Sooty: SOC Analyst's All-in-One Tool
Sooty was developed with the intent of helping SOC analysts automate parts of their work flow. Sooty serves to perform the more mundane and routine checks SOC analysts typically undertake with the hope of freeing the analyst to conduct deeper analysis in a more efficient and timely manner.
Download or clone Sooty from its GitHub repository.
I cloned Sooty into my tools directory with git clone https://github.com/TheresAFewConors/Sooty.git. You’ll need a current implementation of Python 3.x, and be sure to pull in Sooty’s requirements with pip install -r requirements.txt, I was missing a number of them. You’ll also need drop your API keys into their assigned slots in example_config.yaml and rename it config.yaml. The GitHub repo Requirements and Installation section has links for each of the services you’ll want API keys for, and a few pointers for setting them up properly.
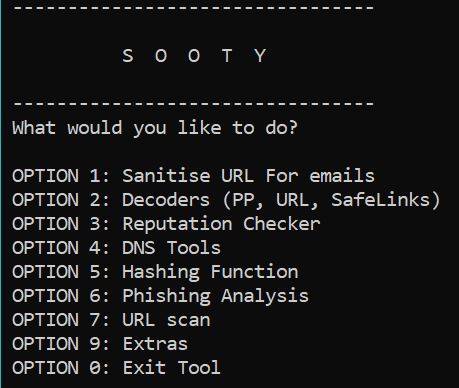
Thereafter, python Sooty.py will get you started. Figure 1 represents the menu you’ll be presented with.
Figure 1: Sooty menu
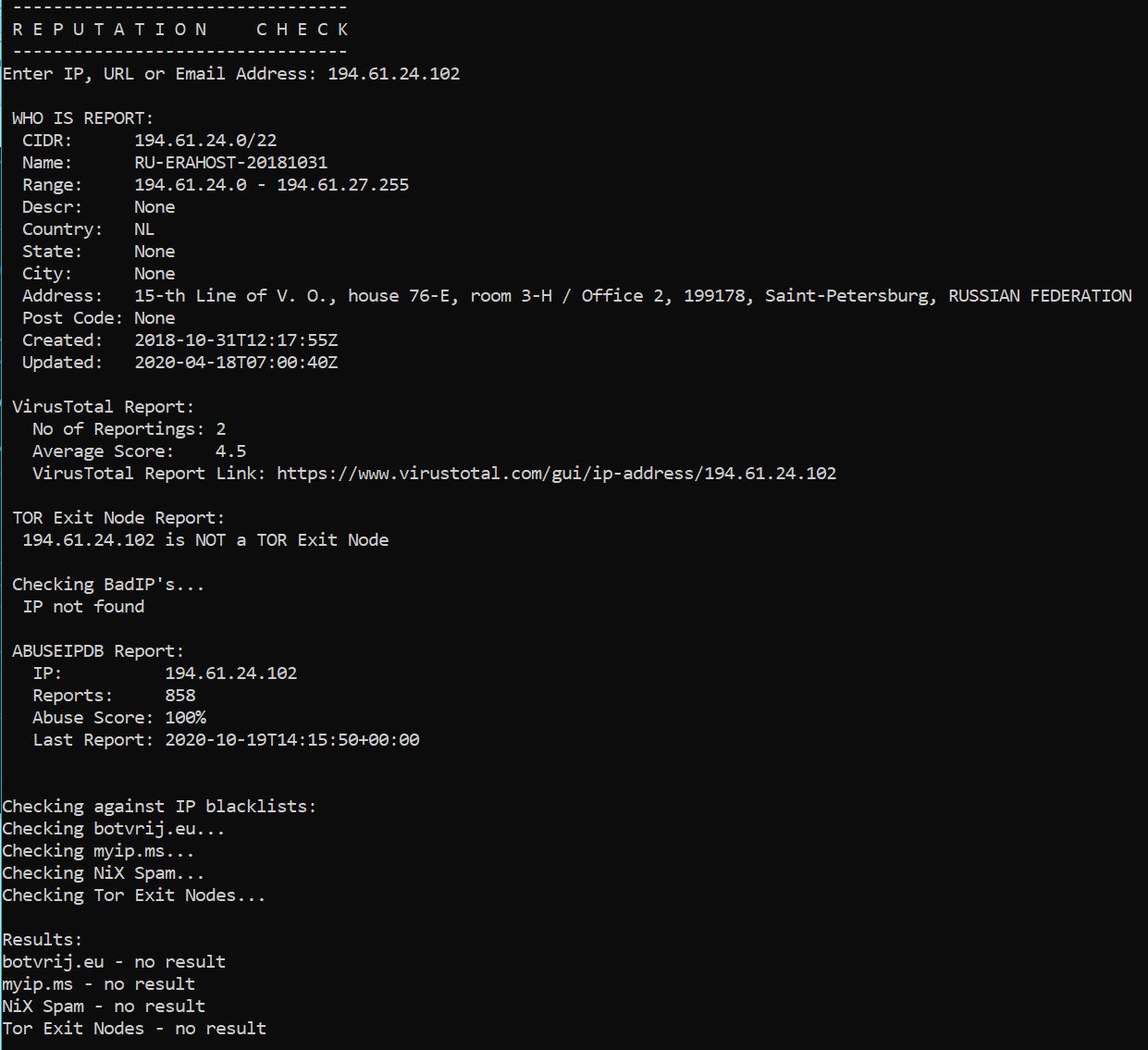
I’ve had the recent pleasure of hunting duties and Sooty went to immediate use for preliminary assessment purposes. An instant IP reputation result is seen in Figure 2.
Figure 2: Sooty IP reputation
Suffice it to say, don’t count that IP on the good guy list.
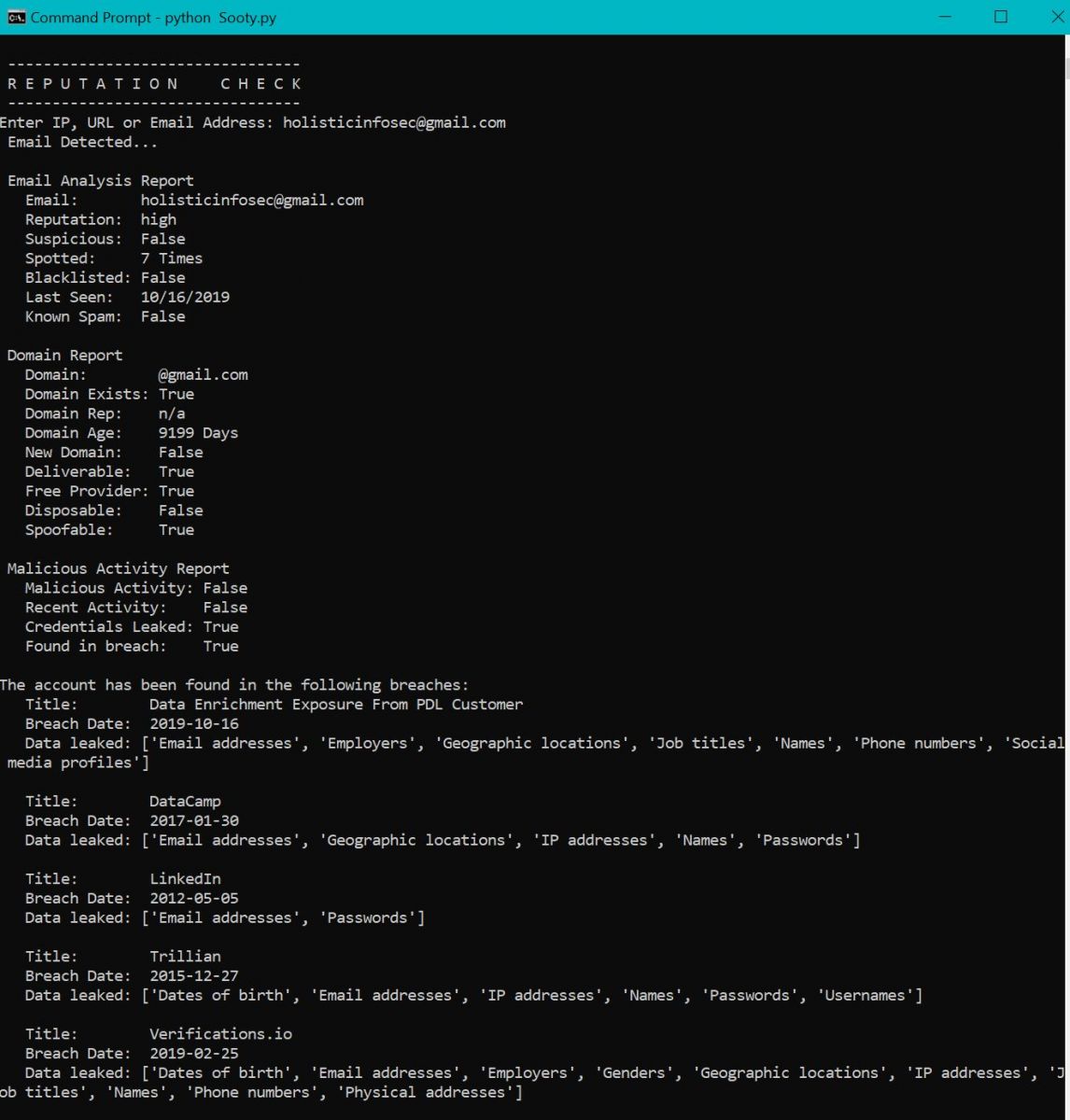
Figure 3 exhibits a check of one of my email addresses.
Figure 3: Sooty email reputation
The email reputation check includes Have I Been Pwned results, you can see the answer to that question is affirmative.
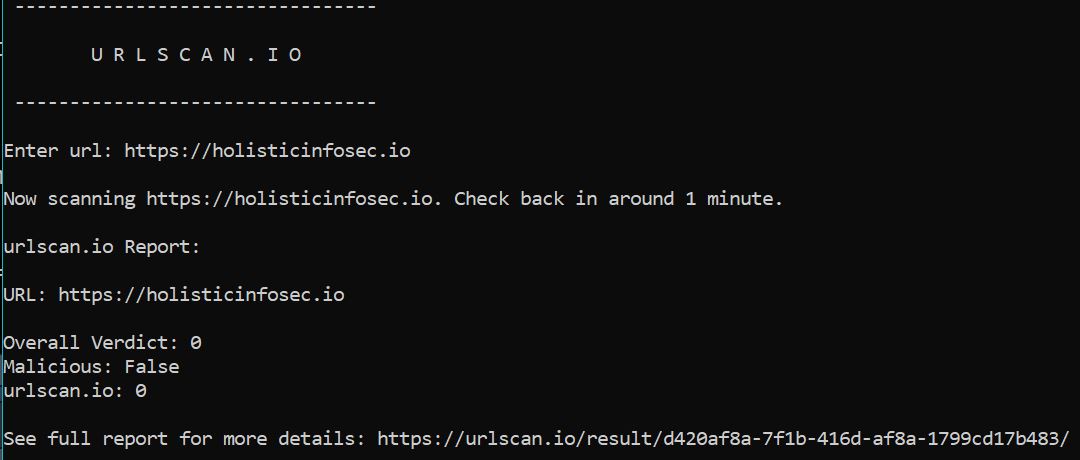
Sooty option 7 will run URLs through urlscan.io as seen in Figure 4.
Figure 4: Sooty urlscan
The decoders, DNS, and phishing checks are handy for…you know…decoding, DNS, and phishing checks as follows.
Decoders: ProofPoint, URLs, Office SafeLinks, URL unShortener, Base64, and Cisco Password 7.
DNS: Reverse DNS, DNS, and WHOIS lookups
Phishing: Analyze Email, Email Addresses for Known Activity, Generate an Email Template based on Analysis, Analyze an URL with Phishtank, and HaveIBeenPwned
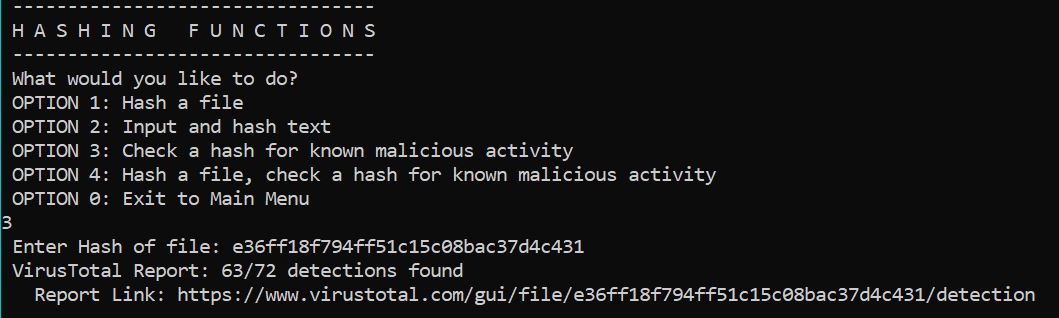
I’m also fond of the hashing functions, particularly Option 3: Check a hash for known malicious activity. As seen in Figure 5, Sooty calls the VirusTotal API, and results are returned very quickly.
Figure 5: Sooty hash check
This is an incredibly handy, convenient tool, it really does deliver as promised, I can vouch for it during real operations, not just toolsmith lab time. I do hope support continues for it. Give it a go and enjoy!
Cheers…until next time.


Comments