Can You Spell 2FA? A Luno Phish Example
This week, I am teaching our intrusion detection in depth class. Probably one of the more technical courses we have to offer, and it is fun to watch students in class getting the hang of "becoming one with the packet" and figuring out how all the bits and bytes align. A couple of doors down, one of my heroes, Doc Blackburn, is teaching probably one of our least technical classes: SEC301, Introduction to Cyber Security (don't tell him: But we sometimes call it security kindergarten). But truth be told, he probably makes more of a difference than all of our fancy technical classes. One of the things he is teaching this week is what "two-factor authentication" (2FA) means. You may remember that from your introduction to cybersecurity: Something you know... something you own... something you are... pick two of them. [2]
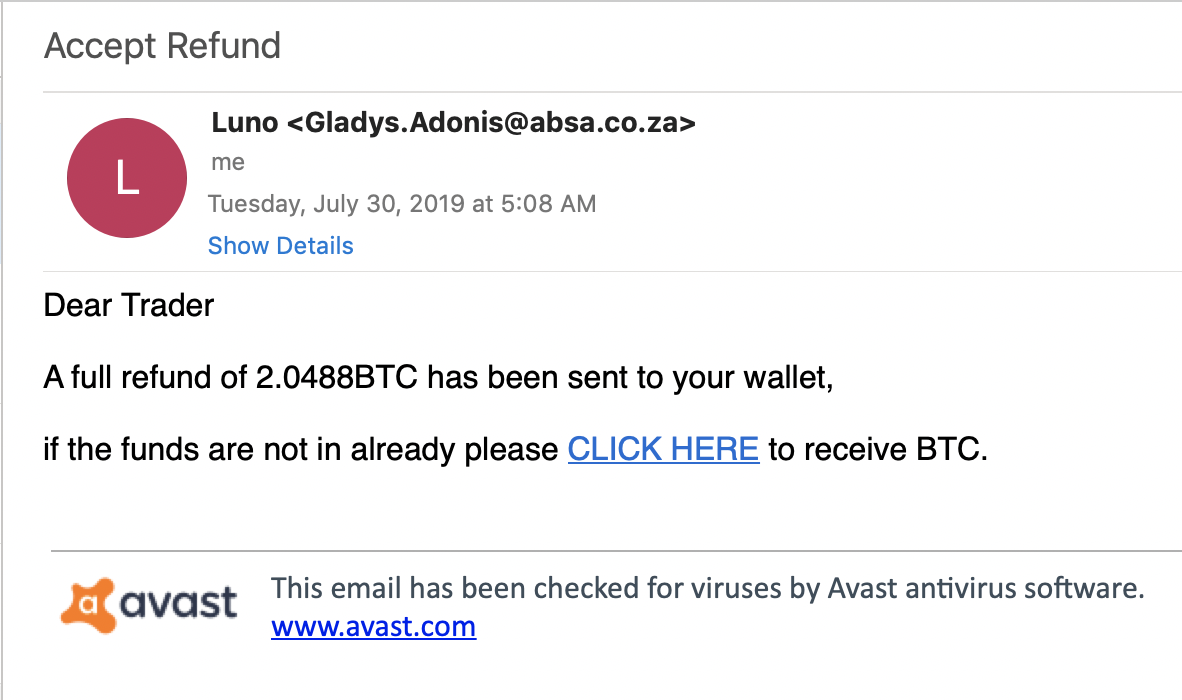
So why am I telling you about this? Earlier today, I received a simple, pretty straight forward and reasonably well-done phish for the Luno cryptocurrency exchange:
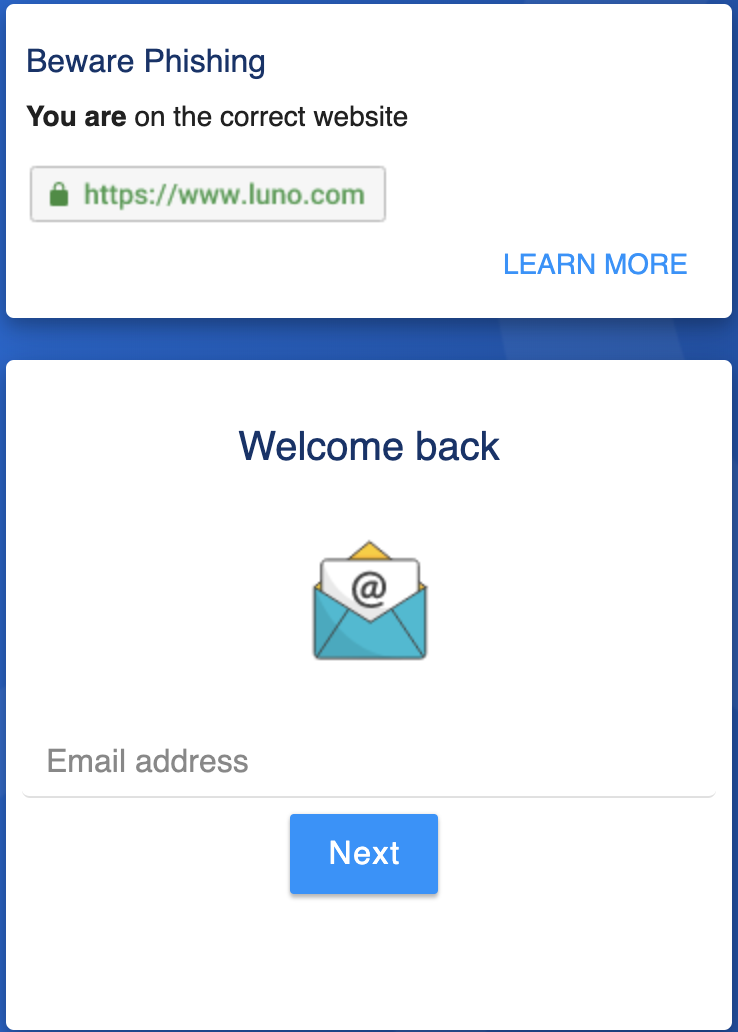
The email hit the typical phishing marks, including the fake Avast notice at the bottom, promising it to be safe. The link leads to hxxps:// rebrand .ly/5xb0pv, a link shortener, which redirects to hxxps:// psd. santana-communications.com/luniooo/. The phishing page looked pretty good. Here is an image of the fake and the real login page:
 |
|
The actual login page will offer an option to login via Google and Facebook. The phishing page doesn't provide these options. Also, note that the phishing page copied the cute warning to verify the URL.
The page will ask for the information twice, claiming that it wasn't entered correctly the first time. This is likely done to avoid typos, and maybe also to catch users that try to prevent phishing by first entering a wrong password to check if it is rejected.
Next, the phishing page will ask for the password as well as for a one-time password code. Great! So Luno uses two-factor authentication? Does the phishing page intercept the authentication and do "something fancy"? No... wait a second.
After asking for your Luno credentials, the phishing page will ask you for your e-mail credentials and phone number. ok... Maybe to be able to reset your credentials?
So I went ahead and signed up for a Luno account. First, the password policy isn't exactly "great." "Password123" was accepted just fine. It never asked me to set up a second factor, so I figured that this is an optional step to be completed after I sign in.
After verifying my email address, and signing in the first time, Luno announced that it would send a one-time password to my email address. Wait... didn't I "give" my email address and password to a phisher? This is why they need it! Luno's two-factor isn't two-factor. All I need is a second password (your email password).
Luno does offer an optional two-factor option that uses SMS. Probably why the phishing page asked for my phone number. However, it appears that this only enables sending the code via SMS in addition to e-mail, not instead of email, plus SMS should not be considered a "second factor" for high-value websites [3]. I am not totally opposed to SMS as a second factor (the phone is becoming what "you have"), but only for lower-risk applications, not for financial sites.
[1] https://www.luno.com
[2] https://en.wikipedia.org/wiki/Multi-factor_authentication
[3] https://pages.nist.gov/800-63-3/sp800-63b.html
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments