Quick Howto: ZIP Files Inside RTF
In diary entry "Quick Howto: Extract URLs from RTF files" I mentioned ZIP files.
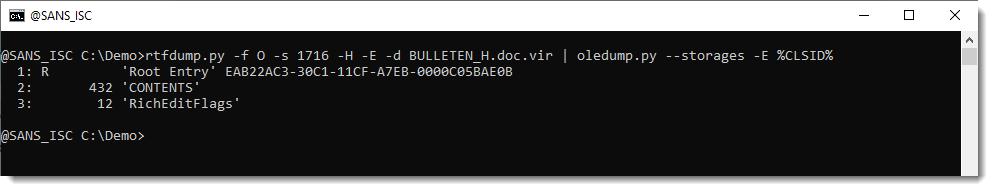
There are OLE objects inside this RTF file:
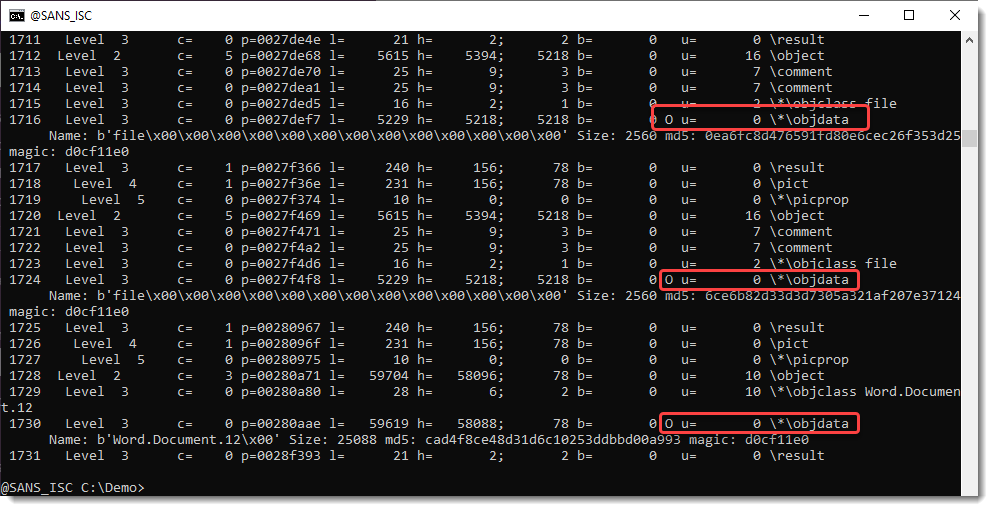
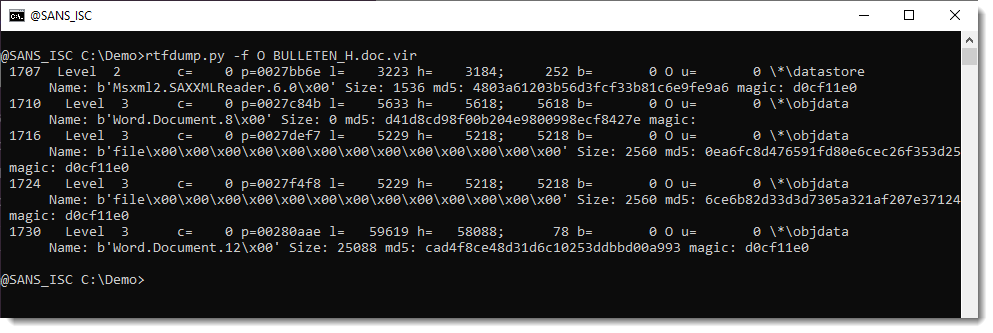
They can be analyzed with oledump.py like this:
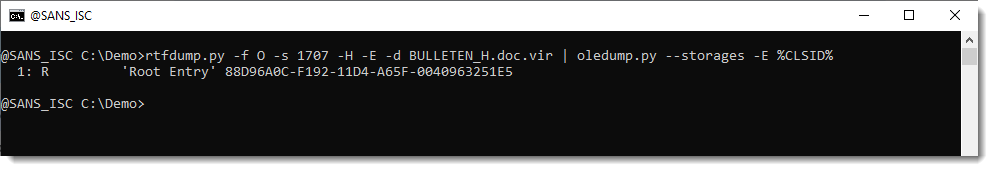
Options --storages and -E %CLSID% are used to show the abused CLSID.
Stream CONTENTS contains the URL:
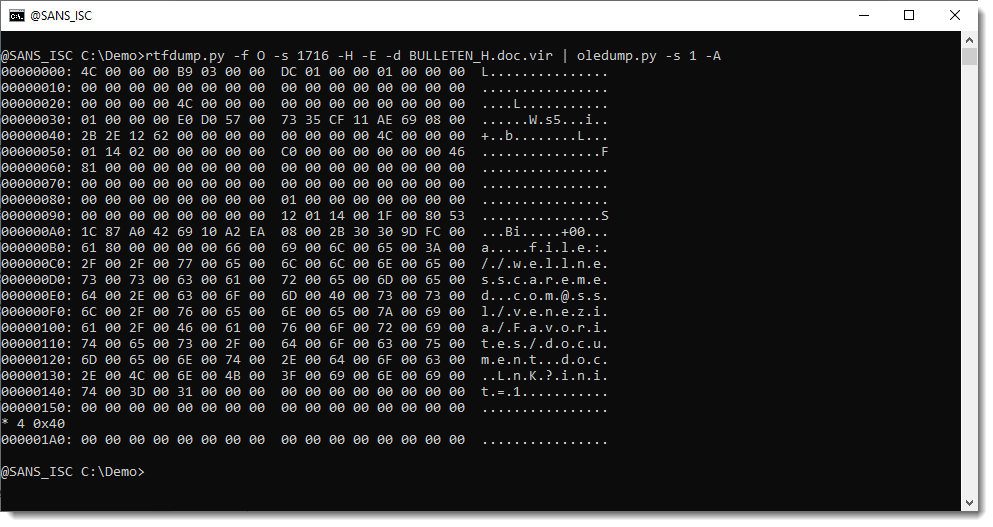
We extracted this URL with the method described in my previous diary entry "Quick Howto: Extract URLs from RTF files".
But this OLE object contains a .docx file.
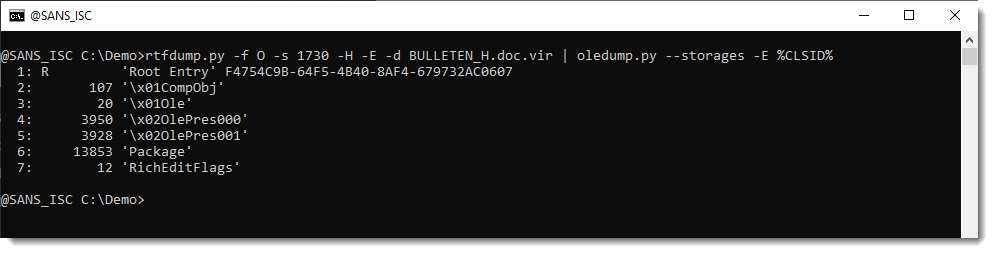
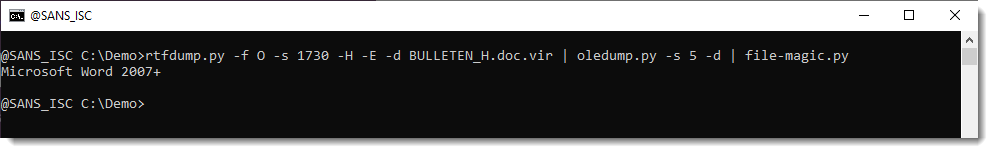
A .docx file is a ZIP container, and thus the URLs it contains are inside compressed files, and will not be extracted with the technique I explained.
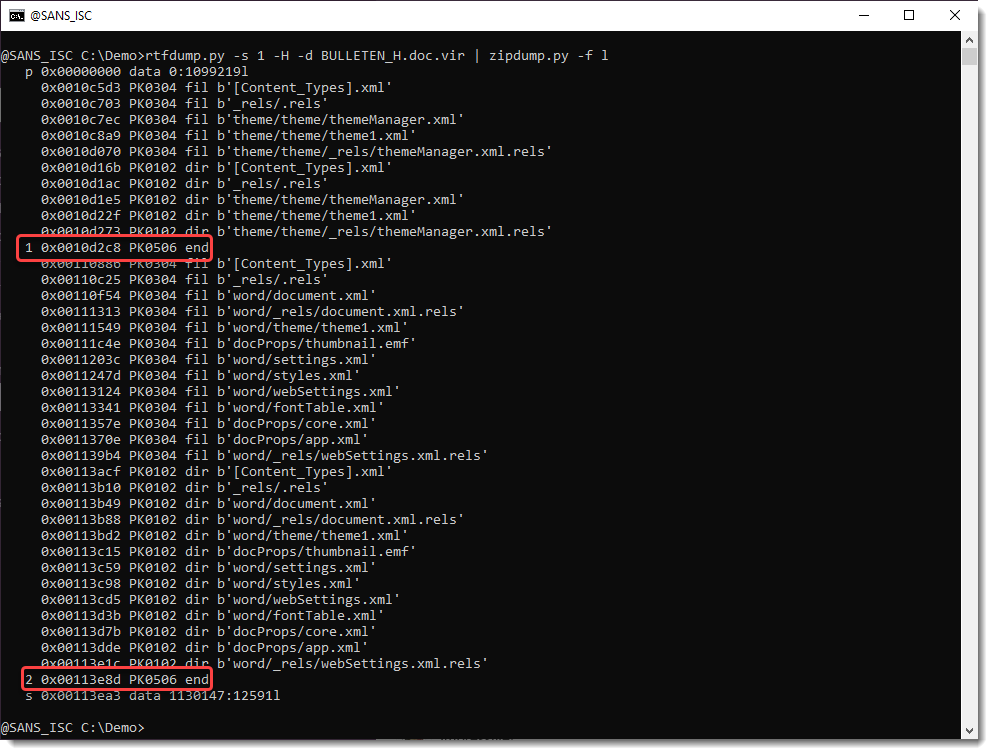
But this file can be looked into with zipdump.py:
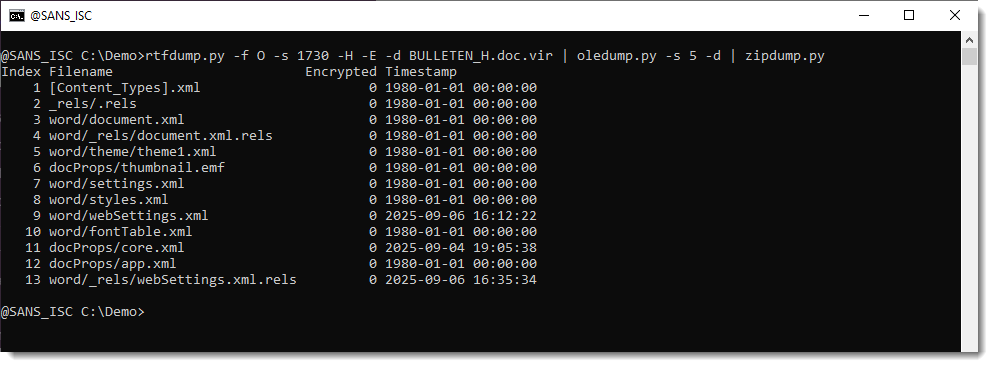
It is possible to search for ZIP files embedded inside RTF files: 50 4B 03 04 -> hex sequence of magic number header for file record in ZIP file.
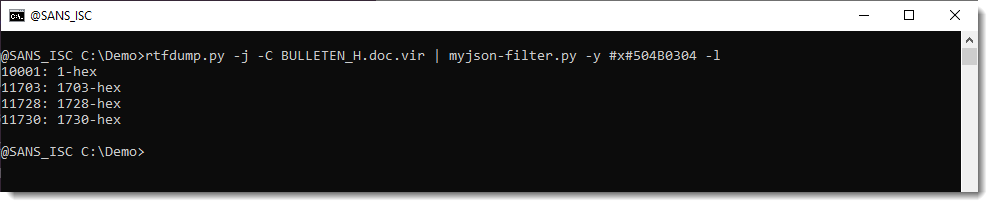
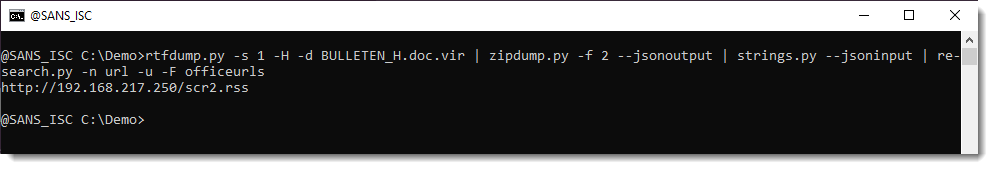
Search for all embedded ZIP files:
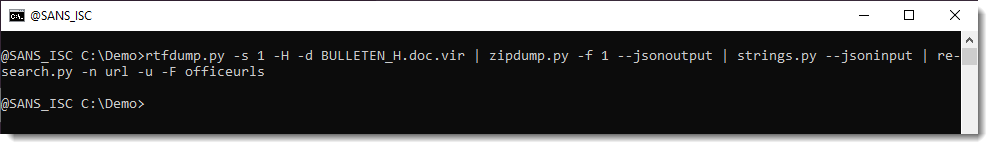
Extract URLs:
Didier Stevens
Senior handler
blog.DidierStevens.com
Wireshark 4.6.4 Released
Wireshark release 4.6.4 fixes 3 vulnerabilities and 15 bugs.
Didier Stevens
Senior handler
blog.DidierStevens.com


Comments