Malicious .tar Attachments
We were informed about a malicious email campaign that uses .iso and .tar attachments.
We've covered .iso attachments before in diary entry "Malicious .iso Attachments": the .iso contains a malicious executable and can be opened with vanilla Windows 8 and later.
For .tar attachments, it's a bit different. The .tar attachment also contains a malicious executable (tar is an Unix archive format), but it can not be opened with vanilla Windows. Archiving software like the popular WinZip has to be installed, for the user to be able to open the .tar attachment.
Adversaries use .tar files for the same reason as .iso files:
1) the malware is contained in a container file, and can thus more easily evade detection
2) the "mark-of-the-web" is not propagated
The "mark-of-the-web" is metadata that indicates that a file originated from the Internet, and has thus a lower trust value. It is implemented with alternate data streams. Applications like Outlook create this metadata: when an attachment is opened or saved to disk, the metadata is created to mark it as originating from the Internet.
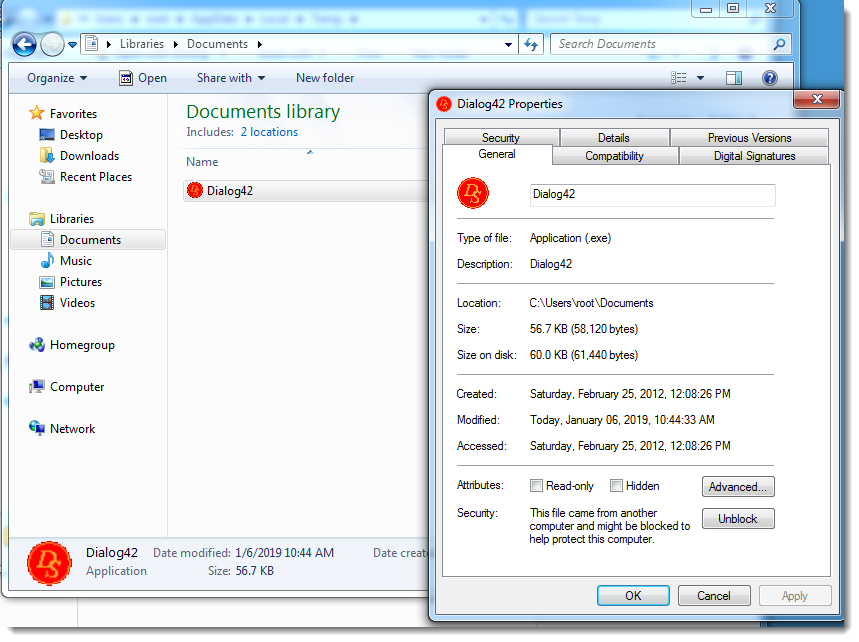
Here is a .tar file (Dialog42.tar, containing Dialog42.exe) with metadata to mark it as originating from the Internet:
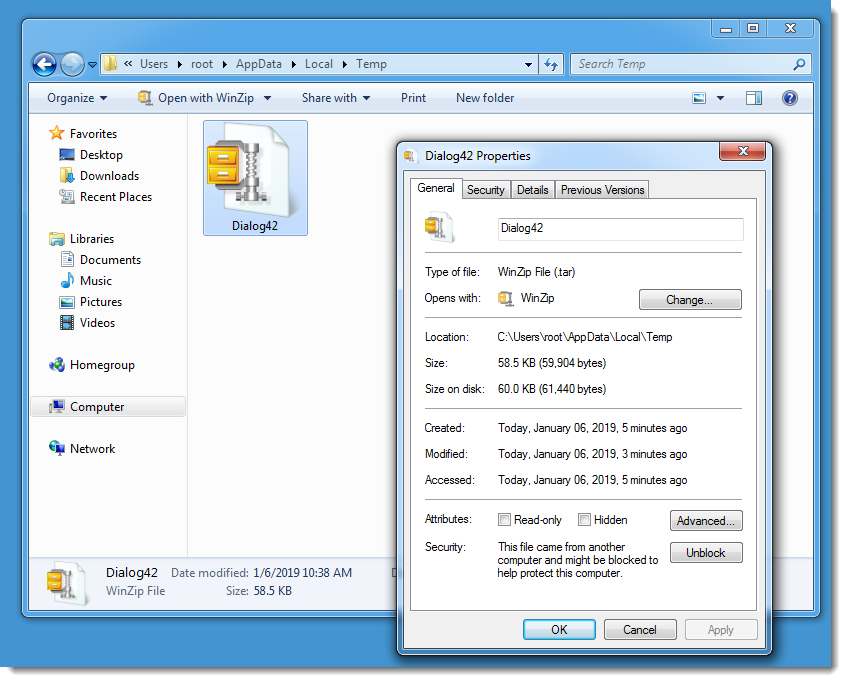
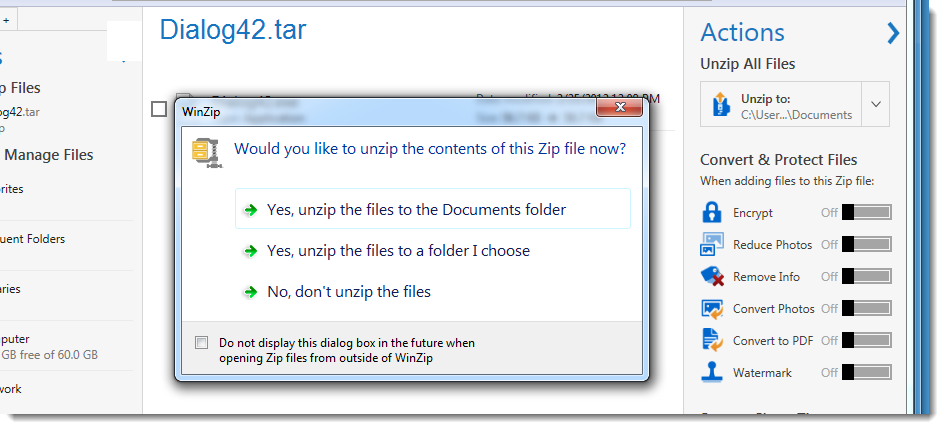
When the .tar file is opened with WinZip to extract the .exe file, the metadata is not propagated to the extracted .exe file:
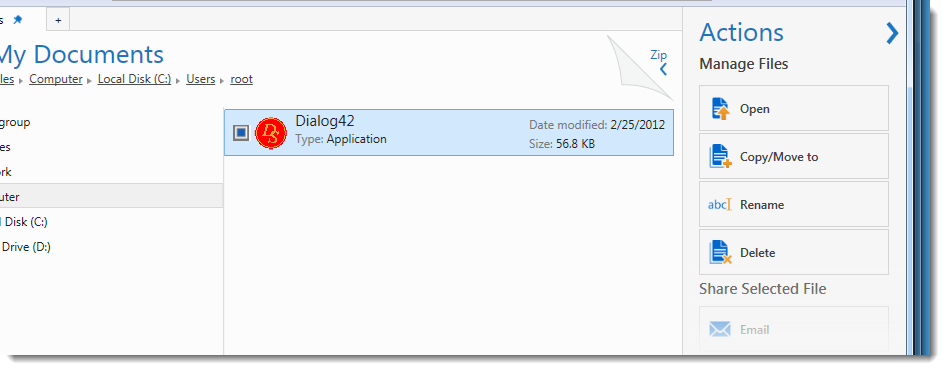
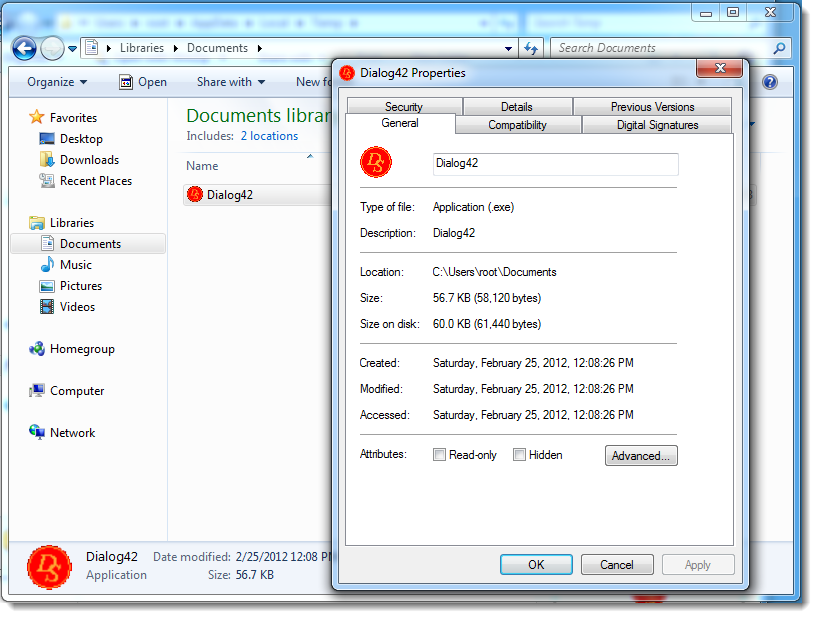
When the executable is started, no warning is displayed:
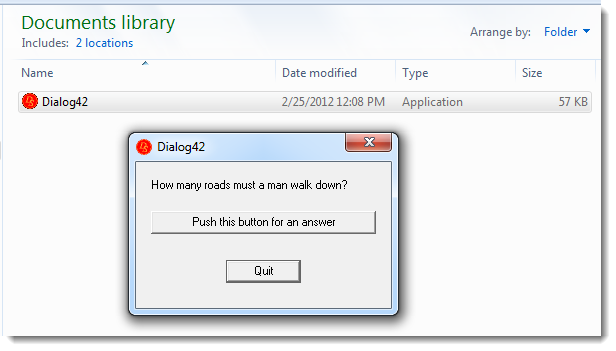
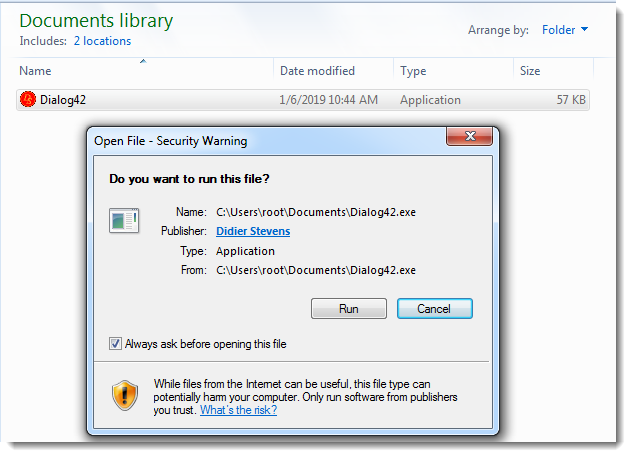
If the "mark-of-the-web" would have been propagated (e.g. the metadata would have been copied from the container to the extracted files), then the user would receive a warning before the file was executed:
Using less popular container formats on Windows allows malware authors to evade detection and reduce the number of alerts, at the risk of ending up on a Windows machine that can not open the container.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments