HTTPS on every port?
Take a look at this Wireshark capture:
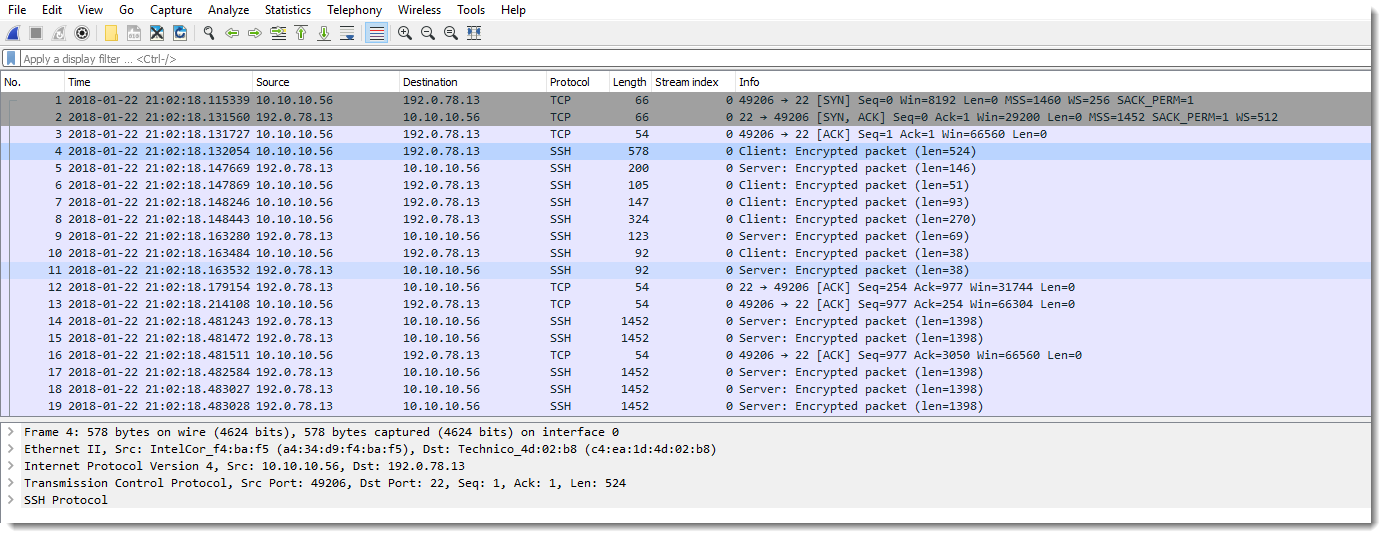
Wireshark dissects this as SSH traffic, but is it really?
Take a look at this Wireshark capture:
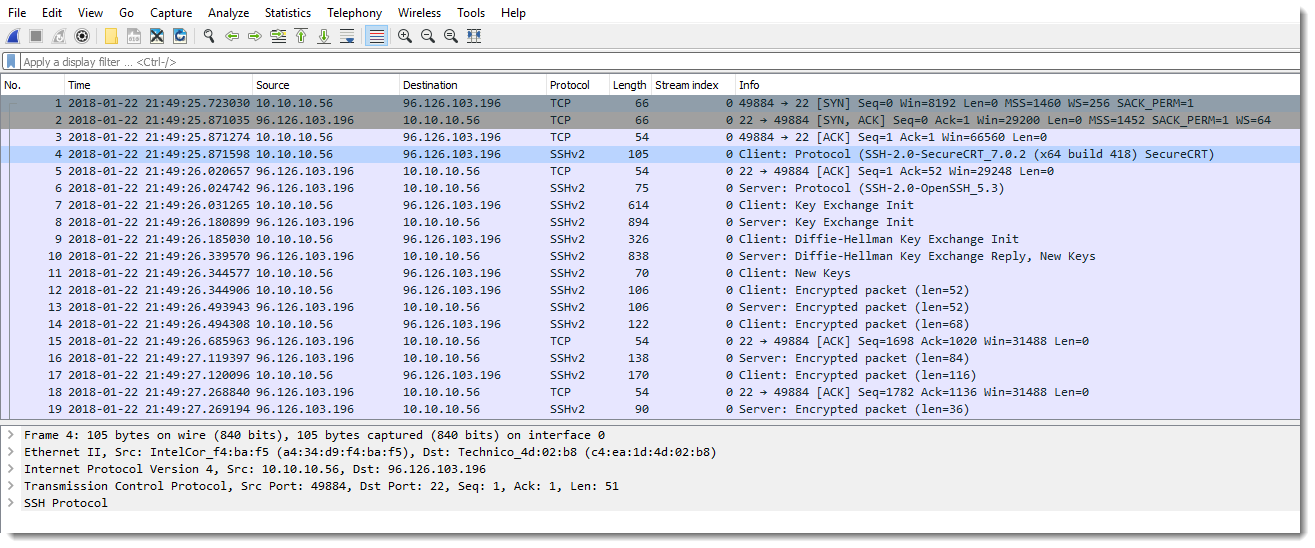
Here, you get more details for the individual SSH packets. So that first capture, is probably not SSH.
Wireshark will try to decode protocols based on several criteria, one of them is the port number. If the port is 22, Wireshark will try to decode the traffic as SSH, even it it is not SSH.
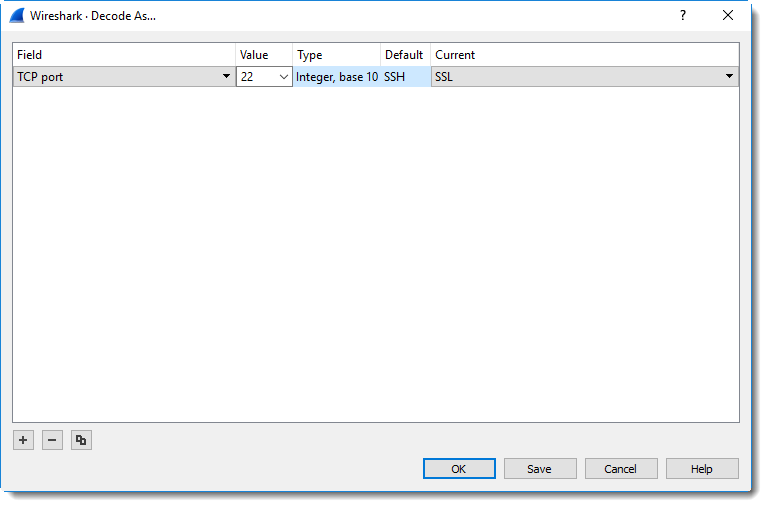
The traffic in the first capture is actually TLS. To get Wireshark to decode this traffic as SSL/TLS, you right-click a packet and select "Decode As...".
And then you configure Wireshark to decode traffic with port 22 as SSL:
And now, you get traffic that is properly dissected:
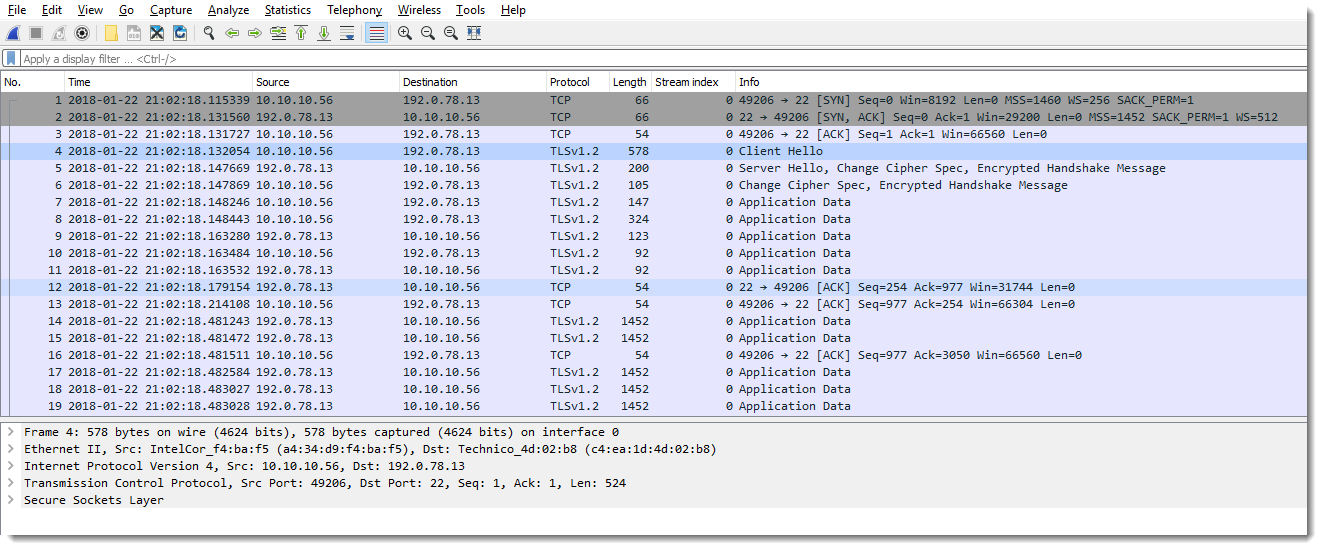
As SSL/TLS becomes ubiquitous, you can expect to find SSL/TLS traffic on non-standard ports. There are a couple of tricks to recognize SSL/TLS traffic: you might see a domain name or strings from the certificate in the first packets, or if you are "brave" enough to look at raw bytes, take a look at the second and third byte of data payload of each TCP packet. If these bytes are all 03 00, or 03 01, or 03 02, or 03 03, then you are most likely dealing with SSL/TLS traffic. These values represent the SSL/TLS version: SSL 3.0, TLS 1.0, TLS 1.1, TLS 1.2.
Using Decode As... is not a permanent change: this setting is discarded when Wireshark is closed.
If you want to make this permanent, you will have to go into the configuration of the dissectors. For example, for SSL/TLS you go to the configuration of the HTTP dissector: Edit / Preferences / Protocols / HTTP
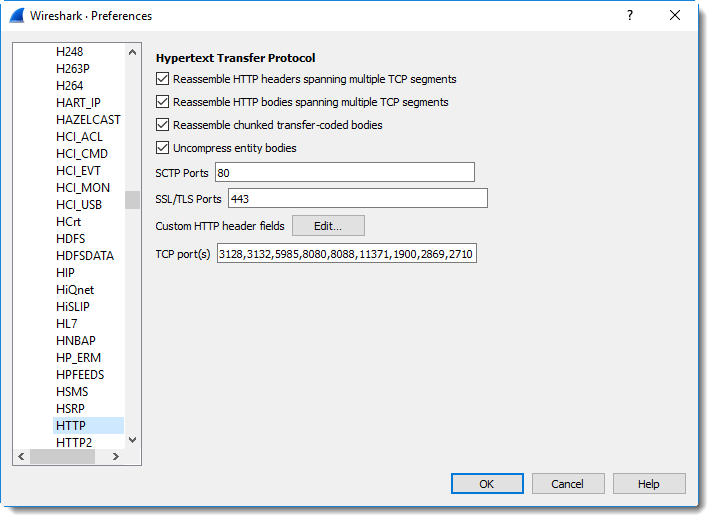
If you want to be able to quickly change decodings, I recommend you use different profiles: the default profile, and a second profile where you configure your custom ports.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments
it would perhaps look at the header and realize there are web requests there
Thanks again!
Anonymous
Jan 24th 2018
8 years ago