Finding the Gold in a Pile of Pennies - Long Tail Analysis in PowerShell
It is said that one piece of Information is like a penny, it’s value is small until it is combined with thousands of other pennies (or nickles, dimes or whatever). This is certainly true when we collect the windows process list or the output of netstat -naob across a domain (the last two stories I've written up) - any single line is of limited value. But once you combine everthing together, it's easy to find trends, or in the case of the Windows process list, outliers - items that only occur on a few stations.
Luckily it is fairly easy in PowerShell to sort this information so that the outliers are easily seen - in a large domain for instance, you might be looking for the windows process hash value that only exists on 1,2 or maybe up to 5 hosts.
This is pretty easy to do - we'll use the Powershell Group-Object command. Working with the domain task list from yesterday, first "group" the list by the hash value:
$DomainTaskList | select pscomputername,filehash,name | Group-Object -Property filehash
Then, sort by "count" (with no arguments, the sort is ascending:
$DomainTaskList | select pscomputername,filehash,name | Group-Object -Property filehash | sort count
Then, select processes that occur on "less than or equal to 2" hosts:
$InterestingHashes = $DomainTaskList | select pscomputername,filehash,name | Group-Object -Property filehash | sort count | where-object {$_.count -le 2}
Or, alternatively, "pick the first 10 in the list"
$InterestingHashes = $DomainTaskList | select pscomputername,filehash,name | Group-Object -Property filehash | sort count | select-object -first 10
Verify that the output looks good:
$InterestingHashes | ft -AutoSize
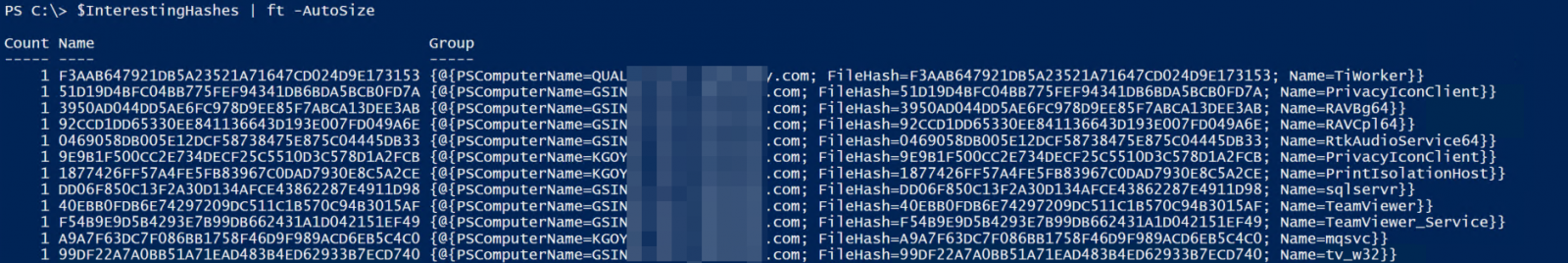
Finally, output to CSV - even in a small domain, on a "first run and clean-up" situation there's usually just too many of these one-offs to list on the screen and deal with.
$InterestingHashes | output-csv "HashesToInvestigate.csv"
Now you can see the value of saving up pennies - what falls out of this exercise is often pure gold!
What did we find? Looking at our output, we can see a few things off the bat that we should look closer at:
- Multiple versions of TeamViewer. This is generally OK if IT knows about it, but most instances were in other business units.
- Every server "thing", which for this client meant some BAAN stuff, a SQL Server and one old Domino server that hadn't been retired yet
- A few ancient versions of Word and PowerPoint - the hashes across the board for these should match if everything is at the same version and are patched up. So finding multiple hashes for WinWord, each as a singleton is a bad sign.
- Multiple windows machines that weren't up to date on patching - several one-off versions of igfxEM, ZeroWireless_Config, wlanext and "IntelCp" processes on desktops with the same OS for instance indicates this
- A few people still running the Domino client (these were all supposed to be retired)
- JavaWS was installed and actually running on a Domnain Controller (oops)
So some things to fix, but no malware - great news!!
If you have a chance to run something like this scan (or if you already have), please use our comment form and let us know if you found anything interesting (good, bad or ugly, let us know!)
===============
Rob VandenBrink
Coherent Security


Comments