Stop calling it a ransomware "attack"
2016-08-07 update: I've posted a follow-up diary [link] that includes information on targeted attacks that do involve ransomware.
Introduction
I dislike the term "ransomware attack." Why, you ask? It's a matter of perception.
The word "attack" indicates specific intent against a particular individual or group. An attack means someone (or something) is targeted. But I'm hesitant to use the terms "attack" and "targeted" when discussing ransomware. Calling a ransomware infection an "attack" focuses blame on an enemy. I consider this mindset dangerously close to fear mongering.
If we continue thinking of ransomware infections as "attacks," we'll never seriously consider a wide variety of issues that allow ransomware infections to happen in the first place.
Ransomware distribution
Ransomware is distributed on a large scale. Criminal groups generally use two methods to distribute malware: malicious spam (malspam) and exploit kit (EK) campaigns. These are most often large-scale operations that attempt to reach as many potential victims as possible.
I view EK campaigns as laying a bunch of mousetraps throughout the web. An EK is not an active attack against a specific victim. People stumble across EKs through casual web browsing. Personally, I've never found any convincing evidence that ransomware infections through EK traffic have been targeted.
But what about malspam, you ask? You might think someone receiving an email with ransomware was targeted. However, I find it hard to believe the massive waves of malspam I sometimes look into are targeted against specific individuals. Especially when it's Locky ransomware, which is widely distributed [1, 2, 3]. When someone's email address is discovered by a spammer, it gets on a list. That list is often shared, and the person's email address will be constantly bombarded by wave after mindless wave of botnet-based malspam.
Ultimately, I believe ransomware infections are the result of large-scale campaigns covering numerous potential victims, and a comparatively small number of people actually get infected.
Yes, those relatively few infections often have major consequences, but they're not the result of narrowly-defined attacks. They're the result of large-scale campaigns. The important part isn't necessarily who is infected. The important part is that enough people with enough resources are infected to make it profitable for the criminals.
Shown above: Roberto probably said, "It's got my name in it, so it must be targeted!"
Assigning criminal intent based on statistics
During my day-to-day research, I usually see ransomware. I also see the malspam and EK vectors this malware comes through. But we should not make any assumptions of criminal intent based on the data we collect. Why? Because no matter how wide we cast our net, we'll never know the full truth.
I still read such reports. The latest one I looked at was based on a July 2016 Osterman Research survey about ransomware [4]. It's typical of what I've been seeing lately. The report states that healthcare and financial services are the industries most vulnerable to ransomware attacks. According to the report, "These industries are among the most dependent on access to their business-critical information, which makes them prime targets for ransomware-producing cyber criminals."
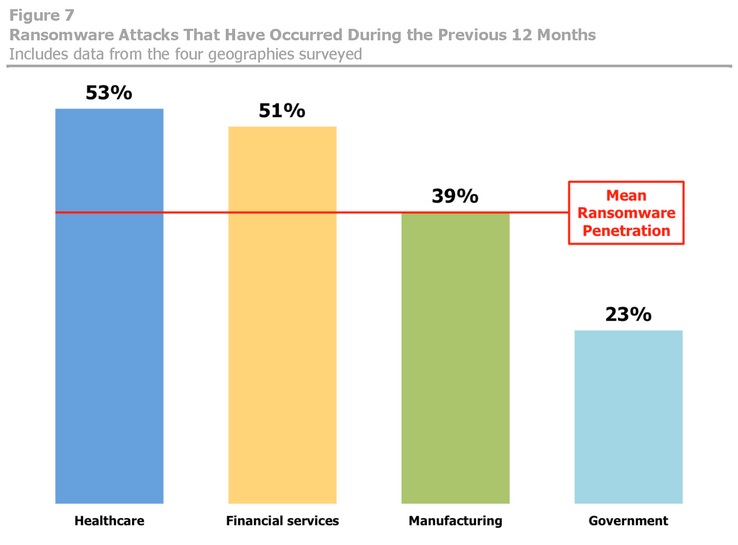
Shown above: One of the charts from the Osterman report.
I enjoyed reading the report. It has some good insights. But whenever I see these statements, I always wonder if those industries are really targeted more than other industries. Or did they have more infections because they're inherently more vulnerable? If they're indeed the most vulnerable, wouldn't it follow they're more likely to get infected during massive campaigns indiscriminately targeting everyone?
Like the large-scale EK or malspam campaigns spreading ransomware I see every day?
I don't know how to describe this. We're saying certain industries are targeted more because they're getting infected more. That just feels wrong. Ransomware doesn't need to be targeted if it's widely distributed.
Yet everyone and their mother are calling these ransomware attacks.
Final words
We tell ourselves we must know our enemy so we can better protect our network. However, I think we put too much focus on the enemy and not enough focus on ourselves.
Is everyone in your organization following best security practices? Is security a truly essential part of your corporate culture? Is security a primary concern when establishing or upgrading your network architecture, or does cost outweigh the best security measures? Most organizations have problems in these areas. We convince ourselves there are certain weaknesses we must live with.
And management really wants to know who was behind that ransomware infection and why your organization was apparently targeted.
But odds are the ransomware was directed at any number of people who either stumbled across it or were unlucky enough to find it in their inbox.
Sure, call it a ransomware incident. Just don't call it a ransomware attack.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://www.fireeye.com/blog/threat-research/2016/03/surge_in_spam_campai.html
[2] https://www.proofpoint.com/us/threat-insight/post/Locky-Ransomware-Cybercriminals-Introduce-New-RockLoader-Malware
[3] http://researchcenter.paloaltonetworks.com/2016/07/unit42-afraidgate-major-exploit-kit-campaign-switches-from-cryptxxx-ransomware-back-to-locky/
[4] https://go.malwarebytes.com/OstermanRansomwareSurvey.html



Comments
Anonymous
Aug 7th 2016
8 years ago
I am working as a freelance writer for quite some time now, and I am usually writing about cyber security, technology innovations etc. So I got an invitation from a certain company from Coppell, TX to write an article for their blog. The proposal was sent via one of the largest platforms for freelancers, and I had a long discussion with their marketing manager, who referred me to their editor. This person added me on Skype and, after a short introduction, she sent me a .zip file with "writing guidelines."
<blockquote class="imgur-embed-pub" lang="en" data-id="a/xgrhh"><a href="//imgur.com/xgrhh"></a></blockquote><script async src="//s.imgur.com/min/embed.js" charset="utf-8"></script>
When I opened the file, I found a .PDF document with the actual writing guidelines, and a couple of additional files that looked suspicious at first, but seemed to be their company's policy and additional guidelines. I actually asked this person what kind of a file is this, and jokingly asked if she is trying to send me a virus, since the file was .exe She convinced me to try and open the link, assuring me that this is just a format that they use for on-boarding new workers... So I did. I soon realized that this software is triggering my processes and I quickly disconnected my computer, but it was too late. My computer was infected.
Ironically, I write about this type of stuff daily, and now I became a victim myself. The thing that surprised me the most is the fact that when I contacted this freelancing service (which will remain unnamed), and they told me that they "don't know why, but that company's profile has already been suspended." Apparently, they aren't doing anything to prevent this type of malicious behavior, they just deal with it once the damage is already done, and they don't pay too much attention to it.
I found the person that employed me in the first place via twitter. I DM her, and she informed me that her company doesn't use that service, and never did. As it turned out, someone actually stole her credentials. Meaning - they used her private image, company profile, everything but an actual email that they used for registration, so when I was researching this company online, prior to the actual attack - everything checked out.
This is how I got tricked into downloading a ransomware. This hacker was dedicated, used an existing company profile, and he was consistent in his efforts.
<blockquote class="imgur-embed-pub" lang="en" data-id="a/4smio"><a href="//imgur.com/4smio"></a></blockquote><script async src="//s.imgur.com/min/embed.js" charset="utf-8"></script>
So, in my humble opinion - it is evident that even if you are careful and well aware of the online threats, you can still get infected. I am not sure why would someone go this far just to get to my computer, and I am guessing that I am just one of the many that this person tricked into downloading a virus, but I am probably one of the few users of this service that are actually prepared for this kind of violation. I always backup my files (I literally backup everything biweekly), and I always check every suspicious link before clicking through. In this case, I was simply outplayed by someone who went that extra mile to get me through a service that I trusted completely.
This is why I believe that companies, institutions, and primarily services that are handling business transactions (in this case, the freelancing company actually handles funds and payments as well), should mind both their and my safety and vouch that people that they are referring me to aren't hackers and cyber criminals. Is this too much to ask for in the year 2016?
Approximately 90% of victims are home users. More than 300.000 attacks happened within the US alone in 2015. This figure is skyrocketing in 2016, and we can expect millions of users affected by this issue by the end of the year 2020. In short - if I am paying your company for services, products, or anything at all, I expect that you care about my online safety. And yours as well.
References:
https://www.securelink.com/securelink-blog/2016-the-year-of-ransomware/
https://securelist.com/analysis/kaspersky-security-bulletin/73038/kaspersky-security-bulletin-2015-overall-statistics-for-2015/
Anonymous
Aug 31st 2016
8 years ago
Thanks for sharing your story! That certainly is an attack. It's definitely a different issue than the various exploit kit-based campaigns I run across, much like mousetraps, set up across the web. My issue isn't that I believe people aren't getting attacked (which I know happens), but the media portrayals that lump wide-scale campaigns that I see with the targeted attacks like you've experienced.
I like seeing affected people tell more stories like yours, where they share the details and provide a clearer picture of the dangers. Something more concrete that can provide a valid counterpoint to what I've been seeing.
Your line "even if you are careful and well aware of the online threats, you can still get infected" is a point well taken.
Thanks again for the details and your perspective. I always appreciate the dialogue, and I hope this is shared more widely.
Regards,
Brad Duncan
ISC Handler
Anonymous
Aug 31st 2016
8 years ago