F5 BIG-IP Unauthenticated RCE Vulnerability (CVE-2022-1388)
TL;DR: Patch your BIG-IP and disconnect the management interface from the internet. Now.
Last week, F5 released an update to its BIG-IP product, patching a vulnerability affecting the iControl REST API. https://support.f5.com/csp/article/K23605346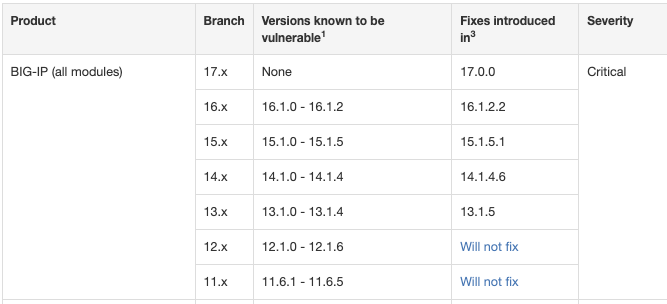
The vulnerability is noteworthy as it does allow unauthenticated attackers to execute arbitrary system commands, create or delete files, or disable services. The attacker, in other words, gains complete control over the affected device.
But the vulnerability does require access to the management port or "self IP addresses." We had a similar severe BIG-IP vulnerability about two years ago, CVE-2020-5902. It, too, was only exploitable via the management interface. I noted, "certainly make sure that the management plane is not exposed to the public Internet. Who knows when the next vulnerability in this feature will be found!". Well, this is the next time. If you didn't listen back then, you will probably not listen now, and you will probably not be reading blogs like this. But here we go again. So let's summarize some of the details:
Affected Devices: Everything older than BIG-IP 17. Patches are available for BIG-IP 13-16. BIG-IP 11 and 12 are vulnerable but too old to be patched.
Two groups announced on Twitter that they had developed exploits, and one stated that they would release an exploit publicly this week. Some noted scanning for BIG IP, but it isn't clear if there is widespread scanning using the exploit, or just finding exposed BIG IP administrative interfaces.
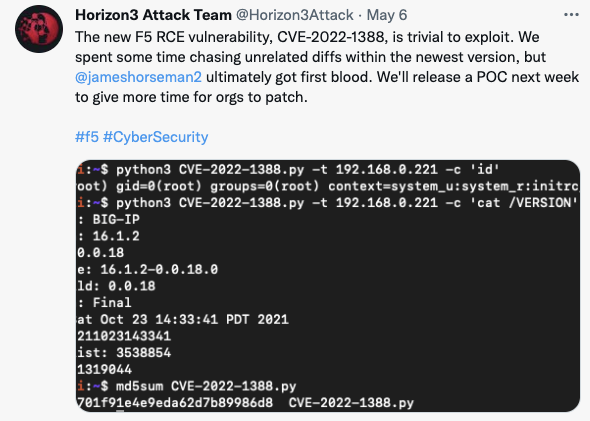
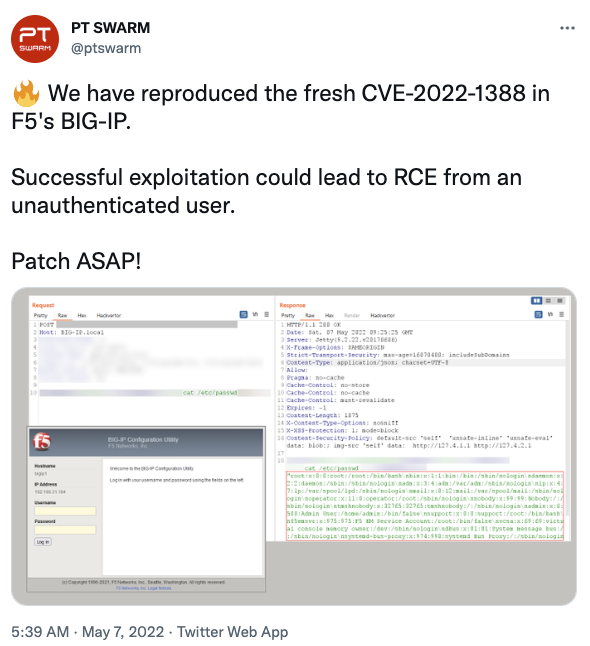
So what should you do?
Usually, I recommend patching first and later attending to the configuration issues. But in this case, I will swap this order: First, make sure you are not exposing the admin interface. If you can't manage that: Don't try patching. Turn off the device instead. If the configuration interface is safe: Patch.
A bit of Googling will lead you to excellent configuration guides like https://github.com/dnkolegov/bigipsecurity/blob/master/README.md . But if all fails: I hear that there may be a manual and help pages provided by F5. If you tossed it when you first unpacked the device: They got it online!
How big of an issue is this? There are not a lot of these devices exposed, luckily. The numbers are a bit "all over," but likely around a thousand. Censys lists 2,555 (https://search.censys.io/search?resource=hosts&sort=RELEVANCE&per_page=25&virtual_hosts=EXCLUDE&q=services.http.response.html_title%3A+%22BIG-IP%26reg%3B-+Redirect%22+ ) Shodan shows 534,051 if you search for BigIP, but this isn't just the management interface. These are also websites behind BIG IP load balancers.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments