Finding Metasploit & Cobalt Strike URLs
Metasploit and Cobalt Strike generate shellcode for http(s) shells. The URLs found in this shellcode have a path that consist of 4 random alphanumeric characters. But they are not completely random: their 8-bit checksum is a member of a small set of constants.
The 8-bit checksum is the sum of the ASCII value of the 4 characters of the path. Take the least significant byte of the sum, and compare it with this table:
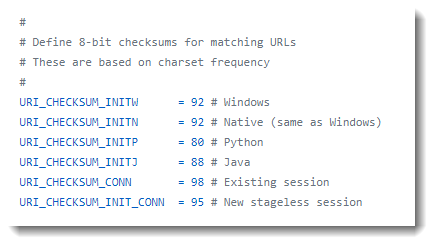
If the checksum is equal to one of these values, the URL could be generated by Metasploit or Cobalt Strike.
I illustrate this with Brad's capture file of Qakbot & Cobalt Strike traffic and my tool metatool.py.
Wireshark's command-line tool tshark is what I used to produce a complete packet tree for each packet. The URLs we are looking for will be somewhere in this output:
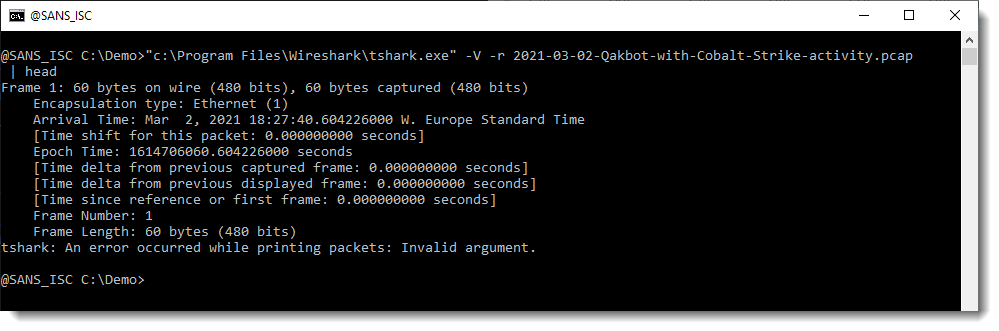
And then I pipe this output into my metatool.py with command url8:
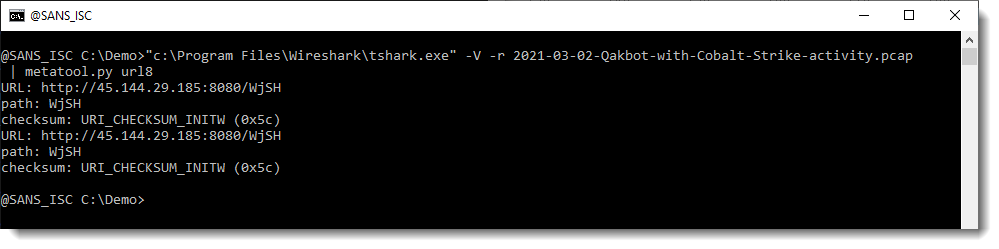
metatool found 2 (identical) URLs whose path has an 8-bit checksum equal to 0x5C (92), or URI_CHECKSUM_INITW, i.e. the 8-bit checksum for a Windows payload.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments