Malpsam pushes Ursnif through Italian language Word docs
Introduction
For the past two weeks or so, I haven't found any malspam using password-protected zip archives with Word documents having macros for Ursnif. However, on Tuesday 2020-02-11, malspam from this campaign has resumed. This time, it used Italian language Word documents with macros for Ursnif. @reecdeep started a Twitter thread with some of the details (link).
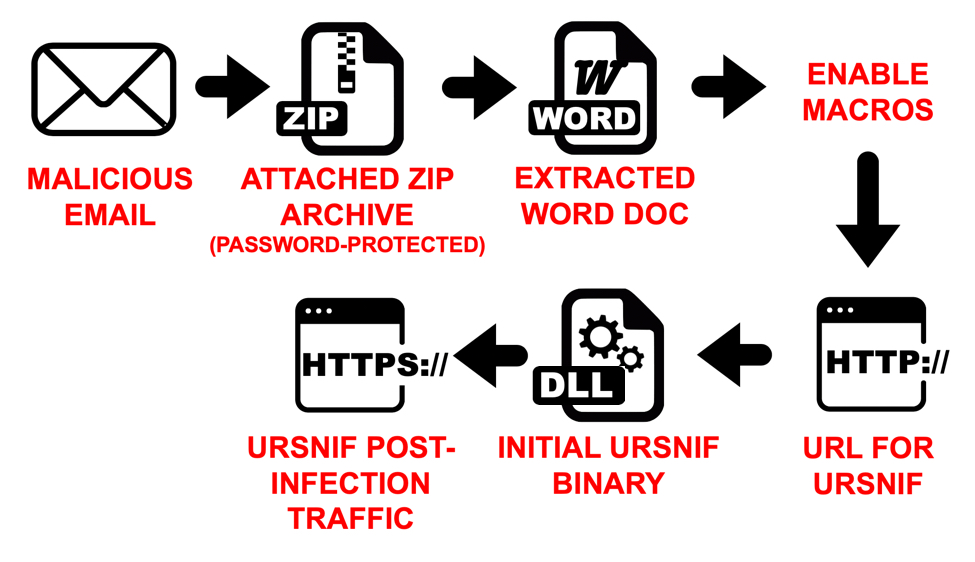
Shown above: An infection chain from this campaign seen on Tuesday 2020-02-11.
Today's diary has a quick review of an infection from this campaign from Tuesday 2020-02-11.
Finding the associated Word documents
I searched VirusTotal Enterprise using the following criteria and found at least 66 password-protected zip archives containing the file info_02_11.doc from Tuesday 2020-02-11:
None of the associated emails had been submitted to VirusTotal, so I had to guess at the password. Several of these zip archives used 111 as the password. One of them used 222 as the password. The example I used for an infection had 333 as the password.
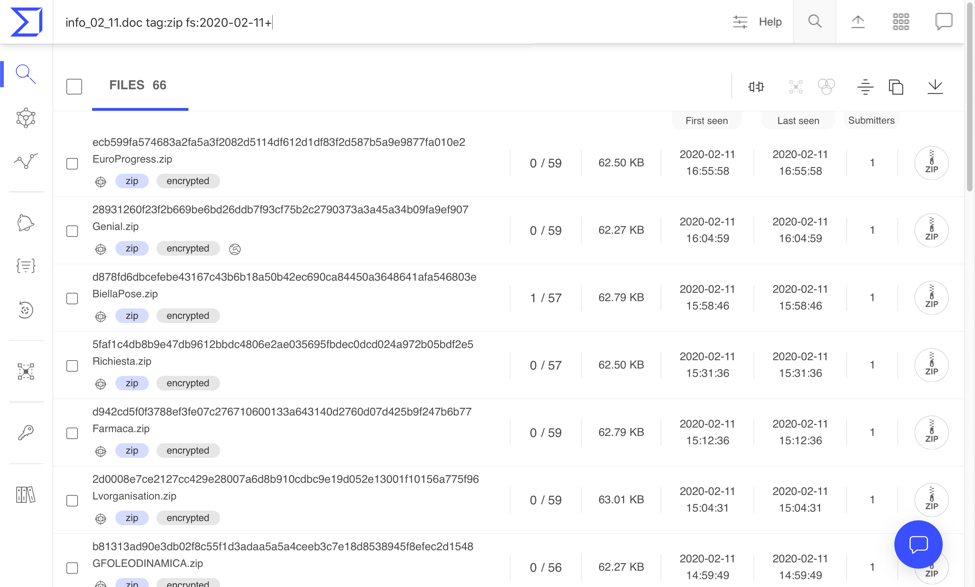
Shown above: Searching VirusTotal Enterprise for zip archives containing info_02_11.doc.
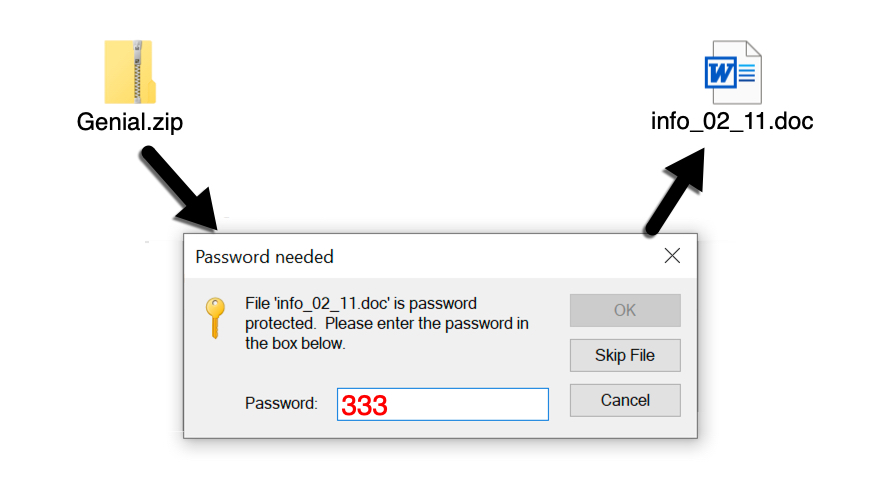
Shown above: After a couple of guesses, I found the proper password for one of the zip archives from my VirusTotal search.
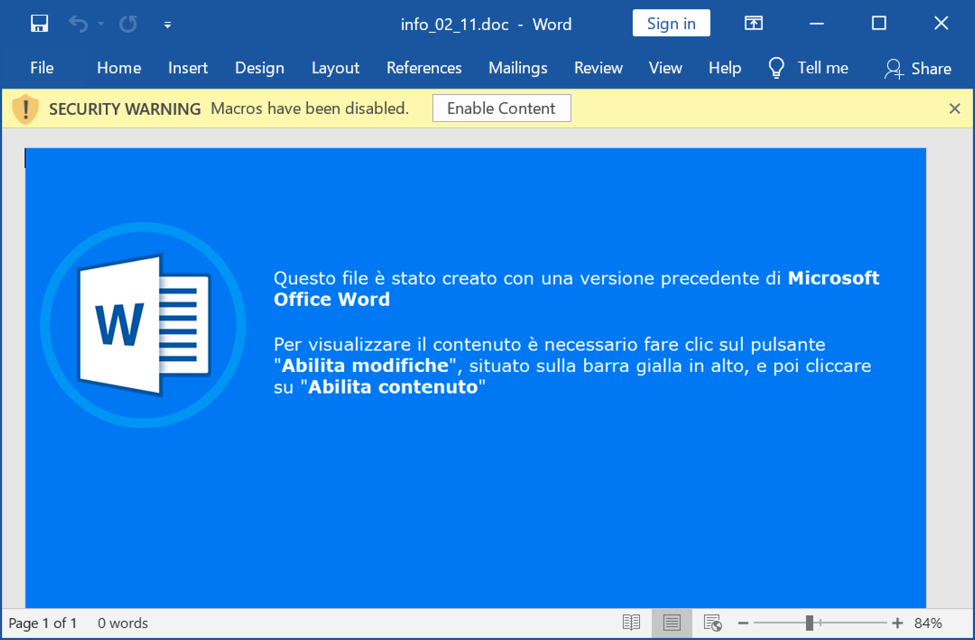
Shown above: Word document extracted from the password-protected zip archive.
Infection traffic
Infection traffic was typical from what I've seen with this campaign.
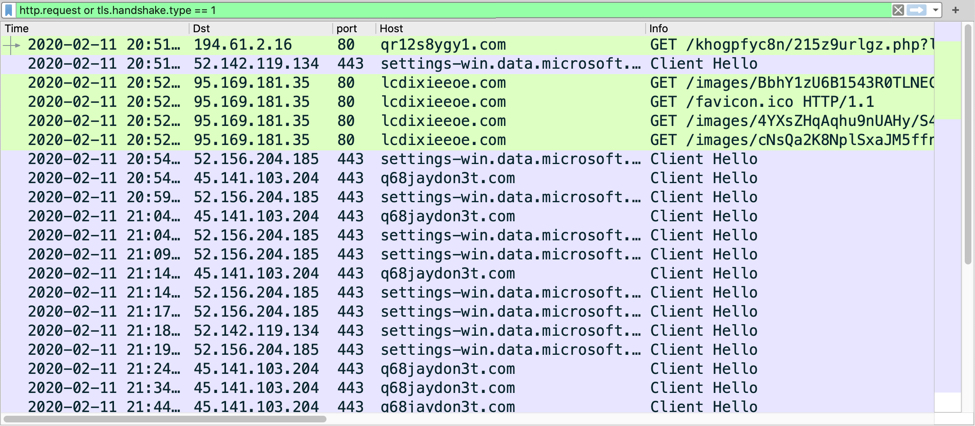
Shown above: Traffic from the infection filtered in Wireshark.
Indicators of Compromise (IoCs)
Traffic from an infected Windows host:
- 194.61.2[.]16 port 80 - qr12s8ygy1[.]com - GET /khogpfyc8n/215z9urlgz.php?l=xubiz8.cab
- port 443 - settings-win.data.microsoft.com - HTTPS traffic (not inherently malicious)
- 95.169.181[.]35 port 80 - lcdixieeoe[.]com - GET /images/[long string of characters].avi
- 45.141.103[.]204 port 443 - q68jaydon3t[.]com - HTTPS/SSL/TLS traffic caused by Ursnif
Associated files:
SHA256 hash: 28931260f23f2b669be6bd26ddb7f93cf75b2c2790373a3a45a34b09fa9ef907
- File size: 63,761 bytes
- File name: Genial.zip
- File description: Password-protected zip archive (password: 333)
SHA256 hash: 00d986b615d4082fe0ba0aa677b15eb97015f2b357ae87828be85b1e895e0d0b
- File size: 70,429 bytes
- File name: info_02_11.doc
- File description: Word doc with macro for Ursnif
SHA256 hash: 4268d7a5f33d411ab4c4fae7363b21755ad9e576e2094df18f3615399945fd41
- File size: 3,605 bytes
- File location: C:\Windows\Temp\a6c9p.xsl
- File description: XSL file dropped by Word macro
SHA256 hash: 996fcd8c55f923e86477d3d8069f9e9b56c6301cf9b2678c5c5c40bf6a636a5f
- File size: 188,416 bytes
- File location: hxxp://qr12s8ygy1[.]com/khogpfyc8n/215z9urlgz.php?l=xubiz8.cab
- File location: C:\Windows\Temp\aVQl7d.dll
- File description: Ursnif binary retrieved using XSL file
Final words
A pcap of the infection traffic along with the associated malware can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments