Using Your Password Manager to Monitor Data Leaks
I wrote this diary while waiting for my flight back to home. Last week, SANSFIRE was held in Washington where I met some ISC handlers. I did not pay too much attention to the security news but I faced an interesting story. Recently, a data leak affected LinkedIn and a friend of mine had a chance to have access to the data (o.a. decrypted passwords). He contacted my and suggested to change my password as soon as possible (as a proof, he sent my password). It was indeed a “valid” one but not my “current” one. More precisely, it was the very first password that I used when a created my LinkedIn account (a long time ago). Interesting… It means that the leaked is not recent.
Passwords are a sensitive topic: don’t play with fire and follow this golden rule: Change them often and don’t re-use them. The “leak” which affected TeamViewer is a good example. I put leak between quotes because it appeared that some of their users were compromised due to password re-use as they stated. To track and analyze this, password managers and dormant accounts can be very useful to track data leaks.
Usually, when I receive an invitation to create an account on a website, I accept it and create a unique email account that will NEVER be used somewhere else. I'm using something like: "website-url (at) unused (dot) rootshell (dot) be" or “login_webshop.com". This helps me to track:
- Spammers: I can “learn” which site leaked (or sold?) my details to spammers.
- Data leaks: By crawling paste websites for my dormant email addresses or logins.
Another interesting feature of some password managers (well, the one I’m using includes it), they keep a history of the previous passwords and time stamps (when they have been changed):
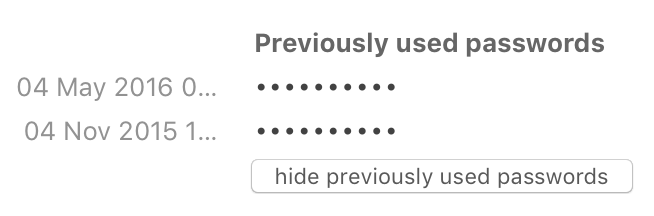
Based on this information, I’m able to estimate when the data leak really occurred and if it is really coming from the supposed victim or from another source. This is a new proof that password managers are mandatory for everybody: they protect you and they contain useful data to analyze security incidents. Stay safe!
My next class:
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |
×
![modal content]()
Diary Archives


Comments
An example problem with this approach came when Microsoft, working with the government, took away my domain (I posted my experience in this forum, in fact, https://isc.sans.edu/forums/diary/Microsoft+NoIP+Takedown/18329). I have since converted to my own .COM (but a lot of my old e-mail addresses are still in use; it's a slow conversion), which I assume is safe from "hostile takeovers."
Anonymous
Jun 20th 2016
9 years ago
On Gmail or with google apps, you can use +: username+whatever@gmail.com. Unfortunately this is less universal because many sites won't let you use + in the email field because they have really poorly written validation code that won't accept it.
Anonymous
Jun 20th 2016
9 years ago
first.last@gmail.com = firstlast@gmail.com
Anonymous
Jun 21st 2016
9 years ago
Anonymous
Dec 8th 2016
9 years ago