Phishing Attempts That Bypass 2FA
In today's world, we all try to do as much as we can to be secure while online. Most have learned the signs to try to spot phishing attempts: misspelled words, broken english, urgent requests etc. We even implement 2FA to help prove that someone is who they say they are when they are authenticating to a site. As we try to up our security game, the bad guys up their tactics too. Amnesty.org shared an interesting write up about phishing attacks that are bypassing 2FA. According to the article, there is a large phishing campaign that is that is targeting Gmail and Yahoo accounts.
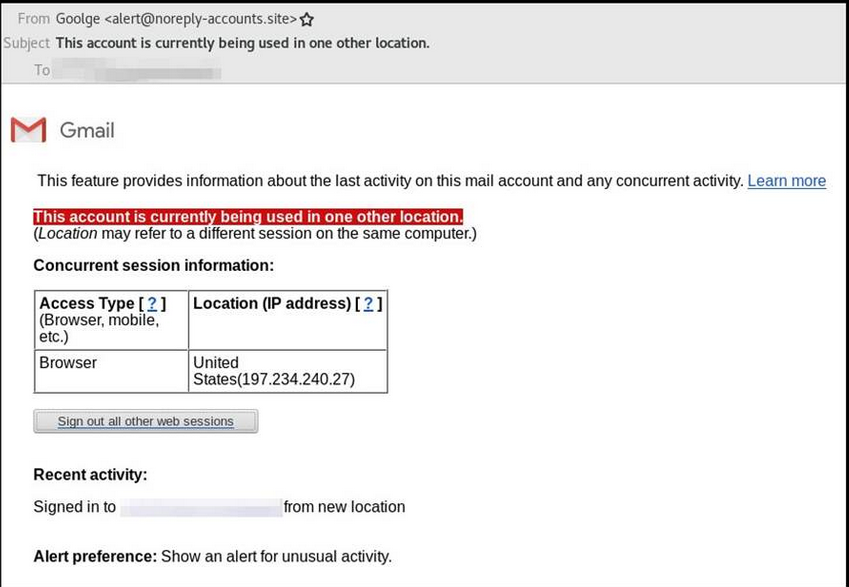
The emails being sent are "proported" to be alerts you would see if someone logged in from another location. This is an example of one the emails being reported:
When the user clicks on the link, they are directed to the phishing site. It seems the server is also running an installation of Selenium with Chrome Driver. Chrome Driver is basically a server that does the implementation of WebDriver, which is used for automated testing of web applications. You can do stuff such as navigating to web pages, user input, JavaScript execution etc. So this phishing site can now interact with the input provided by the user and capture it. If you think MITM attack at this point, you would be correct. How much manipulation is actually done, is not really known, nor the point. The attacker is forwarding the request to authenticate to the actual server. The password is provided and then the user is prompted for the 2FA (whatever method is being used). The user now has the token that has been sent to the user's cell phone (or whatever method is used for the token) and input into the phishing site to authenticate. Plenty of time is allowed for the attacker to actually use the token and authenticate into the account and setup an "app password" so they don't have to mess with 2FA anymore. Just use Outlook or some other app to keep a persistant hold on the account using the app password. The user is none the wiser at this point. Everything looks completely normal.
User awareness is really key, especially as the attacks get more sophisticated. If you look at the email above, it is from "Goolge" which isn't readily apparent at a quick glace. Getting users to think before they click is key, but how else would you detect something like this. Any ideas or suggestions for how to detect this, please send them in!
https://www.amnesty.org/en/latest/research/2018/12/when-best-practice-is-not-good-enough/
https://support.microsoft.com/en-us/help/12409/microsoft-account-app-passwords-and-two-step-verification
http://chromedriver.chromium.org/
https://www.seleniumhq.org/


Comments