NTP DDoS Counts Have Dropped
I was poking around the usual online rags and found a piece on Threat Post. [1] Mike Mimoso was highlighting the decline of the NTP DDoS hole found earlier in the year. The ISC covered it in our diary a few months back.
NTP Reflection Attack
Ongoing NTP Amplification Attacks
NTP Reflection Attacks Continue
So, I went poking through the port data and noticed a good correlation to the Threat Post story. The numbers indicate a sharp decrease in vulnerable systems for the NTP monlist issue. I'd like to suggest that while pundits are citing slow progress for patching Heartbleed, that in actuality, the Heartbleed issue is responsible for the sudden change. The month of May showed an extensive effort for patching and truing up patch levels because of Heartbleed. This effort likely assisted in the NTP issue being patched along with it. The following graph was taken from ISC data gathered here:
https://isc.sans.edu/port.html?&port=123
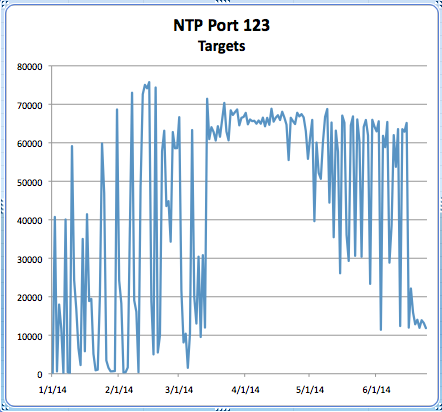
Feel free to share your thoughts on this one.
[1] http://threatpost.com/dramatic-drop-in-vulnerable-ntp-servers-used-in-ddos-attacks/106835


Comments