Live Linux IR with UAC
The other day, I was looking for Linux IR scripts and ran across the tool Unix-like Artifacts Collector or UAC(1) created by Thiago Lahr. As you would expect, it gathers most live stats but also collects Virtual box and Docker info and other data on the system. It can dump results files to SFTP, Azure, S3, and IBM storage natively.
With any tool, you should always test to understand how it affects your system. I ran a simple file timeline collection before and after to see what changes were made.
#git clone https://github.com/tclahr/uac.git
#mac-robber / >before
#uac -a live_response ../
#mac-robber / > after
As expected, files on the system have their access time updated when the tool reads files. Some tools do reset the access times back, but this one does not. It would be best if you collected file times before running the rest of the script. You can specify this via the command line
#uac -a bodyfile/bodyfile.yaml, live_response/\*. .
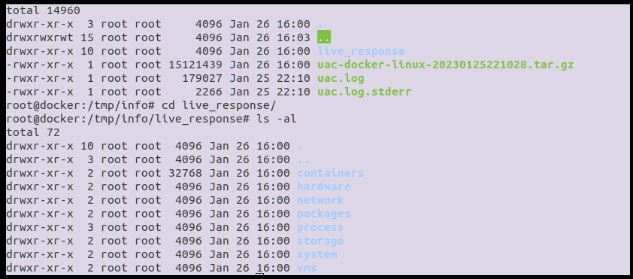
The results are a tar.gz file; when extracted, they have artifacts in the below folder structure.
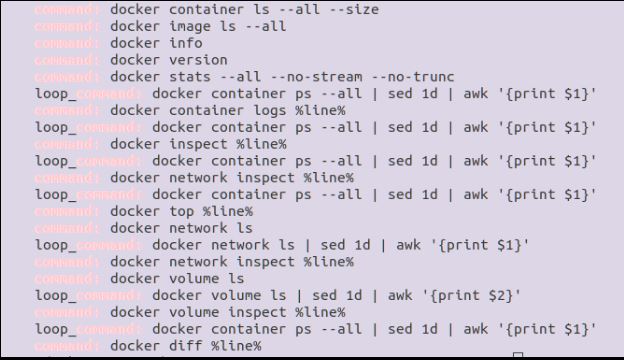
To see what commands it uses to gather data, you can drop into one of the folders under live response and look at at the yml files.
#cd /tmp/usb/uac/artifacts/live_response/containers
#grep 'command:' docker.yaml
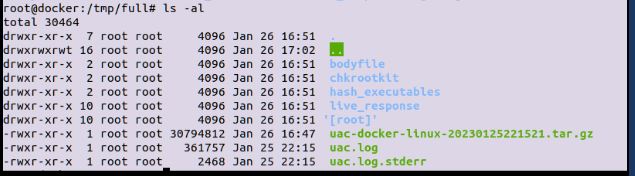
You can also create a super timeline with the data that it collected with a Plaso docker(2). If you do a full collection, it also grabs copies of files in the "Root" dir and the file system line in the bodyfile dir.
UAC can also dump memory
#./uac -a memory_dump/avml.yaml
Its a potent tool that acts as an IR collection "swiss army knife". You can create a collection profile and customize lots of things. Before you add it to your bag of tools, you should test it in many situations and understand its limitations and usage. After more testing and comfort with it, I plan on adding it to my group of collection tools.
Are you using another IR script that you like? Have you rolled your own? Let me know in the comments.
(1) https://github.com/tclahr/uac
(2) https://tclahr.github.io/uac-docs/super_timeline/
--
Tom Webb
@tom_webb@infosec.exchange


Comments