Strolling through Cyberspace and Hunting for Phishing Sites
From time to time and as much as my limited time permits, I often explore the Internet and my DShield logs to see if I can uncover any interesting artifacts that suggest nefarious behaviour. Time-driven events such as tax filing are also considered when I perform such hunting activities. I recently discovered one such site masquerading as the Inland Revenue Authority of Singapore (IRAS) and observed some interesting points.
Firstly, let's look at the website's overall design and feel. Figure 1 below shows the screen capture of the website.
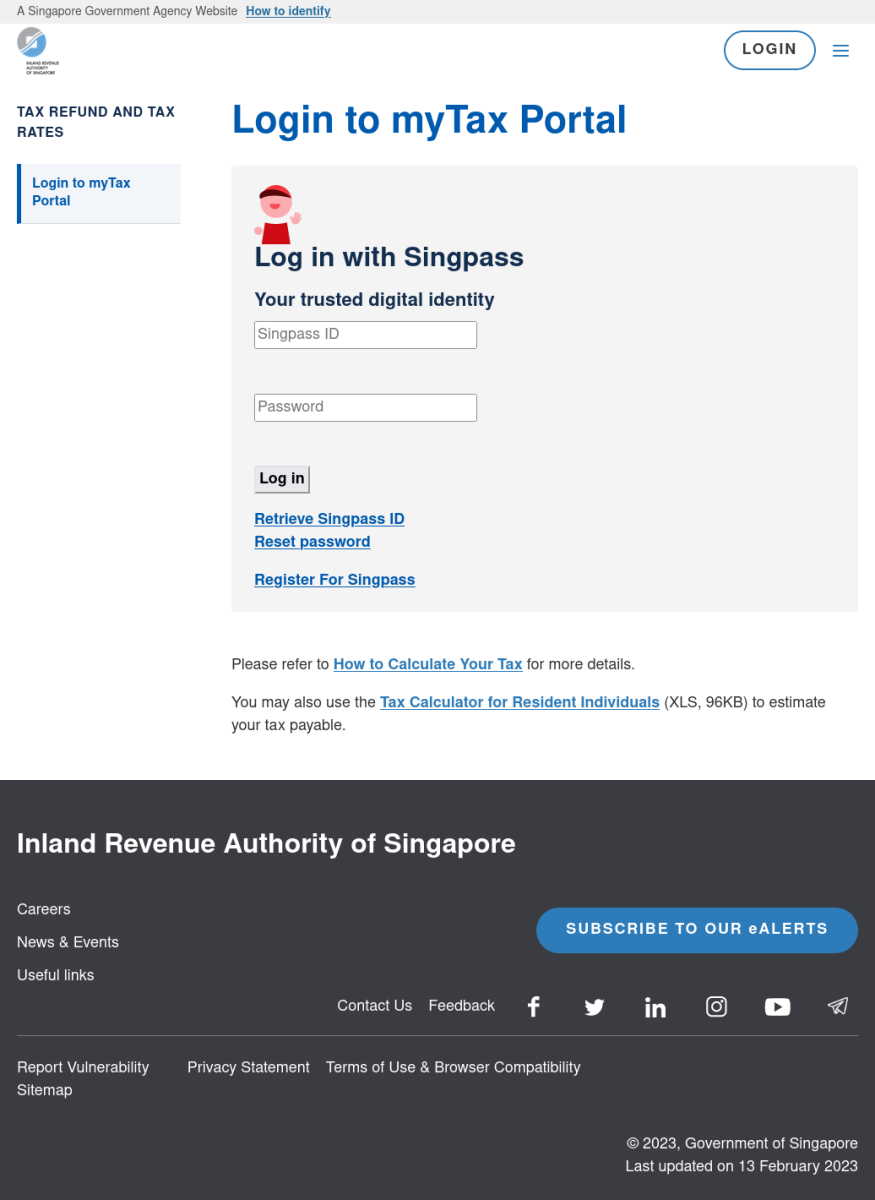
Figure 1: Screenshot of IRAS Phishing Site
The website would look legitimate for individuals unfamiliar with the official IRAS website but had some significant graphical differences from the official tax portal. Again, this website asks users to input their Singapore Personal Access (Singpass) credentials to access government and private services (such as banking) in Singapore. Most of the external links redirect to legitimate Singapore government websites. It was observed that this particular site elected to use an outdated tax calculation spreadsheet (Year of Assessment 2021 vs current Year of Assessment 2022) that was available on the legitimate IRAS website. Similar to a phishing site I analysed previously [1], the webpage checked for the existence of inputs and would highlight if the input fields were not filled in (with reference to Figure 2).
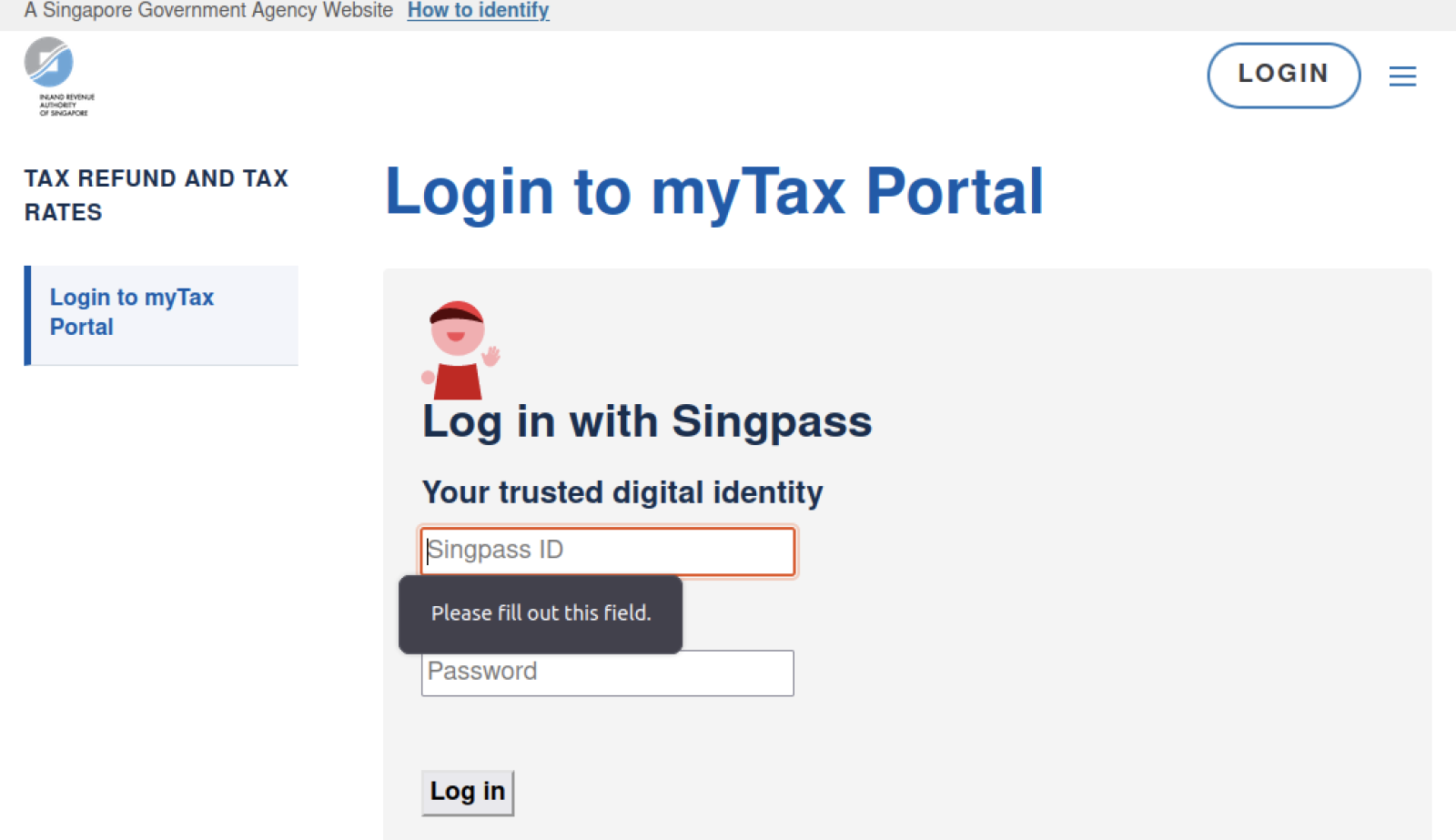
Figure 2: Input Validation Check
Submitting any input to the website will cause the site to redirect to a separate page index2.php, and have parameters such as "gonna=&realip=" in the URL, with your IP address reflected in the "realip=" parameter. After checking the site's HTML code, it was interesting to note that most of the HTML code was copied from the original site. However, some of the .js files had the additional French word "téléchargement" (after consulting fellow ISC handlers who spoke French, it meant downloading).
Finally, I was curious about who owned the website and its origins. Checking the whois records yielded the following information (Figure 3):
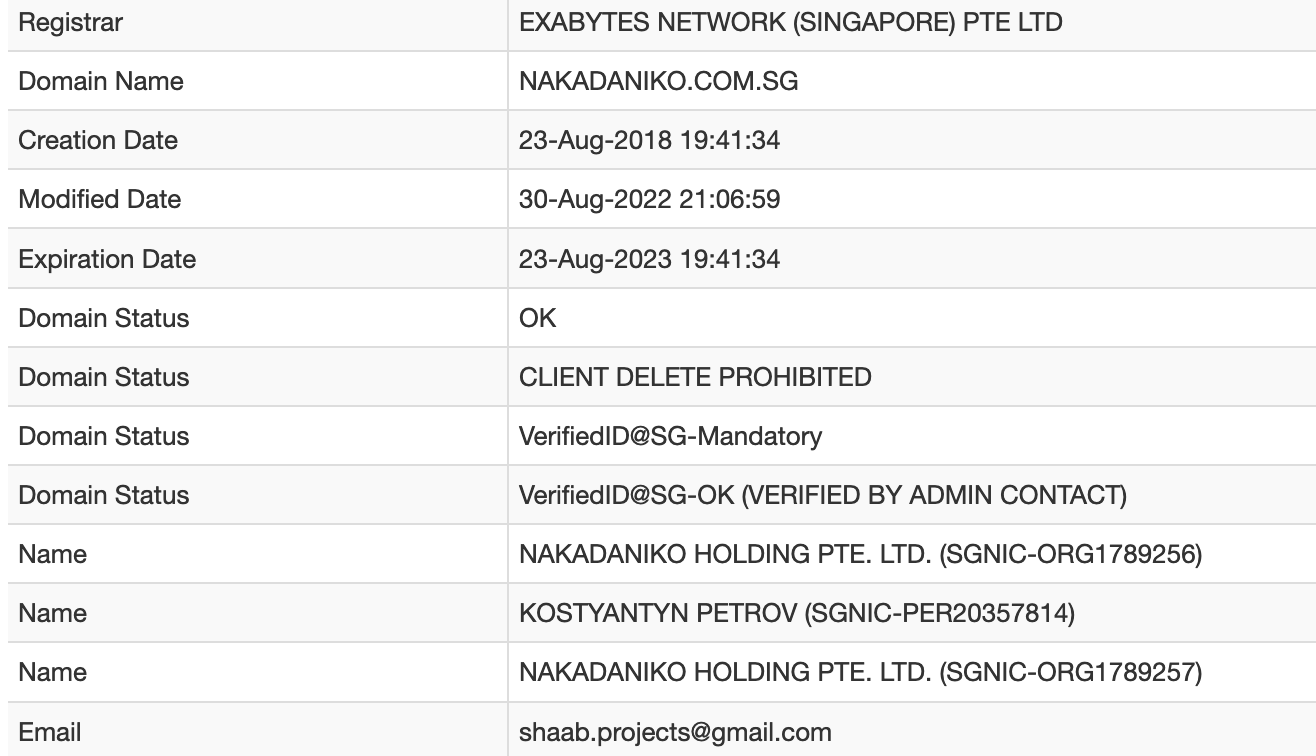
Figure 3: Whois Records of Website
Checking the company records did not yield much information, and the original site did not appear to have anything special. The site may have been created for security awareness purposes, red teaming or used as an actual phishing site. At the point of this diary's publication, the website was still publicly accessible. Nevertheless, the site has been reported to the Singapore Computer Emergency Response Team (SingCERT) for further investigation.
Indicators of Compromise (IOCs):
hxxps://iras[.]nakadaniko[.]com[.]sg
References:
[1] https://isc.sans.edu/diary/28870
-----------
Yee Ching Tok, Ph.D., ISC Handler
Personal Site
Mastodon
Twitter


Comments