A Quick Survey of .zip Domains: Your highest risk is running into Rick Astley.
A week ago, I wrote about Google starting to offer ".zip" domains and the possible risks associated with this [1]. Earlier today, I quickly surveyed registered .zip domains to see what people are doing with them.
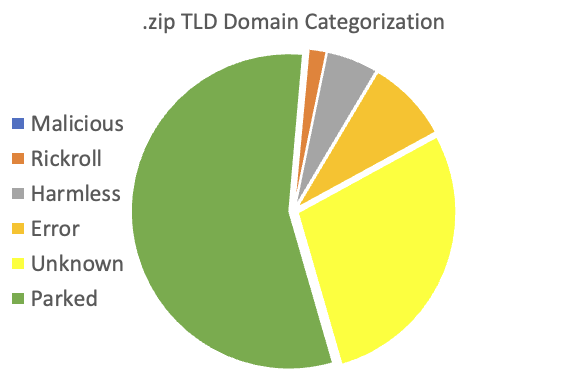
I found a total of 2,753 domains with content. Out of these files, I was able to categorize 1,928. The remaining is still a work in progress.
So far, most domains are "Parked" (1,506). This is typical for new domains displaying a registrar default page until the owner configures content. 229 of the domains are showing various errors. I classified 143 domains as harmless, meaning they link to different other pages that, as far as I can tell, do not provide malicious content. Some "harmless" sites appear registered by security companies or individuals either directing to their page or displaying messages warning about the .zip TLD issues. A few of the pages do, for example, direct to individual LinkedIn profiles.
48 domains direct to Rick Astley ("rickrolling") content or similar videos mostly meant to annoy visitors.
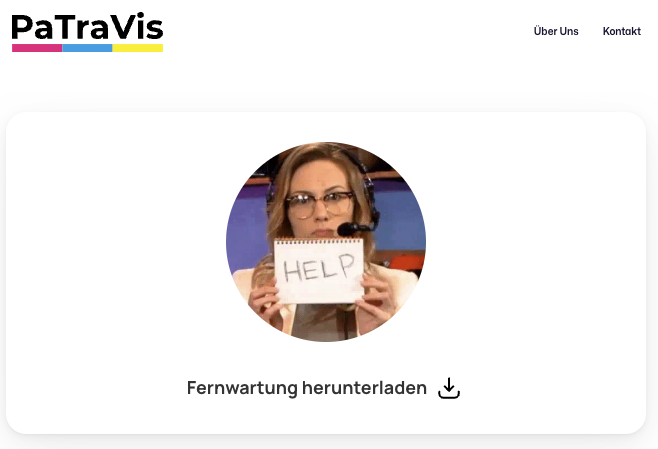
So far, I only found one domain that I consider "suspect": fermwartung[.]zip ("Fernwartung" is the German word for Remote Maintenance). It directs to what looks like a legitimate company's webpage, but the download triggers some suspicious signatures on Virustotal [2]. I am unfamiliar with the company, but according to the web page, they appear to be an IT service provider. It is possible that their remote assistance tool triggers some Anti-Virus warnings.
sentineloneinstaller[.]zip appeared to be advertising Norton Anti-Virus. Currently, the website is down, so I cannot verify if it attempted to play the "fake anti-virus" game.
This is still a work in progress, and I will update this story as I can classify more domains. The classification is based on keywords, so I will surely miss something. Let me know if you find an "interesting" (malicious) .zip domain.
A couple of sites offered online compression/decompression of zip files. There is an obvious risk here that, first of all, the file's content may be leaked, and secondly, the file you get back may be altered. But this is not specific to the ".zip" TLD, and I classified these sites as "harmless" for now.
One site displayed a login form. But I suspect this was just a login form for the site's admin interface. It did not resemble a brand I recognized and only asked for a password, not a username.
[1] https://isc.sans.edu/diary/The+zip+gTLD+Risks+and+Opportunities/29838/
[2] https://www.virustotal.com/gui/file/06298771950708c66951149af0962079c260e08d9eb536a17d9c5f54c0d888a7
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Jeremiah
May 18th 2023
2 years ago
Johannes
May 18th 2023
2 years ago
Sam
May 19th 2023
2 years ago
Meaning, the site is malicious; they're praying their prey will not notice.
formfeed
May 25th 2023
2 years ago
Using a site like Github the perfect place to abuse this... Where the expected outcome is a downloaded file.
https://legit/cooltool/releases/@vMal.ici.ous.zip
More details at: https://medium.com/@bobbyrsec/the-dangers-of-googles-zip-tld-5e1e675e59a5
Steve
May 26th 2023
2 years ago