Huge Signed PE File
Xavier's diary entry "A 'Zip Bomb' to Bypass Security Controls & Sandboxes" reminded me of something. I've seen huge PE files like Xavier saw, but I've also seen a couple of huge PE files that are signed. I will explain here how you can reduce their size.
The PE file that Xavier talked about, can be represented as follows (picture not to scale):

To recover the original PE file, and make it much smaller, suitable for analysis, one removes the NULL block. As Xavier explained.
I've seen PE files like this. What I've also seen a couple of times, is a huge PE file like this (again, picture not to scale):

So right after the huge block of NULLs, comes a digital signature (Authenticode). It's a very small block, but not NULL. The examples I've seen were fake signatures, but this can be done with valid signatures to.
To recover the original PE file, one needs to remove the NULL block and the signature, and also update the reference to the signature inside the PE file (directory entry with offset & size of signature).
This can be done as follows.
As I'm not at liberty to share the samples I have, I took Xavier's sample and added a fake signature with my disitool.py.
Taking a look at that PE file with pecheck.py, you get a warning from the pefile module that the PE file contains a huge amount of NULL bytes.
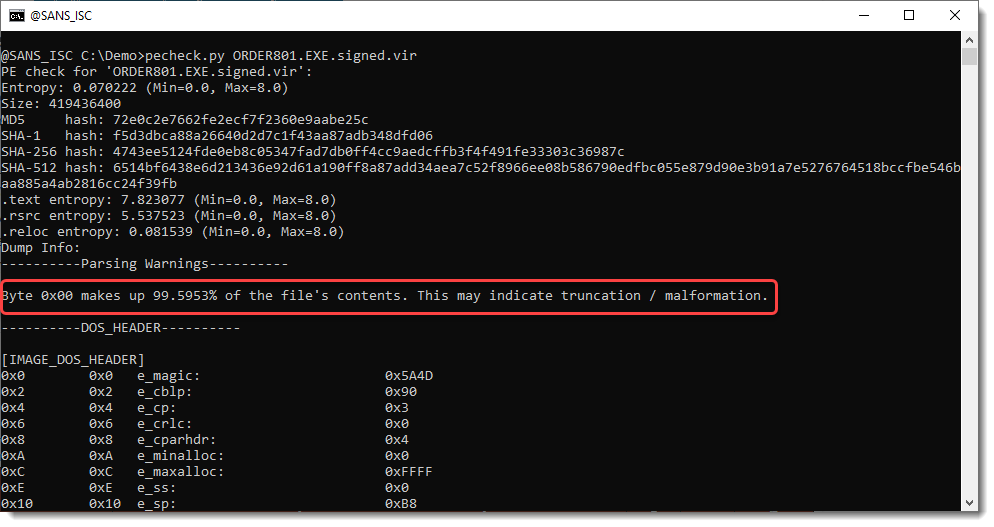
The file is huge: 400 MB. But when you look at the sections, they are in total less than 2 MB:
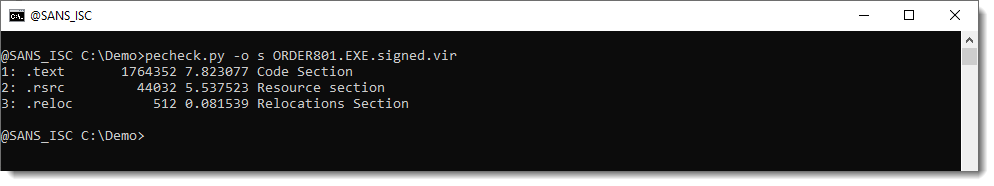
The file contains a digital signature:
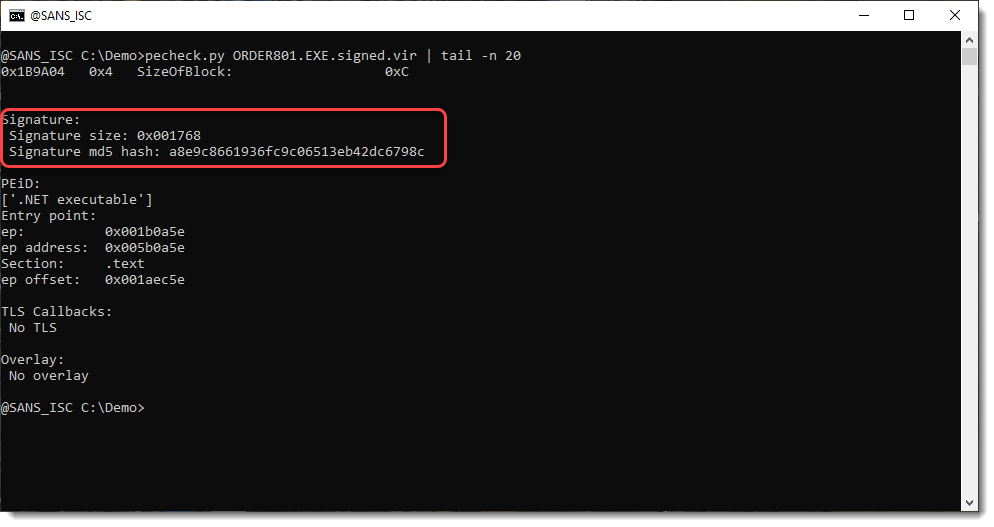
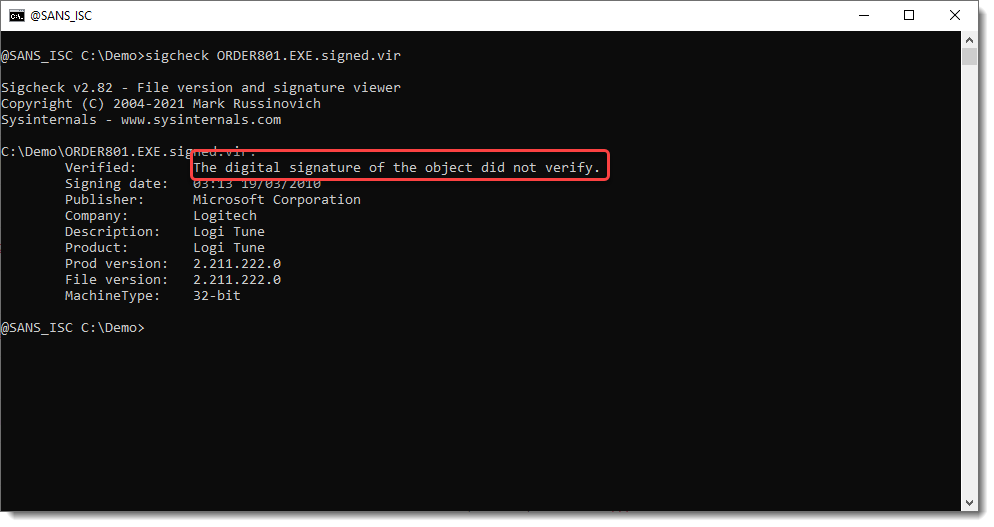
It is fake:
We remove the digital signature with my disitool.py like this:
We verify that the signature is removed:
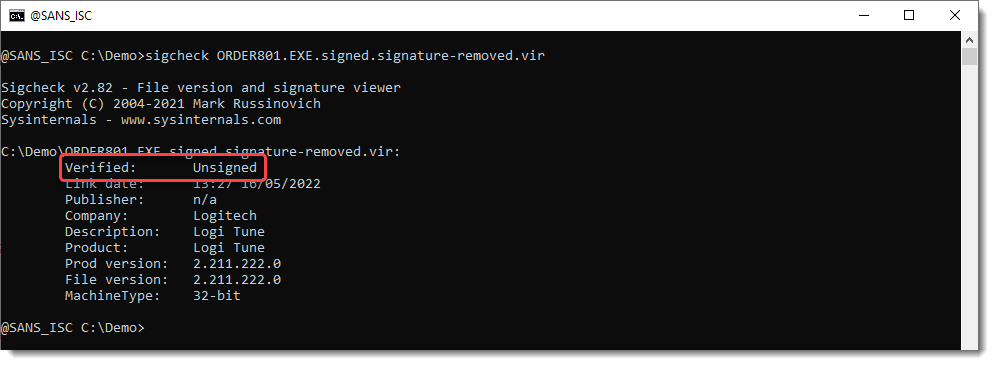
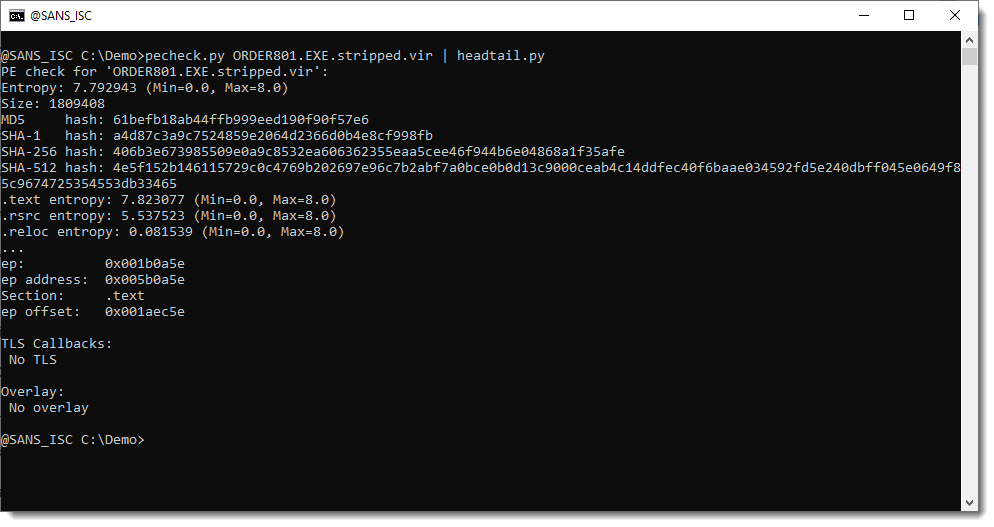
And then we run pecheck.py again:
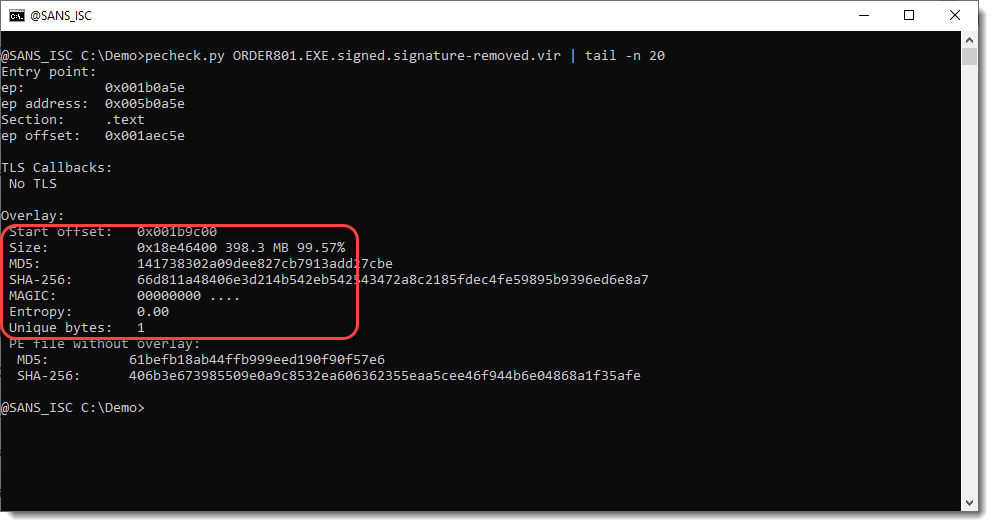
We have a huge overlay of 398MB that consists of NULL bytes only (MAGIC 00000000, entropy 0.0, only 1 unique byte).
We can strip that overlay with pecheck.py using option -o s (s = stripped PE file) and writing the result to disk -D + file redirection:
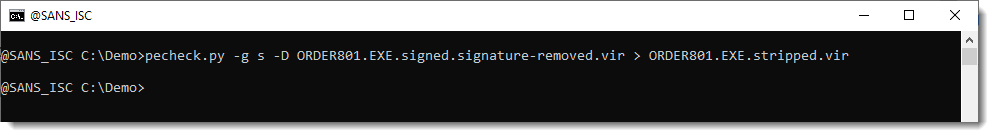
The result is a PE file less than 2 MB:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments
**Software Execution Approval**
A security professional approves the end user running of every new program on the computer/network and all its loaded DLLs based on Authenticode signatures. Instead of AV signatures, everyone (corporate and even home users) would have execution signatures that get updated in near real time.
We have full time IDS/EDR analysts, why not an execution analyst (or MSSP) who investigates new programs introduced on the network. They would approve it and it would get instantly pushed out to every other computer on the network. There could be a learning mode like AppLocker. You would have a somewhat short list of software that is approved to run on your network or computer; especially if an entire software company gets approved by the execution analyst.
The General Process:
1. Hook Windows Loader/LoadLibrary
2. End user launches a *new* program on the network and chooses its priority for getting approved. e.g. needs to be approved in 1 minute, 10 minutes, 30 minutes, tomorrow.
3. The program and its details are sent to the software execution analyst.
4. Analyst investigates (VirusTotal, etc.) the software and allows it to run in some way. e.g. approves the entire publisher to run on your network, or approves it to run on just that computer/OU at a low integrity.
5. The analyst's decision is immediately pushed out to all other computers on the network.
The Question
What are the problems with this malware solution, and do you think they can be solved?
Thanks!
Adam Bray
Anonymous
May 31st 2022
3 years ago