Phishing kits as far as the eye can see
If you’ve never delved too deep into the topic of phishing kits, you might – quite reasonably – expect that they would be the sort of tools, which are traded almost exclusively on dark web marketplaces. This is however not the case – many phishing kits (or “scam pages” or “scamas” as they are called by their creators) are quite often offered fairly openly on the indexed part of the web as well, as are the corresponding “letters” (i.e. the e-mail templates), e-mail validity checkers and other related tools. You may take a look at what is out there yourself – simply search for “scam page” along with the name of your favorite large bank or major online service on Google…
Since I haven’t done so in a while, last weekend I decided to take a look at phishing kits that are available on the “surface” web – more specifically, at those, which have been published during this year. I thought it might be interesting to see what their prices were, which brands and services they “covered” the most and whether there would be any significant increase in the number of phishing kits on offer in the second and third quarter of the year (i.e. in relation to the Covid-19 situation).
The idea was to gather information on at least 100 different phishing kits, as although it would not be a large sample size by any means, it should be enough to give us at least some idea of how things stood. I started by looking at YouTube and planned to go through Google, GitHub and a few file upload and e-commerce sites afterwards. Since I have, however, managed find 104 kits for sale/free download from this year on YouTube alone, just using the first search term I tried, I decided to stop there.
Each of the phishing kits was presented in a standalone video showing its capabilities. Most of the videos had terms “undetected” and “clean” in their titles in an attempt to make the phishing kits look more desirable (and definitely not backdoored).
Some of the videos were offering e-mail templates, access to complex phishing platforms, or tutorials in addition to the scam pages themselves, either as part of a bundle with specific phishing kit or at a premium. Similar selection of additional tools and other materials was available on external e-commerce platforms, where some the kits shown off in the videos were sold.

Of the 104 kits, 18 were offered free of charge (and at least one of these was backdoored - this wasn't mentioned in the video description so it was probably intended as a surprise bonus feature). For 76 of them, price was available by e-mail/ICQ/Telegram/Facebook only and the 10 remaining ones ranged in price from $10 to $100.
The 86 “commercial” phishing kits were offered by 21 sellers, with the most prolific one of them being responsible for 22 different scam pages.
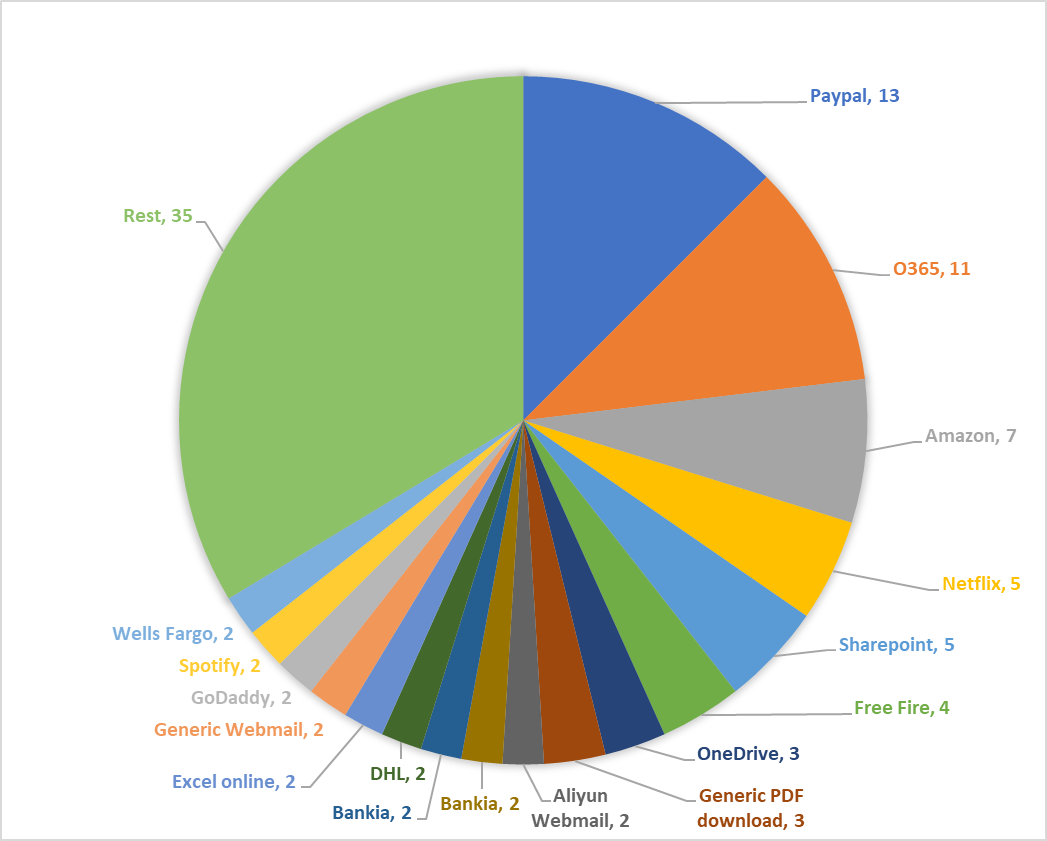
At all, the phishing kits “simulated” sites of 53 different services or brands, from Adobe to Zoom. You may take a look at all of the services and brands, which were “used” by at least two different phishing kits, in the following chart. It probably won’t come as a much of a surprise that PayPal and Office 365 were the two “covered” the most often, but some of the others (e.g. Free Fire) might be a bit unexpected.
It should be mentioned that although most global phishing statistics published for 2020 so far [1,2] don’t show any significant rise in the numbers of spam and phishing e-mails in the wild in relation to Covid-19, the frequency of publishing new phishing kits on “surface” web (or at least on YouTube) seems to have increased significantly from the second half of March onward.
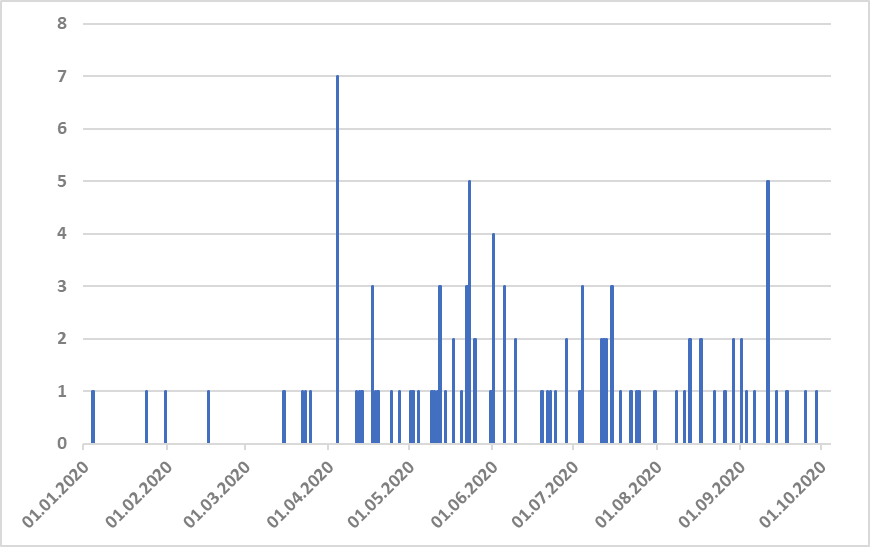
Whether this increase is due to the Covid-19 situation or because YouTube managed to clear most of the phishing kit videos from the first quarter of this year is impossible to say with any certainty, though I tend to lean towards the former explanation being the more probable one.
In any case, as this short excursion to YouTube shows, even on the indexed part of the web there are phishing kits galore…and there is little reason to expect that it will be much different in the near future. Therefore, if you work in infosec in any organization, whose customers might be a good target for semi-targeted phishing, try looking for phishing kits spoofing your brand or service on Google from time to time – you might be surprised at what you find…
[1] https://docs.apwg.org/reports/apwg_trends_report_q2_2020.pdf
[2] https://securelist.com/spam-and-phishing-in-q2-2020/97987/


Comments