Secure Phishing: Netflix Phishing Goes TLS
Phishing for Netflix accounts isn't new. But recently, I see a large number of phishing e-mails for Netflix that lead to sites with valid TLS certificates.
The attack starts with a compromised website. The phishing sites I have seen typically run "the usual" suspect CMS software like Wordpress or Drupal. I haven't had a chance yet to look at a compromised site that was used by this type of phishing attack, but I expect either an unpatched install or plugin or maybe just weak passwords. There is no indication that the attacks use anything "fancy". In some cases, attackers then also take advantage of wildcard DNS records for the domain. With a wildcard DNS record, *anything*.domain.com will point to the same IP address. The attacker will just use a subdomain/hostname to launch the attack. But I have also seen them use specific domain names registered for the phish.
Next, the attacker obtains a TLS certificate for a hostname or the domain used in the phish. The hostname label is typically Netflix related. For example netflix.domain.com or netflix.login.domain.com. The attacker will then use this hostname to trick users to visit the malicious site.
The e-mails that are used to trick the user are the weak part of this exploit in my opinion. For example, here is one that I received on Tuesday:
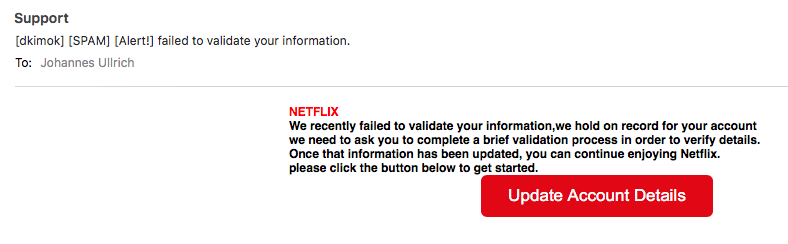
The e-mail was marked as spam, and the e-mail is not worded that well. In this case, the link went to hxxps://www. safenetflax .com , a domain registered just to impersonate Netflix. This domain no longer resolves.
Unlike the phishing e-mails, the websites look very much like the original. The only modification I can spot is that the alternative login methods like Facebook are missing. These methods would of course "spoil the phish." The attacker is interested in usernames and passwords.
The images below show the "real" and "fake" Netflix site:
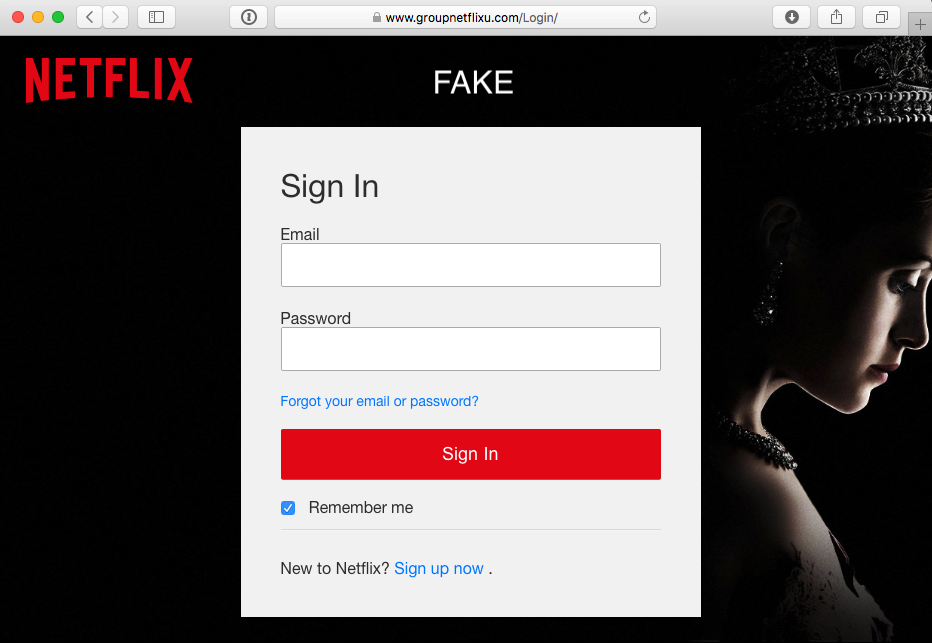 |
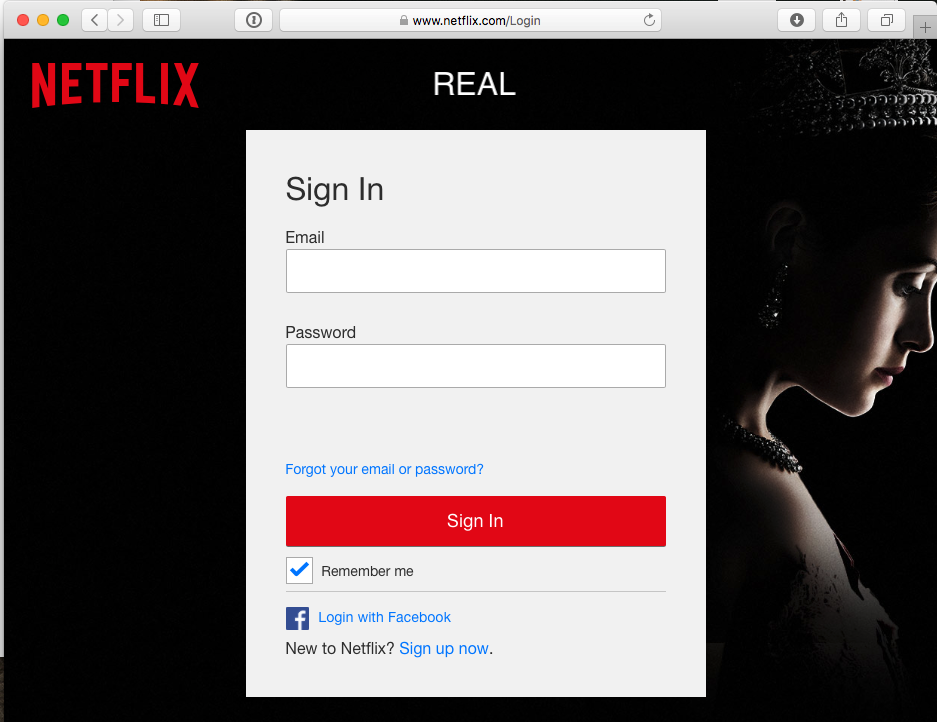 |
Why do attackers go through the trouble? Netflix accounts are not particularly valuable. I have seen them offered from $0.20-0.50 per account, and the prices quoted on public visible sites are not always accurate. But on the other hand, this attack can be automated quite nicely. The exploits used to attack the hosting site is likely automated. Next, "certbot" and the ACME protocol makes it cheap and easy to get the TLS certificate.
I think the attacker actually made a mistake in using TLS. I found the sites pretty easily via certificate transparency logs, and I think Netflix, or someone else, is doing the same thing as I saw these sites often labeled as "deceptive" by Google's safe browsing feature, before the phishing part of the site was life. I doubt many users would notice if the site didn't use TLS.
Once a Netflix account is compromised, it can often be used for a long time undetected as Netflix allows multiple simultaneous streams for its standard and premium accounts. Unless the legitimate user gets "kicked off" for using too many streams, the legitimate user will never know that there is someone else using their account.
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
If an attacker can find that a user/pass combo for Netflix also works on a more "valuable" target account, surely then the effort to steal Netflix creds becomes much more profitable.
Anonymous
Jun 21st 2018
7 years ago
Just found this weekened, that our german domain was used in phishing on
www.ourdomain.de-voucher.com . This was discovered thru Facebook. FB has a phishing detector that works from the CT logs. If your domain is inside a certificate you can get a warning.
Anonymous
Jun 27th 2018
7 years ago