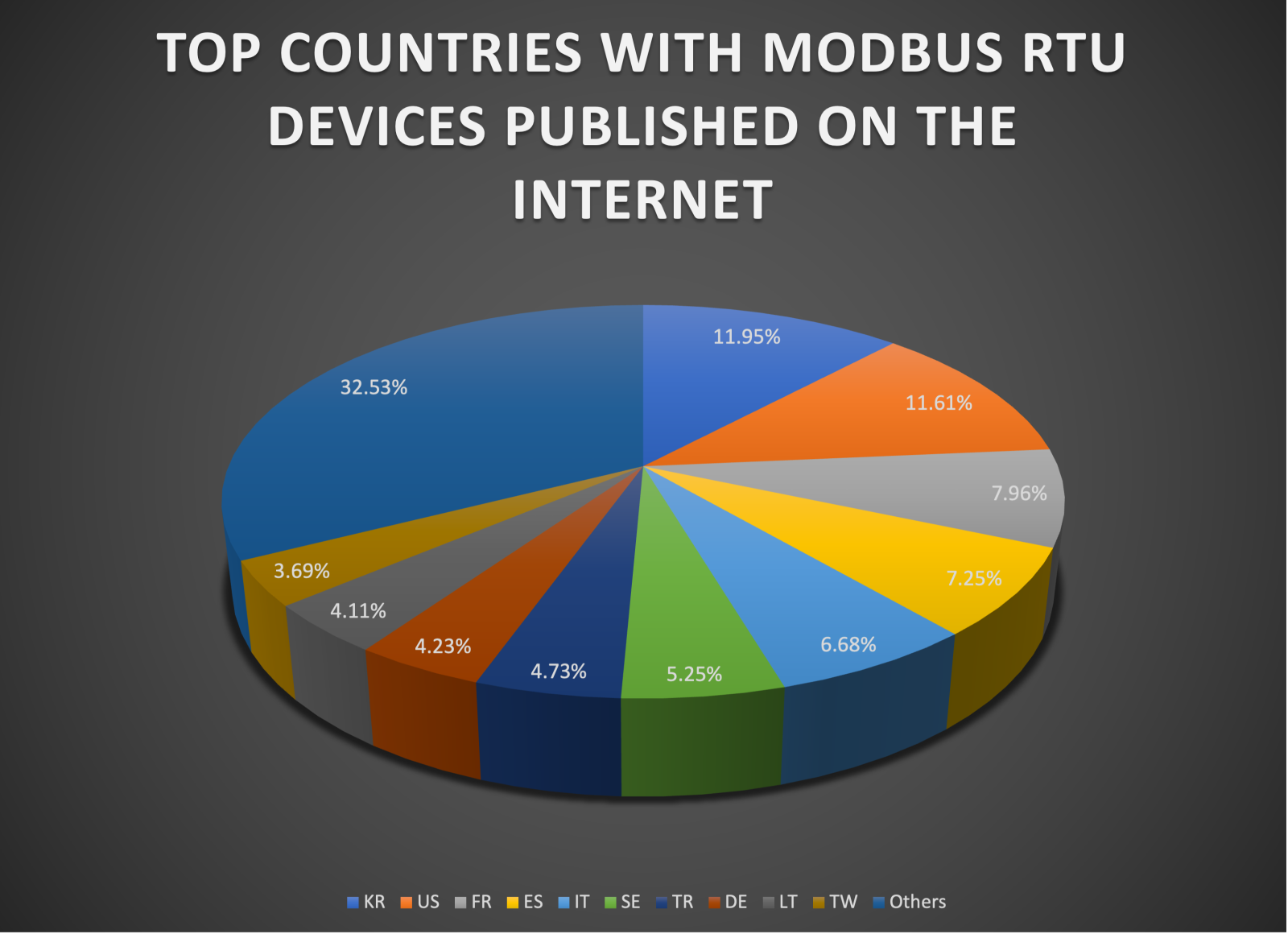
Figure 5: Top countries with modbus RTU devices published to the Internet
Now we can conclude the following:
- The relevant gap continues in the security measures found for IT vs. those found in OT. It is important that companies that have critical infrastructure management within their business establish a transversal cybersecurity strategy that manages all types of technology, including OT.
- The cloud is here to stay. It is definitely feasible to implement SCADA systems using cloud environments. However, the electronic protection of supervisory and control environments as established by standards such as the revised NERC ones is not negotiable.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Mastodon:manuelsantander@infosec.exchange
Linkedin:manuelsantander
email:msantand@isc.sans.org


Comments