"When was this machine infected?"
When responding to a malware incident, important questions to be answered are "How was the machine infected?" and "When was the machine infected?".
I encountered a sample that made the work of analysts a bit lighter in this regard.
While browsing through the code of a H-worm variant, I noticed that this worm creates a registry entry with the method and date of infection, and communicates this to the C2 server.
Here is the code:
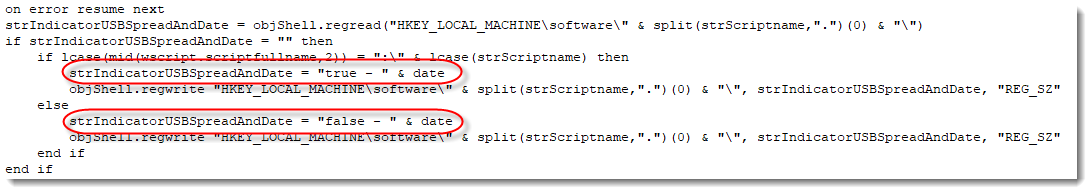
The string strIndicatorUSBSpreadAndDate (a name I chose) will be set to "true - DATE" when the machine is infected via an USB stick, and to "false - DATE" when it is not.
This string is written to the registry:
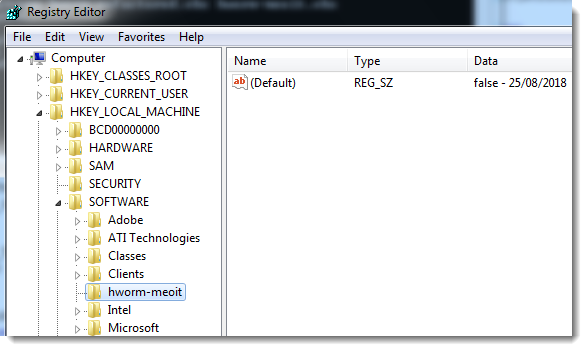
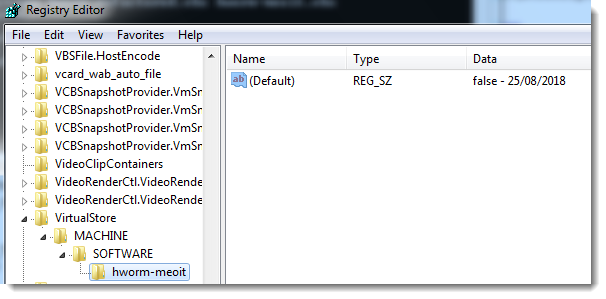
The name of the registry key varies: it's the name of the .vbs file (hworm-meoit is a name I chose). It will be under HKEY_LOCAL_MACHINE\Software if the script was executed (elevated) by an administrator, and under the registry virtualization keys when executed by a normal user:
This value is also communicated to the C2 server with every HTTP POST request (inside the User Agent String header):
.png)
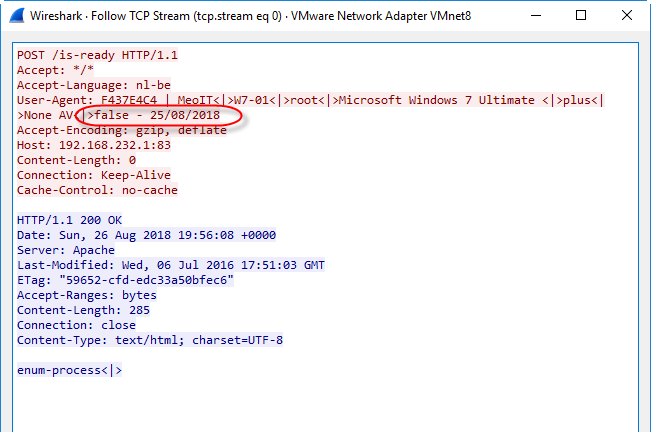
Of course, one would still look at other evidence when establishing a timeline.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments