Assemblyline as a Malware Analysis Sandbox
If you are looking for a malware sandbox that is easy to install and maintain, Assenblyline (AL) [1] is likely the system you want to be part of your toolbox. "Once a file is submitted to Assemblyline, the system will automatically perform multiple checks to determine how to best process the file. One of Assemblyline's most powerful functionalities is its recursive analysis model."[2]
First step, install the server. My server configuration is as follow:
- Ubuntu 22.04
- Ubuntu Server (minimized)
- 8+ Cores
- 16+ GB RAM
- 100 GB
- 100+ GB /var/lib/docker
- Static IP
After rebooting and before installing AL, I update the server and added the following packages:
$ sudo apt-get update
$ sudo apt-get upgrade
$ sudo apt-get install -y apt-transport-https ca-certificates curl gnupg-agent software-properties-common
$ sudo apt-get install net-tools open-vm-tools htop ntp bind9-utils vim
Setup a separate disk for the docker which will also store the sample malware. Mine is 100 GB:
$ sudo cfdisk /dev/sdb
$ sudo pvcreate /dev/sdb1
$ sudo vgcreate malware_vg01 /dev/sdb1
$ sudo vgdisplay malware_vg01
$ sudo lvcreate -n /dev/mapper/malware_vg01-virus --size 99G malware_vg01
$ sudo lvdisplay malware_vg01
$ sudo mkfs.xfs /dev/malware_vg01/virus
Add the new disk to /etc/fstab
$ sudo vi /etc/fstab
Add: /dev/malware_vg01/virus /var/lib/docker xfs defaults,noatime,nosuid 0 0
$ sudo mkdir -p /var/lib/docker
$ sudo mkdir -p /etc/docker
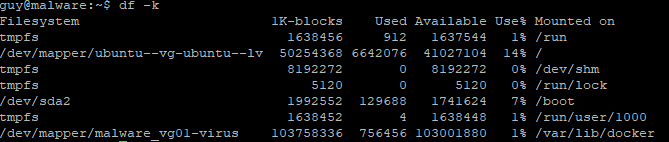
$ sudo mount -a
$ df -k
The server is ready to install Assemblyline. Next, I followed the instructions here to install the software. I selected Docker to install AL for my VM appliance. After completing the installation, it is time to login: admin:admin
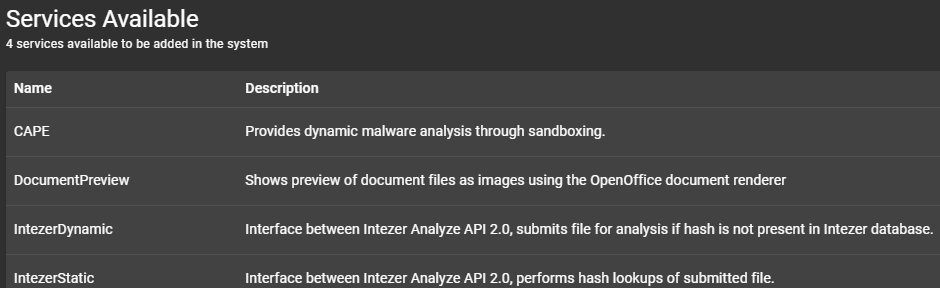
After logging in, check the Services tab for other Services Available you might choose to install. Some of them you need are paid the vendor to access the service (i.e. IntezerDynamic, IntezerStatic) while other are free to use and might need to register to enable them.
Next, it is time to configure some of the other services under the Services tab such as adding an API key to use them (i.e. Virustotal)
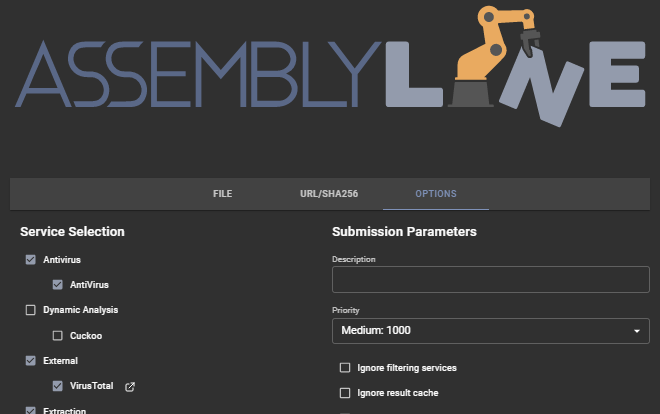
Before submitting any files, check out the Options tab to set other scan services:
Submitting Files via API
This is an example to submitting a sample via Rest API [4]. Check the reference where to go to create an API key in an account in the sandbox with the word mykey to generate the key. Here is an example to submit a file to AL:
$ curl -X POST https://malware/api/v4/submit/ \
-k --insecure \
-H 'x-user: admin' \
-H 'x-apikey: mykey:SomeApiKeyHere' \
-H 'accept: application/json' \
-F 'bin=@myfile.txt'
$ curl -X POST https://malware/api/v4/submit/ -k --insecure -H 'x-user: admin' -H 'x-apikey: mykey:SomeApiKeyHere' -H 'accept: application/json' -F 'bin=@myfile.txt'
Submitting Files to AL
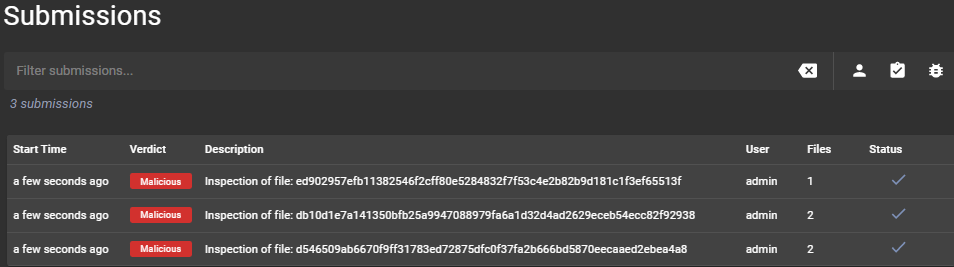
Using some of the files uploaded to my DShield sensor, I submitted 3 of them using the API for analysis.
AL release regular updates who can be seen by clicking on the Bell in the top right corner which shows in green the current version. I found over time the following worked best for me to update my AL by doing the following commands in the following order:
Updating AL
$ sudo apt-get update
$ sudo apt-get upgrade
$ cd ~/deployments/assemblyline
$ sudo docker-compose pull
$ sudo docker-compose build
$ sudo docker-compose up -d
$ sudo docker-compose stop
$ sudo docker-compose start
Indicator of Compromised
ed902957efb11382546f2cff80e5284832f7f53c4e2b82b9d181c1f3ef65513f
db10d1e7a141350bfb25a9947088979fa6a1d32d4ad2629eceb54ecc82f92938
d546509ab6670f9ff31783ed72875dfc0f37fa2b666bd5870eecaaed2ebea4a8
[1] https://cybercentrecanada.github.io/assemblyline4_docs/overview/how_it_works/
[2] https://cybercentrecanada.github.io/assemblyline4_docs/user_manual/submitting_file/
[3] https://cybercentrecanada.github.io/assemblyline4_docs/installation/appliance/docker/
[4] https://cybercentrecanada.github.io/assemblyline4_docs/integration/rest/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu




Comments