What is Listening On Port 9527/TCP?
Last week, Kevin wrote a diary about a marked uptick of port 34567. When I looked at some of the hosts scanning for it, I noticed that many of them are also scanning port 9527. So I put up a little honeypot for this port, and what I found is not the HTTP requests I expected (there are some vulnerabilities in webcam servers associated with this port). Instead, I found that it looks like the attacker is expecting an unauthenticated shell. Here is a typical set of commands:
/bin/busybox LA;
cd /var/tmp; echo -e "/bin/busybox telnetd -p9000 -l/bin/sh; /bin/busybox LA" > telneton; sh telneton;
The first command is a typical test if busybox is installed on the system. The attacker is expecting something like "LA: applet not found" back in return. Next, the attacker is creating a little script in /var/tmp/telneton. This script will be used to start the telnet server on port 9000.
I haven't found yet what the "next step" will be, but am waiting for incoming telnet connections on port 9000. So far I am just getting the usual "webcam" HTTP requests on port 9000 like
REMOTE HI_SRDK_DEV_GetHddInfo MCTP/1.0
CSeq:12
Accept:text/HDP
Func-Version:0x10
Content-Length:15
Segment-Num:0
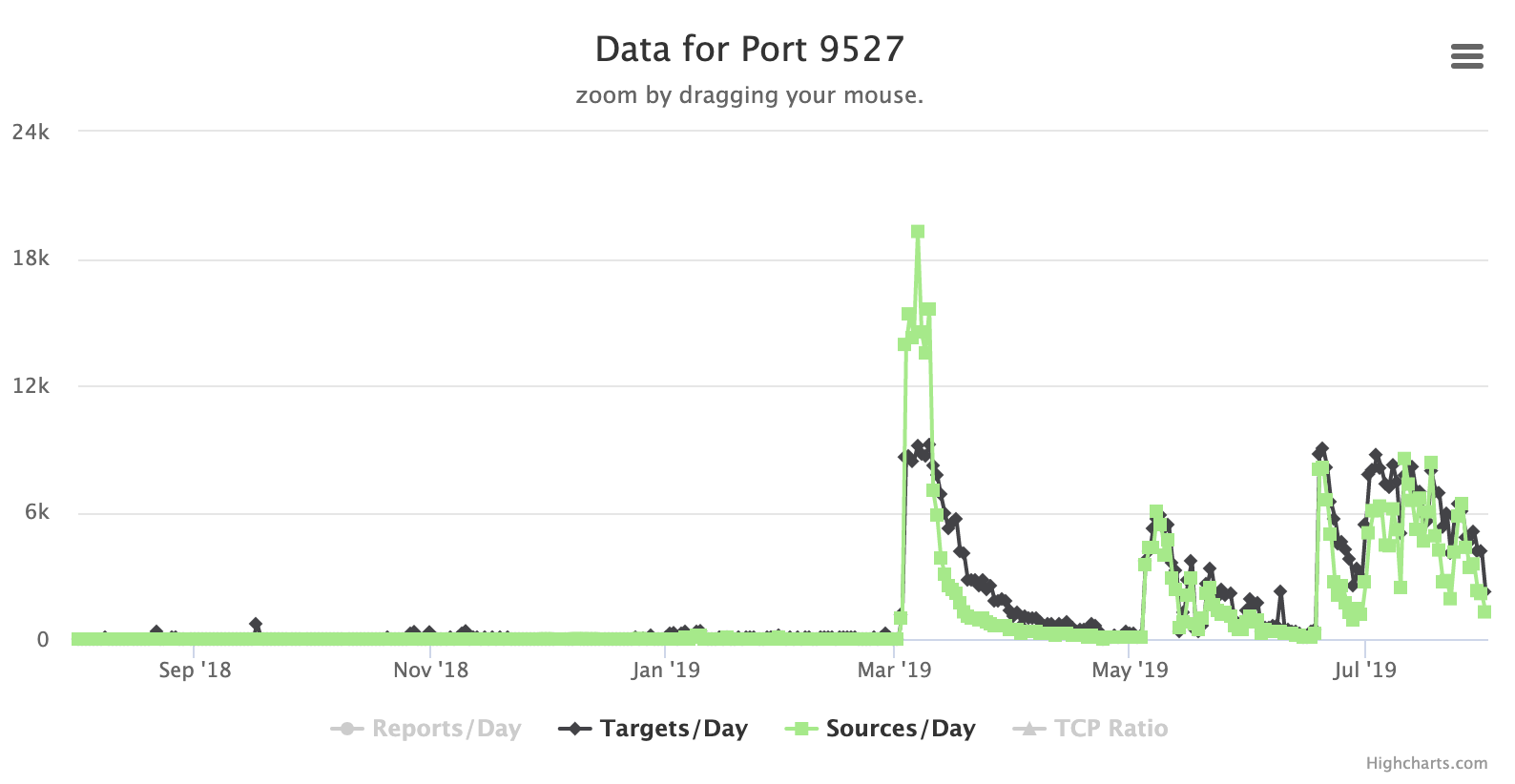
But I think these are unrelated. Scans for port 9527 had some interesting "decay patterns" over the last few months.
Let me know if you have any insight into this activity
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Aug 1st 2019
6 years ago
may i know what tools we are using for port activities please ?
Anonymous
Aug 2nd 2019
6 years ago