Malicious Calendar Subscriptions Are Back?
Did this threat really disappear? This isn’t a brand new technique to deliver malicious content to mobile devices but it seems that attackers started new waves of spam campaigns based on malicious calendar subscriptions. Being a dad, you can imagine that I always performed security awareness with my daughters. Since they use computers and the Internet, my message was always the same: “Don’t be afraid to ask me, there are no stupid questions or shame if you think you did something wrong”.
A few days ago, my youngest one came to me and told me she had the impression that her iPhone was hacked. After a quick check and reassuring her, I switched my dad's cap to the handler one and had a deeper look.
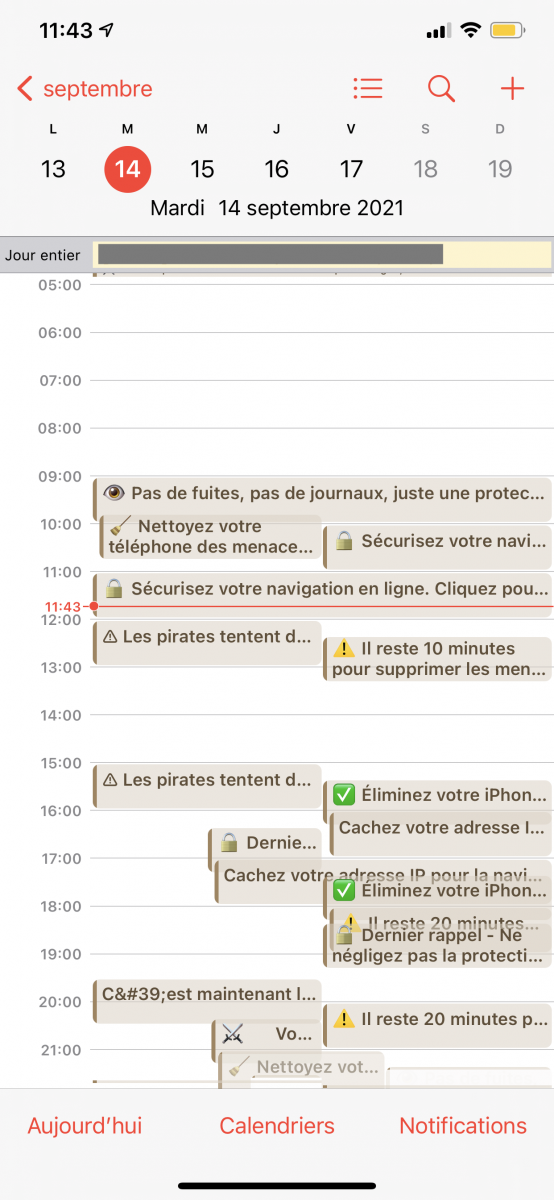
She told me that a pop-up was displayed on the screen and clicked on “Ok” too quickly. It was an unwanted calendar invitation and she subscribed to a spam feed. Her calendar became quickly flooded with events:
They are in French but easy to understand. They pretend to notify you about viruses found on the device and, using reminders, they keep the pressure on the victim:
If you visit the proposed link, you'll get more annoying ads pages, etc. This time hopefully, nothing very malicious but, seeing the latest iOS vulnerabilities[1], this technique could be used to deliver exploits. To get rid of all those messages, you just need to unsubscribe from the calendar.
In conclusion, already read carefully all popups displayed on your mobile phones (obviously on any type of device!).
[1] https://support.apple.com/en-us/HT212807
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key



Comments